Topic 5, Misc. Questions
You have a Microsoft 365 E5 subscription that.
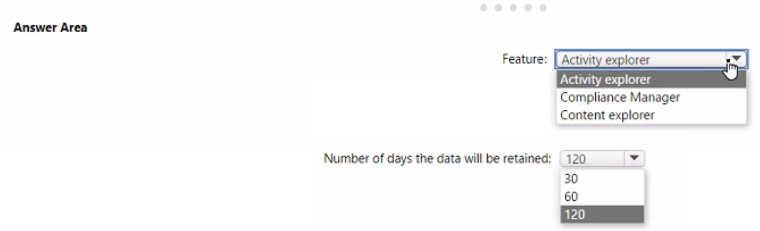
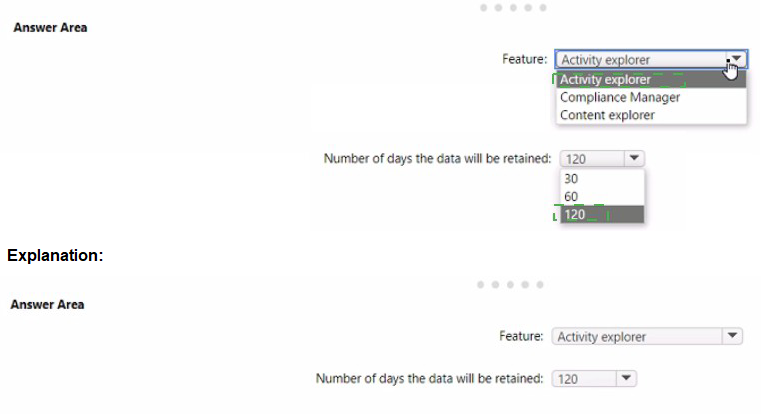
You need to identify whenever a sensitivity label is applied, changed, or removed within the subscription.
Which feature should you use, and how many days will the data be retained? To answer, select the appropriate options in the answer area.
NOTE Each correct selection is worth one point.
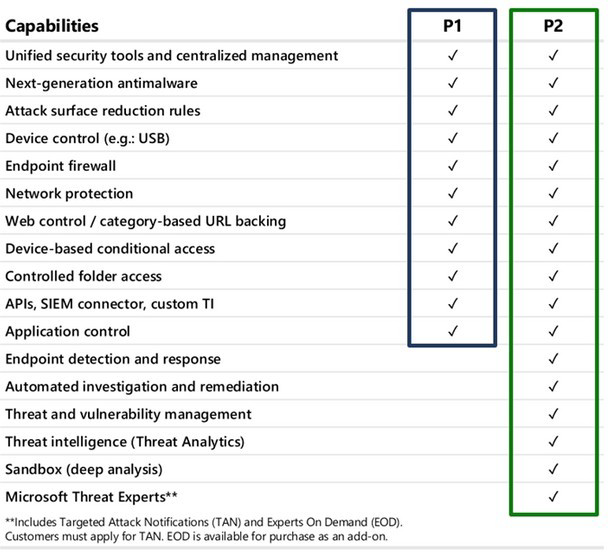
You have a Microsoft 365 E3 subscription that uses Microsoft Defender for Endpoint Plan 1.
Which two Defender for Endpoint features are available to the subscription? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A.
advanced hunting
B.
security reports
C.
digital certificate assessment
D.
device discovery
E.
attack surface reduction (ASR)
security reports
Explanation:
B: Overview of Microsoft Defender for Endpoint Plan 1, Reporting
The Microsoft 365 Defender portal (https://security.microsoft.com) provides easy access to information about detected threats and actions to address those threats.
The Home page includes cards to show at a glance which users or devices are at risk, how many threats were detected, and what alerts/incidents were created.
The Incidents & alerts section lists any incidents that were created as a result of triggered alerts. Alerts and incidents are generated as threats are detected across devices.
The Action center lists remediation actions that were taken. For example, if a file is sent to quarantine, or a URL is blocked, each action is listed in the Action center on the History tab.
The Reports section includes reports that show threats detected and their status.
E: What can you expect from Microsoft Defender for Endpoint P1?
