Topic 5, Misc. Questions
You have a Microsoft 365 E5 subscription.
You need to create Conditional Access policies to meet the following requirements:
All users must use multi-factor authentication (MFA) when they sign in from outside the corporate network.
Users must only be able to sign in from outside the corporate network if the sign-in originates from a compliant device.
All users must be blocked from signing in from outside the United States and Canada.
Only users in the R&D department must be blocked from signing in from both Android and iOS devices.
Only users in the finance department must be able to sign in to an Azure AD enterprise application named App1. All other users must be blocked from signing in to App1.
What is the minimum number of Conditional Access policies you should create?
A.
3
B.
4
C.
5
D.
6
E.
7
F.
8
4
* Only users in the finance department must be able to sign in to an Azure AD enterprise application named App1. All other users must be blocked from signing in to App1.
One Policy.
* Only users in the R&D department must be blocked from signing in from both Android and iOS devices.
One Policy.
* Users must only be able to sign in from outside the corporate network if the sign-in originates from a compliant device.
All users must use multi-factor authentication (MFA) when they sign in from outside the corporate network.
One policy
* All users must be blocked from signing in from outside the United States and Canada. Only users in the R&D department must be blocked from signing in from both Android One Policy
Reference:
https://learn.microsoft.com/en-us/azure/active-directory/conditional-access/planconditional-access
Your company has a Microsoft 365 E5 subscription.
Users in the research department work with sensitive data.
You need to prevent the research department users from accessing potentially unsafe websites by using hyperlinks embedded in email messages and documents. Users in other departments must not be restricted.
What should you do?
A.
Create a data loss prevention (DLP) policy that has a Content is shared condition.
B.
Modify the safe links policy Global settings.
C.
Create a data loss prevention (DLP) policy that has a Content contains condition.
D.
Create a new safe links policy.
Create a new safe links policy.
Explanation:
Use the Microsoft 365 Defender portal to create Safe Links policies
In the Microsoft 365 Defender portal at https://security.microsoft.com, go to Email & Collaboration > Policies & Rules > Threat policies > Safe Links in the Policies section. Or, to go directly to the Safe Links page, use https://security.microsoft.com/safelinksv2.
1. On the Safe Links page, select Create to start the new Safe Links policy wizard.
2. On the Name your policy page, configure the following settings:
Name: Enter a unique, descriptive name for the policy.
Description: Enter an optional description for the policy.
3. When you're finished on the Name your policy page, select Next.
4. On the Users and domains page, identify the internal recipients that the policy applies to (recipient conditions):
Users: The specified mailboxes, mail users, or mail contacts.
*-> Groups:
Members of the specified distribution groups (including non-mail-enabled security groups within distribution groups) or mail-enabled security groups (dynamic distribution groups aren't supported).
The specified Microsoft 365 Groups.
Domains: All recipients in the specified accepted domains in your organization.
You have a Microsoft 365 E5 tenant that contains a Microsoft SharePoint Online site named Site1. Site1 contains the files shown in the following table.
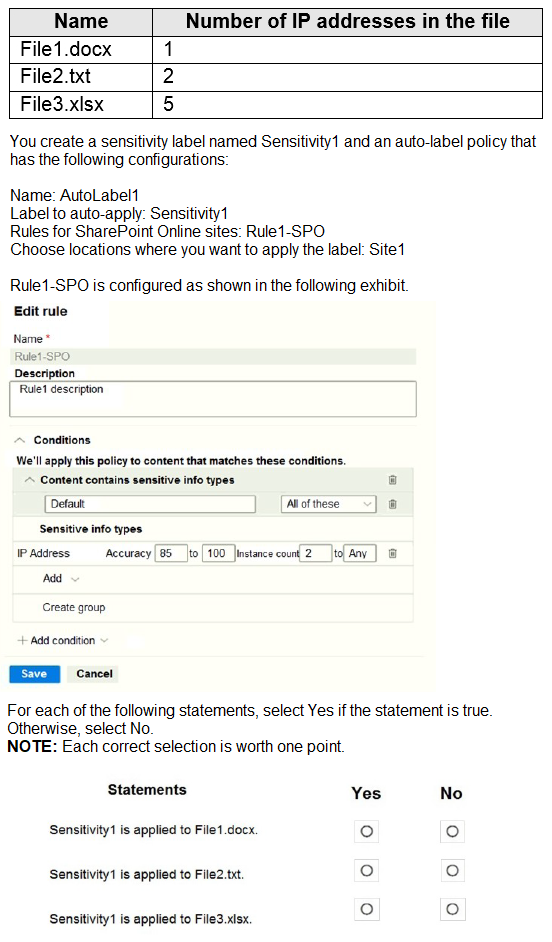
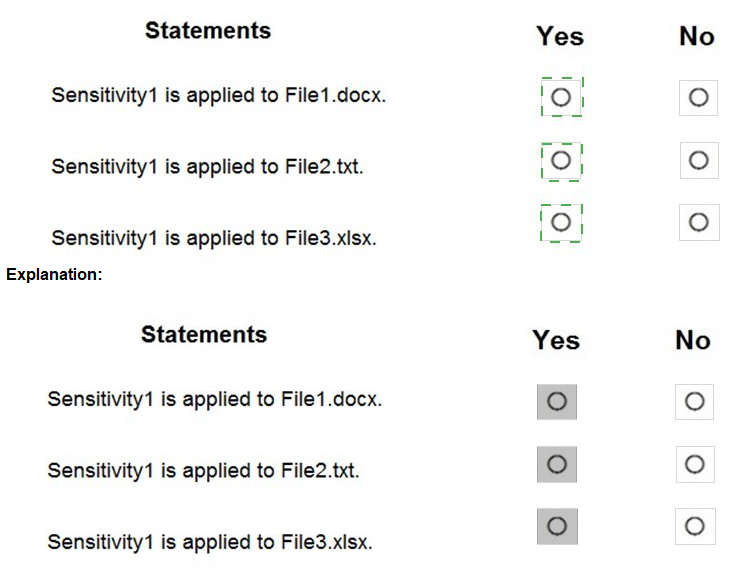
Your on-premises network contains an Active Directory domain named Contoso.com and 500 devices that run either macOS, Windows 8.1. Windows 10, or Windows 11. All the devices are managed by using Microsoft Endpoint Configuration Manager. The domain syncs with Azure Active Directory (Azure AD).
