Refer to the exhibit, which shows a network diagram.

Which IPsec phase 2 configuration should you impalement so that only one remote site is connected at any time?
A. Set route-overlap to allow.
B. Set single-source to enable
C. Set route-overlap to either use—new or use-old
D. Set net-device to enable
Refer to the exhibit, which shows an error in system fortiguard configuration.
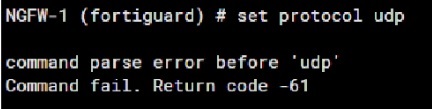
What is the reason you cannot set the protocol to udp in config system fortiguard?
A. udp is not a protocol option.
B. fortiguard-anycast is set to enable. Most Voted.
C. You do not have the corresponding write access.
D. FortiManager provides FortiGuard.
Which two statements about the neighbor-group command are true? (Choose two.)
A. It applies common settings in an OSPF area
B. You can apply it in Internal BGP (IBGP) and External BGP (EBGP)
C. You can configure it on the GUI
D. It is combined with the neighbor-range parameter
Which two statements about IKE version 2 fragmentation are true? (Choose two.)
A. Only some IKE version 2 packets are considered fragmentable
B. The reassembly timeout default value is 30 seconds
C. It is performed at the IP layer
D. The maximum number of IKE version 2 fragments is 128
Which statement about network processor (NP) offloading is true?
A. For TCP traffic FortiGate CPU offloads the first packets of SYN/ACK and ACK of the three-way handshake to NP
B. The NP provides IPS signature matching
C. You can disable the NP for each firewall policy using the command np-acceleration st to loose.
D. The NP checks the session key or IPSec SA
Explanation:
Network processors (NPs) are specialized hardware within FortiGate devices that accelerate certain security functions. One of the primary functions of NPs is to provide IPS signature matching (B), allowing for high-speed inspection of traffic against a database of known threat signatures.
Refer to the exhibit, which shows a custom signature.
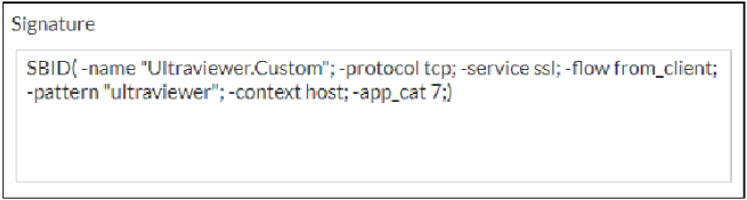
Which two modifications must you apply to the configuration of this custom signature so that you can save it on FortiGate? (Choose two.)
A. Ensure that the header syntax is F-SBID.
B. Add severity.
C. Add attack_id.
D. Start options with --.
You contoured an address object on the tool fortiGate in a Security Fabric. This object is not synchronized with a downstream device. Which two reasons could be the cause? (Choose two)
A. The address object on the tool FortiGate has fabric-object set to disable
B. The root FortiGate has configuration-sync set to enable
C. The downstream TortiGate has fabric-object-unification set to local
D. The downstream FortiGate has configuration-sync set to local
Explanation:
Option A is correct because the address object on the tool FortiGate will not be synchronized with the downstream devices if it has fabric-object set to disable. This option controls whether the address object is shared with other FortiGate devices in the Security Fabric or not1.
Option C is correct because the downstream FortiGate will not receive the address object from the tool FortiGate if it has fabric-object-unification set to local. This option controls whether the downstream FortiGate uses the address objects from the root FortiGate or its own local address objects2.
Option B is incorrect because the root FortiGate has configuration-sync set to enable by default, which means that it will synchronize the address objects with the downstream devices unless they are disabled by the fabric-object option3.
Option D is incorrect because the downstream FortiGate has configuration-sync set to local by default, which means that it will receive the address objects from the root FortiGate unless they are overridden by the fabric-object-unification option4.
References: =
1: Group address objects synchronized from FortiManager5
2: Security Fabric address object unification6
3: Configuration synchronization7
4: Configuration synchronization7
: Security Fabric - Fortinet Documentation
What are two functions of automation stitches? (Choose two.)
A. Automation stitches can be created to run diagnostic commands and email the results when CPU or memory usage exceeds specified thresholds.
B. An automation stitch configured to execute actions in parallel can be set to insert a specific delay between actions.
C. Automation stitches can be configured on any FortiGate device in a Security Fabric environment.
D. An automation stitch configured to execute actions sequentially can take parameters from previous actions as input for the current action.
Which ADVPN configuration must be configured using a script on fortiManager, when using VPN Manager to manage fortiGate VPN tunnels?
A. Enable AD-VPN in IPsec phase 1
B. Disable add-route on hub
C. Configure IP addresses on IPsec virtual interlaces
D. Set protected network to all
Explanation:
To enable AD-VPN, you need to edit an SD-WAN overlay template and enable the Auto-Discovery VPN toggle. This will automatically add the required settings to the IPsec template and the BGP template. You cannot enable AD-VPN directly in the IPsec phase 1 settings using VPN Manager.
References := ADVPN | FortiManager 7.2.0 - Fortinet Documentation
Which two statements about IKE vision 2 are true? (Choose two.)
A. Phase 1 includes main mode
B. It supports the extensible authentication protocol (EAP)
C. It supports the XAuth protocol.
D. It exchanges a minimum of four messages to establish a secure tunnel
Explanation:
IKE version 2 supports the extensible authentication protocol (EAP), which allows for more flexible and secure authentication methods1. IKE version 2 also exchanges a minimum of four messages to establish a secure tunnel, which is more efficient than IKE version 12. References: = IKE settings | FortiClient 7.2.2 - Fortinet Documentation, Technical Tip: How to configure IKE version 1 or 2 … - Fortinet Community
You want to improve reliability over a lossy IPSec tunnel. Which combination of IPSec phase 1 parameters should you configure?
A. fec-ingress and fec-egress
B. Odpd and dpd-retryinterval
C. fragmentation and fragmentation-mtu
D. keepalive and keylive
Explanation:
For improving reliability over a lossy IPSec tunnel, the fragmentation and fragmentation-mtu parameters should be configured. In scenarios where there might be issues with packet size or an unreliable network, setting the IPsec phase 1 to allow for fragmentation will enable large packets to be broken down, preventing them from being dropped due to size or poor network quality. The fragmentation-mtu specifies the size of the fragments. This is aligned with Fortinet's recommendations for handling IPsec VPN over networks with potential packet loss or size limitations.
Which two statements about the Security fabric are true? (Choose two.)
A. FortiGate uses the FortiTelemetry protocol to communicate with FortiAnatyzer.
B. Only the root FortiGate sends logs to FortiAnalyzer
C. Only FortiGate devices with configuration-sync receive and synchronize global CMDB objects that the toot FortiGate sends
D. Only the root FortiGate collects network topology information and forwards it to FortiAnalyzer
Explanation:
In the Security Fabric, only the root FortiGate sends logs to FortiAnalyzer (B). Additionally, only FortiGate devices withconfiguration-syncenabled receive and synchronize global Central Management Database (CMDB) objects that the root FortiGate sends (C). FortiGate uses the FortiTelemetry protocol to communicate with other FortiGates, not FortiAnalyzer (A). The last option (D) is incorrect as all FortiGates can collect and forward network topology information to FortiAnalyzer.
References:
FortiOS Handbook - Security Fabric
| Page 1 out of 6 Pages |