Topic 5, Misc. Questions
You have a Microsoft 365 E5 tenant that connects to Microsoft Defender for Endpoint. You have devices enrolled in Microsoft Intune as shown in the following table.
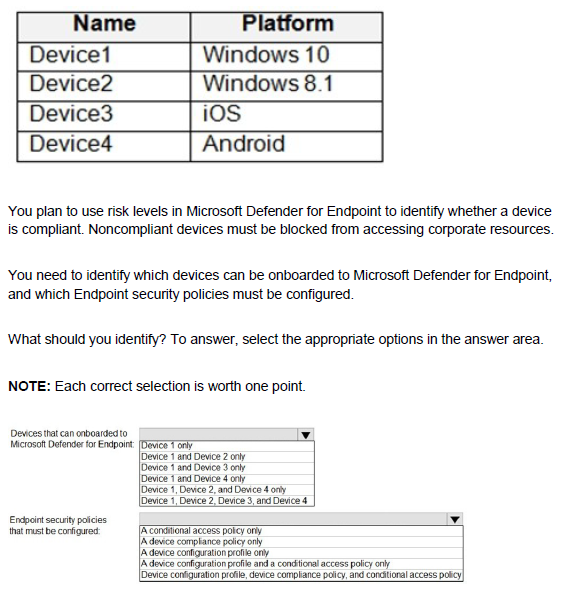
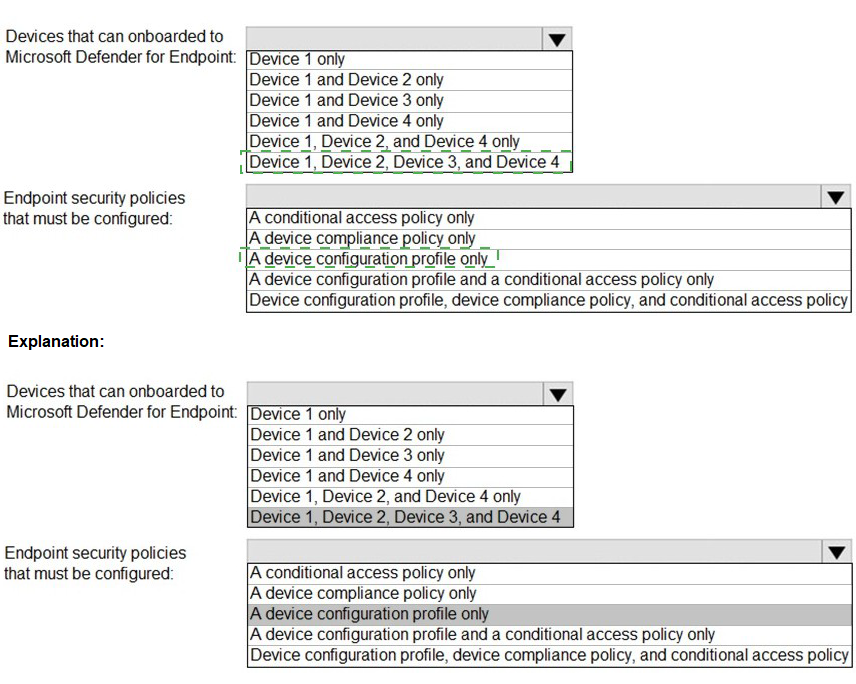
You have a Microsoft 365 E5 subscription.
You plan to implement records management and enable users to designate documents as regulatory records.
You need to ensure that the option to mark content as a regulatory record is visible when you create retention labels.
What should you do first?
A.
Configure custom detection rules
B.
Create an Exact Data Match (EDM) schema
C.
Run the Sec-RegulacoryComplianceUI cmdlet
D.
Run the Sec-LabelPolicy cmdlet
Run the Sec-RegulacoryComplianceUI cmdlet
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.