Microsoft Defender for Endpoint P1 is focused on prevention/EPP including:
Next-generation antimalware that is cloud-based with built-in AI that helps to stop ransomware, known and unknown malware, and other threats in their tracks.
(E) Attack surface reduction capabilities that harden the device, prevent zero days, and offer granular control over access and behaviors on the endpoint. Device based conditional access that offers an additional layer of data protection and breach prevention and enables a Zero Trust approach.
The below table offers a comparison of capabilities are offered in Plan 1 versus Plan 2.
Incorrect:
Not A: P2 is by far the best fit for enterprises that need an EDR solution including automated investigation and remediation tools, advanced threat prevention and threat and vulnerability management (TVM), and hunting capabilities.
Reference:
https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/defenderendpoint-plan-1
https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/microsoftdefender-for-endpoint-plan-1-now-included-in-m365-e3/ba-p/3060639
You have a Microsoft 365 E5 tenant that has sensitivity label support enabled for Microsoft and SharePoint Online.
You need to enable unified labeling for Microsoft 365 groups.
Which cmdlet should you run?
A.
Set-unifiedGroup
B.
Set-Labelpolicy
C.
Execute-AzureAdLebelSync
D.
Add-UnifiedGroupLinks
Execute-AzureAdLebelSync
You have a Microsoft 365 tenant and a LinkedIn company page.
You plan to archive data from the LinkedIn page to Microsoft 365 by using the LinkedIn connector.
Where can you store data from the LinkedIn connector?
A.
a Microsoft OneDrive for Business folder
B.
a Microsoft SharePoint Online document library
C.
a Microsoft 365 mailbox
D.
Azure Files
a Microsoft 365 mailbox
Your network contains an Active Directory forest named contoso.local.
You purchase a Microsoft 365 subscription.
You plan to move to Microsoft 365 and to implement a hybrid deployment solution for the next 12 months.
You need to prepare for the planned move to Microsoft 365.
What is the best action to perform before you implement directory synchronization? More than one answer choice may achieve the goal. Select the BEST answer.
A.
Purchase a third-party X.509 certificate.
B.
Create an external forest trust.
C.
Rename the Active Directory forest.
D.
Purchase a custom domain name.
Purchase a custom domain name.
Explanation:
The first thing you need to do before you implement directory synchronization is to purchase a custom domain name. This could be the domain name that you use in your onpremise Active Directory if it’s a routable domain name, for example, contoso.com. If you use a non-routable domain name in your Active Directory, for example contoso.local, you’ll need to add the routable domain name as a UPN suffix in Active Directory.
Incorrect:
Not C: No need to rename the Active Directory forest. As we use a non-routable domain name contoso.local, we just need to add the routable domain name as a UPN suffix in Active Directory.
Reference:
https://docs.microsoft.com/en-us/office365/enterprise/set-up-directory-synchronization
You have a Microsoft 365 tenant that contains devices registered for mobile device management. The devices are configured as shown in the following table.
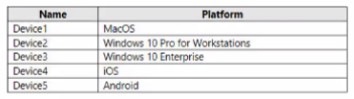
You plan to enable VPN access for the devices.
What is the minimum number of configuration policies required?
A.
3
B.
5
C.
4
D.
1
1
You have a Microsoft 365 E5 subscription that contains two users named Admin1 and Admin2.
All users are assigned a Microsoft 365 Enterprise E5 license and auditing is turned on.
You create the audit retention policy shown in the exhibit. (Click the Exhibit tab.)
