Your company has a single Virtual Private Cloud (VPC) network deployed in Google Cloud
with access from on-premises locations using Cloud Interconnect connections. Your
company must be able to send traffic to Cloud Storage only through the Interconnect links
while accessing other Google APIs and services over the public internet. What should you
do?
A.
Use the default public domains for all Google APIs and services.
B.
Use Private Service Connect to access Cloud Storage, and use the default public
domains for all other Google APIs and services.
C.
Use Private Google Access, with restricted.googleapis.com virtual IP addresses for
Cloud Storage and private.googleapis.com for all other Google APIs and services.
D.
Use Private Google Access, with private.googleapis.com virtual IP addresses for Cloud
Storage and restricted.googleapis.com virtual IP addresses for all other Google APIs and
services.
Use Private Service Connect to access Cloud Storage, and use the default public
domains for all other Google APIs and services.
You work for a university that is migrating to Google Cloud.
These are the cloud requirements:
On-premises connectivity with 10 Gbps
Lowest latency access to the cloud
Centralized Networking Administration Team
New departments are asking for on-premises connectivity to their projects. You want to
deploy the most cost-efficient interconnect solution for connecting the campus to Google
Cloud.
What should you do?
A.
Use Shared VPC, and deploy the VLAN attachments and Dedicated Interconnect in the
host project.
B.
Use Shared VPC, and deploy the VLAN attachments in the service projects. Connect
the VLAN attachment to the Shared VPC's host project.
C.
Use standalone projects, and deploy the VLAN attachments in the individual projects.
Connect the VLAN attachment to the standalone projects' Dedicated Interconnects.
D.
Use standalone projects and deploy the VLAN attachments and Dedicated
Interconnects in each of the individual projects.
Use Shared VPC, and deploy the VLAN attachments and Dedicated Interconnect in the
host project.
You need to enable Cloud CDN for all the objects inside a storage bucket. You want to
ensure that all the object in the storage bucket can be served by the CDN.
What should you do in the GCP Console?
A.
Create a new cloud storage bucket, and then enable Cloud CDN on it.
B.
Create a new TCP load balancer, select the storage bucket as a backend, and then
enable Cloud CDN on the backend.
C.
Create a new SSL proxy load balancer, select the storage bucket as a backend, and
then enable Cloud CDN on the backend.
D.
Create a new HTTP load balancer, select the storage bucket as a backend, enable
Cloud CDN on the backend, and make sure each object inside the storage bucket is
shared publicly.
Create a new HTTP load balancer, select the storage bucket as a backend, enable
Cloud CDN on the backend, and make sure each object inside the storage bucket is
shared publicly.
You have an application running on Compute Engine that uses BigQuery to generate some
results that are stored in Cloud Storage. You want to ensure that none of the application
instances have external IP addresses.
Which two methods can you use to accomplish this? (Choose two.)
A.
Enable Private Google Access on all the subnets
B.
Enable Private Google Access on the VPC.
C.
Enable Private Services Access on the VPC
D.
Create network peering between your VPC and BigQuery
E.
Create a Cloud NAT, and route the application traffic via NAT gateway
Enable Private Google Access on all the subnets
Create a Cloud NAT, and route the application traffic via NAT gateway
You have the following firewall ruleset applied to all instances in your Virtual Private Cloud
(VPC):
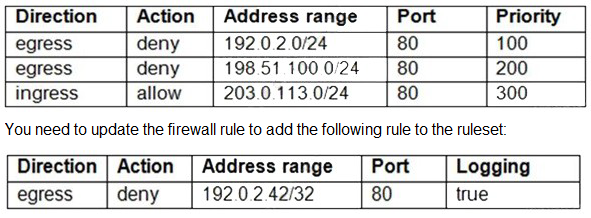
You are using a new user account. You must assign the appropriate identity and Access
Management (IAM) user roles to this new user account before updating the firewall rule.
The new user account must be able to apply the update and view firewall logs. What
should you do?
A.
Assign the compute.securityAdmin and logging.viewer rule to the new user account.