You plan to implement a Microsoft 365 E5 subscription and enable co-management. Which devices can be co-managed after the implementation?
A.
Windows 11 and Windows 10 only
B.
Windows 11, Windows 10-Windows8.1.andmacOS
C.
Windows 11 and macOS only
D.
Windows 11 only
E.
Windows 11. Windows 10, and Windows8.1 only
Windows 11 and macOS only
You have a Microsoft 365 E5 subscription linked to an Azure Active Directory (Azure AD) tenant. The tenant contains a group named Group1 and the users shown in the following table:
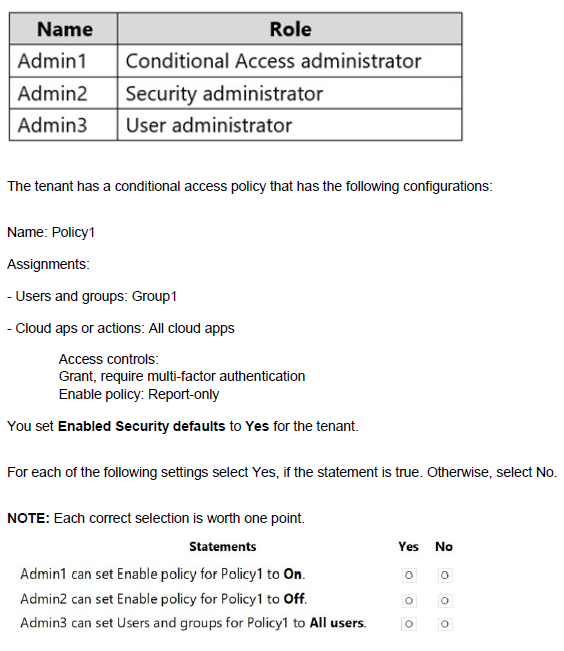
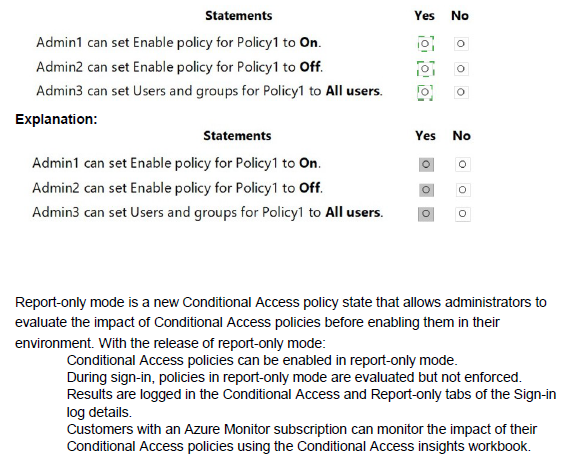
You have a Microsoft 365 E5 tenant.
You create a retention label named Retention1 as shown in the following exhibit.

When users attempt to apply Retention1, the label is unavailable.
You need to ensure that Retention1 is available to all the users.
What should you do?
A.
Create a new label policy
B.
Modify the Authority type setting for Retention!
C.
Modify the Business function/department setting for Retention 1.
D.
Use a file plan CSV template to import Retention1.
Create a new label policy
Your company has 10,000 users who access all applications from an on-premises data center.
You plan to create a Microsoft 365 subscription and to migrate data to the cloud.
You plan to implement directory synchronization.
User accounts and group accounts must sync to Azure AD successfully.
You discover that several user accounts fail to sync to Azure AD.
You need to resolve the issue as quickly as possible.
What should you do?
A.
From Active Directory Administrative Center, search for all the users, and then modify the properties of the user accounts.
B.
Run idfix.exe, and then click Edit.
C.
From Windows PowerShell, run the start-AdSyncSyncCycle -PolicyType Delta
command.
D.
Run idfix.exe, and then click Complete.
