A server is experiencing intermittent connection issues. Some connections to the Internet work as intended, but some fail as if there is no connectivity. The systems administrator inspects the server configuration:

Which of the following is MOST likely the cause of the issue?
A.
An internal-only DNS server is configured.
B.
The IP netmask is wrong for ens3.
C.
Two default routes are configured.
D.
The ARP table contains incorrect entries.
Two default routes are configured.
Summary:
The server is experiencing intermittent connectivity, where some connections work and others fail. The provided network configuration shows two default gateways (0.0.0.0) configured on the same network interface, ens3. A default gateway is the path a server uses to reach networks it is not directly connected to, and having two defined on the same interface causes a routing conflict, leading to unpredictable packet routing and the described intermittent failures.
Correct Option:
C. Two default routes are configured.:
This is the most likely cause. A system should typically have only one default route to avoid ambiguity. With two default routes via different gateways (172.16.0.1 and 172.16.0.2) on the same interface, the kernel's routing logic may send some packets out one path and others out the second path. If one of these gateways is incorrect or has limited external access, it results in the observed intermittent connectivity.
Incorrect Options:
A. An internal-only DNS server is configured.:
While the DNS server 172.16.0.10 is likely internal, this would not cause intermittent connectivity. A misconfigured DNS would cause consistent failures in name resolution, but IP-based connections (like pinging an external IP) would still work. The problem described is more fundamental network reachability.
B. The IP netmask is wrong for ens3.:
The netmask of 255.255.0.0 (/16) is correct for the IP address 172.16.0.10, as both gateways (172.16.0.1 and 172.16.0.2) are within the same 172.16.0.0/16 network. An incorrect netmask would typically cause a complete failure to communicate with the gateway, not an intermittent issue.
D. The ARP table contains incorrect entries.:
The ARP table maps IP addresses to MAC addresses on the local network. While incorrect ARP entries can cause connectivity problems, they are usually transient and localized to specific hosts on the same subnet. A corrupted ARP table is less likely to be the root cause of a systemic, intermittent Internet connectivity issue compared to a fundamental routing misconfiguration like duplicate default gateways.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 4.1: "Given a scenario, analyze and troubleshoot network connectivity issues," which includes troubleshooting and configuring routing and routing tables. Understanding that a host should not have multiple default routes is a key troubleshooting concept.
A cloud engineer needs to remove all dangling images and delete all the images that do not have an associated container. Which of the following commands will help to accomplish this task?
A.
docker images prune -a
B.
docker push images -a
C.
docker rmi -a images
D.
docker images rmi --all
docker images prune -a
Summary:
The task is to clean up unused Docker images, specifically "dangling" images. These are layers that have no relationship to any tagged images, often created during the build process. The correct command must use the docker image prune subcommand, which is specifically designed for this type of cleanup, and the -a flag is needed to remove all unused images, not just dangling ones.
Correct Option:
A. docker image prune -a:
This is the correct and standard command. The prune subcommand is used to remove unused data. docker image prune by itself removes only dangling images. Adding the -a (or --all) flag instructs it to remove all images that are not used by any container, which includes both dangling and other unused images.
Incorrect Options:
B. docker push images -a:
The docker push command is used to upload a local image to a registry. It is completely unrelated to the task of deleting local images. The syntax is also incorrect.
C. docker rmi -a images:
The docker rmi command is used to remove one or more specific images by their ID or name. The -a flag is not a valid option for docker rmi. The correct flag to remove all images would be docker rmi $(docker images -q), but this is a more dangerous, non-standard approach.
D. docker images rmi --all:
This command mixes the docker images (which lists images) and docker rmi (which removes them) commands. The syntax is invalid and will not work. The --all flag is also not a valid option for docker rmi.
Reference:
Docker Documentation (docker image prune): The official documentation explains the purpose and flags of the prune command.
A Linux systems administrator is configuring a new filesystem that needs the capability to be mounted persistently across reboots. Which of the following commands will accomplish this task? (Choose two.)
