Topic 1: Exam Pool A
A company is planning to store a large number of archived documents and make the
documents available to employees through the corporate intranet. Employees will access
the system by connecting through a client VPN service that is attached to a VPC. The data
must not be accessible to the public.
The documents that the company is storing are copies of data that is held on physical
media elsewhere. The number of requests will be low. Availability and speed of retrieval
are not concerns of the company.
Which solution will meet these requirements at the LOWEST cost?
A. Create an Amazon S3 bucket. Configure the S3 bucket to use the S3 One Zone- Infrequent Access (S3 One Zone-IA) storage class as default. Configure the S3 bucket for website hosting. Create an S3 interface endpoint. Configure the S3 bucket to allow access only through that endpoint.
B. Launch an Amazon EC2 instance that runs a web server. Attach an Amazon Elastic File System (Amazon EFS) file system to store the archived data in the EFS One Zone- Infrequent Access (EFS One Zone-IA) storage class Configure the instance security groups to allow access only from private networks.
C. Launch an Amazon EC2 instance that runs a web server Attach an Amazon Elastic Block Store (Amazon EBS) volume to store the archived data. Use the Cold HDD (sc1) volume type. Configure the instance security groups to allow access only from private networks.
D. Create an Amazon S3 bucket. Configure the S3 bucket to use the S3 Glacier Deep Archive storage class as default. Configure the S3 bucket for website hosting. Create an S3 interface endpoint. Configure the S3 bucket to allow access only through that endpoint.
A company is migrating some of its applications to AWS. The company wants to migrate
and modernize the applications quickly after it finalizes networking and security strategies.
The company has set up an AWS Direct Connection connection in a central network account.
The company expects to have hundreds of AWS accounts and VPCs in the near future.
The corporate network must be able to access the resources on AWS seamlessly and also
must be able to communicate with all the VPCs. The company also wants to route its cloud
resources to the internet through its on-premises data center.
Which combination of steps will meet these requirements? (Choose three.)
A. Create a Direct Connect gateway in the central account. In each of the accounts, create an association proposal by using the Direct Connect gateway and the account ID for every virtual private gateway.
B. Create a Direct Connect gateway and a transit gateway in the central network account. Attach the transit gateway to the Direct Connect gateway by using a transit VIF.
C. Provision an internet gateway. Attach the internet gateway to subnets. Allow internet traffic through the gateway.
D. Share the transit gateway with other accounts. Attach VPCs to the transit gateway.
E. Provision VPC peering as necessary.
F. Provision only private subnets. Open the necessary route on the transit gateway and customer gateway to allow outbound internet traffic from AWS to flow through NAT services that run in the data center.
A company has a latency-sensitive trading platform that uses Amazon DynamoDB as a
storage backend. The company configured the DynamoDB table to use on-demand
capacity mode. A solutions architect needs to design a solution to improve the performance
of the trading platform. The new solution must ensure high availability for the trading
platform.
Which solution will meet these requirements with the LEAST latency?
A. Create a two-node DynamoDB Accelerator (DAX) cluster Configure an application to read and write data by using DAX.
B. Create a three-node DynamoDB Accelerator (DAX) cluster. Configure an application to read data by using DAX and to write data directly to the DynamoDB table.
C. Create a three-node DynamoDB Accelerator (DAX) cluster. Configure an application to read data directly from the DynamoDB table and to write data by using DAX.
D. Create a single-node DynamoD8 Accelerator (DAX) cluster. Configure an application to read data by using DAX and to write data directly to the DynamoD8 table.
Explanation: A DAX cluster can be deployed with one or two nodes for development or test workloads. One- and two-node clusters are not fault-tolerant, and we don't recommend using fewer than three nodes for production use. If a one- or two-node cluster encounters software or hardware errors, the cluster can become unavailable or lose cached data.A DAX cluster can be deployed with one or two nodes for development or test workloads. One- and two-node clusters are not fault-tolerant, and we don't recommend using fewer than three nodes for production use. If a one- or two-node cluster encounters software or hardware errors, the cluster can become unavailable or lose cached data.
