Topic 4: Misc. Questions
You have a Microsoft 36S tenant.
You create a named location named HighRiskCountries that contains a list of high-risk
countries.
You need to limit the amount of time a user can stay authenticated when connecting from a
high-risk country.
What should you configure in a conditional access policy? To answer, select the
appropriate options in the answer area.
NOTE: Each correct selection is worth one point.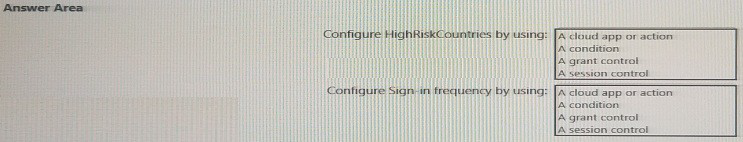
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site
named Site1.
You need to ensure that users can request access to Site. the solution must meet the
following requirements.
• Automatically approve requests from users based on their group membership.
• Automatically remove the access after 30 days
What should you do?
A. Create a Conditional Access policy.
B. Create an access package
C. Configure Role settings in Azure AD Privileged Identity Management
D. Create a Microsoft Defender for Cloud Apps access policy
You have a Microsoft Entra tenant that uses Microsoft Entra ID Premium licenses.
You plan to configure a terms of use (ToU) for the tenant.
You need to upload the ToU document.
Which format should you use for the document?
A. HTML
B. RTF
C. PDF
D. DOCX
You have a Microsoft 365 tenant.
All users have mobile phones and laptops.
The users frequently work from remote locations that do not have Wi-Fi access or mobile
phone connectivity.
While working from the remote locations, the users connect their laptop to a wired network
that has internet
access.
You plan to implement multi-factor authentication (MFA).
Which MFA authentication method can the users use from the remote location?
A. a notification through the Microsoft Authenticator app
B. security questions
C. voice
D. an app password
Note: This question is part of a series of questions that present the same scenario. Each
question in the series contains a unique solution that might meet the stated goals. Some
question sets might have more than one correct solution, while others might not have a
correct solution.
After you answer a question in this section, you will NOT be able to return to it as a result,
these questions will not appear in the review screen.
You have an Amazon Web Services (AWS) account, a Google Workspace subscription,
and a GitHub account.
You deploy an Azure subscription and enable Microsoft 365 Defender.
You need to ensure that you can monitor OAuth authentication requests by using Microsoft
Defender for Cloud Apps.
Solution: From the Microsoft 365 Defender portal, you add the Amazon Web Services app
connector.
Does this meet the goal?
A. Yes
B. No
You create the Azure Active Directory (Azure AD) users shown in the following table.
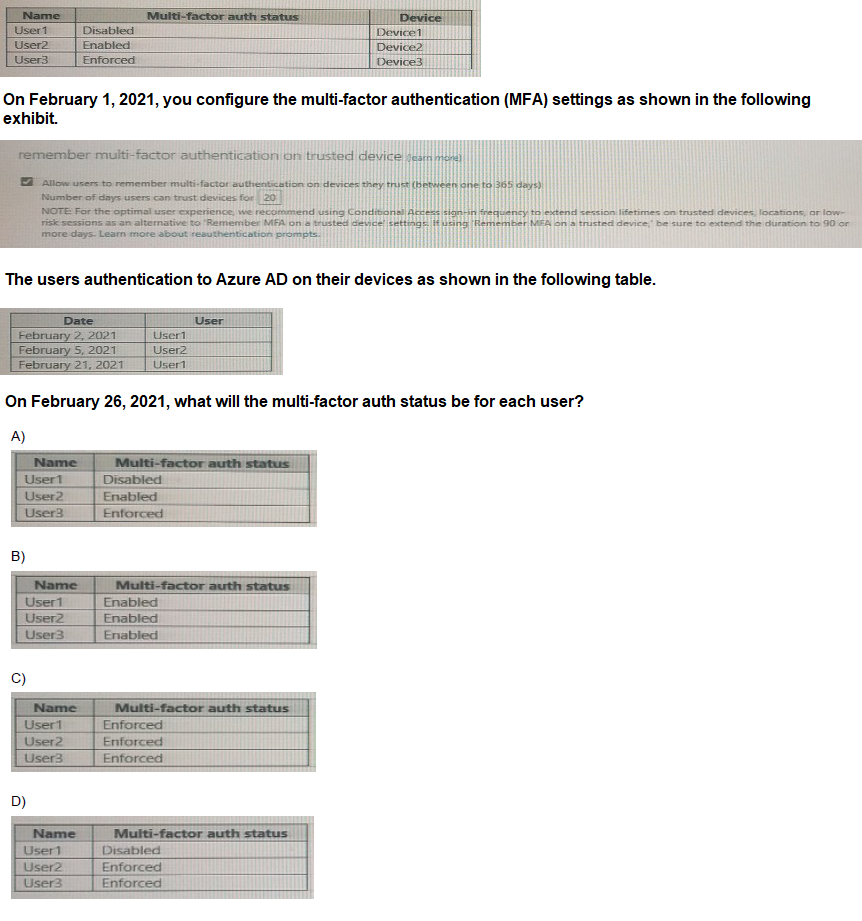
A. Option A
B. Option B
C. Option C
D. Option D
You have an Azure subscription that contains an Azure Automation account named Automation1 and an Azure key vault named Vault1. Vault1 contains a secret named Secret
1.
You enable a system-assigned managed identity for Automation1.
You need to ensure that Automation! can read the contents of Secret1. The solution must
meet the following requirements:
A. From Vault1, configure the Access control (1AM) settings.
B. From Automation1, configure the Identity settings.
C. From Secret1, configure the Access control (1AM) settings
D. From Automation1, configure the Run as accounts settings.
You have an Azure AD tenant that contains a user named User1 User1 needs to manage license assignments and reset user passwords. Which role should you assign to User1?
A. License administrator
B. Helpdesk administrator
C. Billing administrator
D. User administrator
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. You need to be notified if a user downloads more than 50 files in one minute from Site1. Which type of policy should you create in the Microsoft Defender for Cloud Apps portal?
A. session policy
B. anomaly detection policy
C. activity policy
D. file policy
Your network contains an Active Directory forest named contoso.com that is linked to an
Azure Active Directory
(Azure AD) tenant named contoso.com by using Azure AD Connect.
You need to prevent the synchronization of users who have the extensionAttribute15
attribute set to
NoSync.
What should you do in Azure AD Connect?
A. Create an inbound synchronization rule for the Windows Azure Active Directory connector.
B. Configure a Full Import run profile.
C. Create an inbound synchronization rule for the Active Directory Domain Services connector.
D. Configure an Export run profile.
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1. You need to ensure that User1 can create new catalogs and add resources to the catalogs they own. What should you do?
A. From the Roles and administrators blade, modify the Service support administrator role
B. From the identity Governance blade, modify the Entitlement management settings.
C. From the Identity Governance blade, modify the roles and administrators for the General catalog
D. From the Roles and administrators blade, modify the Groups administrator role.
You have a Microsoft 365 E5 subscription. You need to be able to create a Microsoft Defender for Cloud Apps session policy. What should you do first?
A. From the Microsoft Defender portal, select User monitoring.
B. From the Microsoft Entra admin center, create a Conditional Access policy.
C. From the Microsoft Defender portal, select App onboarding/maintenance
D. From the Microsoft Defender portal, create a continuous report
| Page 1 out of 26 Pages |