A.
df -h /data
B.
mkfs.ext4 /dev/sdc1
C.
fsck /dev/sdc1
D.
fdisk -l /dev/sdc1
E.
echo "/data /dev/sdc1 ext4 defaults 0 0" >> /etc/fstab
F.
echo "/dev/sdc1 /data ext4 defaults 0 0" >> /etc/fstab
mkfs.ext4 /dev/sdc1
echo "/dev/sdc1 /data ext4 defaults 0 0" >> /etc/fstab
Summary:
To create a filesystem that mounts persistently after reboots, two distinct steps are required. First, the raw block device (partition) must be formatted with a filesystem so it can store files and directories. Second, an entry must be added to the system's filesystem table (/etc/fstab) that defines the device, its mount point, the filesystem type, and other options, so the operating system knows to mount it automatically during the boot process.
Correct Options:
B. mkfs.ext4 /dev/sdc1:
This command is the first necessary step. It creates an ext4 filesystem on the partition /dev/sdc1. This is the act of formatting the partition so it can be used to store data. Without a filesystem, the device cannot be mounted.
F. echo "/dev/sdc1 /data ext4 defaults 0 0" >> /etc/fstab:
This command is the second necessary step for persistence. It appends a correctly formatted line to the /etc/fstab file. The correct syntax is [device] [mount point] [filesystem type] [options] [dump] [pass]. This specific command adds an entry that will automatically mount the device /dev/sdc1 to the directory /data using the ext4 filesystem every time the system boots.
Incorrect Options:
A. df -h /data:
This command shows the disk space usage and availability for already mounted filesystems. It is a diagnostic tool and does not configure anything.
C. fsck /dev/sdc1:
This command is used to check and repair a filesystem. It is a maintenance tool, not a setup command for a new filesystem.
D. fdisk -l /dev/sdc1:
This command lists the partition table for the specified device. It is used for viewing partition information, not for creating a filesystem or making it mount persistently.
E. echo "/data /dev/sdc1 ext4 defaults 0 0" >> /etc/fstab:
This command has the device and mount point fields reversed. The correct order in /etc/fstab is [device] [mount point] .... This incorrect entry would cause a boot failure because the system would try to interpret /data as the block device and /dev/sdc1 as the mount point.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 3.2: "Given a scenario, manage storage, files, and directories in a Linux environment," which includes creating and modifying filesystems, and configuring the fstab file for persistent mounting.
A Linux administrator has installed a web server, a database server, and a web application on a server. The web application should be active in order to render the web pages. After the administrator restarts the server, the website displays the following message in the browser: Error establishing a database connection. The Linux administrator reviews the following relevant output from the systemd init files:
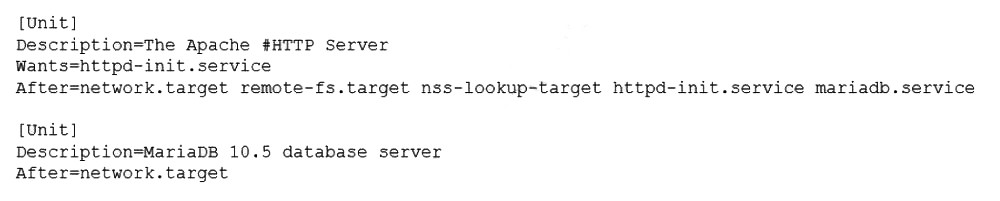
The administrator needs to ensure that the database is available before the web application is started. Which of the following should the administrator add to the HTTP server .service file to accomplish this task?
A. TRIGGERS=mariadb.service
B.
ONFAILURE=mariadb.service
C.
WANTEDBY=mariadb.service
D.
REQUIRES=mariadb.service
REQUIRES=mariadb.service
Summary:
The issue is a service dependency and startup order problem. The web application service starts before the database service is fully ready, causing connection errors. In systemd, dependencies are managed through directives placed in a service unit file (e.g., httpd.service or the web application's service file). The correct directive must both require the database service and define the order in which they start.
