Topic 3: Exam Pool C
A user enters a password to log in to a workstation and is then prompted to enter an authentication code. Which of the following MFA factors or attributes are being utilized in the authentication process? (Select TWO).
A.
Something you know
B.
Something you have
C.
Somewhere you are
D.
Someone you are
E.
Something you are
F.
Something you can do
Something you know
Something you have
Which of the following is MOST likely to contain ranked and ordered information on the
likelihood and potential impact of catastrophic events that may affect business processes
and systems, while also highlighting the residual risks that need to be managed after
mitigating controls have been implemented?
A.
An RTO report
B.
A risk register
C.
business impact analysis
D.
An asset value register
E.
A disaster recovery plan
A risk register
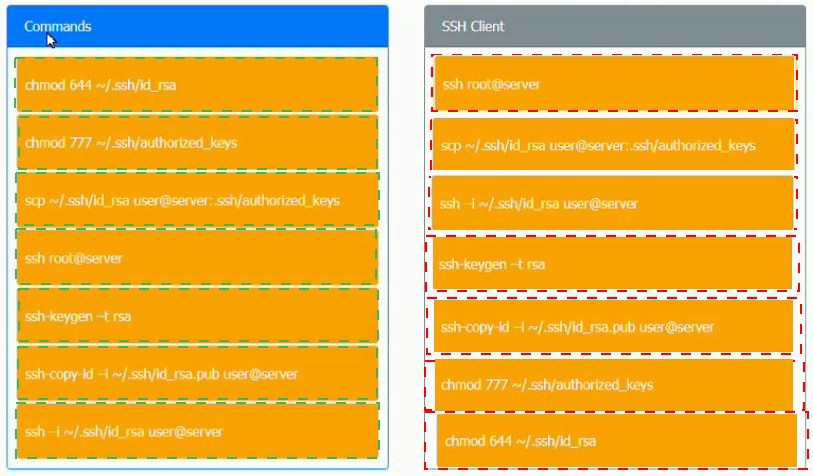
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the
Reset All button.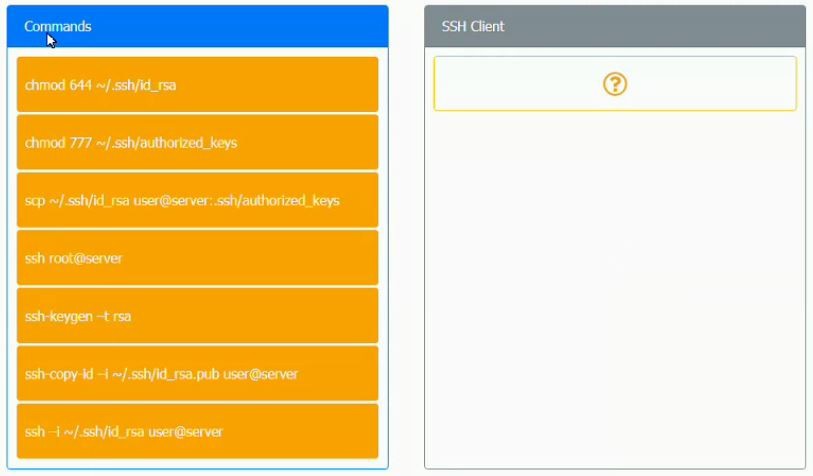
Joe, an employee, receives an email stating he won the lottery. The email includes a link that requests a name, mobile phone number, address, and date of birth be provided to confirm Joe’s identity before sending him the prize. Which of the following BEST describes this type of email?
A.
Spear phishing
B.
Whaling
C.
Phishing
D.
Vishing
Phishing
A security analyst is performing a forensic investigation compromised account credentials. Using the Event Viewer, the analyst able to detect the following message, ‘’Special privileges assigned to new login.’’ Several of these messages did not have a valid logon associated with the user before these privileges were assigned. Which of the following attacks is MOST likely being detected?
A.
Pass-the-hash
B.
Buffer overflow
C.
Cross-site scripting
D.
Session replay
Pass-the-hash
A cybersecurity department purchased o new PAM solution. The team is planning to randomize the service account credentials of the Windows server first. Which of the following would be the BEST method to increase the security on the Linux server?
A.
Randomize the shared credentials
B.
Use only guest accounts to connect.
C.
Use SSH keys and remove generic passwords
D.
Remove all user accounts.
Use SSH keys and remove generic passwords
An organization is developing an authentication service for use at the entry and exit ports of country borders. The service will use data feeds obtained from passport systems, passenger manifests, and high-definition video feeds from CCTV systems that are located at the ports. The service will incorporate machine-learning techniques to eliminate biometric enrollment processes while still allowing authorities to identify passengers with increasing accuracy over time. The more frequently passengers travel, the more accurately the service will identify them. Which of the following biometrics will MOST likely be used,
without the need for enrollment? (Choose two.)
A.
Voice
B.
Gait
C.
Vein
D.
Facial
E.
Retina
F.
Fingerprint
Gait
Facial
A security engineer needs to enhance MFA access to sensitive areas in a building. A key
card and fingerprint scan are already in use. Which of the following would add another
factor of authentication?
A.
Hard token
B.
Retina scan
C.
SMS text
D.
Keypad PIN
Retina scan
An organization has decided to host its web application and database in the cloud Which of
the following BEST describes the security concerns for this decision?
A.
Access to the organization's servers could be exposed to other cloud-provider clients
B.
The cloud vendor is a new attack vector within the supply chain
C.
Outsourcing the code development adds risk to the cloud provider
D.
Vendor support will cease when the hosting platforms reach EOL.
The cloud vendor is a new attack vector within the supply chain
A cybersecurity administrator needs to add disk redundancy for a critical server. The solution must have a two- drive failure for better fault tolerance. Which of the following RAID levels should the administrator select?
A.
0
B.
1
C.
5
D.
6
1
Which of the following algorithms has the SMALLEST key size?
A.
DES
B.
Twofish
C.
RSA
D.
AES
Twofish
Users have been issued smart cards that provide physical access to a building. The cards also contain tokens that can be used to access information systems. Users can log m to any thin client located throughout the building and see the same desktop each time. Which of the following technologies are being utilized to provide these capabilities? (Select TWO)
A.
COPE
B.
VDI
C.
GPS
D.
TOTP
E.
RFID
F.
BYOD
VDI
RFID
| Page 6 out of 74 Pages |
| Previous |