A company plans to deploy a solution to manage its Windows 10 computers. Some
computers are connected to the corporate network and some computers are connected to
the internet,
The solution must meet the following requirements:
Deploy an operating system to the computers.
Join the computer to an on-premises Active Directory domain.
Install Windows updates to the computers.
You need to identify a solution that meets the requirements.
Which solution should you choose?
A.
Microsoft Endpoint Manager
B.
Microsoft Intune
C.
Windows Autopilot
D.
Configuration Manager
Microsoft Endpoint Manager
Endpoint Manager includes the services and tools you use to manage and monitor mobile
devices, desktop computers, virtual machines, embedded devices, and servers. Endpoint
Manager combines services, including Microsoft Intune, Configuration Manager, Desktop
Analytics, co-management, and Windows Autopilot.
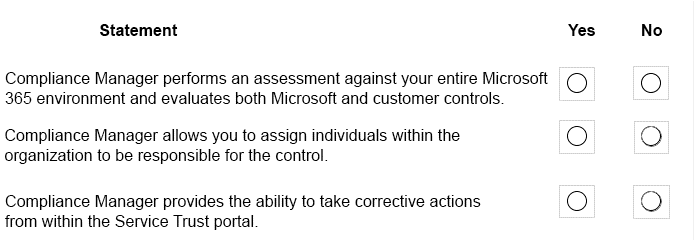
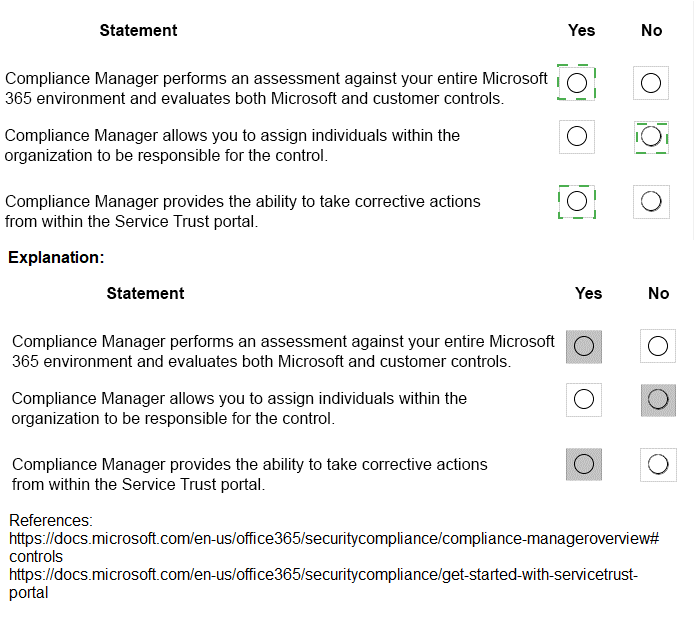
For each of the following statements, select Yes if the statement is true. Otherwise, select
No.
NOTE: Each correct selection is worth pone point.
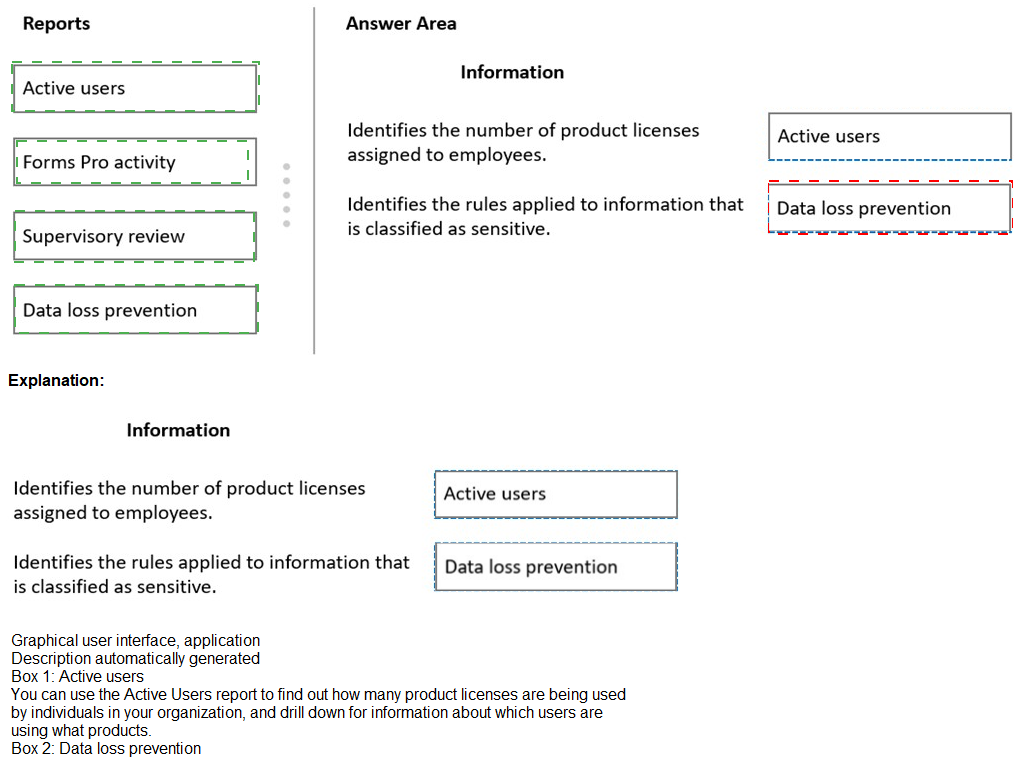
You need to identify which reports provide the information that the company requests.