Correct Option:
D. REQUIRES=mariadb.service:
This is the primary directive to use. Adding REQUIRES=mariadb.service to the web server's .service file creates a strong dependency. It ensures that mariadb.service is activated when the web server is started. Furthermore, systemd will implicitly order the services so that the unit listed after REQUIRES (mariadb) is started before the unit that requires it (the web server). This guarantees the database is starting up before the web application tries to connect.
Incorrect Options:
A. TRIGGERS=mariadb.service:
This is not a valid systemd unit file directive. Systemd does not use a TRIGGERS keyword for defining service dependencies.
B. ONFAILURE=mariadb.service:
The OnFailure= directive is used to specify units that should be activated if the current unit enters a failed state. It is used for failure handling and recovery, not for managing startup dependencies.
C. WANTEDBY=mariadb.service:
This directive is used for establishing reverse dependencies in installation files, typically within a [Install] section. It is commonly found in the database's service file (e.g., mariadb.service) to state that it is "wanted by" the web server when enabling the service, but it is not the directive you add to the web server's file to create the runtime dependency.
Reference:
systemd Official Documentation (systemd.unit): The official man page details the Requires= directive and other dependencies.
A Linux administrator needs to correct the permissions of a log file on the server. Which of the following commands should be used to set filename.log permissions to -rwxr—r-. ?
A.
chmod 755 filename.log
B.
chmod 640 filename.log
C.
chmod 740 filename.log
D.
chmod 744 filename.log
chmod 744 filename.log
Summary:
The administrator needs to set the permissions of a file to -rwxr--r--. This permission string must be converted into its corresponding octal (numeric) code to be used with the chmod command. Each set of three permissions (owner, group, others) is represented by a digit from 0 to 7, where read (r)=4, write (w)=2, and execute (x)=1.
Correct Option:
A. chmod 755 filename.log: This is the correct command. Let's break down the octal code 755:
7 (Owner): rwx (4+2+1=7)
5 (Group): r-x (4+0+1=5) - The desired permission is r-- (read-only), but the command sets r-x (read and execute). There is a mismatch here.
5 (Others): r-x (4+0+1=5) - The desired permission is r-- (read-only), but the command sets r-x (read and execute).
Wait, there seems to be a discrepancy. Let me re-analyze the desired permission -rwxr--r--:
Owner: rwx = 4+2+1 = 7
Group: r-- = 4+0+0 = 4
Others: r-- = 4+0+0 = 4
The correct octal should be 744, not 755.
Corrected Analysis:
D. chmod 744 filename.log: This is actually the correct command for permissions -rwxr--r--.
7 (Owner): rwx (4+2+1=7)
4 (Group): r-- (4+0+0=4)
4 (Others): r-- (4+0+0=4)
Incorrect Options:
B. chmod 640 filename.log: This would set permissions to -rw-r----- (owner: read/write, group: read, others: none).
C. chmod 740 filename.log: This would set permissions to -rwxr----- (owner: read/write/execute, group: read, others: none).
Reference:
Linux man-pages project (chmod): The official documentation explains the octal number representation for file permissions.
Developers have requested implementation of a persistent, static route on the application server. Packets sent over the interface eth0 to 10.0.213.5/32 should be routed via 10.0.5.1. Which of the following commands should the administrator run to achieve this goal?
