Topic 3: Exam Pool C
A critical file server is being upgraded and the systems administrator must determine which
RAID level the new server will need to achieve parity and handle two simultaneous disk
failures. Which of the following RAID levels meets this requirements?
A.
RAID 0+1
B.
RAID 2
C.
RAID 5
D.
RAID 6
RAID 5
Under GDPR, which of the following is MOST responsible for the protection of privacy and
website user rights?
A.
The data protection officer
B.
The data processor
C.
The data owner
D.
The data controller
The data owner
A network technician is installing a guest wireless network at a coffee shop. When a
customer purchases an Item, the password for the wireless network is printed on the recent
so the customer can log in. Which of the following will the technician MOST likely configure
to provide the highest level of security with the least amount of overhead?
A.
WPA-EAP
B.
WEP-TKIP
C.
WPA-PSK
D.
WPS-PIN
WPA-EAP
An analyst needs to set up a method for securely transferring files between systems. One
of the requirements is to authenticate the IP header and the payload. Which of the following
services would BEST meet the criteria?
A.
TLS
B.
PFS
C.
ESP
D.
AH
TLS
A smart switch has the ability to monitor electrical levels and shut off power to a building in the event of power surge or other fault situation. The switch was installed on a wired network in a hospital and is monitored by the facilities department via a cloud application. The security administrator isolated the switch on a separate VLAN and set up a patch routine. Which of the following steps should also be taken to harden the smart switch?
A.
Set up an air gap for the switch.
B.
Change the default password for the switch.
C.
Place the switch In a Faraday cage.
D.
Install a cable lock on the switch
Change the default password for the switch.
A company has limited storage available and online presence that cannot for more than four hours. Which of the following backup methodologies should the company implement to allow for the FASTEST database restore time In the event of a failure, which being maindful of the limited available storage space?
A.
Implement fulltape backup every Sunday at 8:00 p.m and perform nightly tape rotations.
B.
Implement different backups every Sunday at 8:00 and nightly incremental backups at 8:00 p.m