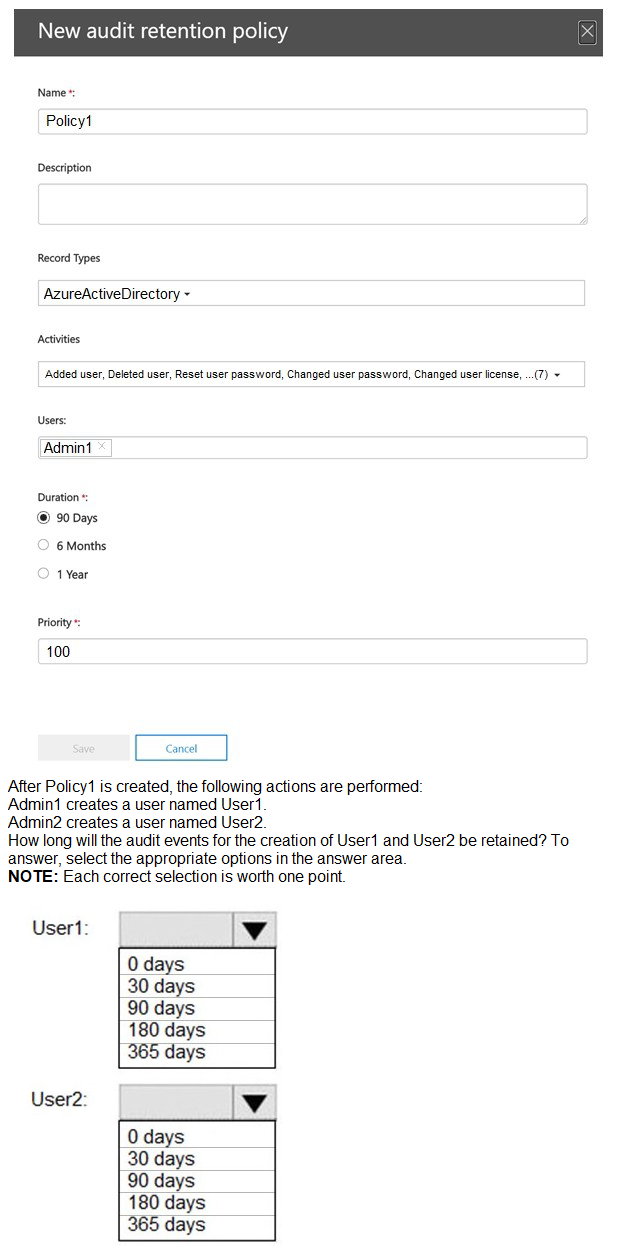
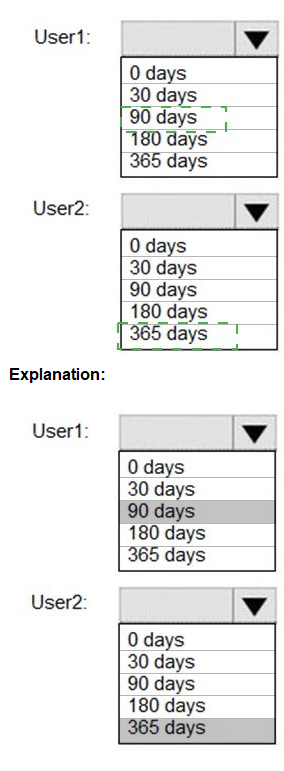
You have a Microsoft 365 tenant.
You plan to create a retention policy as shown in the following exhibit.
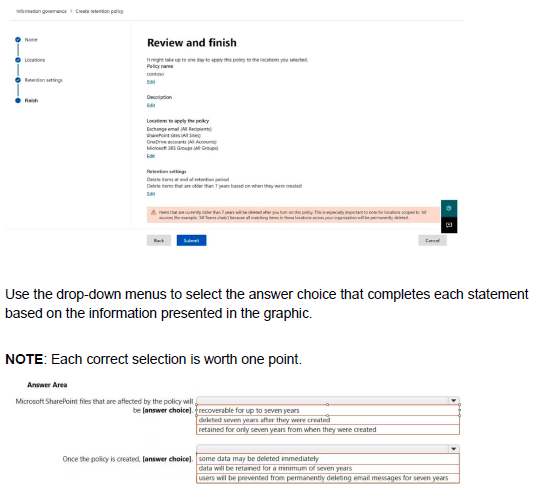
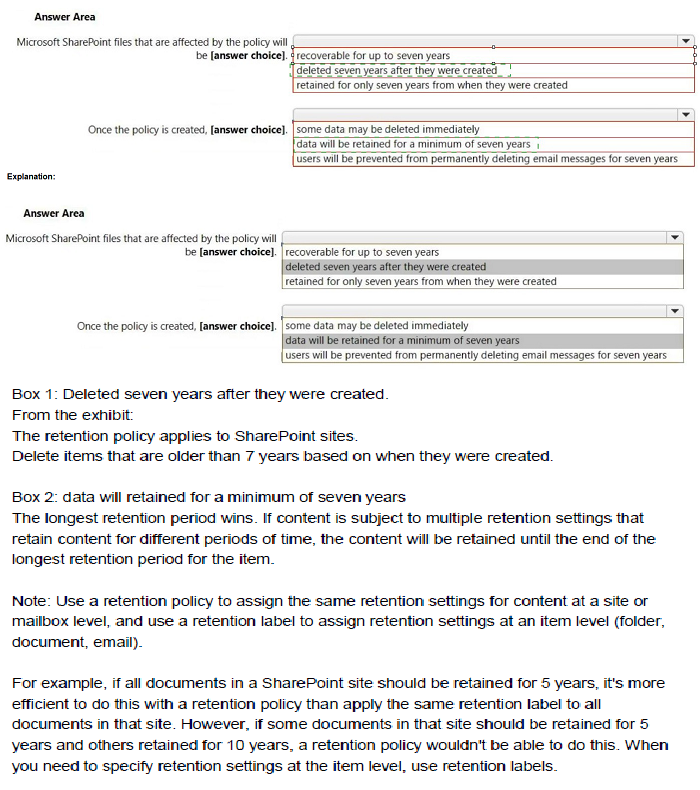
You have a Microsoft 365 E5 tenant.
