A firewall administrator needs to check which egress interface the firewall will use to route the IP 10.2.5.3. Which command should they use?
A. test routing route ip 10.2.5.3 *
B. test routing route ip 10.2.5.3 virtual-router default
C. test routing fib-lookup ip 10.2.5.0/24 virtual-router default
D. test routing fib-lookup ip 10.2.5.3 virtual-router default
Explanation: To determine the egress interface a Palo Alto Networks firewall will use to route a specific IP address, the appropriate command is test routing fib-lookup ip 10.2.5.3 virtual-router default. This command performs a Forwarding Information Base (FIB) lookup for the specified IP address within the context of the specified virtual router, which in this case is the default virtual router. The FIB lookup process checks the routing table and the associated forwarding information to determine the next-hop and the egress interface for the given IP address. This command is instrumental for troubleshooting and verifying routing decisions made by the firewall to ensure that traffic is routed as expected through the network infrastructure.
Which two actions must an engineer take to configure SSL Forward Proxy decryption? (Choose two.)
A. Configure the decryption profile
B. Define a Forward Trust Certificate
C. Configure SSL decryption rules
D. Configure a SSL/TLS service profile
Explanation: To configure SSL Forward Proxy decryption on a Palo Alto Networks firewall,
certain key components must be set up to ensure secure and effective decryption and
inspection of SSL/TLS encrypted traffic:
B. Define a Forward Trust Certificate:
A Forward Trust Certificate is essential for SSL Forward Proxy decryption. This
certificate is used by the firewall to dynamically generate certificates for SSL sites
that are trusted. When the firewall decrypts and inspects the traffic and then re-encrypts
it, the new certificate presented to the client comes from the Forward
Trust Certificate authority. This certificate must be trusted by client devices, often
requiring the Forward Trust CA certificate to be distributed and installed on client
devices.
C. Configure SSL decryption rules:
SSL decryption rules are the policies that determine which traffic is to be
decrypted. These rules specify the source, destination, service, and URL category,
among other criteria. The rules define what traffic the SSL Forward Proxy will
apply to, enabling selective decryption based on security and privacy
requirements.
Together, these components form the basis of the SSL Forward Proxy decryption setup,
allowing for the decryption, inspection, and re-encryption of SSL/TLS encrypted traffic to
identify and prevent threats hidden within encrypted sessions.
What type of address object would be useful for internal devices where the addressing structure assigns meaning to certain bits in the address, as illustrated in the diagram?
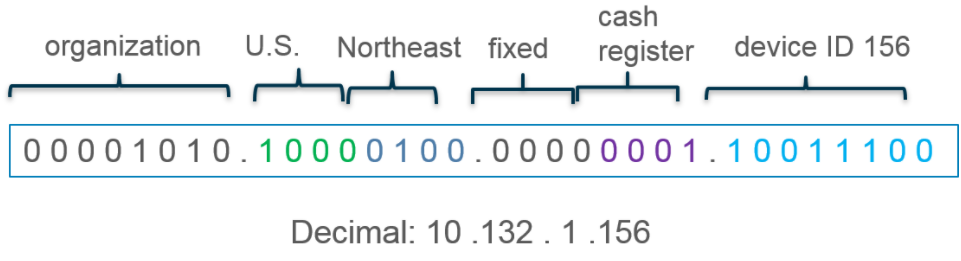
A. IP Netmask
B. IP Wildcard Mask
C. IP Address
D. IP Range
What does SSL decryption require to establish a firewall as a trusted third party and to establish trust between a client and server to secure an SSL/TLS connection'?
A. certificates
B. profiles
C. link state
D. stateful firewall connection
Which log type would provide information about traffic blocked by a Zone Protection profile?
A. Data Filtering
B. IP-Tag
C. Traffic
D. Threat
Explanation: D is the correct answer because the threat log type would provide information about traffic blocked by a Zone Protection profile. This is because Zone Protection profiles are used to protect the network from attacks, including common flood, reconnaissance attacks, and other packet-based attacks1. These attacks are classified as threats by the firewall and are logged in the threat log2. The threat log displays information such as the source and destination IP addresses, ports, zones, applications, threat types, actions, and severity of the threats2.
A network security administrator wants to begin inspecting bulk user HTTPS traffic flows egressing out of the internet edge firewall. Which certificate is the best choice to configure as an SSL Forward Trust certificate?
