A Linux administrator needs to remove software from the server. Which of the following RPM options should be used?
A.
rpm -s
B.
rm -d
C.
rpm -q
D.
rpm -e
rpm -e
Due to low disk space, a Linux administrator finding and removing all log files that were modified more than 180 days ago. Which of the following commands will accomplish this task?
A.
find /var/log -type d -mtime +180 -print -exec rm {} \;
B.
find /var/log -type f -modified +180 -rm
C.
find /var/log -type f -mtime +180 -exec rm {} \
D.
find /var/log -type c -atime +180 –remove
find /var/log -type d -mtime +180 -print -exec rm {} \;
A systems technician is working on deploying several microservices to various RPM-based systems, some of which could run up to two hours. Which of the following commands will allow the technician to execute those services and continue deploying other microservices within the same terminal section?
A.
gedit & disown
B.
kill 9 %1
C.
fg %1
D.
bg %1 job name
gedit & disown
A junior administrator is trying to set up a passwordless SSH connection to one of the servers. The administrator follows the instructions and puts the key in the authorized_key file at the server, but the administrator is still asked to provide a password during the connection.
Given the following output:

Which of the following commands would resolve the issue and allow an SSH connection to be established without a password?
A.
restorecon -rv .ssh/authorized_key
B.
mv .ssh/authorized_key .ssh/authorized_keys
C.
systemctl restart sshd.service
D.
chmod 600 mv .ssh/authorized_key
systemctl restart sshd.service
A Linux administrator cloned an existing Linux server and built a new server from that clone. The administrator encountered the following error after booting the cloned server:
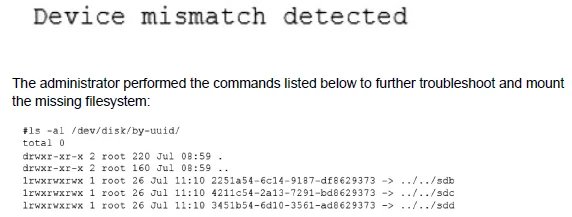
Which of the following should administrator use to resolve the device mismatch issue and mount the disk?
A.
mount disk by device-id
B.
fsck -A
C.
mount disk by-label
D.
mount disk by-blkid
mount disk by-blkid
Some servers in an organization have been compromised. Users are unable to access to the organization’s web page and other services. While reviewing the system log, a systems administrator notices messages from the kernel regarding firewall rules:

A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option B
A Linux systems administrator receives reports from various users that an application hosted on a server has stopped responding at similar times for several days in a row. The administrator logs in to the system and obtains the following output:
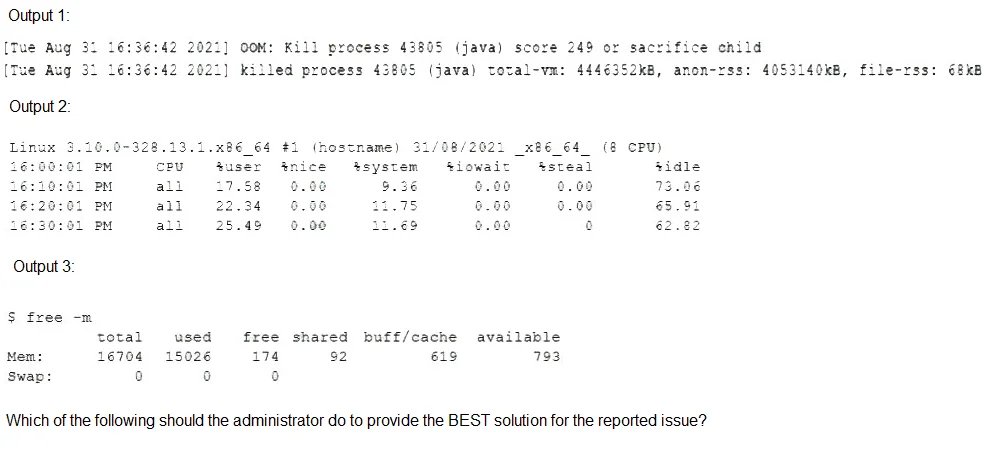
A.
Configure memory allocation policies during business hours and prevent the Java process from going into a zombie state while the server is idle.
B.
Configure a different nice value for the Java process to allow for more users and prevent the Java process from restarting during business hours.
C.
Configure more CPU cores to allow for the server to allocate more processing and prevent the Java process from consuming all of the available resources.
D.
Configure the swap space to allow for spikes in usage during peak hours and prevent the Java process from stopping due to a lack of memory.
Configure memory allocation policies during business hours and prevent the Java process from going into a zombie state while the server is idle.
After installing a new version of a package, a systems administrator notices a new version of the corresponding, service file was Installed In order to use the new version of the, service file, which of the following commands must be Issued FIRST?
A.
systemctl status
B.
systemctl stop
C.
systemctl reinstall
D.
systemctl daemon-reload
systemctl daemon-reload
A systems administrator has been unable to terminate a process. Which of the following should the administrator use to forcibly stop the process?
A.
kill -1
B.
kill -3
C.
kill -15
D.
kill -HUP
E.
kill -TERM
kill -3
Joe, a user, is unable to log in to the Linux system. Given the following output:

Which of the following commands would resolve the issue?
A.
usermod -s /bin/bash joe
B.
pam_tally2 -u joe -r
C.
passwd -u joe
D.
chage -E 90 joe
usermod -s /bin/bash joe
After installing some RPM packages, a systems administrator discovers the last package that was installed was not needed. Which of the following commands can be used to remove the package?
A.
dnf remove packagename
B.
apt-get remove packagename
C.
rpm -i packagename
D.
apt remove packagename
dnf remove packagename
Users have reported that the interactive sessions were lost on a Linux server. A Linux administrator verifies the server was switched to rescue.target mode for maintenance. Which of the following commands will restore the server to its usual target?
A.
telinit 0
B.
systemctl reboot
C.
systemctl get-default
D.
systemctl emergency
systemctl reboot
| Page 8 out of 31 Pages |
| Previous |