Topic 3: Exam Pool C
A security analyst is investigation an incident that was first reported as an issue connecting
to network shares and the internet, While reviewing logs and tool output, the analyst sees
the following: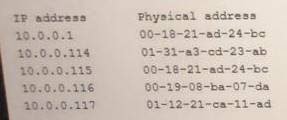
Which of the following attacks has occurred?
A.
IP conflict
B.
Pass-the-hash
C.
MAC flooding
D.
Directory traversal
E.
ARP poisoning
ARP poisoning
Which of the following organizational policies are MOST likely to detect fraud that is being conducted by existing employees? (Select TWO).
A.
Offboarding
B.
Mandatory vacation
C.
Job rotation
D.
Background checks
E.
Separation of duties
F.
Acceptable use
Mandatory vacation
Job rotation
A company was recently breached Part of the company's new cybersecurity strategy is to
centralize the logs from all security devices Which of the following components forwards
the logs to a central source?
A.
Log enrichment
B.
Log aggregation
C.
Log parser
D.
Log collector
Log collector
A cloud administrator is configuring five compute instances under the same subnet in a
VPC Three instances are required to communicate with one another, and the other two
must he logically isolated from all other instances in the VPC. Which of the following must
the administrator configure to meet this requirement?
A.
One security group
B.
Two security groups
C.
Three security groups
D.
Five security groups
Two security groups
Phishing and spear-phishing attacks have been occurring more frequently against a company’s staff. Which of the following would MOST likely help mitigate this issue?
A.
DNSEC and DMARC
B.
DNS query logging
C.
Exact mail exchanger records in the DNS
D.
The addition of DNS conditional forwarders
Exact mail exchanger records in the DNS
A small company that does not have security staff wants to improve its security posture. Which of the following would BEST assist the company?
A.
MSSP
B.
SOAR
C.
IaaS
D.
PaaS
SOAR
A security analyst is investigating an incident to determine what an attacker was able to do
on a compromised laptop. The analyst reviews the following SIEM log: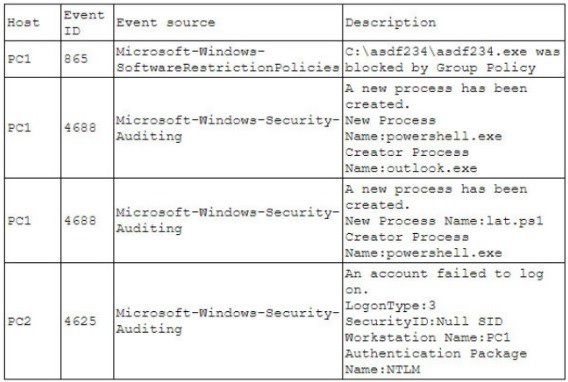
Which of the following describes the method that was used to compromise the laptop?
A.
An attacker was able to move laterally from PC1 to PC2 using a pass-the-hash attack
B.
An attacker was able to bypass application whitelisting by emailing a spreadsheet
attachment with an embedded PowerShell in the file
C.
An attacker was able to install malware to the CAasdf234 folder and use it to gam administrator nights and launch Outlook
D.
An attacker was able to phish user credentials successfully from an Outlook user profile
An attacker was able to move laterally from PC1 to PC2 using a pass-the-hash attack
A security analyst has received an alert about being sent via email. The analyst’s Chief information Security Officer (CISO) has made it clear that PII must be handle with extreme care From which of the following did the alert MOST likely originate?
A.
S/MIME
B.
DLP
C.
IMAP
D.
HIDS
DLP
Explanation: Network-based DLP monitors outgoing data looking for sensitive data. Network-based DLP systems monitor outgoing email to detect and block unauthorized data transfers and monitor data stored in the cloud.
A pharmaceutical sales representative logs on to a laptop and connects to the public WiFi to check emails and update reports. Which of the following would be BEST to prevent other devices on the network from directly accessing the laptop? (Choose two.)
A.
Trusted Platform Module
B.
Ahost-based firewall
C.
A DLP solution
D.
Full disk encryption
E.
A VPN
F.
Antivirus software
Trusted Platform Module
Ahost-based firewall
Which of the following technical controls is BEST suited for the detection and prevention of buffer overflows on hosts?
A.
DLP
B.
HIDS
C.
EDR
D.
NIPS
EDR
A cybersecurity analyst reviews the log files from a web server and sees a series of files that indicates a directory-traversal attack has occurred. Which of the following is the analyst http://selfexamtraining.com/uploadimages/SY0-601-Q-39.jpgMOST likely seeing?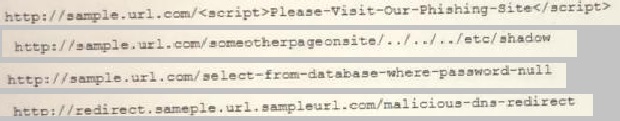
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option B
A global pandemic is forcing a private organization to close some business units and reduce staffing at others. Which of the following would be BEST to help the organization’s executives determine the next course of action?
A.
An incident response plan
B.
A communications plan
C.
A disaster recovery plan
D.
A business continuity plan
A business continuity plan
| Page 3 out of 74 Pages |
| Previous |