Topic 2: Questions Set 2
Which of the following is true about data model attributes?
A. They cannot be created within the data model.
B. They can only be added into a root search dataset.
C. They cannot be edited if inherited from a parent dataset.
D. They can be added to a dataset from search time field extractions.
Data model attributes are fields that are added to a dataset from search time field extractions, calculated fields, lookups, or aliases. They can be created within the data model editor or inherited from a parent dataset. They can be edited or removed unless they are required by the data model. They can be added to any type of dataset, not just root search datasets.ReferencesSee About data models, [Define data model attributes], and [Edit data model datasets] in the Splunk Documentation.
A calculated field may be based on which of the following?
A. Fields generated within a search string
B. Lookup tables
C. Regular expressions
D. Extracted fields
Explanation:
In Splunk, calculated fields allow you to create new fields using expressions that can
transform or combine the values of existing fields. Although all options provided might
seem viable, when selecting only one option that is most representative of a calculated
field, we typically refer to:
D.Extracted fields: Calculated fields are often based on fields that have already been
extracted from your data. Extracted fields are those that Splunk has identified and pulled
outfrom the event data based on patterns, delimiters, or other methods such as regular
expressions or automatic extractions. These fields can then be used in expressions to
create calculated fields.
For example, you might have an extracted field for the time in seconds, and you want to
create a calculated field for the time in minutes. You would use the extracted field in a
calculation to create the new field.
It's important to note that although fields generated within a search string (A) and regular
expressions (C) can also be used in the calculation of a new field, and lookup tables (B)
can be used to enrich data, option D is typically what one refers to when discussing
calculated fields, as it implies a direct transformation or calculation based on fields that
have been extracted from the raw data.
What is the purpose of the fillnull command?
A. Replace empty values with a specified value.
B. Create a new field based on the values in an existing field.
C. Rename a specific field in the search results.
D. Replace all values in a specific field with a default value.
Explanation:
Thefillnullcommand in Splunk is used to handle missing data within search results. It plays
a crucial role in data normalization and preparation, especially before performing statistical
analyses or visualizations.
A.Replace empty values with a specified value:This is the correct answer. Thefillnull
command is specifically designed to replace null values (empty values) with a specified
default value. This is particularly useful in ensuring consistency within your data, especially
when performing operations that require numerical values or when you want to distinguish
between genuinely missing data and zeroes, for instance.
Example Usage:... | fillnull value=0This command would replace all null values in
the search results with 0.
Clicking a SEGMENT on a chart, ________.
A. drills down for that value
B. highlights the field value across the chart
C. adds the highlighted value to the search criteria
When you mouse over and click to add a search term this (these. Boolean operator(s) is (are. not implied. (Select all that apply).
A. OR
B. ( )
C. AND
D. NOT
Explanation: When you mouse over and click to add a search term from the Fields sidebar or from an event in your search results, Splunk automatically adds the term to your search string with an implied ANDoperator2. However, this does not apply to some Boolean operators such as OR, NOT and parentheses (). These operators are not implied when you add a search term and you have to type them manually if you want to use them in your search string2. Therefore, options A, B and D are correct, while option C is incorrect because AND is implied when you add a search term.
Which command is used to create choropleth maps?
A. geostats
B. cluster
C. geom
How could the following syntax for the chart command be rewritten to remove the OTHER category? (select all that apply)
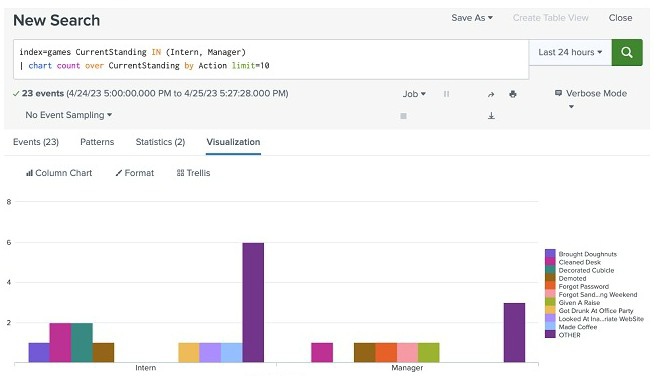
A. | chart count over CurrentStanding by Action useother=f
B. | chart count over CurrentStanding by Action usenull-f useother-t
C. | chart count over CurrentStanding by Action limit=10 useother=f
D. | chart count over CurrentStanding by Action limit-10
Explanation: In Splunk, when using thechartcommand, theuseotherparameter can be set
tofalse(f) to remove the 'OTHER' category, which is a bucket that Splunk uses to
aggregate low-cardinality groups into a single group to simplify visualization. Here's how
the options break down:
A.| chart count over CurrentStanding by Action useother=fThis command correctly
sets theuseotherparameter tofalse, which would prevent the 'OTHER' category from being
displayed in the resulting visualization.
B.| chart count over CurrentStanding by Action usenull=f useother=tThis command
hasuseotherset totrue(t), which means the 'OTHER' category would still be included, so
this is not a correct option.
C.| chart count over CurrentStanding by Action limit=10 useother=fSimilar to option A,
this command also setsuseothertofalse, additionally imposing a limit to the top 10 results,
which is a way to control the granularity of the chart but also to remove the 'OTHER'
category.
D.| chart count over CurrentStanding by Action limit-10This command has a syntax
error (limit-10should belimit=10) and does not include theuseother=fclause. Therefore, it
would not remove the 'OTHER' category, making it incorrect.
The correct answers to rewrite the syntax to remove the 'OTHER' category are options A
and C, which explicitly setuseother=f.
In which Settings section are macros defined?
A. Fields
B. Tokens
C. Advanced Search
D. Searches, Reports, Alerts
The gauge command:
A. creates a single-value visualization
B. allows you to set colored ranges for a single-value visualization
C. creates a radial gauge visualization
Which statement is true?
A. Pivot is used for creating datasets.
B. Data model are randomly structured datasets.
C. Pivot is used for creating reports and dashboards.
D. In most cases, each Splunk user will create their own data model.
Pivot is used for creating reports and dashboards. Pivot is a tool that allows you to create reports and dashboards from your data models without writing any SPL commands. Pivot
can help you visualize and analyze your data using various options, such as filters, rows,
columns,cells, charts, tables, maps, etc. Pivot can also help you accelerate your reports
and dashboards by using summary data from your accelerated data models.
Pivot is not used for creating datasets or data models. Datasets are collections of events
that represent your data in a structured and hierarchical way. Data models are predefined
datasets for various domains, such as network traffic, web activity, authentication, etc.
Datasets and data models can be created by using commands such as datamodel or pivot.
Select this in the fields sidebar to automatically pipe you search results to the rare command
A. events with this field
B. rare values
C. top values by time
D. top values
Explanation: The fields sidebar is a panel that shows the fields that are present in your search results2. The fields sidebar has two sections: selected fields and interesting fields2. Selected fields are fields that you choose to display in your search results by clicking on them in the fields sidebar or by using the fieldscommand2. Interesting fields are fields that appear in at least 20 percent of events or have high variability among values2. For each field in the fields sidebar, you can select one of the following options: events with this field, rare values, top values by time or top values2. If you select rare values, Splunk will automatically pipe your search results to the rare command, which shows the least common values of a field2. Therefore, option B is correct, while options A, C and D are incorrect because they do not pipe your search results to the rare command.
When should transaction be used?
A. Only in a large distributed Splunk environment.
B. When calculating results from one or more fields.
C. When event grouping is based on start/end values.
D. When grouping events results in over 1000 events in each group.
| Page 10 out of 23 Pages |
| Previous |