Topic 1: Mix Questions
A SysOps Administrator runs a web application that is using a microservices approach
whereby different responsibilities of the application have been divided in a separate
microservice running on a different Amazon EC2 instance. The administrator has been
tasked with reconfiguring the infrastructure to support this approach.
How can the administrator accomplish this with the LEAST administrative overhead?
A.
Use Amazon CloudFront to log the URL and forward the request.
B.
Use Amazon CloudFront to rewrite the header based on the microservice and forward the request.
C.
Use an Application Load Balancer (ALB) and do path-based routing.
D.
Use a Network Load Balancer (NLB) and do path-based routing.
Use an Application Load Balancer (ALB) and do path-based routing.
Explanation: https://aws.amazon.com/premiumsupport/knowledge-center/elb-achievepath-
based-routing-alb/
A development team recently deployed a new version of a web application to production.
After the release, penetration testing revealed a cross-site scripting vulnerability that could
expose user data.
Which AWS service will mitigate this issue?
A.
AWS Shield Standard
B.
AWS WAF
C.
Elastic Load Balancing
D.
Amazon Cognito
AWS Shield Standard
A company uses AWS Cloud Formation templates to deploy cloud infrastructure. An analysis of all the company's templates shows that the company has declared the same components in multiple templates. A SysOps administrator needs to create dedicated templates that have their own parameters and conditions for these common components. Which solution will meet this requirement?
A.
Develop a CloudFormaiion change set.
B.
Develop CloudFormation macros.
C.
Develop CloudFormation nested stacks.
D.
Develop CloudFormation stack sets.
Develop CloudFormation nested stacks.
A manufacturing company uses an Amazon RDS DB instance to store inventory of all stock items. The company maintains several AWS Lambda functions that interact with the database to add, update, and delete items. The Lambda functions use hardcoded credentials to connect to the database.
A SysOps administrator must ensure that the database credentials are never stored in plaintext and that the password is rotated every 30 days.
Which solution will meet these requirements in the MOST operationally efficient manner?
A.
Store the database password as an environment variable for each Lambda function. Create a new Lambda function that is named
PasswordRotate. Use Amazon EventBridge (Amazon CloudWatch Events) to schedule the PasswordRotate function every 30 days to change the database password and update the environment variable for each Lambda function.
B.
Use AWS Key Management Service (AWS KMS) to encrypt the database password and to store the encrypted password as an environment
variable for each Lambda function. Grant each Lambda function access to the KMS key so that the database password can be decrypted when required. Create a new Lambda function that is named PasswordRotate to change the password every 30 days.
C.
Use AWS Secrets Manager to store credentials for the database. Create a Secrets Manager secret, and select the database so that Secrets Manager will use a Lambda function to update the database password automatically. Specify an automatic rotation schedule of 30 days. Update each Lambda function to access the database password from
SecretsManager.
D.
Use AWS Systems Manager Parameter Store to create a secure string to store credentials for the database. Create a new Lambda function called PasswordRotate. Use
Amazon EventBridge (Amazon CloudWatch Events) to schedule the PasswordRotate
function every 30 days to change the database password and to update the secret within
Parameter Store. Update each Lambda function to access the database password from
Parameter Store.
Use AWS Secrets Manager to store credentials for the database. Create a Secrets Manager secret, and select the database so that Secrets Manager will use a Lambda function to update the database password automatically. Specify an automatic rotation schedule of 30 days. Update each Lambda function to access the database password from
SecretsManager.
Explanation: When you choose to enable rotation, Secrets Manager supports the following
Amazon Relational Database Service (Amazon RDS) databases with AWS written and
tested Lambda rotation function templates, and full configuration of the rotation process:
Amazon Aurora on Amazon RDS
MySQL on Amazon RDS
PostgreSQL on Amazon RDS
Oracle on Amazon RDS
MariaDB on Amazon RDS
Microsoft SQL Server on Amazon RDS
https://docs.aws.amazon.com/secretsmanager/latest/userguide/intro.html
A company hosts a web portal on Amazon EC2 instances. The web portal uses an Elastic Load Balancer (ELB) and Amazon Route 53 for its public DNS service. The ELB and the EC2 instances are deployed by way of a single AWS CloudFormation stack in the us-east- 1 Region. The web portal must be highly available across multiple Regions. Which configuration will meet these requirements?
A.