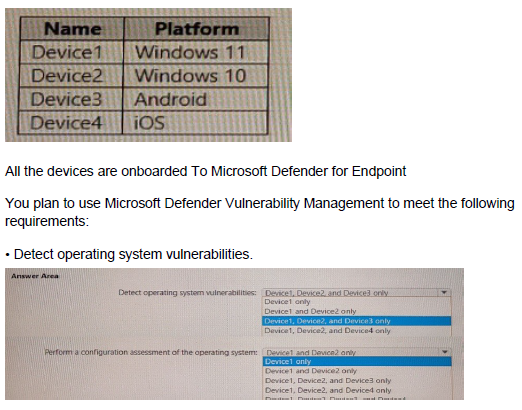
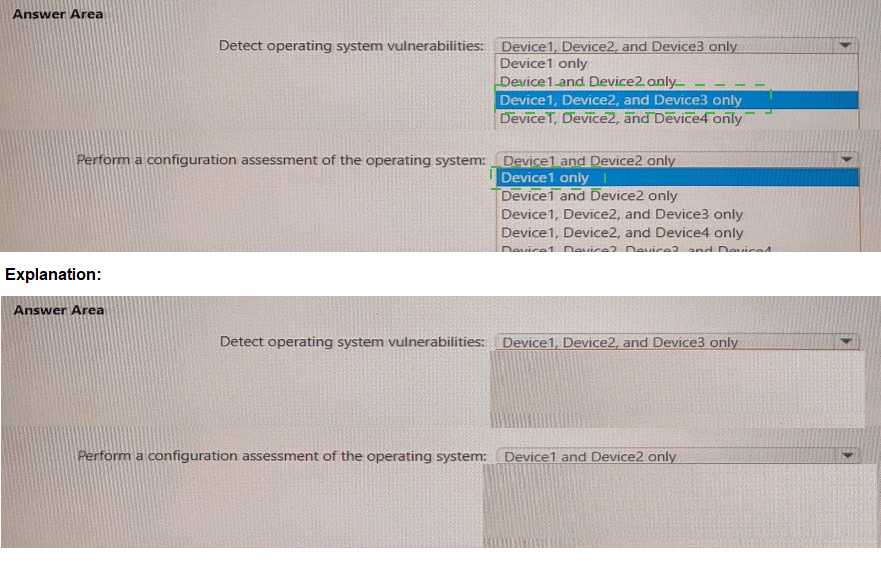
You have a Microsoft 365 E5 tenant that contains 500 Windows 10 devices. The devices are enrolled in Microsoft intune.
You plan to use Endpoint analytics to identify hardware issues.
You need to enable Window health monitoring on the devices to support Endpoint analytics. What should you do?
A.
Configure the Endpoint analytics baseline regression threshold.
B.
Create a configuration profile.
C.
Create a Windows 10 Security Baseline profile
D.
Create a compliance policy.
Create a configuration profile.
Note: This question is part of a series of questions that present the same scenario.
Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others
might not have a correct solution. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the users shown in the following table.
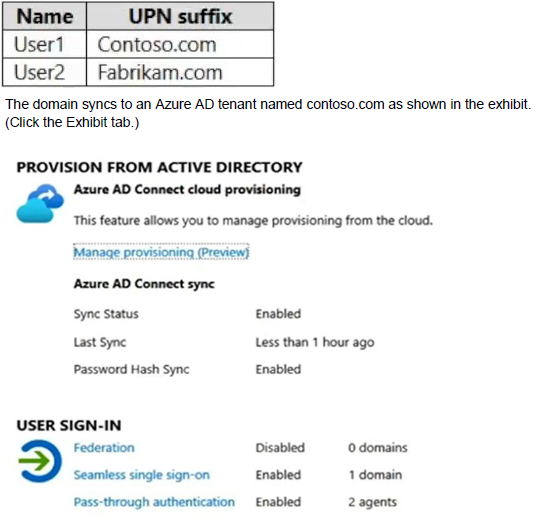
User2 fails to authenticate to Azure AD when signing in as user2@fabrikam.com.