Apply the new firewall rule with a priority of 50.
B.
Assign the compute.securityAdmin and logging.bucketWriter role to the new user
account. Apply the new firewall rule with a priority of 150.
C.
Assign the compute.orgSecurityPolicyAdmin and logging.viewer role to the new user
account. Apply the new firewall rule with a priority of 50.
D.
Assign the compute.orgSecurityPolicyAdmin and logging.bucketWriter role to the new
user account. Apply the new firewall rule with a priority of 150.
Assign the compute.securityAdmin and logging.viewer rule to the new user account.
Apply the new firewall rule with a priority of 50.
You need to establish network connectivity between three Virtual Private Cloud networks,
Sales, Marketing, and Finance, so that users can access resources in all three VPCs. You
configure VPC peering between the Sales VPC and the Finance VPC. You also configure
VPC peering between the Marketing VPC and the Finance VPC. After you complete the
configuration, some users cannot connect to resources in the Sales VPC and the Marketing
VPC. You want to resolve the problem.
What should you do?
A.
Configure VPC peering in a full mesh.
B.
Alter the routing table to resolve the asymmetric route
C.
Create network tags to allow connectivity between all three VPCs.
D.
Delete the legacy network and recreate it to allow transitive peering.
Configure VPC peering in a full mesh.
Your company has a single Virtual Private Cloud (VPC) network deployed in Google Cloud
with access from your on-premises network using Cloud Interconnect. You must configure
access only to Google APIs and services that are supported by VPC Service Controls
through hybrid connectivity with a service level agreement (SLA) in place. What should you
do?
A.
Configure the existing Cloud Routers to advertise the Google API's public virtual IP
addresses.
B.
Use Private Google Access for on-premises hosts with restricted.googleapis.com virtual
IP addresses.
C.
Configure the existing Cloud Routers to advertise a default route, and use Cloud NAT to
translate traffic from your on-premises network.
D.
Add Direct Peering links, and use them for connectivity to Google APIs that use public
virtual IP addresses.
Use Private Google Access for on-premises hosts with restricted.googleapis.com virtual
IP addresses.
You want to configure a NAT to perform address translation between your on-premises
network blocks and GCP.
Which NAT solution should you use?
A.
Cloud NAT
B.
An instance with IP forwarding enabled
C.
An instance configured with iptables DNAT rules
D.
An instance configured with iptables SNAT rules
Cloud NAT
You are responsible for enabling Private Google Access for the virtual machine (VM)
instances in your Virtual Private Cloud (VPC) to access Google APIs. All VM instances
have only a private IP address and need to access Cloud Storage. You need to ensure that
all VM traffic is routed back to your on-premises data center for traffic scrubbing via your
existing Cloud Interconnect connection. However, VM traffic to Google APIs should remain
in the VPC. What should you do?
A.
Delete the default route in your VPC.
Create a private Cloud DNS zone for googleapis.com, create a CNAME for
*.googleapis.com to restricted googleapis.com, and create an A record for restricted
googleapis com that resolves to the addresses in 199.36.153.4/30.
Create a static route in your VPC for the range 199.36.153.4/30 with the default internet
gateway as the next hop.
B.
Delete the default route in your VPC and configure your on-premises router to advertise
0.0.0.0/0 via Border Gateway Protocol (BGP).
Create a public Cloud DNS zone with a CNAME for *.google.com to private googleapis
com, create a CNAME for * googleapis.com to private googleapis com, and create an A
record for Private googleapis.com that resolves to the addresses in 199.36.153 8/30.
Create a static route in your VPC for the range 199 .36.153.8/30 with the default internet
gateway as the next hop.
C.
Configure your on-premises router to advertise 0.0.0.0/0 via Border Gateway Protocol
(BGP) with a lower priority (MED) than the default VPC route.
Create a private Cloud DNS zone for googleapis.com, create a CNAME for *
googieapis.com to private googleapis com, and create an A record for
private.googleapis.com that resolves to the addresses in 199 .36.153.8/30.
Create a static route in your VPC for the range 199.36. 153.8/30 with the default internet
gateway as the next hop.