Deploy a copy of the stack in the us-west-2 Region. Create a single start of authority
(SOA) record in Route 53 that includes the IP address from each ELB. Configure the SOA
record with health checks. Use the ELB in us-east-1 as the primary record and the ELB in
us-west-2 as the secondary record.
B.
Deploy a copy of the stack in the us-west-2 Region. Create an additional A record in Route 53 that includes the ELB in us-west-2 as an alias target. Configure the A records with a failover routing policy and health checks. Use the ELB in us-east-1 as the primary record and the ELB in us-west-2 as the secondary record.
C.
Deploy a new group of EC2 instances in the us-west-2 Region. Associate the new EC2 instances with the existing ELB, and configure load balancer health checks on all EC2 instances. Configure the ELB to update Route 53 when EC2 instances in us-west-2 fail
health checks.
D.
Deploy a new group of EC2 instances in the us-west-2 Region. Configure EC2 health checks on all EC2 instances in each Region. Configure a peering connection between the
VPCs. Use the VPC in us-east-1 as the primary record and the VPC in us-west-2 as the secondary record.
Deploy a copy of the stack in the us-west-2 Region. Create an additional A record in Route 53 that includes the ELB in us-west-2 as an alias target. Configure the A records with a failover routing policy and health checks. Use the ELB in us-east-1 as the primary record and the ELB in us-west-2 as the secondary record.
A SysOps administrator is building a process for sharing Amazon RDS database snapshots between different accounts associated with different business units within the same company. All data must be encrypted at rest. How should the administrator implement this process?
A.
Write a script to download the encrypted snapshot, decrypt it using the AWS KMS encryption key used to encrypt the snapshot, then create a new volume in each account.
B.
Update the key policy to grant permission to the AWS KMS encryption key used to encrypt the snapshot with all relevant accounts, then share the snapshot with those accounts.
C.
Create an Amazon EC2 instance based on the snapshot, then save the instance's
Amazon EBS volume as a snapshot and share it with the other accounts. Require each
account owner to create a new volume from that snapshot and encrypt it.
D.
Create a new unencrypted RDS instance from the encrypted snapshot, connect to the instance using SSH/RDP. export the database contents into a file, then share this file with the other accounts.
Update the key policy to grant permission to the AWS KMS encryption key used to encrypt the snapshot with all relevant accounts, then share the snapshot with those accounts.
A company has attached the following policy to an IAM user: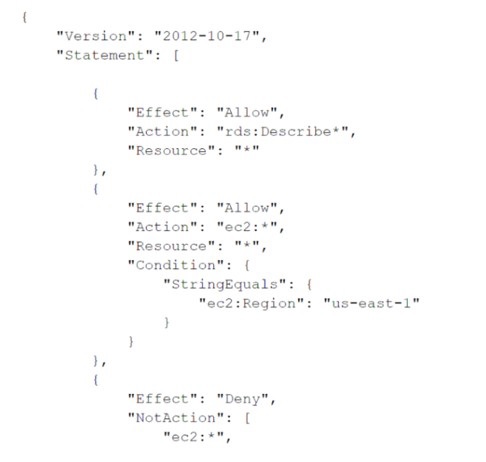
Which of the following actions are allowed for the IAM user?
A.
Amazon RDS DescribeDBInstances action in the us-east-1 Region
B.
Amazon S3 Putobject operation in a bucket named testbucket
C.
Amazon EC2 Describe Instances action in the us-east-1 Region
D.
Amazon EC2 AttachNetworkinterf ace action in the eu-west-1 Region
Amazon EC2 Describe Instances action in the us-east-1 Region
A SysOps administrator noticed that the cache hit ratio for an Amazon CloudFront
distribution is less than 10%.
Which collection of configuration changes will increase the cache hit ratio for the
distribution? (Select TWO.)
A.
Ensure that only required cookies, query strings, and headers are forwarded in the Cache Behavior Settings.
B.
Change the Viewer Protocol Policy to use HTTPS only.
C.
Configure the distribution to use presigned cookies and URLs to restrict access to the distribution.
D.
Enable automatic compression of objects in the Cache Behavior Settings.
E.
Increase the CloudFront time to live (TTL) settings in the Cache Behavior Settings
Ensure that only required cookies, query strings, and headers are forwarded in the Cache Behavior Settings.
Increase the CloudFront time to live (TTL) settings in the Cache Behavior Settings
While setting up an AWS managed VPN connection, a SysOps administrator creates a
customer gateway resource in AWS The customer gateway device resides in a data center
with a NAT gateway in front of it
What address should be used to create the customer gateway resource?