A company is running an application in the AWS Cloud. The company's security team must
approve the creation of all new IAM users. When a new IAM user is created, all access for
the user must be removed automatically. The security team must then receive a notification
to approve the user. The company has a multi-Region AWS CloudTrail trail In the AWS
account.
Which combination of steps will meet these requirements? (Select THREE.)
A. Create an Amazon EventBridge (Amazon CloudWatch Events) rule. Define a pattern with the detail-type value set to AWS API Call via CloudTrail and an eventName of CreateUser.
B. Configure CloudTrail to send a notification for the CreateUser event to an Amazon Simple Notification Service (Amazon SNS) topic.
C. Invoke a container that runs in Amazon Elastic Container Service (Amazon ECS) with AWS Fargate technology to remove access
D. Invoke an AWS Step Functions state machine to remove access.
E. Use Amazon Simple Notification Service (Amazon SNS) to notify the security team.
F. Use Amazon Pinpoint to notify the security team.
A company is in the process of implementing AWS Organizations to constrain its
developers to use only Amazon EC2. Amazon S3 and Amazon DynamoDB. The
developers account resides In a dedicated organizational unit (OU). The solutions architect
has implemented the following SCP on the developers account:
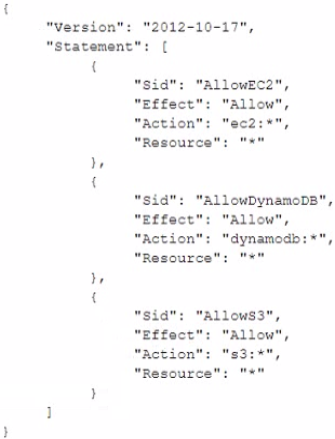
When this policy is deployed, IAM users in the developers account are still able to use
AWS services that are not listed in the policy. What should the solutions architect do to
eliminate the developers' ability to use services outside the scope of this policy?
A. Create an explicit deny statement for each AWS service that should be constrained
B. Remove the Full AWS Access SCP from the developer account's OU
C. Modify the Full AWS Access SCP to explicitly deny all services
D. Add an explicit deny statement using a wildcard to the end of the SCP
A software as a service (SaaS) based company provides a case management solution to
customers A3 part of the solution. The company uses a standalone Simple Mail Transfer
Protocol (SMTP) server to send email messages from an application. The application also
stores an email template for acknowledgement email messages that populate customer
data before the application sends the email message to the customer.
The company plans to migrate this messaging functionality to the AWS Cloud and needs to
minimize operational overhead.
Which solution will meet these requirements MOST cost-effectively?
A. Set up an SMTP server on Amazon EC2 instances by using an AMI from the AWS Marketplace. Store the email template in an Amazon S3 bucket. Create an AWS Lambda function to retrieve the template from the S3 bucket and to merge the customer data from the application with the template. Use an SDK in the Lambda function to send the email message.
B. Set up Amazon Simple Email Service (Amazon SES) to send email messages. Store the email template in an Amazon S3 bucket. Create an AWS Lambda function to retrieve the template from the S3 bucket and to merge the customer data from the application with the template. Use an SDK in the Lambda function to send the email message
C. Set up an SMTP server on Amazon EC2 instances by using an AMI from the AWS Marketplace. Store the email template in Amazon Simple Email Service (Amazon SES) with parameters for the customer data. Create an AWS Lambda function to call the SES template and to pass customer data to replace the parameters. Use the AWS Marketplace SMTP server to send the email message.
D. Set up Amazon Simple Email Service (Amazon SES) to send email messages. Store the email template on Amazon SES with parameters for the customer data. Create an AWS Lambda function to call the SendTemplatedEmail API operation and to pass customer data to replace the parameters and the email destination.
Explanation: In this solution, the company can use Amazon SES to send email messages, which will minimize operational overhead as SES is a fully managed service that handles sending and receiving email messages. The company can store the email template on Amazon SES with parameters for the customer data and use an AWS Lambda function to call the SendTemplatedEmail API operation, passing in the customer data to replace the parameters and the email destination. This solution eliminates the need to set up and manage an SMTP server on EC2 instances, which can be costly and time-consuming.