Run idfix.exe, and then click Edit.
Explanation:
IdFix is used to perform discovery and remediation of identity objects and their attributes in an on-premises Active Directory environment in preparation for migration to Azure Active Directory. IdFix is intended for the Active Directory administrators responsible for directory synchronization with Azure Active Directory.
Reference:
https://docs.microsoft.com/en-us/office365/enterprise/prepare-directory-attributes-forsynch- with-idfix
You have a Microsoft 365 E5 subscription. The subscription contains users that have the following types of devices:
• Windows 10
• Android
• OS
On which devices can you configure the Endpoint DLP policies?
A.
Windows 10 only
B.
Windows 10 and Android only
C.
Windows 10 and macO Sonly
D.
Windows 10, Android, and iOS
Windows 10 and macO Sonly
Endpoint data loss prevention (Endpoint DLP) extends the activity monitoring and protection capabilities of DLP to sensitive items that are physically stored on Windows 10, Windows 11, and macOS (Catalina 10.15 and higher) devices. Once devices are onboarded into the Microsoft Purview solutions, the information about what users are doing with sensitive items is made visible in activity explorer and you can enforce protective actions on those items via DLP policies.
https://docs.microsoft.com/en-us/microsoft-365/compliance/endpoint-dlp-learnabout?view=o365-worldwide
You have a Microsoft 365 subscription that uses an Azure AD tenant named contoso.com. The tenant contains the users shown in the following table.
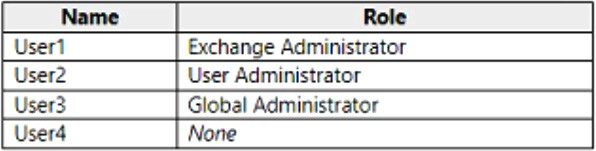
You add another user named User5 to the User Administrator role.
You need to identify which two management tasks User5 can perform.
Which two tasks should you identify? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A.
Delete User2 and User4 only.
B.
Reset the password of User4 only
C.
Reset the password of any user in Azure AD.
D.
Delete User1, User2, and User4 only.
E.
Reset the password of User2 and User4 only.
F.
Delete any user in Azure AD.
Delete User2 and User4 only.
Reset the password of User2 and User4 only.
Explanation:
Users with the User Administrator role can create users and manage all aspects of users with some restrictions (see below).
Only on users who are non-admins or in any of the following limited admin roles:
• Directory Readers
• Guest Inviter
• Helpdesk Administrator
• Message Center Reader
• Reports Reader
• User Administrator
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/directoryassign-admin-roles#available-roles
Your company has a Microsoft 365 subscription.
you implement sensitivity Doris for your company.
You need to automatically protect email messages that contain the word Confidential m the subject line.
What should you create?
A.
a sharing policy from the Exchange admin center
B.
a mail flow rule from the Exchange admin center
C.
a message Dace from the Microsoft 365 security center
D.
a data loss prevention (DLP) policy from the Microsoft 365 compliance center
a mail flow rule from the Exchange admin center
You have a Microsoft 365 subscription.
You have an Azure AD tenant that contains the users shown in the following table.
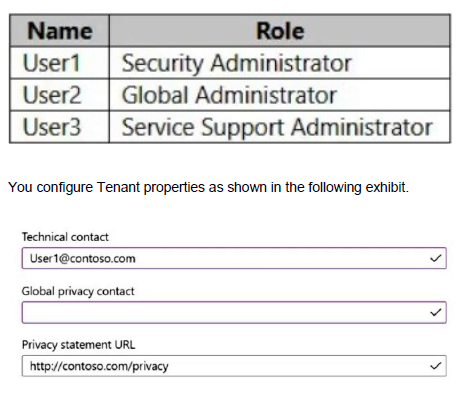
Which users will be contacted by Microsoft if the tenant experiences a data breach?
A.
Used only
B.
User2 only
C.
User3 only
D.
Used and User2 only
E.
User2 and User3 only
User2 only
Explanation:
Microsoft 365 is committed to notifying customers within 72 hours of breach declaration. The customer's tenant administrator will be notified.
Reference:
https://learn.microsoft.com/en-us/compliance/regulatory/gdpr-breach-office365
You have a hybrid deployment of Microsoft 365 that contains the users shown in the following table.
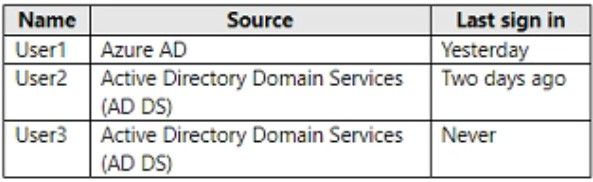
Azure AD Connect has the following settings:
Password Hash Sync: Enabled
Pass-through authentication: Enabled
You need to identify which users will be able to authenticate by using Azure AD if connectivity between on-premises Active Directory and the internet is lost.
Which users should you identify?
A.
none
B.
Used only1
C.
User1 and User2 only
D.
User1. User2, and User3
User1. User2, and User3
| Page 7 out of 26 Pages |
| Previous |