A Linux administrator modified the SSH configuration file. Which of the following commands should be used to apply the configuration changes?
A.
systemctl stop sshd
B.
systemctl mask sshd
C.
systemctl reload sshd
D.
systemctl start sshd
systemctl reload sshd
Summary:
After modifying a service's configuration file (in this case, for the SSH daemon, sshd), the service needs to be made aware of the new settings. The goal is to apply the changes without causing a full service interruption that would drop existing user connections. The correct command will gracefully instruct the service to reload its configuration file while maintaining its current running state and active sessions.
Correct Option:
C. systemctl reload sshd:
This is the correct command. The reload instruction sends a specific signal (SIGHUP) to the sshd process. This signal tells the SSH daemon to reread its configuration file (sshd_config) and apply the new settings without shutting down. Crucially, it maintains existing connections, only applying the new configuration to subsequent connection attempts.
Incorrect Options:
A. systemctl stop sshd:
This command would completely stop the SSH service. This would terminate all active SSH connections and prevent any new ones from being established until the service is started again. It is overly disruptive for a simple configuration change.
B. systemctl mask sshd:
This command does not apply configuration changes; it prevents the service from being started, manually or automatically. A masked service cannot be started until it is unmasked. This is a administrative lock, not a method for applying configs.
D. systemctl start sshd:
This command is used to start a service that is currently stopped. If the service is already running (as it would be after a configuration edit), this command would typically fail or have no effect. It does not force a reload of the configuration.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 3.1: "Given a scenario, use the appropriate system and service management commands to accomplish administrative tasks," which includes managing and troubleshooting systemd services. Knowing the difference between restart, reload, and stop/start is critical for applying configuration changes with minimal service impact.
A cloud engineer needs to check the link status of a network interface named eth1 in a Linux server. Which of the following commands can help to achieve the goal?
A.
ifconfig hw eth1
B.
netstat -r eth1
C.
ss -ti eth1
D.
ip link show eth1
ip link show eth1
Summary:
The engineer needs to verify the operational state of a specific network interface (eth1), specifically whether it has a physical/link-layer connection (carrier detection) and if the interface is administratively "UP". This requires a command that displays low-level network device information, including the link state flags.
Correct Option:
D. ip link show eth1:
This is the modern and correct command for this task. It displays the state of the network interface eth1. The output will show flags like UP (administratively enabled) and LOWER_UP (which indicates a physical link is detected), providing a clear view of the link status.
Incorrect Options:
A. ifconfig hw eth1:
The ifconfig command is considered deprecated. The hw option is used to set the hardware address (MAC address), not to display the link status. The standard ifconfig eth1 command shows some status information but the ip link command is more reliable and detailed for link state.
B. netstat -r eth1:
The netstat -r command displays the kernel routing table. It does not take an interface name as a filter in this way and does not show physical link status information.
C. ss -ti eth1:
The ss command is used to dump socket statistics. The -t flag is for TCP sockets, and -i shows internal TCP information. It is used for analyzing network connections, not for checking the physical or administrative state of a network interface.
Reference:
Linux man-pages project (ip-link): The official documentation for the ip link command, which is used to manage network devices.
A systems administrator is checking the system logs. The administrator wants to look at the last 20 lines of a log. Which of the following will execute the command?
A. tail -v 20
B. tail -n 20
C. tail -c 20
D. tail -l 20
Summary:
The administrator needs to view the most recent entries at the end of a log file. The tail command is specifically designed for this purpose, showing the last part of files by default. The correct command must use the appropriate option to specify the number of lines to display from the end of the file.
Correct Option:
B. tail -n 20:
This is the standard and correct command. The -n flag (number) instructs tail to output the last specified number of lines. Therefore, tail -n 20 [logfile] will display the last 20 lines of the given log file, which is exactly what the administrator wants to do.
Incorrect Options:
A. tail -v 20:
The -v (verbose) flag is used to always output headers giving file names. It is not used to specify the number of lines and is irrelevant to the task of limiting output to 20 lines.
C. tail -c 20:
The -c flag (bytes) outputs the last specified number of bytes from the file, not lines. This would show a fragmented, partial line and is not the intended way to view the last 20 log entries.
D. tail -l 20:
There is no -l (lowercase L) flag in the standard tail command. This is an invalid option and will result in an error.
Reference:
Linux man-pages project (tail): The official documentation explains the -n option for outputting the last N lines.