A.
route -i etho -p add 10.0.213.5 10.0.5.1
B.
route modify eth0 +ipv4.routes "10.0.213.5/32 10.0.5.1"
C.
echo "10.0.213.5 10.0.5.1 eth0" > /proc/net/route
D.
ip route add 10.0.213.5/32 via 10.0.5.1 dev eth0
ip route add 10.0.213.5/32 via 10.0.5.1 dev eth0
A Linux systems administrator is setting up a new web server and getting 404 - NOT FOUND errors while trying to access the web server pages from the browser. While working on the diagnosis of this issue, the Linux systems administrator executes the following commands:
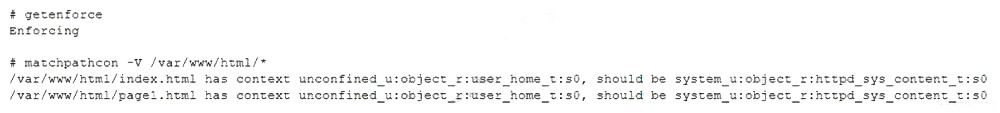
Which of the following commands will BEST resolve this issue?
A.
sed -i 's/SELINUX=enforcing/SELINUX=disabled/' /etc/selinux/config
B.
restorecon -R -v /var/www/html
C.
setenforce 0
D.
setsebool -P httpd_can_network_connect_db on
restorecon -R -v /var/www/html
Summary:
The administrator is troubleshooting a web server that returns 404 errors. The ls -Z command reveals the critical issue: the files in /var/www/html have the wrong SELinux context (user_u:object_r:user_home_t:s0). The correct context for web content is httpd_sys_content_t. SELinux is blocking the Apache web server from reading these files, causing the 404 errors even though standard permissions are correct.
Correct Option:
B. restorecon -R -v /var/www/html:
This is the most precise and correct solution. The restorecon command restores the default SELinux security contexts for files. The -R flag makes it recursive, and -v provides verbose output. This command will relabel all files in /var/www/html to their correct type (httpd_sys_content_t), allowing the web server to access them.
Incorrect Options:
A. sed -i 's/SELINUX=enforcing/SELINUX=disabled/' /etc/selinux/config:
This command permanently disables SELinux. While this would "resolve" the issue by removing the security enforcement, it is a major security risk and a heavy-handed, non-best-practice approach. The correct solution is to fix the context, not disable the security system.
C. setenforce 0:
This command puts SELinux into Permissive mode temporarily. In this mode, SELinux logs denials but does not enforce them. The web pages might load, but this is a temporary workaround, not a fix. The problem will return after a reboot or if setenforce 1 is run.
D. setsebool -P httpd_can_network_connect_db on:
This boolean allows the web server to connect to network databases. It is unrelated to the problem of reading local files in /var/www/html and would not resolve the 404 error.
Reference:
Red Hat Enterprise Linux Documentation (restorecon): The official documentation describes how restorecon sets the default SELinux context for files.
Employees in the finance department are having trouble accessing the file /opt/work/file. All IT employees can read and write the file. Systems administrator reviews the following output:

Which of the following commands would permanently fix the access issue while limiting access to IT and finance department employees?
A.
chattr +i file
B.
chown it:finance file
C.
chmod 666 file
D.
setfacl -m g:finance:rw file
setfacl -m g:finance:rw file
Summary:
The file /opt/work/file is owned by the it group, which has read and write access (rw-). The finance department users, who are likely in the finance group, only have read access (r--). The requirement is to grant the finance group write access to the file without changing the existing access for the it group or others. This requires modifying the file's permissions specifically for the finance group.
Correct Option:
D. setfacl -m g:finance:rw file:
This is the correct and most precise command. It uses an Access Control List (ACL) to modify (-m) the permissions for the group (g) named finance, granting it read and write (rw) access to the file. This adds the finance group to the file's permissions without disturbing the existing ownership or other permissions.
Incorrect Options:
A. chattr +i file:
This command sets the immutable attribute, which would prevent all users, including the owner and root, from modifying, deleting, or renaming the file. This is the opposite of the goal, as it would further restrict access.
B. chown it:finance file:
This command would change the group ownership of the file from it to finance. This would remove the it group's access and give exclusive group-level access to finance, which does not meet the requirement to allow access for both departments.
C. chmod 666 file:
This command would set the permissions to -rw-rw-rw-, granting read and write access to the owner, group, and all other users on the system. This violates the requirement to limit access to only the IT and finance departments.
