Topic 3: Exam Pool C
During a routine scan of a wireless segment at a retail company, a security administrator
discovers several devices are connected to the network that do not match the company's
naming convention and are not in the asset Inventory. WiFi access Is protected with 255-
Wt encryption via WPA2. Physical access to the company's facility requires two-factor
authentication using a badge and a passcode Which of the following should the
administrator implement to find and remediate the Issue? (Select TWO).
A.
Check the SIEM for failed logins to the LDAP directory.
B.
Enable MAC filtering on the switches that support the wireless network.
C.
Run a vulnerability scan on all the devices in the wireless network
D.
Deploy multifactor authentication for access to the wireless network
E.
Scan the wireless network for rogue access points.
F.
Deploy a honeypot on the network
Enable MAC filtering on the switches that support the wireless network.
Scan the wireless network for rogue access points.
Explanation: security is pretty good already up to a point, clearly Rogue AP bypass is in the picture MAC filtering on the switch the AP's hang from will ensure the only AP's allowed to touch the core network are approved known AP's and ze "bad guys" will find themselves trapped on an AP island with nowhere to go!
A company has drafted an insider-threat policy that prohibits the use of external storage devices. Which of the following would BEST protect the company from data exfiltration via removable media?
A.
Monitoring large data transfer transactions in the firewall logs
B.
Developing mandatory training to educate employees about the removable media policy
C.
Implementing a group policy to block user access to system files
D.
Blocking removable-media devices and write capabilities using a host-based security tool
Blocking removable-media devices and write capabilities using a host-based security tool
A security administrator checks the table of a network switch, which shows the following output: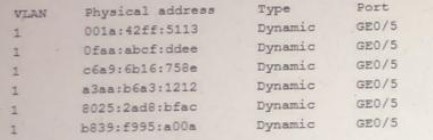
Which of the following is happening to this switch?
A.
MAC Flooding
B.
DNS poisoning
C.
MAC cloning
D.
ARP poisoning
MAC Flooding
Local guidelines require that all information systems meet a minimum-security baseline to
be compliant. Which of the following can security administrators use to assess their system
configurations against the baseline?
A.
SOAR playbook
B.
Security control matrix
C.
Risk management framework
D.
Benchmarks
Benchmarks
A nuclear plant was the victim of a recent attack, and all the networks were air gapped. A
subsequent investigation revealed a worm as the source of the issue. Which of the
following BEST explains what happened?
A.
A malicious USB was introduced by an unsuspecting employee.
B.
The ICS firmware was outdated
C.
A local machine has a RAT installed.
D.
The HVAC was connected to the maintenance vendor
A malicious USB was introduced by an unsuspecting employee.
An organization's Chief Security Officer (CSO) wants to validate the business's involvement
in the incident response plan to ensure its validity and thoroughness. Which of the following
will the CSO MOST likely use?
A.
An external security assessment
B.
A bug bounty program
C.
A tabletop exercise
D.
A red-team engagement
A tabletop exercise
Which of the following ISO standards is certified for privacy?
A.
ISO 9001
B.
ISO 27002
C.
ISO 27701
D.
ISO 31000
ISO 27701
Explanation: ISO 27701 also abbreviated as PIMS (Privacy Information Management
System) outlines a framework for Personally Identifiable Information (PII) Controllers and
PII Processors to manage data privacy. Privacy information management systems are
sometimes referred to as personal information management systems.
https://pecb.com/whitepaper/the-future-of-privacy-with-isoiec-27701
The IT department at a university is concerned about professors placing servers on the university network in an attempt to bypass security controls. Which of the following BEST represents this type of threat?
A.
A script kiddie
B.
Shadow IT
C.
Hacktivism
D.
White-hat
Shadow IT
On which of the following is the live acquisition of data for forensic analysis MOST
dependent? (Choose two.)
A.
Data accessibility
B.
Legal hold
C.
Cryptographic or hash algorithm
D.
Data retention legislation
E.
Value and volatility of data
F.
Right-to-audit clauses
Value and volatility of data
Right-to-audit clauses
A symmetric encryption algorithm Is BEST suited for:
A.
key-exchange scalability.
B.
protecting large amounts of data.
C.
providing hashing capabilities,
D.
implementing non-repudiation.
implementing non-repudiation.
A retail executive recently accepted a job with a major competitor. The following week, a security analyst reviews the security logs and identifies successful logon attempts to access the departed executive's accounts. Which of the following security practices would have addressed the issue?
A.
A non-disclosure agreement
B.
Least privilege
C.
An acceptable use policy
D.
Ofboarding
Ofboarding
A company recently transitioned to a strictly BYOD culture due to the cost of replacing lost or damaged corporate-owned mobile devices. Which of the following technologies would be BEST to balance the BYOD culture while also protecting the company’s data?
A.
Containerization
B.
Geofencing
C.
Full-disk encryption
D.
Remote wipe
Full-disk encryption
| Page 14 out of 74 Pages |
| Previous |