In which two scenarios would it be necessary to use Proxy IDs when configuring site-to-site VPN Tunnels? (Choose two.)
A. Firewalls which support policy-based VPNs.
B. The remote device is a non-Palo Alto Networks firewall.
C. Firewalls which support route-based VPNs.
D. The remote device is a Palo Alto Networks firewall.
What action does a firewall take when a Decryption profile allows unsupported modes and unsupported traffic with TLS 1.2 protocol traverses the firewall?
A. It blocks all communication with the server indefinitely.
B. It downgrades the protocol to ensure compatibility.
C. It automatically adds the server to the SSL Decryption Exclusion list
D. It generates an decryption error message but allows the traffic to continue decryption
A security team has enabled real-time WildFire signature lookup on all its firewalls. Which additional action will further reduce the likelihood of newly discovered malware being allowed through the firewalls?
A. increase the frequency of the applications and threats dynamic updates.
B. Increase the frequency of the antivirus dynamic updates
C. Enable the "Hold Mode" option in Objects > Security Profiles > Antivirus
D. Enable the "Report Grayware Files" option in Device > Setup > WildFire.
An administrator is creating a new Dynamic User Group to quarantine users for suspicious activity. Which two objects can Dynamic User Groups use as match conditions for group membership? (Choose two.)
A. Source IP address
B. Dynamic tags
C. Static tags
D. Ldap attributes
A company has recently migrated their branch office's PA-220S to a centralized Panorama. This Panorama manages a number of PA-7000 Series and PA-5200 Series devices All device group and template configuration is managed solely within Panorama. They notice that commit times have drastically increased for the PA-220S after the migration. What can they do to reduce commit times?
A. Disable "Share Unused Address and Service Objects with Devices" in Panorama Settings.
B. Update the apps and threat version using device-deployment
C. Perform a device group push using the "merge with device candidate config" option
D. Use "export or push device config bundle" to ensure that the firewall is integrated with the Panorama config.
An enterprise Information Security team has deployed policies based on AD groups to restrict user access to critical infrastructure systems. However, a recent phishing campaign against the organization has prompted Information Security to look for more controls that can secure access to critical assets. For users that need to access these systems. Information Security wants to use PAN-OS multi-factor authentication (MFA) integration to enforce MFA. What should the enterprise do to use PAN-OS MFA?
A. Configure a Captive Portal authentication policy that uses an authentication sequence.
B. Configure a Captive Portal authentication policy that uses an authentication profile that references a RADIUS profile.
C. Create an authentication profile and assign another authentication factor to be used by a Captive Portal authentication policy.
D. Use a Credential Phishing agent to detect, prevent, and mitigate credential phishing campaigns.
An engineer needs to collect User-ID mappings from the company's existing proxies. What two methods can be used to pull this data from third party proxies? (Choose two.)
A. Client probing
B. Syslog
C. XFF Headers
D. Server Monitoring
Explanation: To collect User-ID information from third-party proxies, Palo Alto Networks supports several methods of integrating user information. Syslog parsing allows the firewall to receive syslog messages from external services, parse them, and extract user information. X-Forwarded-For (XFF) headers, which are used in HTTP requests and proxies, can carry the original IP address of a client connecting through a proxy, and this information can be used by the firewall to map the user IDs. Syslog is commonly used for integrating third-party devices like proxies with User-ID, and XFF headers are specifically mentioned in the context of integrating user mappings from HTTP traffic. Client probing and Server Monitoring are not the correct methods for pulling data from third-party proxies. For further details, refer to the Palo Alto Networks documentation on User-ID integration and the "PAN-OS® Administrator’s Guide".
A firewall administrator is configuring an IPSec tunnel between Site A and Site B. The Site
A firewall uses a DHCP assigned address on the outside interface of the firewall, and the
Site B firewall uses a static IP address assigned to the outside interface of the firewall.
However, the use of dynamic peering is not working.
Refer to the two sets of configuration settings provided. Which two changes will allow the
configurations to work? (Choose two.)