You need to ensure that User2 can access the resources in Azure AD.
Solution: From the on-premises Active Directory domain, you set the UPN suffix for User2 to @contoso.com. You instruct User2 to sign in as user2@contoso.com.
Does this meet the goal?
A.
Yes
B.
No
Yes
The on-premises Active Directory domain is named contoso.com. You can enable users to sign on using a different UPN (different domain), by adding the domain to Microsoft 365 as a custom domain. Alternatively, you can configure the user account to use the existing domain (contoso.com).
You have a Microsoft 365 E5 tenant that contains the users shown in the following table.

Your company has a Microsoft 365 E5 tenant.
Users at the company use the following versions of Microsoft Office:
• Microsoft 365 Apps for enterprise
• Office for the web
• Office 2016
• Office 2019
The company currently uses the following Office file types:
• .docx
• .xlsx
• .doc
• xls
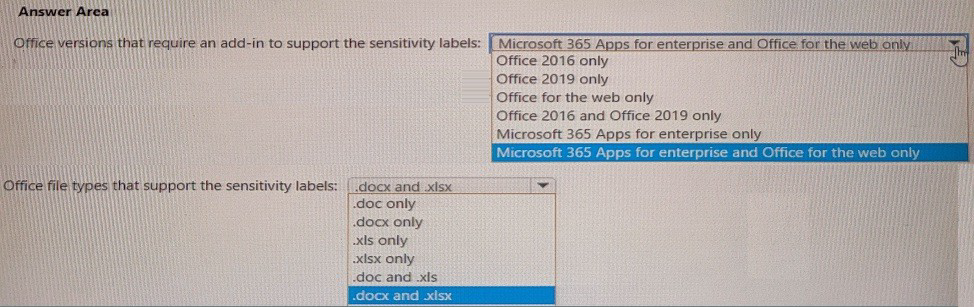
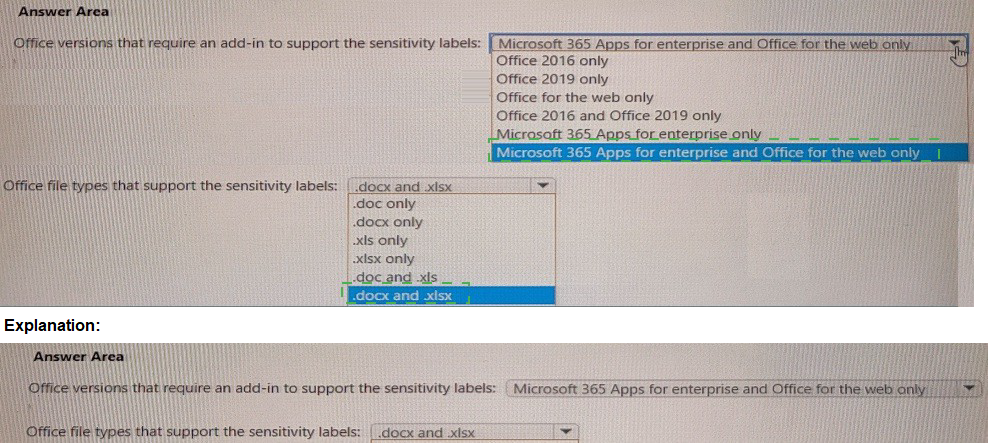
You plan to use sensitivity labels. You need to identify the following:
• Which versions of Office require an add-in to support the sensitivity labels.
• Which file types support the sensitivity labels.
What should you identify? To answer, select the appropriate options in the answer area,
NOTE: Each correct selection is worth one point.
