Topic 2: Questions Set 2
When would transaction be used instead of stats
A. To group events based on a single field value.
B. To see results of a calculation
C. To have a faster and more efficient search
D. To group events based on start/end values
Explanation: The transaction command is used to group events that are related by some common fields or conditions, such as start/end values, time span, or pauses. The stats command is used to calculate statistics on a group of events by a common field value.
How is an event type created from the search window? (select all that apply)
A. In the top right corner, click Save As > Event Type.
B. In an event's detail dropdown, click Event Actions > Build Event Type.
C. Edit eventtypes.conf and add a new stanza.
D. Add | eventtype to the SPL and execute the search.
Explanation:
In Splunk, you can create an event type from the search window by running a search that
would make a good event type, then clicking Save As and selecting Event Type1. This
opens the Save as Event Type dialog, where you can provide the event type name and
optionally apply tags to it1.
You can also create an event type by editing the eventtypes.conf file and adding a new
stanza1. Each stanza in the eventtypes.conf file represents an event type1. The stanza
name isthe name of the event type, and the search attribute specifies the search string that
defines the event type1.
Which method in the Field Extractor would extract the port number from the following
event? |
10/20/2022 - 125.24.20.1 ++++ port 54 - user: admin
A. Delimiter
B. rex command
C. The Field Extractor tool cannot extract regular expressions
D. Regular expression
Explanation: The rex command allows you to extract fields from events using regular
expressions. You can use the rex command to specify a named group that matches the
port number in the event. For example:
rex "\+\+\+\+port (?
This will create a field called port with the value 54 for the event.
The delimiter method is not suitable for this event because there is no consistent delimiter
between the fields. The regular expression method is not a valid option for the Field
Extractor tool. The Field Extractor tool can extract regular expressions, but it is not a
method by itself.
This is what Splunk uses to categorize the data that is being indexed
A. Host
B. Sourcetype
C. Index
D. Source
Consider the following search:
Index=web sourcetype=access_combined
The log shows several events that share the same JSESSIONID value
(SD404K289O2F151). View the events as a group. From the following list, which search
groups events by JSESSIONID?
A. index=web sourcetype=access_combined SD404K289O2F151 I table JSESSIONID
B. index=web sourcetype=access_combined JSESSIONID
C. index=web sourcetype=access_combined I highlight JSESSIONID I search SD404K289O2F151
D. index-web sourcetype=access_combined I transaction JSESSIONID I search SD404K289O2F151
Which of the following objects can a calculated field use as a source?
A. An alias of a field.
B. A field added by an automatic lookup.
C. The tag field.
D. The eventtype field.
Explanation: The correct answer is B. A field added by an automatic lookup.
A calculated field is a field that is added to events at search time by using an eval
expression. A calculated field can use the values of two or more fields that are already present in the events to perform calculations.A calculated field can use any field as a
source, as long as the field is extracted before the calculated field is defined1.
An automatic lookup is a way to enrich events with additional fields from an external
source, such as a CSV file or a database.An automatic lookup can add fields to
eventsbased on the values ofexisting fields, such as host, source, sourcetype, or any other
extracted field2.An automatic lookup is performed before the calculated fields are defined,
so the fields added by the lookup can be used as sources for the calculated fields3.
Therefore, a calculated field can use a field added by an automatic lookup as a source.
Which of the following is included with the Common Information Model (CIM) add-on?
A. Search macros
B. Event category tags
C. Workflow actions
D. tsidx files
Explanation: The correct answer is B. Event category tags. This is because the CIM addon contains a collection of preconfigured data models that you can apply to your data at search time. Each data model in the CIM consists of a set of field names and tags that define the least common denominator of a domain of interest. Event category tags are used to classify events into high-level categories, such as authentication, network traffic, or web activity. You can use these tags to filter and analyze events based on their category. You can learn more about event category tags from the Splunk documentation12. The other options are incorrect because they are not included with the CIM add-on. Search macros are reusable pieces of search syntax that you can invoke from other searches. They are not specific to the CIM add-on, although some Splunk apps may provide their own search macros. Workflow actions are custom links or scripts that you can run on specific fields or events. They are also not specific to the CIM add-on, although some Splunk apps may provide their own workflow actions. tsidx files are index files that store the terms and pointers to the raw data in Splunk buckets. They are part of the Splunk indexing process and have nothing to do with the CIM add-on.
Which of the following searches would create a graph similar to the one below?