A Linux administrator is adding a new configuration file to a Git repository. Which of the following describes the correct order of Git commands to accomplish the task successfully?
A.
pull -> push -> add -> checkout
B.
pull -> add -> commit -> push
C.
checkout -> push -> add -> pull
D.
pull -> add -> push -> commit
pull -> add -> commit -> push
Summary:
The task is to add a new configuration file to a Git repository, which is a standard version control operation. The correct sequence must ensure the local repository is up-to-date, stage the new file, permanently save the change locally, and then upload that change to the remote repository for collaboration.
Correct Option:
B. pull -> add -> commit -> push:
This is the standard and correct sequence for contributing a change.
pull: First, integrate the latest changes from the remote repository to avoid conflicts.
add: Stage the new configuration file, telling Git to start tracking it.
commit: Permanently save the staged file to the local repository's history with a descriptive message.
push: Upload the local commit(s) to the remote repository to share the change with others.
Incorrect Options:
A. pull -> push -> add -> checkout:
This sequence is illogical. You cannot push before you have staged (add) and saved (commit) your changes. checkout is used for switching branches, not for adding new files.
C. checkout -> push -> add -> pull:
This order is incorrect. It attempts to push with no committed changes and stages the file (add) only after trying to push. The pull command is also performed too late, after other actions have already been attempted.
D. pull -> add -> push -> commit:
This sequence is invalid. The push command only sends committed changes to the remote server. You cannot push changes that have only been staged (add) but not yet committed.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This question aligns with Objective 1.2: "Given a scenario, perform version control using Git," which requires candidates to know the basic Git workflow and the function of common commands like pull, add, commit, and push. The official Git website, git-scm.com, is the canonical reference for this process.
A systems administrator installed a new software program on a Linux server. When the systems administrator tries to run the program, the following message appears on the screen.

Which of the following commands will allow the systems administrator to check whether the system supports virtualization?
A.
dmidecode -s system-version
B.
lscpu
C.
sysctl -a
D.
cat /sys/device/system/cpu/possible
lscpu
Summary:
The error message indicates the program cannot run because virtualization (KVM) is not available. This is typically due to the CPU lacking hardware virtualization support (Intel VT-x or AMD-V) or it being disabled in the BIOS. The administrator needs a command to check the CPU's features and capabilities to determine if virtualization is supported and enabled at the hardware level.
Correct Option:
B. lscpu:
This is the best command for this task. lscpu displays detailed information about the CPU architecture and its features. The administrator should look for Virtualization in the output (e.g., VT-x for Intel or AMD-V for AMD), which confirms hardware support. It also shows if hypervisor support is present.
Incorrect Options:
A. dmidecode -s system-version:
This command queries the DMI (SMBIOS) table to display only the system version string (e.g., the server model). It does not provide information about CPU features like virtualization support.
C. sysctl -a:
This command displays all kernel parameters. While it shows a vast amount of system information, it is not the most direct way to check for CPU hardware virtualization flags. The output is also very verbose and difficult to parse for this specific information.
D. cat /sys/device/system/cpu/possible:
This file shows the range of possible CPUs on the system (e.g., "0-3" for 4 cores). It does not provide any information about the features or capabilities of those CPUs, such as virtualization support.
Reference:
Linux man-pages project (lscpu): The official documentation describes lscpu as a command that displays information about the CPU architecture, including flags and virtualization features.
A Linux administrator wants to set the SUID of a file named dev_team.text with 744 access rights. Which of the following commands will achieve this goal?
A.
chmod 4744 dev_team.txt
B.
chmod 744 --setuid dev_team.txt
C.
chmod -c 744 dev_team.txt
D.
chmod -v 4744 --suid dev_team.txt
chmod 4744 dev_team.txt
Summary:
The administrator needs to set two distinct permissions on a file: the standard "744" access rights (owner: rwx, group: r--, others: r--) and the special SUID (Set User ID) bit. In the numeric (octal) mode used by chmod, special permissions (SUID, SGID, Sticky Bit) are represented by an extra digit prepended to the standard three-digit permission code. The SUID bit is represented by the number 4.
Correct Option:
A. chmod 4744 dev_team.txt:
This is the correct command. The four-digit octal mode 4744 breaks down as follows:
The first digit (4) sets the SUID bit.
The next three digits (744) set the standard permissions: 7 (rwx) for the owner, 4 (r--) for the group, and 4 (r--) for others.
This command achieves both requirements in a single, standard operation.