A. A self-signed Certificate Authority certificate generated by the firewall
B. A Machine Certificate for the firewall signed by the organization's PKI
C. A web server certificate signed by the organization's PKI
D. A subordinate Certificate Authority certificate signed by the organization's PKI
Explanation: Regardless of whether you generate Forward Trust certificates from your Enterprise Root CA or use a self-signed certificate generated on the firewall, generate a separate subordinate Forward Trust CA certificate for each firewall. The flexibility of using separate subordinate CAs enables you to revoke one certificate when you decommission a device (or device pair) without affecting the rest of the deployment and reduces the impact in any situation in which you need to revoke a certificate. Separate Forward Trust CAs on each firewall also helps troubleshoot issues because the CA error message the user sees includes information about the firewall the traffic is traversing. If you use the same Forward Trust CA on every firewall, you lose the granularity of that information.
An administrator is assisting a security engineering team with a decryption rollout for inbound and forward proxy traffic. Incorrect firewall sizing is preventing the team from decrypting all of the traffic they want to decrypt. Which three items should be prioritized for decryption? (Choose three.)
A. Financial, health, and government traffic categories
B. Known traffic categories
C. Known malicious IP space
D. Public-facing servers,
E. Less-trusted internal IP subnets
An administrator is troubleshooting intermittent connectivity problems with a user's GlobalProtect connection. Packet captures at the firewall reveal missing UDP packets, suggesting potential packet loss on the connection. The administrator aims to resolve the issue by enforcing an SSL tunnel over TCP specifically for this user. What configuration change is necessary to implement this troubleshooting solution for the user?
A. Enable SSL tunnel within the GlobalProtect gateway remote user's settings.
B. Modify the user's client to prioritize UDP traffic for GlobalProtect.
C. Enable SSL tunnel over TCP in a new agent configuration for the specific user.
D. Increase the user's VPN bandwidth allocation in the GlobalProtect settings.
When you import the configuration of an HA pair into Panorama, how do you prevent the import from affecting ongoing traffic?
A. Set the passive link state to shutdown".
B. Disable config sync.
C. Disable the HA2 link.
D. Disable HA.
Explanation:
To prevent the import from affecting ongoing traffic when you import the configuration of an HA pair into Panorama, you should disable config sync on both firewalls. Config sync is a
feature that enables the firewalls in an HA pair to synchronize their configurations and
maintain consistency. However, when you import the configuration of an HA pair into
Panorama, you want to avoid any changes to the firewall configuration until you verify and
commit the imported configuration on Panorama. Therefore, you should disable config sync
before importing the configuration, and re-enable it after committing the changes on
Panorama12.
References: Migrate a Firewall HA Pair to Panorama Management, PCNSE
Study Guide (page 50)
An administrator configures a site-to-site IPsec VPN tunnel between a PA-850 and an external customer on their policy-based VPN devices. What should an administrator configure to route interesting traffic through the VPN tunnel?
A. Proxy IDs
B. GRE Encapsulation
C. Tunnel Monitor
D. ToS Header
Which source is the most reliable for collecting User-ID user mapping?
A. Syslog Listener
B. Microsoft Exchange
C. Microsoft Active Directory
D. GlobalProtect
Refer to the exhibit.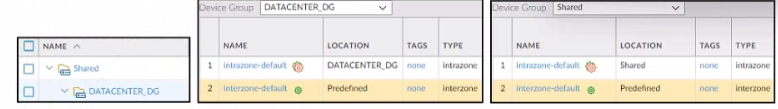
Based on the screenshots above what is the correct order in which the various rules are
deployed to firewalls inside the DATACENTER_DG device group?
A. shared pre-rules
DATACENTER DG pre rules
rules configured locally on the firewall
shared post-rules
DATACENTER_DG post-rules
DATACENTER.DG default rules
B. shared pre-rules
DATACENTER_DG pre-rules
rules configured locally on the firewall
shared post-rules
DATACENTER.DG post-rules
shared default rules
C. shared pre-rules
DATACENTER_DG pre-rules
rules configured locally on the firewall
DATACENTER_DG post-rules
shared post-rules
shared default rules
D. shared pre-rules
DATACENTER_DG pre-rules
rules configured locally on the firewall
DATACENTER_DG post-rules
shared post-rules
DATACENTER_DG default rules
| Page 6 out of 27 Pages |
| Previous |