Which reports should you select? To answer, drag the appropriate reports to the correct
type of information. Each report may be used once, more than once, or not at all. You may
need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

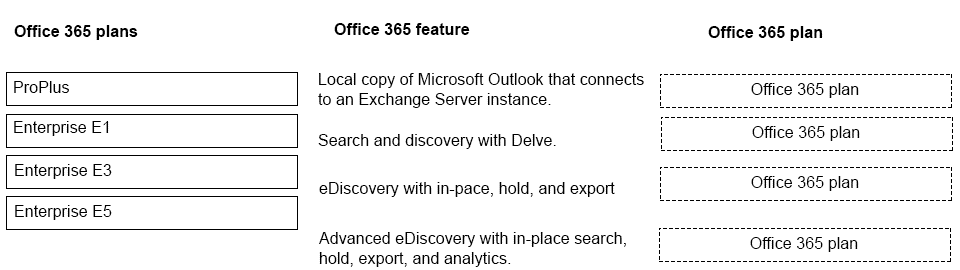
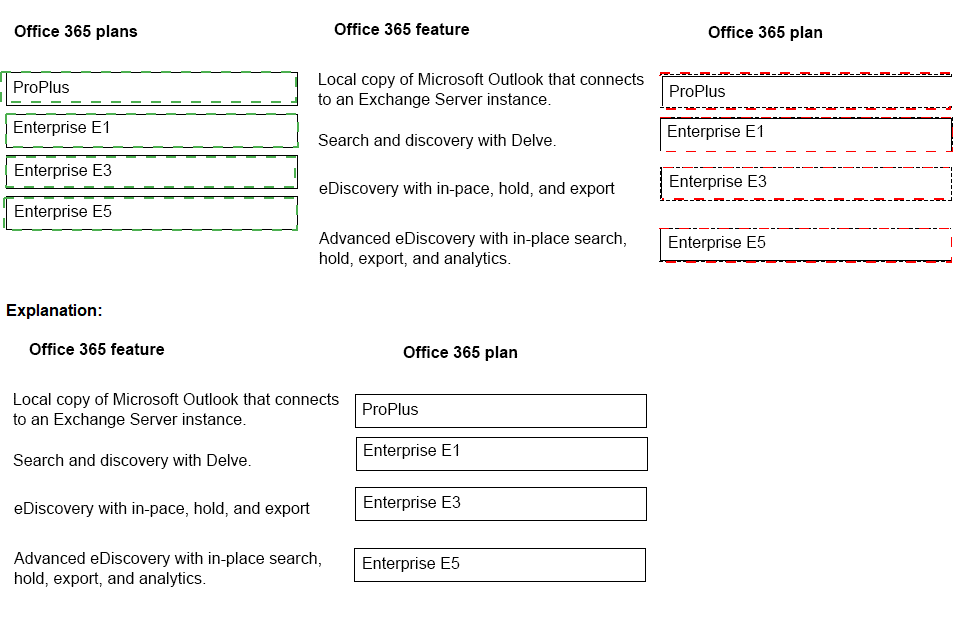
You are a Microsoft 365 administrator for a company.