D.
Delete the default route in your VPC and configure your on-premises router to advertise
0.0.0.0/0 via Border Gateway Protocol (BGP).
Create a private Cloud DNS zone for googleapis.com, create a CNAME for *
googieapis.com to Private googleapis.com, and create an A record for
private.googleapis.com that resolves to the addresses in 199.36.153.8/30.
Create a static route in your VPC for the range 199.36.153.8/30 with the default internet
gateway as the next hop.
Configure your on-premises router to advertise 0.0.0.0/0 via Border Gateway Protocol
(BGP) with a lower priority (MED) than the default VPC route.
Create a private Cloud DNS zone for googleapis.com, create a CNAME for *
googieapis.com to private googleapis com, and create an A record for
private.googleapis.com that resolves to the addresses in 199 .36.153.8/30.
Create a static route in your VPC for the range 199.36. 153.8/30 with the default internet
gateway as the next hop.
You have just deployed your infrastructure on Google Cloud. You now need to configure
the DNS to meet the following requirements:
Your on-premises resources should resolve your Google Cloud zones.
Your Google Cloud resources should resolve your on-premises zones.
You need the ability to resolve “.internal” zones provisioned by Google Cloud.
What should you do?
A.
Configure an outbound server policy, and set your alternative name server to be your
on-premises DNS resolver. Configure your on-premises DNS resolver to forward Google
Cloud zone queries to Google's public DNS 8.8.8.8.
B.
Configure both an inbound server policy and outbound DNS forwarding zones with the
target as the on-premises DNS resolver. Configure your on-premises DNS resolver to
forward Google Cloud zone queries to Google Cloud's DNS resolver.
C.
Configure an outbound DNS server policy, and set your alternative name server to be
your on-premises DNS resolver. Configure your on-premises DNS resolver to forward
Google Cloud zone queries to Google Cloud's DNS resolver.
D.
Configure Cloud DNS to DNS peer with your on-premises DNS resolver. Configure your
on-premises DNS resolver to forward Google Cloud zone queries to Google's public DNS
8.8.8.8.
Configure an outbound server policy, and set your alternative name server to be your
on-premises DNS resolver. Configure your on-premises DNS resolver to forward Google
Cloud zone queries to Google's public DNS 8.8.8.8.
You need to create a new VPC network that allows instances to have IP addresses in both
the 10.1.1.0/24 network and the 172.16.45.0/24 network.
What should you do?
A.
Configure global load balancing to point 172.16.45.0/24 to the correct instance.
B.
Create unique DNS records for each service that sends traffic to the desired IP address.
C.
Configure an alias-IP range of 172.16.45.0/24 on the virtual instances within the VPC subnet of 10.1.1.0/24.
D.
Use VPC peering to allow traffic to route between the 10.1.0.0/24 network and the
172.16.45.0/24 network.
Configure an alias-IP range of 172.16.45.0/24 on the virtual instances within the VPC subnet of 10.1.1.0/24.
You need to ensure your personal SSH key works on every instance in your project. You
want to accomplish this as efficiently as possible.
What should you do?
A.
Upload your public ssh key to the project Metadata
B.
Upload your public ssh key to each instance Metadata.
C.
Create a custom Google Compute Engine image with your public ssh key embedded
D.
Use gcloud compute ssh to automatically copy your public ssh key to the instance
Upload your public ssh key to the project Metadata
Overview By creating and managing SSH keys, you can let users access a Linux instance
through third-party tools. An SSH key consists of the following files: A public SSH key file
that is applied to instance-level metadata or project-wide metadata. A private SSH key file
that the user stores on their local devices. If a user presents their private SSH key, they
can use a third-party tool to connect to any instance that is configured with the matching
public SSH key file, even if they aren't a member of your Google Cloud project. Therefore,
you can control which instances a user can access by changing the public SSH key
metadata for one or more instances.
https://cloud.google.com/compute/docs/instances/adding-removing-ssh-keys#addkey
| Page 3 out of 13 Pages |
| Previous |