Topic 2: Questions Set 2
This clause is used to group the output of a stats command by a specific name.
A. Rex
B. As
C. List
D. By
Why would the following search produce multiple transactions instead of one?
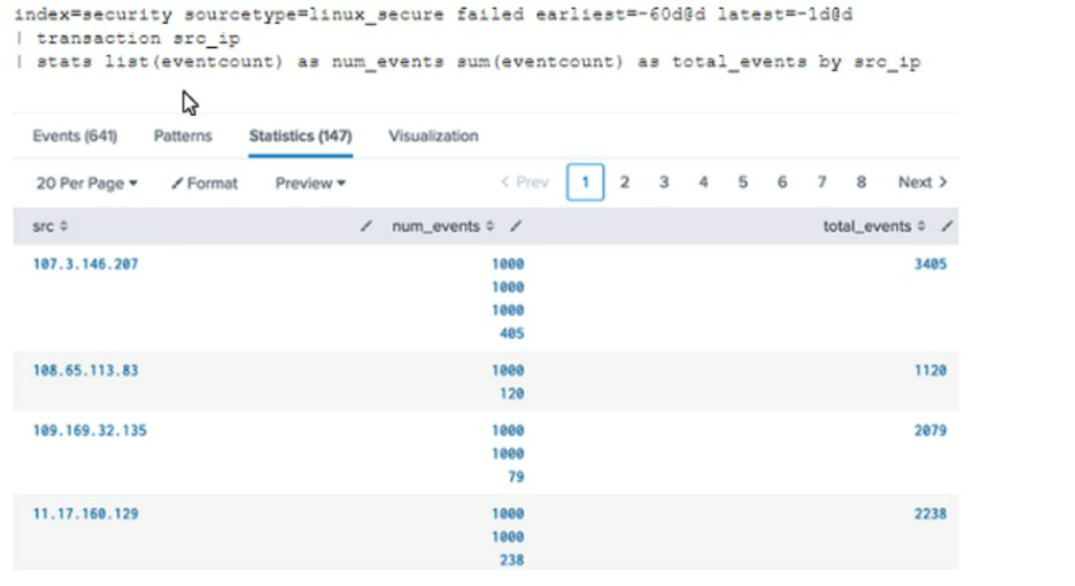
A. The maxspan option is not included
B. The transaction command has a limit of 1000 events per transaction.
C. The transaction and commands cannot be used together
D. The stats list () function is used
Explanation:
In Splunk, thetransactioncommand is used to group events that share common
characteristics into a single transaction1.By default, thetransactioncommand groups all
matching events into a single transaction1.
However, you can use themaxspanoption to limit the time span of the transactions1.If the
time span between the first and last event in a transaction exceeds themaxspanvalue,
thetransactioncommand will start a new transaction1.
Therefore, if themaxspanoption is not included in the search, thetransactioncommand
might produce multiple transactions instead of one if the time span between the first and
last event in a transaction exceeds the defaultmaxspanvalue1.
Here is an example of how you can use themaxspanoption in a search:
index=main sourcetype=access_combined | transaction someuniqefield maxspan=1h
In this search, thetransactioncommand groups events that share the
samesomeuniqefieldvalue into a single transaction, but only if the time span between the
first and last event in the transaction does not exceed 1 hour1.If the time span exceeds 1
hour, thetransactioncommand will start a new transaction1.
What field must be present in order to use the timechart command?
A. _raw
B. rime
C. _time
D. index
Explanation: The timechart command in Splunk requires the _time field to be present in the dataset because it uses time as the primary axis for charting data. The _time field represents the time of events and is essential for commands that generate visualizations based on time, such as timechart. This command groups the events into time intervals and performs statistical functions on those time intervals. Without the _time field, the timechart command will not function properly.
Which search retrieves events with the event type web_errors?
A. tag=web_errors
B. eventtype=web_errors
C. eventtype "web errors"
D. eventtype (web_errors)
Explanation:
The correct answer is B. eventtype=web_errors.
An event type is a way to categorize events based on a search. An event type assigns a
label to events that match a specific search criteria.Event types can be used to filter and
group events, create alerts, or generate reports1.
To search for events that have a specific event type, you need to use the eventtype field
with the name of the event type as the value. The syntax for this is:
eventtype=
For example, if you want to search for events that have the event type web_errors, you can
use the following syntax:
eventtype=web_errors
This will return only the events that match the search criteria defined by the web_errors
event type.
The other options are not correct because they use different syntax or fields that are not
related to event types. These options are:
A. tag=web_errors: This option uses the tag field, which is a way to add descriptive
keywords to events based on field values. Tags are different from event types,
although they can be used together.Tags can be used to filter and group events by
common characteristics2.
C. eventtype “web errors”: This option uses quotation marks around the event type
name, which is not valid syntax for the eventtype field.Quotation marks are used to
enclose phrases or exact matches in a search3.
D. eventtype (web_errors): This option uses parentheses around the event type
name, which is also not valid syntax for the eventtype field.Parentheses are used
to group expressions or terms in a search3.
Which knowledge object is used to normalize field names to comply with the Splunk Common Information Model (CIM)?
A. Field alias
B. Event types
C. Search workflow action
D. Tags
Explanation:
The correct answer isA. Field alias123.