You need to recommend an-appropriate Microsoft Office 365 plan for a customer that
minimizes costs.
Which subscription plans should you recommend? To answer, drag the appropriate plans
to the correct features. Each plan may be used once, more than once, or not at all.
NOTE: Each correct selection is worth one point.
A company plans to implement an insider risk solution in Microsoft 365.
The company needs to implement a solution that meets the following requirements:
• Uses machine learning to identify email risks.
• Provides workflows to remediate email risks.
• Provides a dashboard to display email risks, actions, and trends.
You need to identify a solution that meets the requirements. Which solution should you
select?
A.
Core eDiscovery cases
B.
Sensitivity labels
C.
Communication compliance policies
D.
Advanced eDiscovery cases
Communication compliance policies
This question requires that you evaluate the bold text to determine if it is correct.
A company needs to protect documents and emails by automatically applying
classifications and labels. You must minimize costs. You should implement Microsoft Azure
Information Protection for Microsoft Office 365.
Review the underlined text If it makes the statement correct select No change is needed. If
the statement is incorrect, select the answer choice that makes the statement correct.
A.
No change needed
B.
Azure Information Protection Premium P2
C.
Azure Information Protection Premium PI
D.
Microsoft 365 E3
Azure Information Protection Premium P2
You need to determine the release date of Microsoft 365 features.
What should you use?
A.
Office Deployment Tool release history
B.
Microsoft 365 admin center
C.
Microsoft System Center
D.
Microsoft 365 Roadmap
E.
Windows Insider program
Microsoft 365 Roadmap
You deploy Enterprise Mobility + Security E5 and assign Microsoft 365 licenses to all
employees.
Employees must not be able to share documents at forward emails that contain sensitive
information outside the company.
You need to enforce the file sharing restrictions.
What should you do?
A.
Use Microsoft Azure Information Protection to define a label. Associate the label with an
Azure Rights Management template that prevents the sharing of files or emails that are
marked with the label.
B.
Create a Microsoft SharePoint Online content type named Sensitivity Apply the content
type to other content types in Microsoft. 356 a Microsoft Azure Rights Management
template that prevents the sharing of any content where the Sensitivity column value is set
to Sensitive.
C.
Use Microsoft Azure Information Rights Protection to define a label. Associate the label
with an Active Directory Rights Management template that prevents the sharing of files or
emails that are marked with the label.
D.
Create a label named Sensitive. Apply a Data Layer Protection policy that notifies users
when their document contains personally identifiable information (PII).
Use Microsoft Azure Information Protection to define a label. Associate the label with an
Azure Rights Management template that prevents the sharing of files or emails that are
marked with the label.
You are a Microsoft 365 administrator for a company. You use products that are in private
preview, public preview, or general availability (GA).
You need to determine at which phases you can receive support from the Microsoft 365
admin center.
For which product phase or phases can you receive support?
A.
GA, private preview, and public preview
B.
GA and private preview only
C.
GA only
D.
GA and public preview only
E.
public preview and private preview only
GA only
A company is evaluating Microsoft 365 services.
You need to determine which payment options are supported with a multiple profile. Which
three options are supported'' Each correct answer presents a complete solution. NOTE:
Each correct selection is worth one point.
A.
debit card
B.
credit card
C.
money order
D.
cash
E.
check
debit card
credit card
money order
A company is evaluating Microsoft 365.
You need to identify the collaboration features of OneDrive.
What are two collaboration features of OneDrive? Each correct answer presents part of the
solution.
NOTE: Each correct selection is worth one point.
A.
Inviting external users to an online meeting.
B.
Chatting with multiple users.
C.
Coauthoring of supported documents.
D.
Sharing files with external users.
Coauthoring of supported documents.
Sharing files with external users.
A company deploys Microsoft Azure AD. You run the Identity Secure Score report. The
report displays five security items. Which three security items on the report have the most
impact on the score? Each correct answer presents a complete solution. NOTE: Each
correct selection is worth one point.
A.
Enable policy to block legacy authentication.
B.
Enable user risk policy.
C.
Require multi-factor authentication for all users.
D.
Delete/block accounts not used in last 30 days.
E.
Do not expire passwords.
Enable policy to block legacy authentication.
Enable user risk policy.
Require multi-factor authentication for all users.
| Page 2 out of 26 Pages |
| Previous |