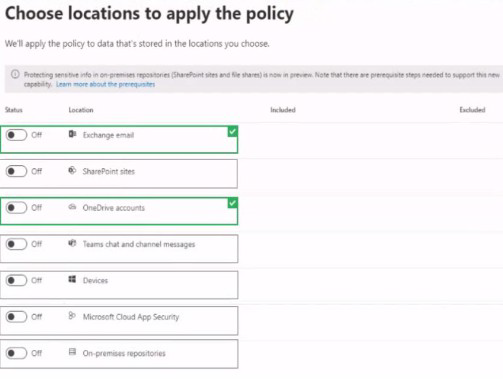
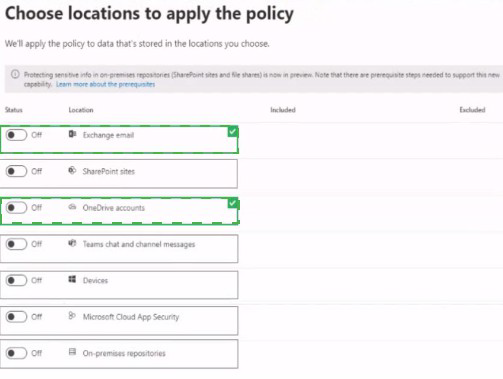
You have a Microsoft 365 E5 tenant
You create a data toss prevention (DLP) policy to prevent users from using Microsoft Teams to share internal documents with external users.
To which two locations should you apply the policy? To answer, select the appropriate locations in the answer area.
NOTE: Each correct selection is worth one point.
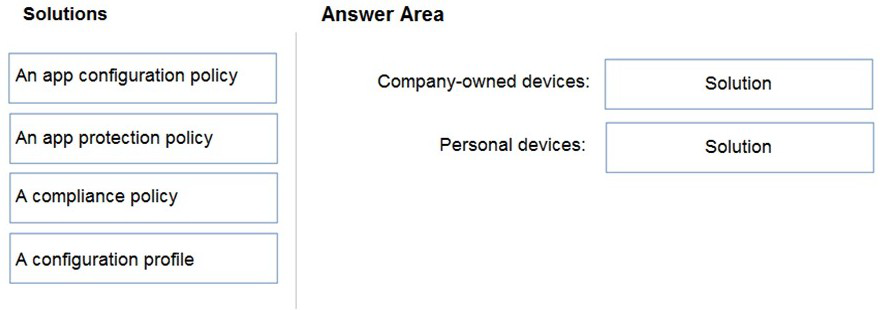
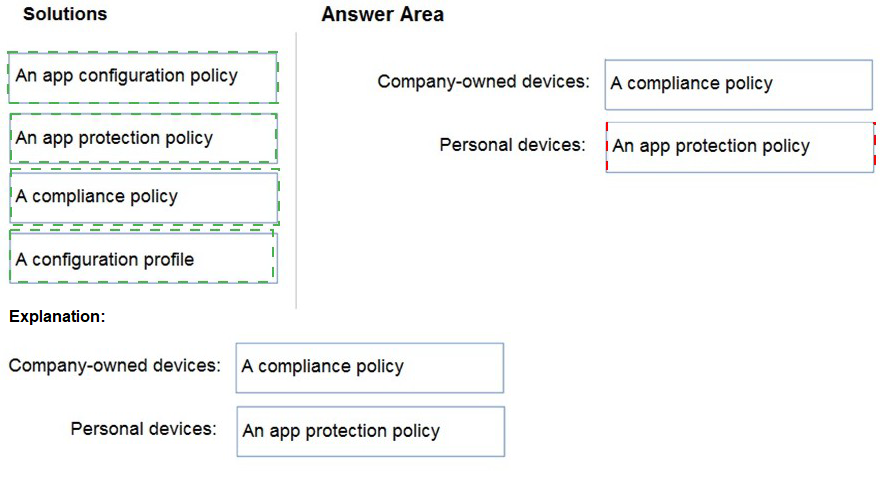
Your company has a Microsoft 365 E5 tenant.