A health insurance company stores personally identifiable information (PII) in an Amazon
S3 bucket. The company uses server-side encryption with S3 managed encryption keys
(SSE-S3) to encrypt the objects. According to a new requirement, all current and future
objects in the S3 bucket must be encrypted by keys that the company’s security team
manages. The S3 bucket does not have versioning enabled.
Which solution will meet these requirements?
A. In the S3 bucket properties, change the default encryption to SSE-S3 with a customer managed key. Use the AWS CLI to re-upload all objects in the S3 bucket. Set an S3 bucket policy to deny unencrypted PutObject requests.
B. In the S3 bucket properties, change the default encryption to server-side encryption with AWS KMS managed encryption keys (SSE-KMS). Set an S3 bucket policy to deny unencrypted PutObject requests. Use the AWS CLI to re-upload all objects in the S3 bucket.
C. In the S3 bucket properties, change the default encryption to server-side encryption with AWS KMS managed encryption keys (SSE-KMS). Set an S3 bucket policy to automatically encrypt objects on GetObject and PutObject requests.
D. In the S3 bucket properties, change the default encryption to AES-256 with a customer managed key. Attach a policy to deny unencrypted PutObject requests to any entities that access the S3 bucket. Use the AWS CLI to re-upload all objects in the S3 bucket.
A company is building a serverless application that runs on an AWS Lambda function that
is attached to a VPC. The company needs to integrate the application with a new service from an external provider. The external provider supports only requests that come from
public IPv4 addresses that are in an allow list.
The company must provide a single public IP address to the external provider before the
application can start using the new service.
Which solution will give the application the ability to access the new service?
A. Deploy a NAT gateway. Associate an Elastic IP address with the NAT gateway. Configure the VPC to use the NAT gateway.
B. Deploy an egress-only internet gateway. Associate an Elastic IP address with the egress-only internet gateway. Configure the elastic network interface on the Lambda function to use the egress-only internet gateway.
C. Deploy an internet gateway. Associate an Elastic IP address with the internet gateway. Configure the Lambda function to use the internet gateway.
D. Deploy an internet gateway. Associate an Elastic IP address with the internet gateway. Configure the default route in the public VPC route table to use the internet gateway.
Explanation: This solution will give the Lambda function access to the internet by routing
its outbound traffic through the NAT gateway, which has a public Elastic IP address. This
will allow the external provider to whitelist the single public IP address associated with the
NAT gateway, and enable the application to access the new service
Deploying a NAT gateway and associating an Elastic IP address with it, and then
configuring the VPC to use the NAT gateway, will give the application the ability to access
the new service. This is because the NAT gateway will be the single public IP address that
the external provider needs for the allow list. The NAT gateway will allow the application to
access the service, while keeping the underlying Lambda functions private.
When configuring NAT gateways, you should ensure that the route table associated with
the NAT gateway has a route to the internet gateway with a target of the internet gateway.
Additionally, you should ensure that the security group associated with the NAT gateway
allows outbound traffic from the Lambda functions.
A company's solutions architect is reviewing a new internally developed application in a
sandbox AWS account The application uses an AWS Auto Scaling group of Amazon EC2
instances that have an IAM instance profile attached Part of the application logic creates
and accesses secrets from AWS Secrets Manager The company has an AWS Lambda
function that calls the application API to test the functionality The company also has
created an AWS CloudTrail trail in the account
The application's developer has attached the SecretsManagerReadWnte AWS managed
IAM policy to an IAM role The IAM role is associated with the instance profile that is
attached to the EC2 instances The solutions architect has invoked the Lambda function for
testing
The solutions architect must replace the SecretsManagerReadWnte policy with a new
policy that provides least privilege access to the Secrets Manager actions that the
application requires
What is the MOST operationally efficient solution that meets these requirements?