C.
Implement nightly full backups every Sunday at 8:00 p.m
D.
Implement full backups every Sunday at 8:00 p.m and nightly differential backups at 8:00
Implement different backups every Sunday at 8:00 and nightly incremental backups at 8:00 p.m
Which of the following job roles would sponsor data quality and data entry initiatives that
ensure business and regulatory requirements are met?
A.
The data owner
B.
The data processor
C.
The data steward
D.
The data privacy officer.
The data steward
An information security incident recently occurred at an organization, and the organization
was required to report the incident to authorities and notify the affected parties. When the
organization's customers became of aware of the incident, some reduced their orders or
stopped placing orders entirely. Which of the following is the organization experiencing?
A.
Reputation damage
B.
Identity theft
C.
Anonymlzation
D.
Interrupted supply chain
Reputation damage
A network administrator has been asked to install an IDS to improve the security posture of an organization. Which of the following control types is an IDS?
A.
Corrective
B.
Physical
C.
Detective
D.
Administrative
Detective
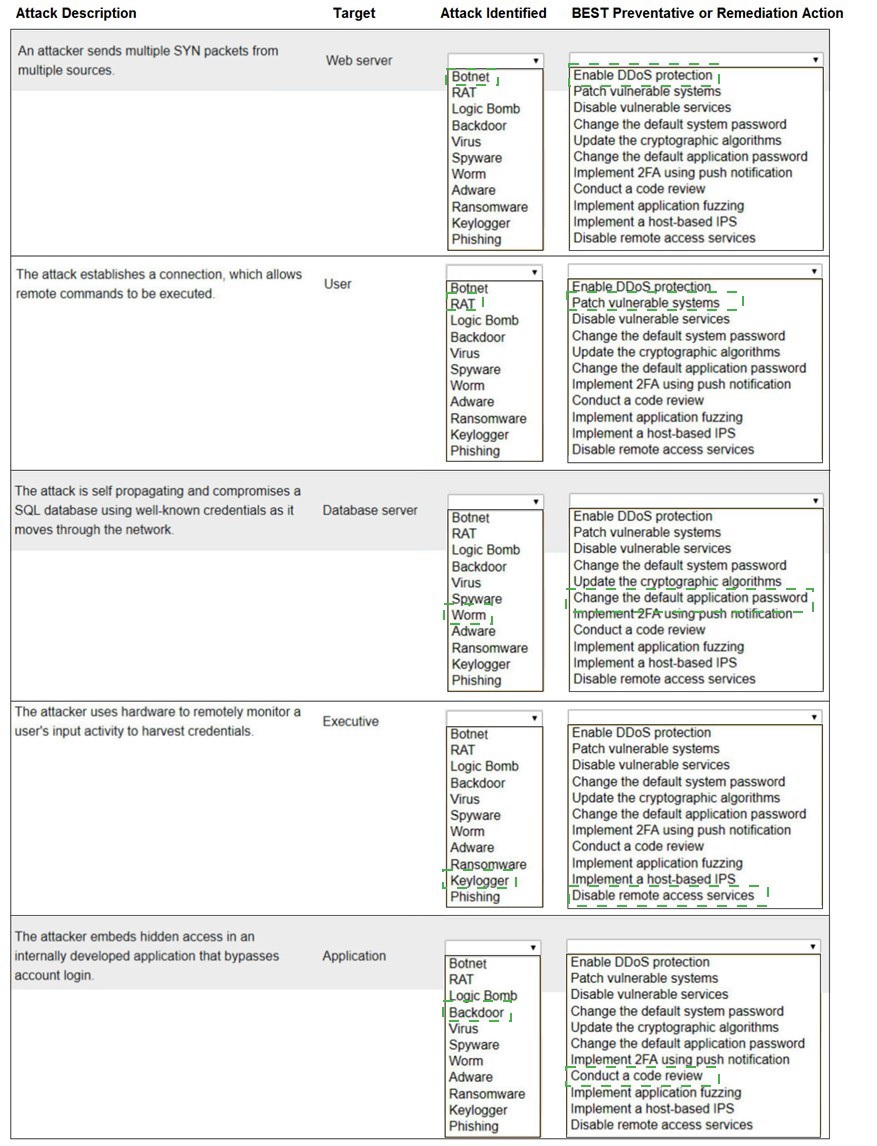
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used. If at any time you would like to bring back the initial state of the simulation, please click the
Reset All button.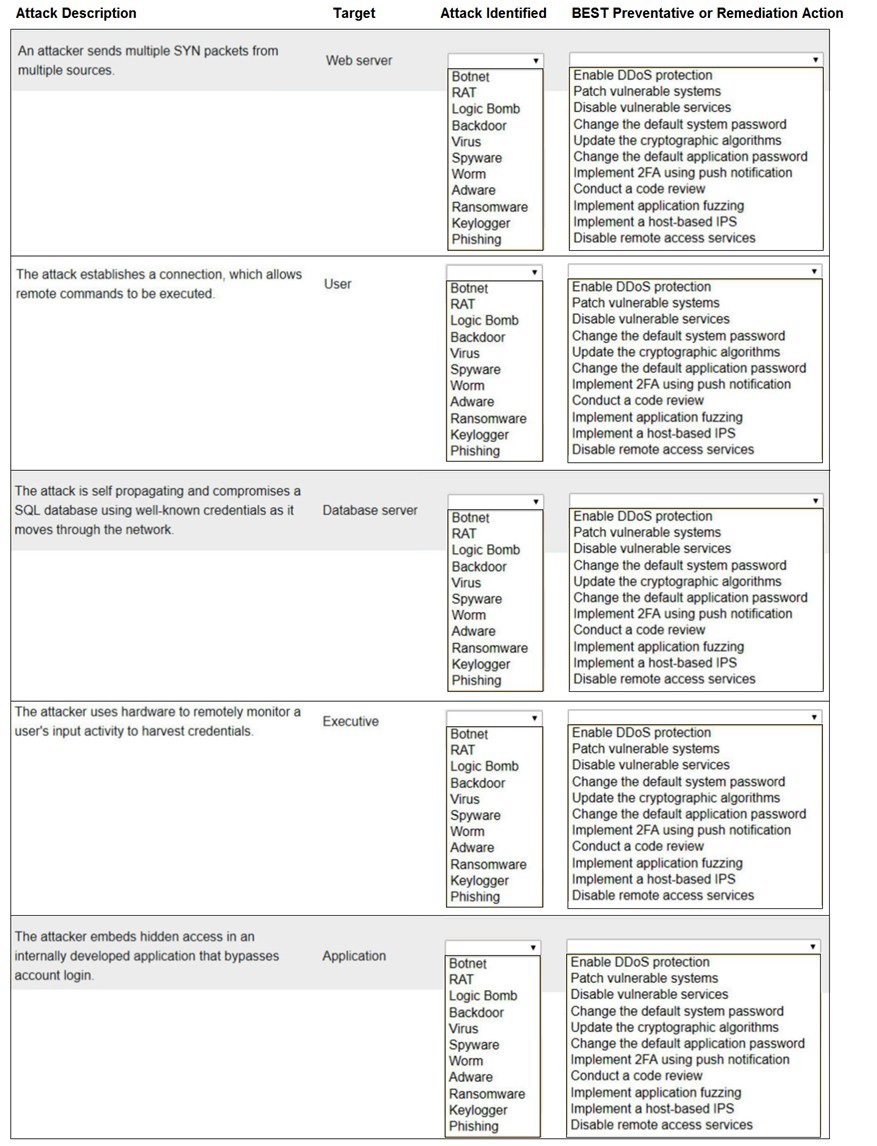
Which of the following control sets should a well-written BCP include? (Select THREE)
A.
Preventive
B.
Detective
C.
Deterrent
D.
Corrective
Preventive
Corrective
A company recently set up an e-commerce portal to sell its product online. The company wants to start accepting credit cards for payment, which requires compliance with a security standard. Which of the following standards must the company comply with before accepting credit cards on its e-commerce platform?
A.
PCI DSS
B.
ISO 22301
C.
ISO 27001
D.
NIST CSF
PCI DSS
Explanation: Additionally, many organizations should abide by certain standards. For
example, organizations handling credit card information need to comply with the Payment
Card Industry Data Security Standard (PCI DSS). PCI DSS includes six control objectives
and 12 specific requirementsthat help prevent fraud.
| Page 10 out of 74 Pages |
| Previous |