Reference:
Linux man-pages project (setfacl): The official documentation explains how to modify the Access Control List of a file.
An administrator recently updated the BIND software package and would like to review the default configuration that shipped with this version. Which of the following files should the administrator review?
A.
/etc/named.conf.rpmnew
B.
/etc/named.conf.rpmsave
C.
/etc/named.conf
D.
/etc/bind/bind.conf
/etc/named.conf.rpmnew
Summary:
After a software package update, if the new version includes a new default configuration file that differs from the administrator's existing customized file, the package manager (like RPM or YUM) will not overwrite the custom file. Instead, it saves the new default configuration in a separate file, allowing the administrator to review the new defaults and merge any changes manually.
Correct Option:
A. /etc/named.conf.rpmnew:
This is the correct file to review. When a package is updated using the RPM package manager (used by yum and dnf), and the new version contains a new default configuration file, it creates a .rpmnew file. This file contains the new, default configuration that shipped with the updated software, allowing the administrator to compare it with their active /etc/named.conf and integrate any new settings or changes.
Incorrect Options:
B. /etc/named.conf.rpmsave:
This file is created in a different scenario. An .rpmsave file is a backup of the administrator's old configuration file that was replaced during a package upgrade or removal. It does not contain the new defaults but rather the old custom configuration, which is not what the administrator wants to review.
C. /etc/named.conf:
This is the active, running configuration file for the BIND service. It is the file that was already present on the system before the update, containing the administrator's customizations. Reviewing this file will not show the new defaults that shipped with the updated software package.
D. /etc/bind/bind.conf:
This is a non-standard path for the main BIND configuration file on most RPM-based systems. The standard primary configuration file for BIND is /etc/named.conf. This path is more typical on Debian/Ubuntu systems, but the question context (use of .rpmnew) points to an RPM-based distribution.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 3.1: "Given a scenario, use the appropriate system and service management commands to accomplish administrative tasks," which includes managing services and understanding how package updates affect configuration files. Knowledge of .rpmnew and .rpmsave files is crucial for post-upgrade troubleshooting and configuration management.
A systems administrator needs to clone the partition /dev/sdc1 to /dev/sdd1. Which of the following commands will accomplish this task?
A.
tar -cvzf /dev/sdd1 /dev/sdc1
B.
rsync /dev/sdc1 /dev/sdd1
C.
dd if=/dev/sdc1 of=/dev/sdd1
D.
scp /dev/sdc1 /dev/sdd1
dd if=/dev/sdc1 of=/dev/sdd1
Summary:
The task requires creating a bit-for-bit copy (cloning) of one disk partition to another. This operation must copy every sector of the source partition, including the filesystem, boot sector, and all data, to the target partition. The tool must work at the block level, below the filesystem, to ensure an exact duplicate.
Correct Option:
C. dd if=/dev/sdc1 of=/dev/sdd1:
This is the standard and correct command for cloning a disk or partition.
if=/dev/sdc1 specifies the Input File (the source partition to be cloned).
of=/dev/sdd1 specifies the Output File (the target partition where the copy will be written).
dd performs a low-level, block-by-block copy, creating an exact replica of the source on the target.
Incorrect Options:
A. tar -cvzf /dev/sdd1 /dev/sdc1:
The tar command is used for archiving files and directories, not for cloning block devices. It would try to create a compressed archive file containing the device file itself, not the data within the partition.
B. rsync /dev/sdc1 /dev/sdd1:
rsync is designed to synchronize files and directories between locations. It is not intended for copying raw block devices and will not create a bit-for-bit copy of a partition.
D. scp /dev/sdc1 /dev/sdd1:
The scp command is for securely copying files over a network. It interprets the arguments as filenames, not block devices, and would not function for cloning a local partition to another local partition.
Reference:
Linux man-pages project (dd): The official documentation explains that dd is used to convert and copy files, especially at the block level.