A. Generate a policy based on CloudTrail events for the IAM role Use the generated policy output to create a new IAM policy Use the newly generated IAM policy to replace the SecretsManagerReadWnte policy that is attached to the IAM role
B. Create an analyzer in AWS Identity and Access Management Access Analyzer Use the IAM role's Access Advisor findings to create a new IAM policy Use the newly created IAM policy to replace the SecretsManagerReadWnte policy that is attached to the IAM role
C. Use the aws cloudtrail lookup-events AWS CLI command to filter and export CloudTrail events that are related to Secrets Manager Use a new IAM policy that contains the actions from CloudTrail to replace the SecretsManagerReadWnte policy that is attached to the IAM role
D. Use the IAM policy simulator to generate an IAM policy for the IAM role Use the newly generated IAM policy to replace the SecretsManagerReadWnte policy that is attached to the IAM role
Explanation: The IAM policy simulator will generate a policy that contains only the
necessary permissions for the application to access Secrets Manager, providing the least
privilege necessary to get the job done. This is the most efficient solution as it will not
require additional steps such as analyzing CloudTrail events or manually creating and
testing an IAM policy.
You can use the IAM policy simulator to generate an IAM policy for an IAM role by
specifying the role and the API actions and resources that the application or service
requires. The simulator will then generate an IAM policy that grants the least privilege
access to those actions and resources.
Once you have generated an IAM policy using the simulator, you can replace the existing
SecretsManagerReadWnte policy that is attached to the IAM role with the newly generated
policy. This will ensure that the application or service has the least privilege access to the Secrets Manager actions that it requires.
You can access the IAM policy simulator through the IAM console, AWS CLI, and AWS
SDKs.
A solutions architect has developed a web application that uses an Amazon API Gateway
Regional endpoint and an AWS Lambda function. The consumers of the web application
are all close to the AWS Region where the application will be deployed. The Lambda
function only queries an Amazon Aurora MySQL database. The solutions architect has
configured the database to have three read replicas.
During testing, the application does not meet performance requirements. Under high load,
the application opens a large number of database connections. The solutions architect
must improve the application's performance.
Which actions should the solutions architect take to meet these requirements? (Choose
two.)
A. Use the cluster endpoint of the Aurora database.
B. Use RDS Proxy to set up a connection pool to the reader endpoint of the Aurora database.
C. Use the Lambda Provisioned Concurrency feature.
D. Move the code for opening the database connection in the Lambda function outside of the event handler.
E. Change the API Gateway endpoint to an edge-optimized endpoint.
A company has created an OU in AWS Organizations for each of its engineering teams Each OU owns multiple AWS accounts. The organization has hundreds of AWS accounts A solutions architect must design a solution so that each OU can view a breakdown of usage costs across its AWS accounts. Which solution meets these requirements?
A. Create an AWS Cost and Usage Report (CUR) for each OU by using AWS Resource Access Manager Allow each team to visualize the CUR through an Amazon QuickSight dashboard.
B. Create an AWS Cost and Usage Report (CUR) from the AWS Organizations management account- Allow each team to visualize the CUR through an Amazon QuickSight dashboard
C. Create an AWS Cost and Usage Report (CUR) in each AWS Organizations member account Allow each team to visualize the CUR through an Amazon QuickSight dashboard.
D. Create an AWS Cost and Usage Report (CUR) by using AWS Systems Manager Allow each team to visualize the CUR through Systems Manager OpsCenter dashboards
A company wants to use a third-party software-as-a-service (SaaS) application. The thirdparty
SaaS application is consumed through several API calls. The third-party SaaS
application also runs on AWS inside a VPC.
The company will consume the third-party SaaS application from inside a VPC. The
company has internal security policies that mandate the use of private connectivity that
does not traverse the internet. No resources that run in the company VPC are allowed to
be accessed from outside the company’s VPC. All permissions must conform to the
principles of least privilege.
Which solution meets these requirements?
A. Create an AWS PrivateLink interface VPC endpoint. Connect this endpoint to the endpoint service that the third-party SaaS application provides. Create a security group to limit the access to the endpoint. Associate the security group with the endpoint.
B. Create an AWS Site-to-Site VPN connection between the third-party SaaS application and the company VPC. Configure network ACLs to limit access across the VPN tunnels.
C. Create a VPC peering connection between the third-party SaaS application and the company VPUpdate route tables by adding the needed routes for the peering connection.
D. Create an AWS PrivateLink endpoint service. Ask the third-party SaaS provider to create an interface VPC endpoint for this endpoint service. Grant permissions for the endpoint service to the specific account of the third-party SaaS provider.
| Page 8 out of 41 Pages |
| Previous |