Incorrect Options:
B. chmod 744 --setuid dev_team.txt:
The chmod command does not have a --setuid option. Special permissions like SUID are set using the numeric prefix or the u+s symbolic notation, not with a long-format flag.
C. chmod -c 744 dev_team.txt:
The -c flag only provides a verbose output if a change is made. The permission mode 744 does not include the SUID bit (it would be 4744), so this command would only set the standard 744 permissions, not the SUID.
D. chmod -v 4744 --suid dev_team.txt:
Similar to option B, --suid is not a valid option for the chmod command. The -v flag is for verbose output, but the --suid flag is redundant and incorrect because the SUID is already specified by the leading 4 in the 4744 octal mode.
Reference:
Linux man-pages project (chmod): The official documentation explains the numeric mode, including the optional leading digit for setting special bits.
Which of the following is a function of a bootloader?
A.
It initializes all the devices that are required to load the OS.
B.
It mounts the root filesystem that is required to load the OS.
C.
It helps to load the different kernels to initiate the OS startup process.
D.
It triggers the start of all the system services.
It helps to load the different kernels to initiate the OS startup process.
Summary:
A bootloader is a small program that resides in the Master Boot Record (MBR) or EFI system partition. Its primary job is to bridge the gap between the computer's firmware (BIOS/UEFI) and the full operating system. After the firmware completes its hardware checks, it hands control to the bootloader, which is responsible for the next critical step in the startup process.
Correct Option:
C. It helps to load the different kernels to initiate the OS startup process:
This is the core, defining function of a bootloader. The bootloader's main task is to locate the operating system's kernel on the storage device, load it into memory, and then transfer control to it. Advanced bootloaders like GRUB can also present a menu to let users choose between different kernels or operating systems.
Incorrect Options:
A. It initializes all the devices that are required to load the OS:
This is the function of the computer's firmware (BIOS/UEFI). The firmware performs the Power-On Self-Test (POST) and initializes critical hardware before the bootloader even starts.
B. It mounts the root filesystem that is required to load the OS:
The bootloader itself does not mount the root filesystem. It loads the kernel and an initial RAM disk (initramfs), which contains the necessary drivers and tools to mount the root filesystem later in the boot process.
D. It triggers the start of all the system services:
This is the job of the init system (like systemd or SysVinit), which is the first process started by the kernel (PID 1). The bootloader's role is complete once the kernel is loaded and executing.
Reference:
GNU GRUB Manual: The documentation for GRUB, the most common Linux bootloader, describes its purpose as loading an operating system kernel.
A systems administrator requires that all files that are created by the user named web have read-only permissions by the owner. Which of the following commands will satisfy this requirement?
A.
chown web:web /home/web
B.
chmod -R 400 /home/web
C.
echo "umask 377" >> /home/web/.bashrc
D.
setfacl read /home/web
echo "umask 377" >> /home/web/.bashrc
Summary:
The requirement is to ensure that any new file created by the user web automatically has read-only permissions for the owner. This is not about changing existing files, but about setting a default permission for future files. The umask (user file creation mask) is the kernel variable that controls the default permissions for newly created files and directories by subtracting its value from the base permissions.
Correct Option:
C. echo "umask 377" >> /home/web/.bashrc:
This is the correct solution. The umask value is subtracted from the base permissions (typically 666 for files). A umask of 377 (octal) means:
Files: 666 - 377 = 400 (r-------- or read-only for owner)
By adding this command to /home/web/.bashrc, it sets this umask for every login shell the web user starts, ensuring all new files they create will have the required read-only permission for the owner.
Incorrect Options:
A. chown web:web /home/web:
This command changes the ownership of the /home/web directory to the user and group web. It does not affect the permissions of files within the directory, either existing or new.
B. chmod -R 400 /home/web:
This command recursively sets all existing files and directories in /home/web to read-only for the owner. However, it does not affect new files created afterward. Furthermore, applying 400 to directories would break them, as directories require the execute bit (x) to be accessible.
D. setfacl read /home/web:
This command is syntactically incorrect and does not make sense. setfacl is for setting Access Control Lists, but the syntax used is invalid. Even a correct ACL command would likely manage access for other users, not the default permissions for the owning user.
Reference:
Bash Reference Manual (Bash Builtins): The official documentation describes umask as a builtin command that sets the file creation mask.