Users access resources in the tenant by using both personal and company-owned Android devices. Company policies requires that the devices have a threat level of medium or lower to access Microsoft Exchange Online mailboxes.
You need to recommend a solution to identify the threat level of the devices and to control access of the devices to the resources.
What should you include in the solution for each device type? To answer, drag the appropriate components to the correct devices. Each component may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
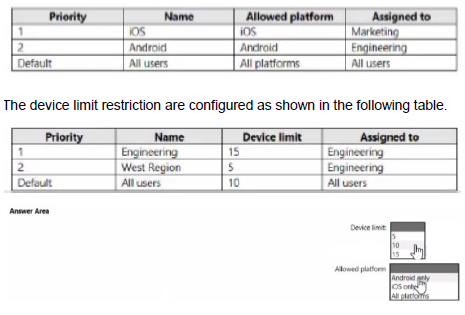
Your company has a Microsoft 365 tenant
You plan to allow users that are members of a group named Engineering to enroll their mobile device in mobile device management (MDM)
The device type restriction are configured as shown in the following table.

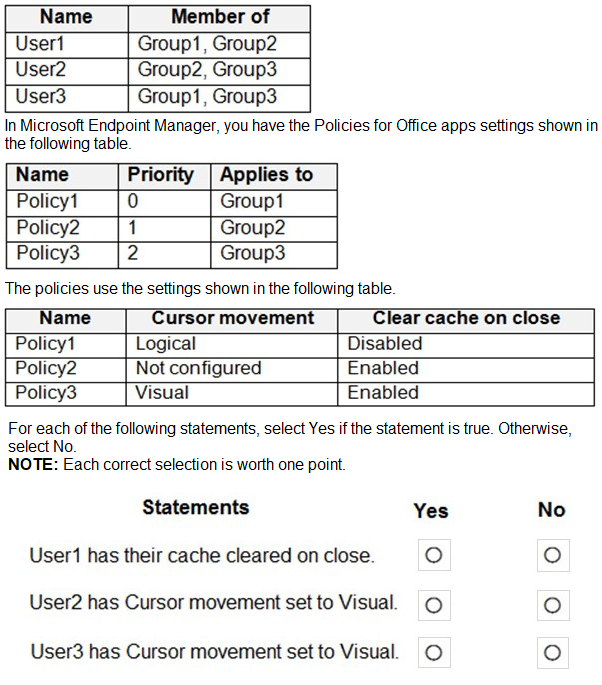
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
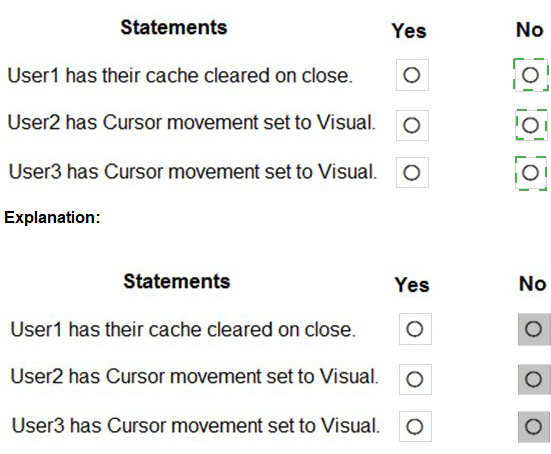
You have a Microsoft 365 E5 subscription.
Al users have Mac computers. ATI the computers are enrolled in Microsoft Endpoint Manager and onboarded to Microsoft Defender for Endpoint.
You need to configure Microsoft Defender for Endpoint on the computers.
What should you create from the Endpoint Management admin center?
A.
a Microsoft Defender for Endpoint baseline profile
B.
an update policy for iOS
C.
a device configuration profile
D.
a mobile device management (MDM) security baseline profile
a mobile device management (MDM) security baseline profile
| Page 2 out of 26 Pages |
| Previous |