Topic 2: Misc. Questions
You have containerized a legacy application that stores its configuration on an NFS share. You need to deploy this application to Google Kubernetes Engine (GKE) and do not want the application serving traffic until after the configuration has been retrieved. What should you do?
A. Use the gsutil utility to copy files from within the Docker container at startup, and start the service using an ENTRYPOINT script.
B. Create a PersistentVolumeClaim on the GKE cluster. Access the configuration files from the volume, and start the service using an ENTRYPOINT script.
C. Use the COPY statement in the Dockerfile to load the configuration into the container image. Verify that the configuration is available, and start the service using an ENTRYPOINT script.
D. Add a startup script to the GKE instance group to mount the NFS share at node startup. Copy the configuration files into the container, and start the service using an ENTRYPOINT script.
Your application performs well when tested locally, but it runs significantly slower when you deploy it to App Engine standard environment. You want to diagnose the problem. What should you do?
A. File a ticket with Cloud Support indicating that the application performs faster locally.
B. Use Stackdriver Debugger Snapshots to look at a point-in-time execution of the application.
C. Use Stackdriver Trace to determine which functions within the application have higher latency.
D. Add logging commands to the application and use Stackdriver Logging to check where the latency problem occurs.
You are building a new API. You want to minimize the cost of storing and reduce the latency of serving images. Which architecture should you use?
A. App Engine backed by Cloud Storage
B. Compute Engine backed by Persistent Disk
C. Transfer Appliance backed by Cloud Filestore
D. Cloud Content Delivery Network (CDN) backed by Cloud Storage
Your company’s corporate policy states that there must be a copyright comment at the very beginning of all source files. You want to write a custom step in Cloud Build that is triggered by each source commit. You need the trigger to validate that the source contains a copyright and add one for subsequent steps if not there. What should you do?
A. Build a new Docker container that examines the files in /workspace and then checks and adds a copyright for each source file. Changed files are explicitly committed back to the source repository.
B. Build a new Docker container that examines the files in /workspace and then checks and adds a copyright for each source file. Changed files do not need to be committed back to the source repository.
C. Build a new Docker container that examines the files in a Cloud Storage bucket and then checks and adds a copyright for each source file. Changed files are written back to the Cloud Storage bucket.
D. Build a new Docker container that examines the files in a Cloud Storage bucket and then checks and adds a copyright for each source file. Changed files are explicitly committed back to the source repository.
You are developing an ecommerce web application that uses App Engine standard
environment and Memorystore for Redis. When a user logs into the app, the application
caches the user’s information (e.g., session, name, address, preferences), which is stored
for quick retrieval during checkout.
While testing your application in a browser, you get a 502 Bad Gateway error. You have
determined that the application is not connecting to Memorystore. What is the reason for
this error?
A. Your Memorystore for Redis instance was deployed without a public IP address
B. You configured your Serverless VPC Access connector in a different region than your App Engine instance.
C. The firewall rule allowing a connection between App Engine and Memory store was removed during an infrastructure update by the DevOps team.
D. You configured your application to use a Serverless VPC Access connector on a different subnet in a different availability zone than your App Engine instance.
Your company's development teams want to use Cloud Build in their projects to build and push Docker images to Container Registry. The operations team requires all Docker images to be published to a centralized, securely managed Docker registry that the operations team manages. What should you do?
A. Use Container Registry to create a registry in each development team's project. Configure the Cloud Build build to push the Docker image to the project's registry. Grant the operations team access to each development team's registry.
B. Create a separate project for the operations team that has Container Registry configured. Assign appropriate permissions to the Cloud Build service account in each developer team's project to allow access to the operation team's registry.
C. Create a separate project for the operations team that has Container Registry configured. Create a Service Account for each development team and assign the appropriate permissions to allow it access to the operations team's registry. Store the service account key file in the source code repository and use it to authenticate against the operations team's registry.
D. Create a separate project for the operations team that has the open source Docker Registry deployed on a Compute Engine virtual machine instance. Create a username and password for each development team. Store the username and password in the source code repository and use it to authenticate against the operations team's Docker registry.
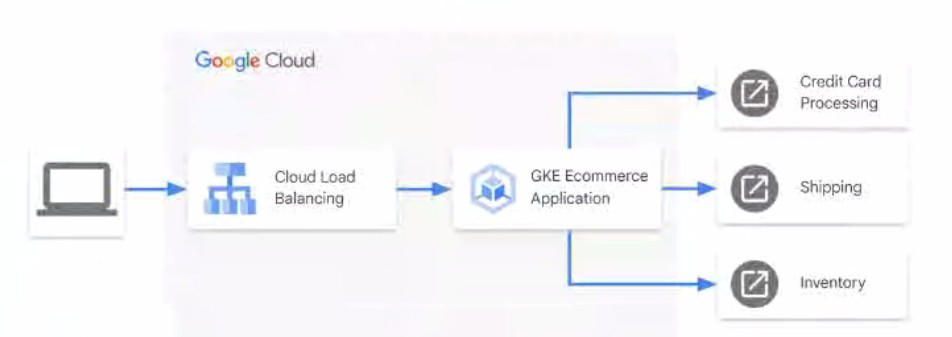
You have an ecommerce application hosted in Google Kubernetes Engine (GKE) that
receives external requests and forwards them to third-party APIs external to Google Cloud.