In Splunk, a field alias is a knowledge object that you can use to assign an alternate name
to a field3.This can be particularly useful when you want to normalize your data to comply
with the Splunk Common Information Model (CIM)12.
The CIM provides a methodology for normalizing values to a common field name1.It acts
as a search-time schema to define relationships in the event data while leaving the raw
machine data intact2.By using field aliases, you can map vendor fields to common fields
that are the same for each data source in a given domain4.This allows you to correlate
events from different source types by normalizing these different occurrences to a common
structure and naming convention1.
Which of the following options will define the first event in a transaction?
A. startswith
B. with
C. startingwith
D. firstevent
Explanation:
The explanation is as follows:
Thetransactioncommand is used to find transactions based on events that meet
various constraints12.
Transactions are made up of the raw text (the _raw field) of each member, the
time and date fields of the earliest member, as well as the union of all other fields of each member1.
Thestartswithoption is used to define the first event in a transaction by specifying a
search term or an expression that matches the event13.
For example,| transaction clientip JSESSIONID startswith="view"will create
transactions based on theclientipandJSESSIONIDfields, and the first event in each
transaction will contain the term “view” in the _raw field2.
For choropleth maps,splunk ships with the following KMZ files (select all that apply)
A. States of the United States
B. States and provinces of the united states and Canada
C. Countries of the European Union
D. Countries of the World
Explanation: Splunk ships with the following KMZ files for choropleth maps: States of the
United States and Countries of the World. A KMZ file is a compressed file that contains a
KML file and other resources. A KML file is an XML file that defines geographic features
and their properties. AKMZ file can be used to create choropleth maps in Splunk by using
the geom command. A choropleth map is a type of map that shows geographic regions
with different colors based on some metric. Splunk ships with two KMZ files that define the
geographic regions for choropleth maps:
States of the United States: This KMZ file defines the 50 states of the United
States and their boundaries. The name of this KMZ file is us_states.kmz and it is
located in the $SPLUNK_HOME/etc/apps/maps/appserver/static/geo directory.
Countries of the World: This KMZ file defines the countries of the world and their
boundaries. The name of this KMZ file is world_countries.kmz and it is located in
the $SPLUNK_HOME/etc/apps/maps/appserver/static/geo directory.
Splunk does not ship with KMZ files for States and provinces of the United States and
Canada or Countries of the European Union. However, you can create your own KMZ files
or download them from external sources and use them in Splunk.
A user wants to create a workflow action that will retrieve a specific field value from an event and run a search in a new browser window in the user's Splunk instance. What kind of workflow action should they create?
A. A Run workflow action, because the user is running a new search with a specific field value from an event returned in the user's search.
B. A Search workflow action, because the user is running a new search with a specific field value from an event returned in the user's search.
C. A POST workflow action, because the search is being sent to the user's current Splunk instance.
D. A GET workflow action, because a field value needs to be retrieved from the events returned in the user's search.
Explanation: A Search workflow action is the appropriate choice when a user wants to retrieve a specific field value from an event and run a search in a new browser window within their Splunk instance (Option B). This type of workflow action allows users to define a search that utilizes field values from selected events as parameters, enabling more detailed investigation or context-specific analysis based on the original search results.
When using | timchart by host, which filed is representted in the x-axis?
A. date
B. host
C. time
D. -time
Which type of workflow action sends field values to an external resource (e.g. a ticketing system)?
A. POST
B. Search
C. GET
D. Format
Explanation: The type of workflow action that sends field values to an external resource (e.g. a ticketing system) is POST. A POST workflow action allows you to send a POST request to a URI location with field values or static values as arguments. For example, you can use a POST workflow action to create a ticket in an external system with information from an event.
Which field extraction method should be selected for comma-separated data?
A. Regular expression
B. Delimiters
C. eval expression
D. table extraction
Explanation: The correct answer is B. Delimiters. This is because the delimiters method is designed for structured event data, such as data from files with headers, where all of the fields in the events are separated by a common delimiter, such as a comma or space. You can select a sample event, identify the delimiter, and then rename the fields that the field extractor finds. You can learn more about the delimiters method from the Splunk documentation1. The other options are incorrect because they are not suitable for comma separated data. The regular expression method works best with unstructured event data, where you select and highlight one or more fields to extract from a sample event, and the field extractor generates a regular expression that matches similar events and extracts the fields from them. The eval expression is a command that lets you calculate new fields or modify existing fields using arithmetic, string, and logical operations. The table extraction is a feature that lets you extract tabular data from PDF files or web pages. You can learn more about these methods from the Splunk documentation23.
Which search string would only return results for an event type called success ful_purchases?
A. tag=success ful_purchases
B. Event Type:: successful purchases
C. successful_purchases
D. event type—success ful_purchases
Explanation: This is because event types are added to events as a field named eventtype, and you can use this field as a search term to find events that match a specific event type. For example, eventtype=successful_purchases returns all events that have been categorized as successful purchases by the event type definition. The other options are incorrect because they either use a different field name (tag), a different syntax (Event Type:: or event type—), or have a typo (success ful_purchases). You can learn more about how to use event types in searches from the Splunk documentation1.
| Page 3 out of 23 Pages |
| Previous |