Which two profiles should be configured when sharing tags from threat logs with a remote User-ID agent? (Choose two.)
A. Log Ingestion
B. HTTP
C. Log Forwarding
D. LDAP
Explanation: >Threat logs, create a log forwarding profile to define how you want the firewall or Panorama to handle logs. >Configure an HTTP server profile to forward logs to a remote User-ID agent. > Select the log forwarding profile you created then select this server profile as the HTTP server profile https://docs.paloaltonetworks.com/pan-os/11- 0/pan-os-admin/policy/use-auto-tagging-to-automate-security-actions
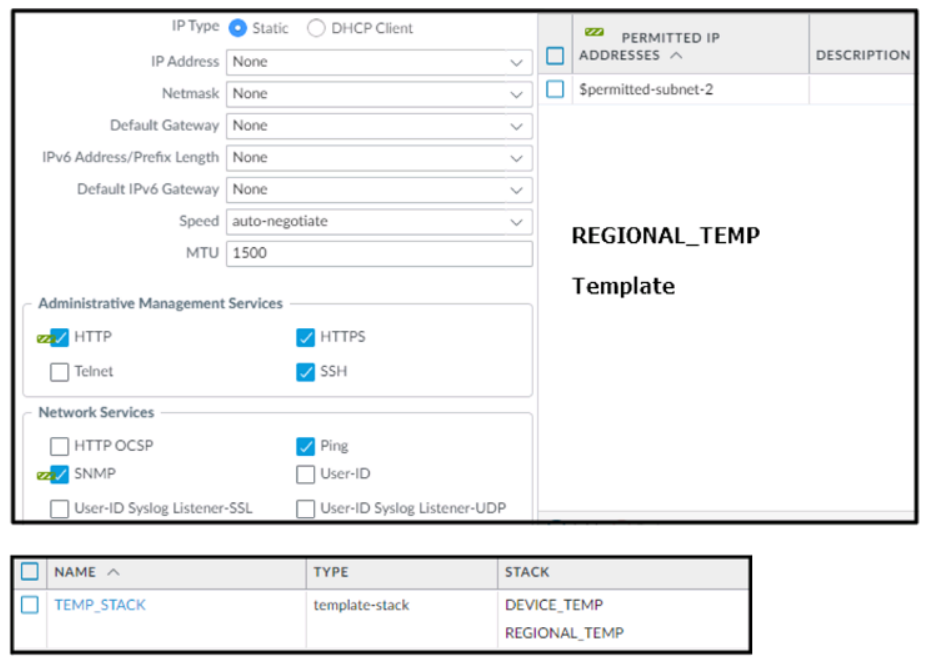
Based on the screenshots above, and with no configuration inside the Template Stack
itself, what access will the device permit on its Management port?
A. The firewall will allow HTTP Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-1.
B. The firewall will allow HTTP Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-2.
C. The firewall will allow HTTP, Telnet, SNMP, HTTPS, SSH and Ping from IP addresses defined as $permitted-subnet-1 and $permitted-subnet-2.
D. The firewall will allow HTTP, Telnet, HTTPS, SSH, and Ping from IP addresses defined as $permitted-subnet-1 and $permitted-subnet-2.
Explanation: https://live.paloaltonetworks.com/t5/panorama-discussions/panorama-force-template-valueoption/ td-p/496620 "- Force Template Value will as the name suggest remove any local configuratio and apply the value define the panorama template. But this is valid only for overlapping configuration" "You need to be careful, what is actually defined in the template. For example - if you decide to enable HA in the template, but after that you decide to not push it with template and just disable it again (remove the check from the "Enable HA" checkbox). This still will be part of the template, because now your template is explicitely defining HA disabled. If you made a change in the template, and later decide that you don't want to control this setting with template, you need to revert the config by clicking the green bar next to the changed value"
Which CLI command displays the physical media that are connected to ethernet1/8?
A. > show system state filter-pretty sys.si. p8. stats
B. > show system state filter-pretty sys.sl.p8.phy
C. > show system state filter-pretty sys.sl.p8.med
D. > show interface ethernet1/8
Explanation: The CLI command "show system state filter-pretty sys.sl.p8.phy" is used to display detailed physical layer information, which would include the physical media connected to a specific interface such as ethernet1/8. This command is designed to filter the output to show relevant physical layer information for the specified interface. For more information on Palo Alto Networks CLI commands and their outputs, refer to the "PAN-OS® CLI Reference Guide".