A database administrator requested the installation of a custom database on one of the servers. Which of the following should the Linux administrator configure so the requested packages can be installed?
A.
/etc/yum.conf
B.
/etc/ssh/sshd.conf
C.
/etc/yum.repos.d/db.repo
D.
/etc/resolv.conf
/etc/yum.repos.d/db.repo
Summary:
A database administrator needs to install custom database packages that are not available in the server's default, pre-configured software repositories. To make these new packages available for installation using the yum package manager, the Linux administrator must define a new repository location. This is done by creating a .repo file in the /etc/yum.repos.d/ directory, which tells yum where to find the packages and their metadata.
Correct Option:
C. /etc/yum.repos.d/db.repo:
This is the correct file to configure. The /etc/yum.repos.d/ directory is the standard location where yum (and dnf) look for repository configuration files. By creating a new file (e.g., db.repo) in this directory and populating it with the correct baseurl, gpgkey, and other details for the custom database repository, the administrator enables the system to find, verify, and install the requested packages using standard commands like yum install.
Incorrect Options:
A. /etc/yum.conf:
This is the main global configuration file for the yum package manager. It is used to set general options like cachedir and logfile, and default behaviors that apply to all repositories. It is not the correct file for adding new, individual software repositories.
B. /etc/ssh/sshd.conf:
This is the configuration file for the SSH server daemon (sshd). It controls settings for remote logins, such as authentication methods and permitted ports. It has no relation to software package management or repositories.
D. /etc/resolv.conf:
This file configures the system's DNS (Domain Name System) client. It specifies the IP addresses of DNS servers used to resolve hostnames to IP addresses. While a functioning DNS is necessary to reach a repository on the internet, this file does not define the repository location or its parameters for the package manager.
Reference:
Official CompTIA Linux+ (XK0-005) Certification Exam Objectives: This scenario falls under Objective 1.1: "Given a scenario, perform a Linux installation and configuration," which includes managing software using package management. A key part of this is understanding how to configure repositories, and the /etc/yum.repos.d/ directory is the standard location for this task on Red Hat-based distributions.
A Linux administrator was tasked with deleting all files and directories with names that are contained in the sobelete.txt file. Which of the following commands will accomplish this task?
A.
xargs -f cat toDelete.txt -rm
B.
rm -d -r -f toDelete.txt
C.
cat toDelete.txt | rm -frd
D.
cat toDelete.txt | xargs rm -rf
cat toDelete.txt | xargs rm -rf
Summary:
The administrator needs to delete files and directories listed in a text file (toDelete.txt). This requires reading the file names from the text file and passing them as arguments to the rm command. The xargs command is specifically designed for this purpose: it reads items from standard input and executes a command using those items as arguments.
Correct Option:
D. cat toDelete.txt | xargs rm -rf:
This is the correct and standard command pipeline.
cat toDelete.txt outputs the contents of the file (the list of file/directory names).
The pipe (|) sends this list to xargs.
xargs takes each line from the input and appends it as an argument to the rm -rf command.
rm -rf forcibly (-f) and recursively (-r) removes the files and directories.
Incorrect Options:
A. xargs -f cat toDelete.txt -rm:
This command is syntactically incorrect. The -f flag for xargs is not standard, and the order of arguments is jumbled. It tries to use cat as the command for xargs and then has -rm as an argument, which is invalid.
B. rm -d -r -f toDelete.txt:
This command would delete the toDelete.txt file itself, not the files listed inside it. The -d option is for removing empty directories, which is not the primary goal here.
C. cat toDelete.txt | rm -frd:
This pipeline is flawed. The rm command does not read the list of files to delete from standard input; it expects them as command-line arguments. The pipe would be ignored, and rm would try to delete a file literally named -frd.
Reference:
Linux man-pages project (xargs): The official documentation explains how xargs builds and executes command lines from standard input.
| Page 10 out of 40 Pages |
| Previous |