Which of the following tasks is the responsibility of a Splunk Cloud administrator?
A. Configuring deployer
B. Configuring cluster master
C. Configuring indexers
D. Configuring indexes
Explanation: In Splunk Cloud, configuring indexes is one of the primary responsibilities of a Splunk Cloud administrator. This task includes setting up new indexes, managing retention policies, and configuring index settings as required by the organization's data retention and compliance policies. Other tasks like configuring deployer, cluster master, or indexers are typically handled by Splunk Enterprise administrators, not Splunk Cloud administrators.
In what scenarios would transforms.conf be used?
A. Per-Event Index Routing, Applying Event Types, SEOCMD operations
B. Per-Event Sourcetype, Per-Event Host Name, Per-Event Index Routing
C. Per-Event Host Name, Per-Event Index Rooting, SEDCMD operations
D. Per-Event Sourcetype, Per-Event Index Routing, Applying Event Types
Explanation: transforms.conf is used for various advanced data processing tasks in
Splunk, including:
Per-Event Sourcetype: Dynamically assigning a sourcetype based on event
content.
Per-Event Host Name: Dynamically setting the host field based on event content.
Per-Event Index Routing: Directing specific events to different indexes based on
their content.
Option B correctly identifies these common uses of transforms.conf.
In which of the following situations should Splunk Support be contacted?
A. When a custom search needs tuning due to not performing as expected.
B. When an app on Splunkbase indicates Request Install.
C. Before using the delete command.
D. When a new role that mirrors sc_admin is required.
Explanation: In Splunk Cloud, when an app on Splunkbase indicates "Request Install," it
means that the app is not available for direct self-service installation and requires
intervention from Splunk Support. This could be because the app needs to undergo an
additional review for compatibility with the managed cloud environment or because it
requires special installation procedures.
In these cases, customers need to contact Splunk Support to request the installation of the
app. Support will ensure that the app is properly vetted and compatible with Splunk Cloud
before proceeding with the installation.
Splunk Cloud Reference: For further details, consult Splunk’s guidelines on requesting
app installations in Splunk Cloud and the processes involved in reviewing and approving apps for use in the cloud environment.
A customer has worked with their LDAP administrator to configure an LDAP strategy in Splunk. The configuration works, and user Mia can log into Splunk using her LDAP Account. After some time, the Splunk Cloud administrator needs to move Mia from the user role to the power role. How should they accomplish this?
A. Ask the LDAP administrator to move Mia's account to an appropriately mapped LDAP group.
B. Have Mia log into Splunk, then update her own role in user settings.
C. Create a role named Power in Splunk, then map Mia's account to that role.
D. Use the Cloud Monitoring Console app as an administrator to map Mia's account to the power role.
Explanation: In Splunk Cloud, role-based access controls are managed by mapping LDAP groups to Splunk roles. Therefore, any change in roles should be managed by the LDAP administrator, who can adjust Mia’s group to an LDAP group mapped to the power role.
What Splunk command will allow an administrator to view the runtime configuration instructions for a monitored file in Inputs. cont on the forwarders?
A. ./splunk _internal call /services/data/input.3/filemonitor
B. ./splunk show config inputs.conf
C. ./splunk _internal rest /services/data/inputs/monitor
D. ./splunk show config inputs
Explanation: To view the runtime configuration instructions for a monitored file in
inputs.conf on the forwarder, the correct command to use involves accessing the internal REST API that provides details on data inputs.
C. ./splunk _internal rest /services/data/inputs/monitor is the correct answer. This
command uses Splunk's internal REST endpoint to retrieve information about
monitored files, including their runtime configurations as defined in inputs.conf.
Which of the following is true when integrating LDAP authentication?
A. Splunk stores LDAP end user names and passwords on search heads.
B. The mapping of LDAP groups to Splunk roles happens automatically.
C. Splunk Cloud only supports Active Directory LDAP servers.
D. New user data is cached the first time a user logs in.
Explanation: When integrating LDAP authentication with Splunk, new user data is cached the first time a user logs in. This means that Splunk does not store LDAP usernames and passwords; instead, it relies on the LDAP server for authentication. The mapping of LDAP groups to Splunk roles must be configured manually; it does not happen automatically. Additionally, Splunk Cloud supports various LDAP servers, not just Active Directory.
Which of the following is not a path used by Splunk to execute scripts?
A. SPLUNK_HOME/etc/system/bin
B. SPLUNK HOME/etc/appa/
C. SPLUNKHOMS/ctc/scripts/local
D. SPLUNK_HOME/bin/scripts
Explanation: Splunk executes scripts from specific directories that are structured within its
installation paths. These directories typically include:
SPLUNK_HOME/etc/system/bin: This directory is used to store scripts that are
part of the core Splunk system configuration.
SPLUNK_HOME/etc/apps/
SPLUNK_HOME/bin/scripts: This is a standard directory for storing scripts that
may be globally accessible within Splunk's environment.