After implementing a new NGFW, a firewall engineer sees a VoIP traffic issue going through the firewall After troubleshooting the engineer finds that the firewall performs NAT on the voice packets payload and opens dynamic pinholes for media ports What can the engineer do to solve the VoIP traffic issue?
A. Disable ALG under H.323 application
B. Increase the TCP timeout under H.323 application
C. Increase the TCP timeout under SIP application
D. Disable ALG under SIP application
Following a review of firewall logs for traffic generated by malicious activity, how can an administrator confirm that WildFire has identified a virus?
A. By navigating to Monitor > Logs > WildFire Submissions, applying filter "(subtype eq wildfire-virus)"
B. By navigating to Monitor > Logs > Threat, applying filter "(subtype eq wildfire-virus)'
C. By navigating to Monitor > Logs > Traffic, applying filter "(subtype eq virus)"
D. By navigating to Monitor > Logs> Threat, applying filter "(subtype eq virus)"
A company requires that a specific set of ciphers be used when remotely managing their Palo Alto Networks appliances. Which profile should be configured in order to achieve this?
A. SSH Service profile
B. SSL/TLS Service profile
C. Certificate profile
D. Decryption profile
Explanation: SSL/TLS profile is only the TLS versions, not ciphers. Decryption Profile is
for SSL Inbound and Forward Proxy applications, not mgmt of the PANW Firewall. There's
also KB articles to strengthen SSH, but I couldn't find any for HTTPS, on the mgmt
interface:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA14u0000004OOQCA
2&lang=en_US%E2%80%A9
An engineer creates a set of rules in a Device Group (Panorama) to permit traffic to various services for a specific LDAP user group. What needs to be configured to ensure Panorama can retrieve user and group information for use in these rules?
A. A service route to the LDAP server
B. A Master Device
C. Authentication Portal
D. A User-ID agent on the LDAP server
A decryption policy has been created with an action of "No Decryption." The decryption profile is configured in alignment to best practices. What protections does this policy provide to the enterprise?
A. It allows for complete visibility into certificate data, ensuring secure connections to all websites.
B. It ensures that the firewall checks its certificate store, enabling sessions with trusted self-signed certificates even when an alternative trust anchor exists.
C. It encrypts all certificate information to maintain privacy and compliance with local regulations.
D. It enhances security by actively blocking access to potentially insecure sites with expired certificates or untrusted issuers.
Review the screenshots.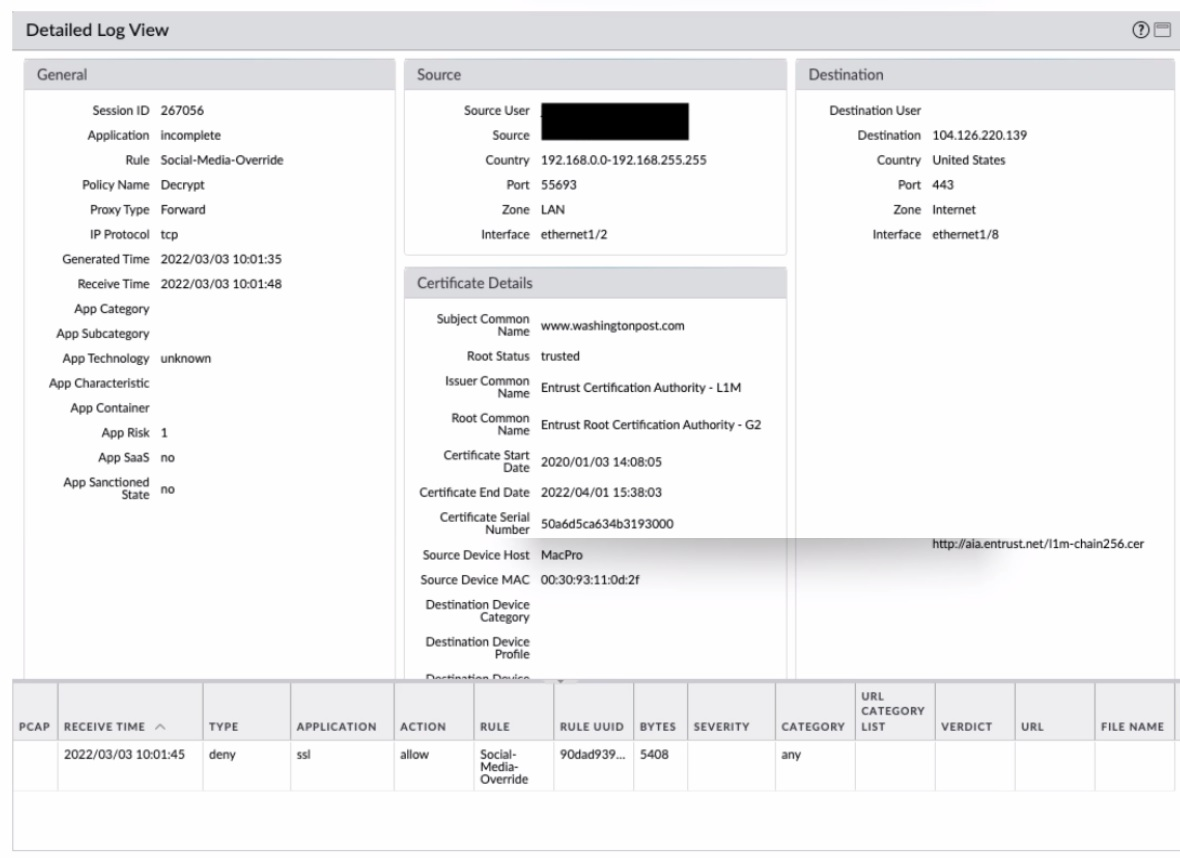
What is the most likely reason for this decryption error log?
A. The Certificate fingerprint could not be found.
B. The client expected a certificate from a different CA than the one provided.
C. The client received a CA certificate that has expired or is not valid.
D. Entrust is not a trusted root certificate authority (CA).
An administrator needs to build Security rules in a Device Group that allow traffic to specific users and groups defined in Active Directory. What must be configured in order to select users and groups for those rules from Panorama?