While inspecting a recently compromised Linux system, the administrator identified a number of processes that should not have been running:
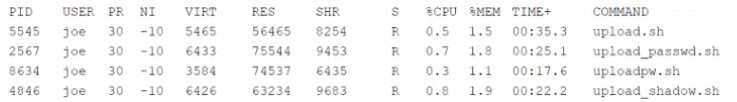
Which of the following commands should the administrator use to terminate all of the identified processes?
A.
pkill -9 -f "upload*.sh"
B.
kill -9 "upload*.sh"
C.
killall -9 -upload*.sh"
D.
skill -9 "upload*.sh"
pkill -9 -f "upload*.sh"
Summary:
The administrator has identified multiple malicious processes with names matching the pattern "upload*.sh" that need to be terminated immediately. The solution requires a command that can kill multiple processes at once based on a pattern match against their full command line, not just the process name. The -9 signal (SIGKILL) is used to force-terminate processes that are unresponsive.
Correct Option:
A. pkill -9 -f "upload*.sh":
This is the correct command. The pkill command is designed to signal processes based on their name and other attributes. The -f flag is crucial as it allows pkill to match against the full command line, not just the process name. Combined with the -9 signal for a forceful kill and the pattern "upload*.sh", this command will terminate all processes whose command line contains a string starting with "upload" and ending with ".sh".
Incorrect Options:
B. kill -9 "upload*.sh":
The kill command is used to send signals to processes, but it requires a Process ID (PID) or a job specification, not a name or pattern. It does not support wildcards for process names, so this command will fail with an error.
C. killall -9 -upload*.sh":
The killall command terminates processes by name, but it matches the base process name only. It would look for a process named exactly -upload*.sh, which is incorrect. Even with the correct syntax killall -9 upload.sh, it would only kill processes named upload.sh, not other scripts matching the upload*.sh pattern like upload1.sh or upload_backdoor.sh.
D. skill -9 "upload*.sh":
The skill command is an older utility for sending signals to processes. While it can sometimes accept a pattern, its behavior is less consistent and standardized than pkill. The pkill command is the more modern, reliable, and recommended tool for this specific task.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 4.3: "Given a scenario, analyze and troubleshoot application and hardware issues," which includes managing and troubleshooting processes. Knowing how to use tools like pkill and killall to terminate multiple processes efficiently is a key security and administration skill.
A Linux administrator is troubleshooting an issue in which an application service failed to start on a Linux server. The administrator runs a few commands and gets the following outputs:
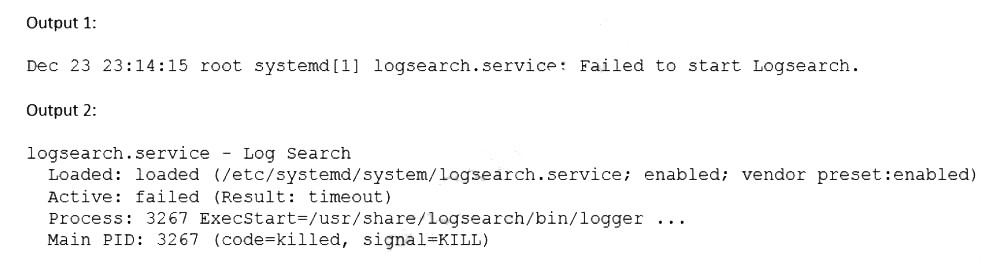
Based on the above outputs, which of the following is the MOST likely action the administrator should take to resolve this issue?
A.
Enable the logsearch.service and restart the service.
B.
Increase the TimeoutStartUSec configuration for the logsearch.sevice.
C.
Update the OnCalendar configuration to schedule the start of the logsearch.service.
D.
Update the KillSignal configuration for the logsearch.service to use TERM.
Increase the TimeoutStartUSec configuration for the logsearch.sevice.
Summary:
The systemctl status output reveals that the logsearch.service failed to start due to a timeout. The journalctl output confirms the service is active but has not yet begun its main operation ("started..."). Crucially, the systemctl show output reveals the service has a very short TimeoutStartUSec=1min 30s and has already been active for ActiveEnterTimestampMonotonic=2min 1s, meaning it has exceeded its startup timeout, causing systemd to kill it. The service needs more time to initialize.
Correct Option:
B. Increase the TimeoutStartUSec configuration for the logsearch.service:
This is the most direct and likely solution. The service is taking longer than the configured 90 seconds to start. The administrator should edit the service unit file (e.g., /etc/systemd/system/logsearch.service) and increase the TimeoutStartSec value (e.g., to 5min) to give the service adequate time to complete its startup routine before systemd intervenes.