However, C. SPLUNKHOMS/ctc/scripts/local is not a recognized or standard path used
by Splunk for executing scripts. This path does not adhere to the typical directory structure
within the SPLUNK_HOME environment, making it the correct answer as it does not
correspond to a valid script execution path in Splunk.
In which file can the SH0ULD_LINEMERCE setting be modified?
A. transforms.conf
B. inputs.conf
C. props.conf
D. outputs.conf
Explanation: The SHOULD_LINEMERGE setting is used in Splunk to control whether or not multiple lines of an event should be combined into a single event. This setting is configured in the props.conf file, where Splunk handles data parsing and field extraction. Setting SHOULD_LINEMERGE = true merges lines together based on specific rules.
At what point in the indexing pipeline set is SEDCMD applied to data?
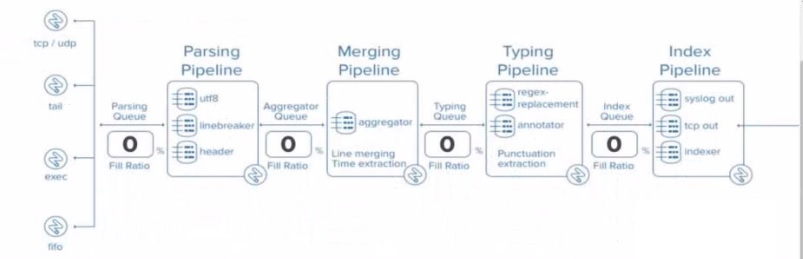
A. In the aggregator queue
B. In the parsing queue
C. In the exec pipeline
D. In the typing pipeline
Explanation: In Splunk, SEDCMD (Stream Editing Commands) is applied during the
Typing Pipeline of the data indexing process. The Typing Pipeline is responsible for
various tasks, such as applying regular expressions for field extractions, replacements, and
data transformation operations that occur after the initial parsing and aggregation steps.
Here’s how the indexing process works in more detail:
Parsing Pipeline: In this stage, Splunk breaks incoming data into events, identifies
timestamps, and assigns metadata.
Merging Pipeline: This stage is responsible for merging events and handling timebased
operations.
Typing Pipeline: The Typing Pipeline is where SEDCMD operations occur. It
applies regular expressions and replacements, which is essential for modifying raw
data before indexing. This pipeline is also responsible for field extraction and other
similar operations.
Index Pipeline: Finally, the processed data is indexed and stored, where it
becomes available for searching.
Splunk Cloud Reference: To verify this information, you can refer to the official Splunk
documentation on the data pipeline and indexing process, specifically focusing on the
stages of the indexing pipeline and the roles they play. Splunk Docs often discuss the exact
sequence of operations within the pipeline, highlighting when and where commands like
SEDCMD are applied during data processing.
When should Splunk Cloud Support be contacted?
A. For scripted input troubleshooting.
B. For all configuration changes.
C. When unable to resolve issues or perform problem isolation.
D. For resizing, license changes, or any purchases.
Explanation: Splunk Cloud Support should be contacted when issues arise that cannot be
resolved internally or when problem isolation has been unsuccessful.
C. When unable to resolve issues or perform problem isolation is the correct answer. Splunk Cloud Support is typically involved when internal troubleshooting
has been exhausted, and the issue requires expert assistance or deeper
investigation. While scripted input troubleshooting might be handled by internal
teams, contacting support for unresolved issues is the appropriate step.
When a forwarder phones home to a Deployment Server it compares the check-sum value of the forwarder's app to the Deployment Server's app. What happens to the app If the check-sum values do not match?
A. The app on the forwarder is always deleted and re-downloaded from the Deployment Server.
B. The app on the forwarder is only deleted and re-downloaded from the Deployment Server if the forwarder's app has a smaller check-sum value.
C. The app is downloaded from the Deployment Server and the changes are merged.
D. A warning is generated on the Deployment Server stating the apps are out of sync. An Admin will need to confirm which version of the app should be used.
Explanation: When a forwarder phones home to a Deployment Server, it compares the checksum of its apps with those on the Deployment Server. If the checksums do not match, the app on the forwarder is always deleted and re-downloaded from the Deployment Server. This ensures that the forwarder has the most current and correct version of the app as dictated by the Deployment Server.
When monitoring directories that contain mixed file types, which setting should be omitted from inputs, conf and instead be overridden in propo.conf?
A. sourcetype
B. host
C. source
D. index
Explanation: When monitoring directories containing mixed file types, the sourcetype
should typically be overridden in props.conf rather than defined in inputs.conf. This is
because sourcetype is meant to classify the type of data being ingested, and when dealing
with mixed file types, setting a single sourcetype in inputs.conf would not be effective for
accurate data classification. Instead, you can use props.conf to define rules that apply
different sourcetypes based on the file path, file name patterns, or other criteria. This allows
for more granular and accurate assignment of sourcetypes, ensuring the data is properly
parsed and indexed according to its type.
Splunk Cloud Reference: For further clarification, refer to Splunk's official documentation
on configuring inputs and props, especially the sections discussing monitoring directories
and configuring sourcetypes.
| Page 2 out of 7 Pages |
| Previous |