A. A User-ID Certificate profile must be configured on Panorama.
B. The Security rules must be targeted to a firewall in the device group and have Group Mapping configured.
C. User-ID Redistribution must be configured on Panorama to ensure that all firewalls have the same mappings.
D. A master device with Group Mapping configured must be set in the device group where the Security rules are configured.
Explanation: When building Security rules in a Device Group that need to allow traffic to
specific users and groups defined in Active Directory, it's essential to have user and group
information available in Panorama to select these entities for the rules.
D. A master device with Group Mapping configured must be set in the device group
where the Security rules are configured:
The concept of a "master device" in Panorama refers to a specific firewall that is
designated to provide certain settings or information, such as user and group
mappings from Active Directory, to Panorama. This information can then be used
across other firewalls within the same device group.
By configuring Group Mapping on a master device, Panorama can leverage this
information to populate user and group objects. These objects can then be used in
Security rules within the device group, allowing for the creation of policies that are
based on user identity and group membership, as defined in Active Directory.
This setup ensures that Panorama has the necessary context to apply user- and
group-based policies accurately across the managed firewalls, facilitating
centralized management and consistency in policy enforcement.
A consultant advises a client on designing an explicit Web Proxy deployment on PAN-OS 11 0 The client currently uses RADIUS authentication in their environment. Which two pieces of information should the consultant provide regarding Web Proxy authentication? (Choose two.)
A. Kerberos or SAML authentication need to be configured
B. LDAP or TACACS+ authentication need to be configured
C. RADIUS is only supported for a transparent Web Proxy.
D. RADIUS is not supported for explicit or transparent Web Proxy
Explanation: For explicit Web Proxy deployment on PAN-OS, Palo Alto Networks currently supports Kerberos and SAML as authentication methods. RADIUS is not supported for explicit or transparent Web Proxy authentication on Palo Alto Networks appliances, which means that if the client is currently using RADIUS, they will need to configure an alternate supported authentication method. LDAP or TACACS+ authentication is not directly supported for Web Proxy authentication in PAN-OS.For more information on supported Web Proxy authentication methods, please refer to the latest Palo Alto Networks "PANOS ® Web Interface Reference Guide".
An engineer is configuring a firewall with three interfaces:
A. Set DNS and Palo Alto Networks Services to use the ethernet1/1 source interface.
B. Set DNS and Palo Alto Networks Services to use the ethernet1/2 source interface.
C. Set DNS and Palo Alto Networks Services to use the MGT source interface.
D. Set DDNS and Palo Alto Networks Services to use the MGT source interface.
| Page 3 out of 27 Pages |
| Previous |