The third-party APIs are responsible for credit card processing, shipping, and inventory
management using the process shown in the diagram.
Your customers are reporting that the ecommerce application is running slowly at
unpredictable times. The application doesn't report any metrics You need to determine the
cause of the inconsistent performance What should you do?
A. Install the Ops Agent inside your container and configure it to gather application metrics.
B. Install the OpenTelemetry library for your respective language, and instrument your application.
C. Modify your application to read and forward the x-Cloud-Trace-context header when it calls the downstream services.
D. Enable Managed Service for Prometheus on the GKE cluster to gather application metrics.
You work at a rapidly growing financial technology startup. You manage the payment
processing application written in Go and hosted on Cloud Run in the Singapore region
(asia-southeast1). The payment processing application processes data stored in a Cloud
Storage bucket that is also located in the Singapore region.
The startup plans to expand further into the Asia Pacific region. You plan to deploy the
Payment Gateway in Jakarta, Hong Kong, and Taiwan over the next six months. Each
location has data residency requirements that require customer data to reside in the
country where the transaction was made. You want to minimize the cost of these
deployments. What should you do?
A. Create a Cloud Storage bucket in each region, and create a Cloud Run service of the payment processing application in each region.
B. Create a Cloud Storage bucket in each region, and create three Cloud Run services of the payment processing application in the Singapore region.
C. Create three Cloud Storage buckets in the Asia multi-region, and create three Cloud Run services of the payment processing application in the Singapore region.
D. Create three Cloud Storage buckets in the Asia multi-region, and create three Cloud Run revisions of the payment processing application in the Singapore region.
Your web application is deployed to the corporate intranet. You need to migrate the web application to Google Cloud. The web application must be available only to company employees and accessible to employees as they travel. You need to ensure the security and accessibility of the web application while minimizing application changes. What should you do?
A. Configure the application to check authentication credentials for each HTTP(S) request to the application.
B. Configure Identity-Aware Proxy to allow employees to access the application through its public IP address.
C. Configure a Compute Engine instance that requests users to log in to their corporate account. Change the web application DNS to point to the proxy Compute Engine instance. After authenticating, the Compute Engine instance forwards requests to and from the web application.
D. Configure a Compute Engine instance that requests users to log in to their corporate account. Change the web application DNS to point to the proxy Compute Engine instance. After authenticating, the Compute Engine issues an HTTP redirect to a public IP address hosting the web application.
You are developing a microservice-based application that will run on Google Kubernetes Engine (GKE). Some of the services need to access different Google Cloud APIs. How should you set up authentication of these services in the cluster following Google recommended best practices? (Choose two.)
A. Use the service account attached to the GKE node.
B. Enable Workload Identity in the cluster via the gcloud command-line tool.
C. Access the Google service account keys from a secret management service.
D. Store the Google service account keys in a central secret management service.
E. Use gcloud to bind the Kubernetes service account and the Google service account using roles/iam.workloadIdentity.
Users are complaining that your Cloud Run-hosted website responds too slowly during traffic spikes. You want to provide a better user experience during traffic peaks. What should you do?
A. Read application configuration and static data from the database on application startup.
B. Package application configuration and static data into the application image during build time.
C. Perform as much work as possible in the background after the response has been returned to the user.
D. Ensure that timeout exceptions and errors cause the Cloud Run instance to exit quickly so a replacement instance can be started.
Your company has a BigQuery dataset named "Master" that keeps information about employee travel and expenses. This information is organized by employee department. That means employees should only be able to view information for their department. You want to apply a security framework to enforce this requirement with the minimum number of steps. What should you do?
A. Create a separate dataset for each department. Create a view with an appropriate WHERE clause to select records from a particular dataset for the specific department. Authorize this view to access records from your Master dataset. Give employees the permission to this department-specific dataset.
B. Create a separate dataset for each department. Create a data pipeline for each department to copy appropriate information from the Master dataset to the specific dataset for the department. Give employees the permission to this department-specific dataset.
C. Create a dataset named Master dataset. Create a separate view for each department in the Master dataset. Give employees access to the specific view for their department.
D. Create a dataset named Master dataset. Create a separate table for each department in the Master dataset. Give employees access to the specific table for their department.
| Page 5 out of 22 Pages |
| Previous |