Topic 5, Misc. Questions
You have a Microsoft 365 tenant.
You plan to manage incidents in the tenant by using the Microsoft 365 security center.
Which Microsoft service source will appear on the Incidents page of the Microsoft 365 security center?
A.
Microsoft Defender for CloudUse the
B.
Microsoft Purview
C.
Azure Arc
D.
Microsoft Defender for Identity
Microsoft Defender for Identity
You have a Microsoft 365 subscription.
Your network uses an IP address space of 51.40.15.0/24.
An Exchange Online administrator recently created a role named Role1 from a computer on the network.
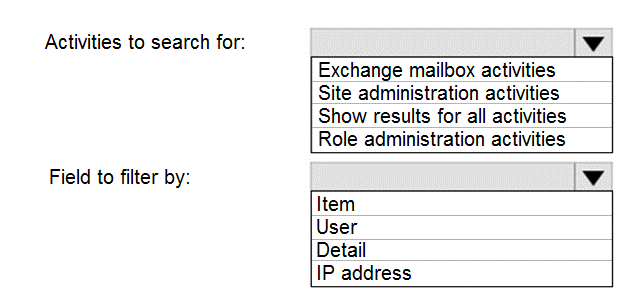
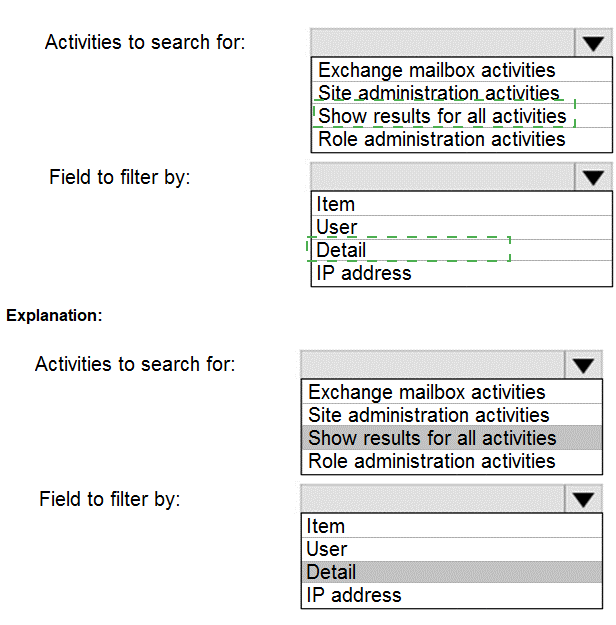
You need to identify the name of the administrator by using an audit log search.
For which activities should you search and by which field should you filter in the audit log search? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You create an account tor a new security administrator named SecAdmin1.
You need to ensure that SecAdmin1 can manage Microsoft Defender for Office 365 settings and policies for Microsoft Teams, SharePoint and OneDrive.
Solution: From the Azure Active Directory admin center, you assign SecAdmin1 the Teams Administrator role.
Does this meet the goal?
A.
Yes
B.
No
No
You have a Microsoft 365 E5 tenant that contains the resources shown in the following table.
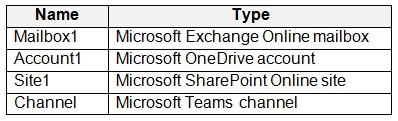
To which resources can you apply a sensitivity label by using an auto-labeling policy?
A.
Mailbox1 and Site1 only
B.
Mailbox1, Account1, and Site1 only
C.
Account1 and Site1 only
D.
Mailbox1, Account1, Site1, and Channel1
E.
Account1, Site1, and Channel1 only
Account1, Site1, and Channel1 only
You have a Microsoft 365 E5 subscription that contains the following user:
Name: User1
UPN: user1@contoso.com
Email address: user1@marketmg.contoso.com
MFA enrollment status: Disabled
When User1 attempts to sign in to Outlook on the web by using the user1@marketing.contoso.com email address, the user cannot sign in.
You need to ensure that User1 can sign in to Outlook on the web by using user1@marketing.contoso.com.
What should you do?
A.
Assign an MFA registration policy to User1.
B.
Reset the password of User1.
C.
Add an alternate email address for User1.
D.
Modify the UPN of User1.
Modify the UPN of User1.
Microsoft’s recommended best practices are to match UPN to primary SMTP address. This article addresses the small percentage of customers that cannot remediate UPN’s to match.
Note: A UPN is an Internet-style login name for a user based on the Internet standard RFC 822. The UPN is shorter than a distinguished name and easier to remember. By convention, this should map to the user's email name. The point of the UPN is toconsolidate the email and logon namespaces so that the user only needs to remember a single name.
Configure the Azure AD multifactor authentication registration policy Azure Active Directory (Azure AD) Identity Protection helps you manage the roll-out of Azure AD multifactor authentication (MFA) registration by configuring a Conditional Access policy to require MFA registration no matter what modern authentication app you're signing in to.
Reference:
https://docs.microsoft.com/en-us/windows/win32/ad/naming-properties#userprincipalname
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription that contains a user named User1.
You need to enable User1 to create Compliance Manager assessments.
Solution: From the Microsoft 365 compliance center, you add User1 to the Compliance Manager Assessors role group.
Does this meet the goal?
A.
Yes
B.
No
Yes
You have a Microsoft 365 subscription.
You suspect that several Microsoft Office 365 applications or services were recently updated.
You need to identify which applications or services were recently updated.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A.
From the Microsoft 365 admin center review the Service health blade
B.
From the Microsoft 365 admin center, review the Message center blade.
C.
From the Microsoft 365 admin center review the Products blade.
D.
From the Microsoft 365 Admin mobile agg, review the messages.
From the Microsoft 365 admin center, review the Message center blade.