Incorrect Options:
A. Enable the logsearch.service and restart the service:
The service is already enabled, as shown by the systemctl status output (Loaded: loaded...; enabled). Enabling it again is redundant and does not address the core timeout issue.
C. Update the OnCalendar configuration to schedule the start of the logsearch.service:
The OnCalendar setting is for timer units, not regular service units. There is no indication this service is triggered by a timer; it is failing when started manually or at boot.
D. Update the KillSignal configuration for the logsearch.service to use TERM:
The KillSignal dictates what signal systemd uses to stop the service. The problem is that the service is being killed because it failed to start within the allotted time, not that it's responding poorly to a stop signal.
Reference:
systemd Official Documentation (systemd.service): The official man page explains the TimeoutStartSec directive and other service timeouts.
An administrator attempts to rename a file on a server but receives the following error.
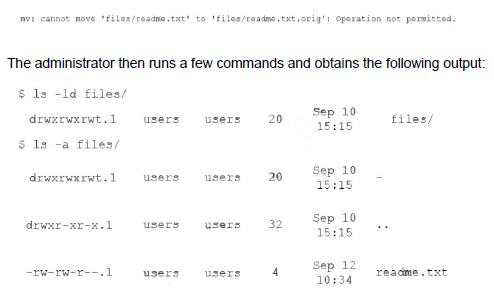
Which of the following commands should the administrator run NEXT to allow the file to be renamed by any user?
A.
chgrp reet files
B.
chacl -R 644 files
C.
chown users files
D.
chmod -t files
chmod -t files
Summary:
The administrator cannot rename a file despite having write permission to the directory. The ls -l output shows the directory has a t flag in the permissions (drwxrwxrwt), which is the sticky bit. In a directory, the sticky bit restricts file deletion and renaming so that only the file's owner, the directory's owner, or root can remove or rename files, even if other users have write access to the directory. This is the cause of the "Operation not permitted" error.
Correct Option:
D. chmod -t files:
This command removes the sticky bit from the files directory. The -t flag in chmod removes the sticky bit permission. Once this is done, any user with write access to the directory will be able to rename files within it, resolving the issue.
Incorrect Options:
A. chgrp reet files:
This command tries to change the group ownership of the directory to reet. The group is already reet, so this changes nothing. Furthermore, the problem is not group ownership but the special directory permission (sticky bit).
B. chacl -R 644 files:
This command is for managing Access Control Lists (ACLs), not standard permissions. The 644 mode is for files, not directories, and would remove execute permission, breaking the directory's functionality. It does not address the sticky bit.
C. chown users files:
This command changes the ownership of the directory to the user users. The current owner is root, and changing it is unnecessary and could have unintended consequences. The root cause is the sticky bit, not the ownership.
Reference:
Linux man-pages project (chmod): The official documentation explains the special permissions, including the sticky bit (t).
A newly created container has been unable to start properly, and a Linux administrator is analyzing the cause of the failure. Which of the following will allow the administrator to determine the FIRST command that is executed inside the container right after it starts?
A.
docker export
B.
docker info
C.
docker start
D.
docker inspect
docker inspect
Summary:
When a container fails to start, the administrator needs to inspect its configuration to diagnose the issue. The key is to find the initial command (the ENTRYPOINT or CMD) that the container is configured to run at startup. This information is stored in the container's metadata and configuration, not in its runtime state or filesystem.
Correct Option:
D. docker inspect
This is the correct command. docker inspect provides detailed, low-level information about a container's configuration in JSON format. Within this output, the administrator can find the Path and Args fields (or the combined Cmd), which show the exact command and arguments that are executed when the container starts. This allows the administrator to see the first command and identify if it is incorrect or missing.
Incorrect Options:
A. docker export
This command exports the container's filesystem as a tar archive. It is used to create a snapshot of the files, not to inspect the startup command or configuration.
B. docker info
The docker info command displays system-wide information about the Docker installation (like number of containers, storage driver, etc.), not detailed configuration for a specific container. It does not take a container ID as an argument.
C. docker start
This command is used to start a stopped container. If the container is already failing to start, running this command again will not provide any new diagnostic information about why it is failing; it will just reattempt the failed startup process.
Reference:
Docker Documentation (docker inspect): The official documentation states that docker inspect returns low-level information on Docker objects, which includes the container's configuration.
| Page 12 out of 40 Pages |
| Previous |