Site A configuration: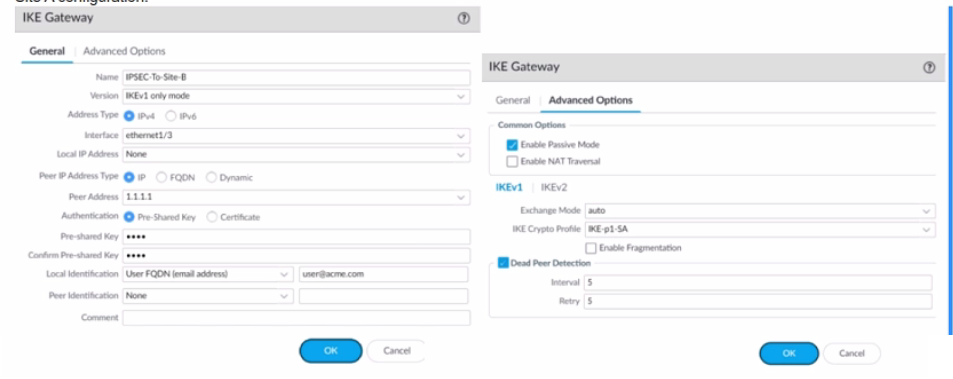
A. Enable NAT Traversal on Site B firewall
B. Configure Local Identification on Site firewall
C. Disable passive mode on Site A firewall
D. Match IKE version on both firewalls.
Explanation: The image shows an IKE Gateway configuration where Site B is set to IKEv1
only mode, and passive mode is not enabled. For dynamic peering to work when Site A is
using a DHCP assigned address:
Passive mode on Site A needs to be disabled. In passive mode, the firewall will not
initiate the IKE negotiation and will only respond to negotiation requests from the
peer. Since Site A has a dynamic IP, it must be able to initiate the connection to
Site B, which has a static IP.
Matching the IKE version between Site A and Site B is also necessary for
successful IPSec tunnel establishment. Since Site B is set to IKEv1 only mode,
Site A also needs to be configured to use IKEv1 to ensure that both sites are using
the same version for the IKE negotiation process.
NAT Traversal is used when there are NAT devices between the two endpoints, but there's
no indication that this is the case here. Additionally, local identification on Site A is not
necessarily related to the issue with dynamic peering not working.
A root cause analysis investigation into a recent security incident reveals that several decryption rules have been disabled. The security team wants to generate email alerts when decryption rules are changed. How should email log forwarding be configured to achieve this goal?
A. With the relevant configuration log filter inside Device > Log Settings
B. With the relevant system log filter inside Objects > Log Forwarding
C. With the relevant system log filter inside Device > Log Settings
D. With the relevant configuration log filter inside Objects > Log Forwarding
Explanation: To generate email alerts when decryption rules are changed in a Palo Alto
Networks firewall, you would configure email log forwarding based on specific system logs
that capture changes to decryption policies. This is done by setting up log forwarding
profiles with filters that match events related to decryption rule modifications. These profiles
are then applied to the relevant log types within the firewall's log settings.
To specifically monitor for changes to decryption rules, you would navigate to the Device >
Log Settings section of the firewall's web interface. Here, you can configure log forwarding
for system logs, which capture configuration changes among other system-level events. By
creating a filter that looks for logs associated with decryption rule changes, and associating
this filter with an email server profile, the firewall can automatically send out email alerts
whenever a decryption rule is modified.
A network security engineer is going to enable Zone Protection on several security zones How can the engineer ensure that Zone Protection events appear in the firewall's logs?
A. Select the check box "Log packet-based attack events" in the Zone Protection profile
B. No action is needed Zone Protection events appear in the threat logs by default
C. Select the check box "Log Zone Protection events" in the Content-ID settings of the firewall
D. Access the CLI in each firewall and enter the command set system setting additionalthreat- log on
A firewall administrator has been tasked with ensuring that all Panorama configuration is committed and pushed to the devices at the end of the day at a certain time. How can they achieve this?
A. Use the Scheduled Config Push to schedule Commit to Panorama and also Push to Devices.
B. Use the Scheduled Config Push to schedule Push to Devices and separately schedule an API call to commit all Panorama changes.
C. Use the Scheduled Config Export to schedule Push to Devices and separately schedule an API call to commit all Panorama changes
D. Use the Scheduled Config Export to schedule Commit to Panorama and also Push to Devices
An administrator is attempting to create policies tor deployment of a device group and template stack. When creating the policies, the zone drop down list does not include the required zone. What must the administrator do to correct this issue?
A. Specify the target device as the master device in the device group
B. Enable "Share Unused Address and Service Objects with Devices" in Panorama settings
C. Add the template as a reference template in the device group
D. Add a firewall to both the device group and the template
Explanation: In order to see what is in a template, the device-group needs the template referenced. Even if you add the firewall to both the template and device-group, the device-group will not see what is in the template. The following link has a video that demonstrates that B is the correct answer.
| Page 11 out of 27 Pages |
| Previous |