A.
The private IP address of the customer gateway device
B.
The MAC address of the NAT device in front of the customer gateway device
C.
The public IP address of the customer gateway device
D.
The public IP address of the NAT device in front of the customer gateway device
The public IP address of the NAT device in front of the customer gateway device
A company's IT department noticed an increase in the spend of their developer AWS account. There are over 50 developers using the account, and the finance team wants to
determine the service costs incurred by each developer.
What should a SysOps administrator do to collect this information? (Select TWO.)
A.
Activate the createdBy tag in the account.
B.
Analyze the usage with Amazon CloudWatch dashboards.
C.
Analyze the usage with Cost Explorer.
D.
Configure AWS Trusted Advisor to track resource usage.
E.
Create a billing alarm in AWS Budgets.
Activate the createdBy tag in the account.
Analyze the usage with Cost Explorer.
A company monitors its account activity using AWS CloudTrail. and is concerned that some
log files are being tampered with after the logs have been delivered to the account's
Amazon S3 bucket.
Moving forward, how can the SysOps administrator confirm that the log files have not been
modified after being delivered to the S3 bucket?
A.
Stream the CloudTrail logs to Amazon CloudWatch Logs to store logs at a secondary location.
B.
Enable log file integrity validation and use digest files to verify the hash value of the log file.
C.
Replicate the S3 log bucket across regions, and encrypt log files with S3 managed keys.
D.
Enable S3 server access logging to track requests made to the log bucket for security audits.
Enable log file integrity validation and use digest files to verify the hash value of the log file.
A SysOps administrator is setting up an automated process to recover an Amazon EC2
instance In the event of an underlying hardware failure. The recovered instance must have
the same private IP address and the same Elastic IP address that the original instance had.
The SysOps team must receive an email notification when the recovery process is initiated.
Which solution will meet these requirements?
A.
Create an Amazon CloudWatch alarm for the EC2 instance, and specify the
SiatusCheckFailedjnstance metric. Add an EC2 action to the alarm to recover the instance.
Add an alarm notification to publish a message to an Amazon Simple Notification Service
(Amazon SNS> topic. Subscribe the SysOps team email address to the SNS topic.
B.
Create an Amazon CloudWatch alarm for the EC2 Instance, and specify the
StatusCheckFailed_System metric. Add an EC2 action to the alarm to recover the instance.
Add an alarm notification to publish a message to an Amazon Simple Notification Service
(Amazon SNS) topic. Subscribe the SysOps team email address to the SNS topic.
C.
Create an Auto Scaling group across three different subnets in the same Availability
Zone with a minimum, maximum, and desired size of 1. Configure the Auto Seating group
to use a launch template that specifies the private IP address and the Elastic IP address.
Add an activity notification for the Auto Scaling group to send an email message to the
D.
Create an Auto Scaling group across three Availability Zones with a minimum,
maximum, and desired size of 1. Configure the Auto Scaling group to use a launch
template that specifies the private IP address and the Elastic IP address. Add an activity
notification for the Auto Scaling group to publish a message to an Amazon Simple
Notification Service (Amazon SNS) topic. Subscribe the SysOps team email address to the
SNS topic.
Create an Amazon CloudWatch alarm for the EC2 Instance, and specify the
StatusCheckFailed_System metric. Add an EC2 action to the alarm to recover the instance.
Add an alarm notification to publish a message to an Amazon Simple Notification Service
(Amazon SNS) topic. Subscribe the SysOps team email address to the SNS topic.
Explanation: You can create an Amazon CloudWatch alarm that monitors an Amazon
EC2 instance and automatically recovers the instance if it becomes impaired due to an
underlying hardware failure or a problem that requires AWS involvement to repair.
Terminated instances cannot be recovered. A recovered instance is identical to the original
instance, including the instance ID, private IP addresses, Elastic IP addresses, and all
instance metadata. If the impaired instance has a public IPv4 address, the instance retains
the public IPv4 address after recovery. If the impaired instance is in a placement group, the
recovered instance runs in the placement group. When the StatusCheckFailed_System
alarm is triggered, and the recover action is initiated, you will be notified by the Amazon
SNS topic that you selected when you created the alarm and associated the recover action.
https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-instance-recover.html
| Page 2 out of 41 Pages |
| Previous |