From the Microsoft 365 Admin mobile agg, review the messages.
You have a Microsoft 365 subscription.
Your company has a customer ID associated to each customer. The customer IDs contain 10 numbers followed by 10 characters. The following is a sample customer ID: 12-456-7890-abc-defghij.
You plan to create a data loss prevention (DLP) policy that will detect messages containing customer IDs.
D18912E1457D5D1DDCBD40AB3BF70D5D
What should you create to ensure that the DLP policy can detect the customer IDs?
A.
a sensitive information type
B.
a sensitivity label
C.
a supervision policy
D.
a retention label
a sensitive information type
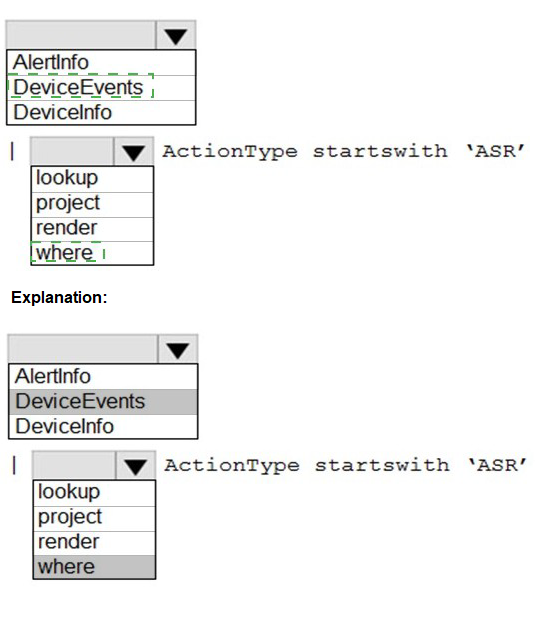
You have a Microsoft 365 E5 tenant that contains 100 Windows 10 devices.
You plan to attack surface reduction (ASR) rules for the Windows 10 devices.
You configure the ASR rules in audit mode and collect audit data in a Log Analytics workspace.
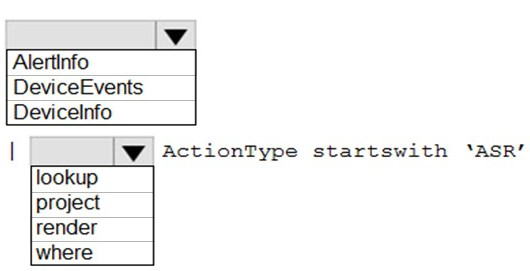
You need to find the ASR rules that match the activities on the devices.
How should you complete the Kusto query? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
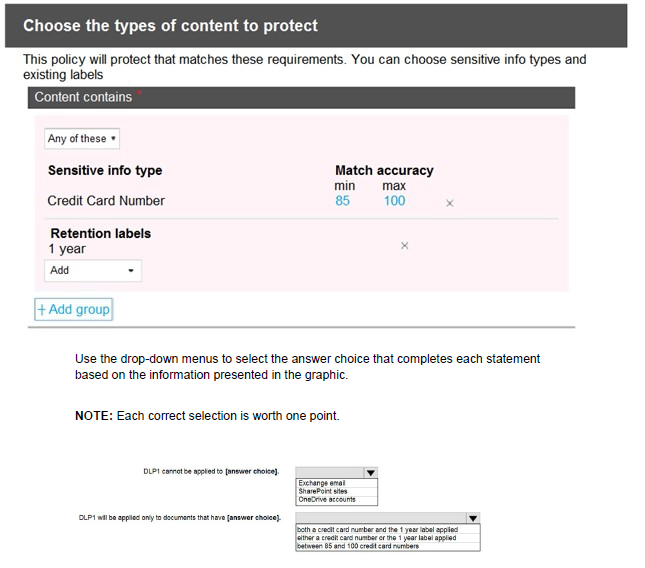
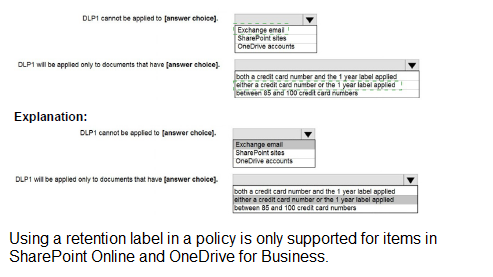
You configure a data loss prevention (DLP) policy named DLP1 as shown in the following exhibit.
Your company has digitally signed applications.
You need to ensure that Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP) considers the digitally signed applications safe and never analyzes them.
What should you create in the Microsoft Defender Security Center?
A.
a custom detection rule
B.
an allowed/blocked list rule
C.
an alert suppression rule
D.
an indicator
an indicator
You have a Microsoft 365 E5 subscription that contains a user named User1.
User1 exceeds the default daily limit of allowed email messages and is on the Restricted entities list.
You need to remove User1 from the Restricted entities list.
What should you use?
A.
the Exchange admin center
B.
the Microsoft Purview compliance portal
C.
the Microsoft 365 admin center
D.
the Microsoft 365 Defender portal
E.
the Microsoft Entra admin center
the Microsoft 365 Defender portal
Explanation:
Admins can remove user accounts from the Restricted entities page in the Microsoft 365 Defender portal or in Exchange Online PowerShell.
Remove a user from the Restricted entities page in the Microsoft 365 Defender portal In the Microsoft 365 Defender portal at https://security.microsoft.com, go to Email & collaboration > Review > Restricted entities. Or, to go directly to the Restricted entities page, use https://security.microsoft.com/restrictedentities.
Reference:
https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/removing-userfrom-restricted-users-portal-after-spam
| Page 9 out of 26 Pages |
| Previous |