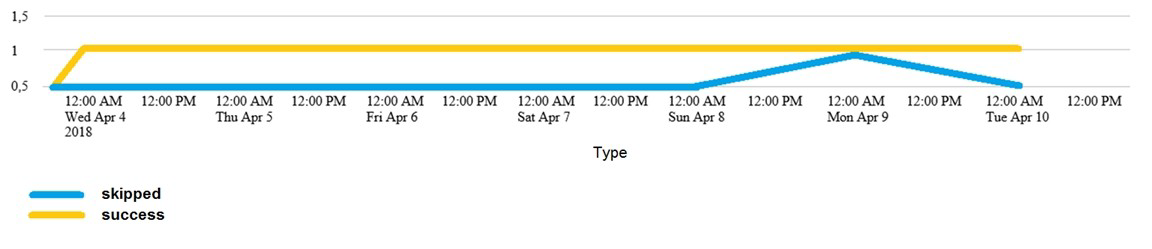
A. index_internal seourcetype=Savesplunker | fields sourcetype, status | transaction status maxspan-id | start count states
B. index_internal seourcetype=Savesplunker | fields sourcetype, status | transaction status maxspan-id | chart count states by -time
C. index_internal seourcetype=Savesplunker | fields sourcetype, status | transaction status maxspan-id | timechart count by status
D. None of these searches would generate a similart graph.
Explanation: The following search would create a graph similar to the one below:
index_internal sourcetype=Savesplunker | fields sourcetype, status | transaction status
maxspan=1d | timechart count by status
The search does the following:
It uses index_internal to specify the internal index that contains Splunk logs and
metrics.
It uses sourcetype=Savesplunker to filter events by the sourcetype that indicates
the Splunk Enterprise Security app.
It uses fields sourcetype, status to keep only the sourcetype and status fields in
the events.
It uses transaction status maxspan=1d to group events into transactions based on
the status field with a maximum time span of one day between the first and last
events in a transaction.
It uses timechart count by status to create a time-based chart that shows the count
of transactions for each status value over time.
The graph shows the following:
It is a line graph with two lines, one yellow and one blue.
The x-axis is labeled with dates from Wed, Apr 4, 2018 to Tue, Apr 10, 2018.
The y-axis is labeled with numbers from 0 to 15.
The yellow line represents “shipped” and the blue line represents “success”.
The yellow line has a steady increase from 0 to 15, while the blue line has a sharp
increase from 0 to 5, then a decrease to 0, and then a sharp increase to 10.
The graph is titled “Type”.
Which of the following statements describes an event type?
A. A log level measurement: info, warn, error.
B. A knowledge object that is applied before fields are extracted.
C. A field for categorizing events based on a search string.
D. Either a log, a metric, or a trace.
Explanation: This is because an event type is a knowledge object that assigns a userdefined name to a set of events that match a specific search criteria. For example, you can create an event type named successful_purchase for events that have sourcetype=access_combined, status=200, and action=purchase. Then, you can use eventtype=successful_purchase as a search term to find those events. You can also use event types to create alerts, reports, and dashboards. You can learn more about event types from the Splunk documentation1. The other options are incorrect because they do not describe what an event type is. A log level measurement is a field that indicates the severity of an event, such as info, warn, or error. A knowledge object that is applied before fields are extracted is a source type, which identifies the format and structure of the data. Either a log, a metric, or a trace is a type of data that Splunk can ingest and analyze, but not an event type.
The timechart command buckets data in time intervals depending on:
A. the number of events returned
B. the selected time range
C. the type of visualization selected
Explanation: The timechart command buckets data in time intervals depending on the selected time range2. The timechart command is similar to the chart command but it automatically groups events into time buckets based on the _time field2. The size of the time buckets depends on the time range that you select for your search. For example, if you select Last 24 hours as your time range, Splunk will use 30-minute buckets for your timechart. If you select Last 7 days as your time range, Splunk will use 4-hourbuckets for your timechart2. Therefore, option B is correct, while options A and C are incorrect because they are not factors that affect the size of the time buckets.
A POST workflow action will pass which types of arguments to an external website?
A. Clear text only.
B. A mix of clear text strings and variables.
C. It can only send raw event data.
D. Variables only.
Explanation: A POST workflow action in Splunk is designed to send data to an external web service by using HTTP POST requests. This type of workflow action can pass a combination of clear text strings and variables derived from the search results or event data. The clear text strings might include static text or predefined values, while the variables are dynamic elements that represent specific fields or values extracted from the Splunk events. This flexibility allows for constructing detailed and context-specific requests to external systems, enabling various integration and automation scenarios. The POST request can include both types of data, making it versatile for different use cases.
When using the transaction command, how are evicted transactions identified?
A. Closed_txn field is set to o, or false.
B. Max_txn field is set to O, or false.
C. Txn_field is set to 1, or true.
D. open_txn field is set to 1, or true.
Explanation:
The transaction command is a Splunk command that finds transactions based on
events that meet various constraints1.
Transactions are made up of the raw text (the _raw field) of each member, the
time and date fields of the earliest member, as well as the union of all other fields
of each member1.
The transaction command adds some fields to the raw events that are part of the
transaction12. These fields are:
Therefore, evicted transactions can be distinguished from non-evicted transactions
by checking the value of the closed_txn field. The closed_txn field is set to 0, or
false, for evicted transactions and 1, or true for non-evicted, or closed,
transactions23.
| Page 2 out of 23 Pages |
| Previous |