The Microsoft Secure Score for the tenant is shown in the following exhibit.

You plan to enable Security defaults for Azure Active Directory (Azure AD).
Which three improvement actions will this affect?
A.
Require MFA for administrative roles.
B.
Ensure all users can complete multi-factor authentication for secure access
C.
Enable policy to block legacy authentication
D.
Enable self-service password reset
E.
Use limited administrative roles
Require MFA for administrative roles.
Ensure all users can complete multi-factor authentication for secure access
Enable policy to block legacy authentication
From the Microsoft 365 compliance center, you configure a data loss prevention (DLP) policy for a Microsoft SharePoint Online site named Site1. Site1 contains the roles shown in the following table.

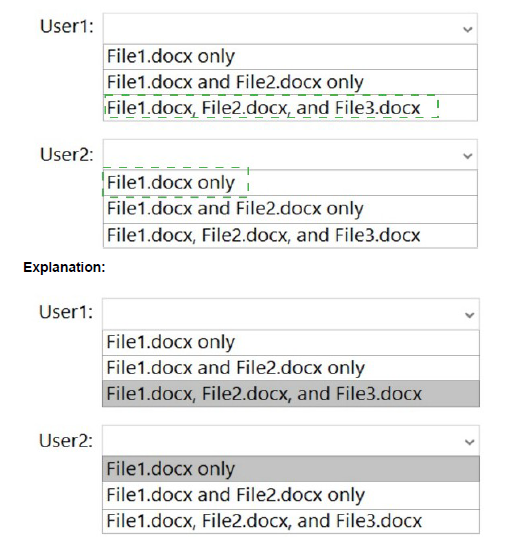
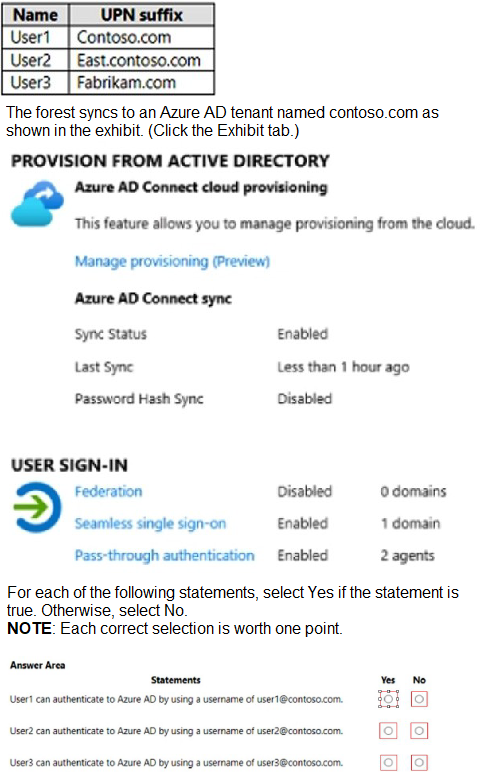
Your network contains an on-premises Active Directory forest named contoso.com. The forest contains the following domains:
Contoso.com
East.contoso.com
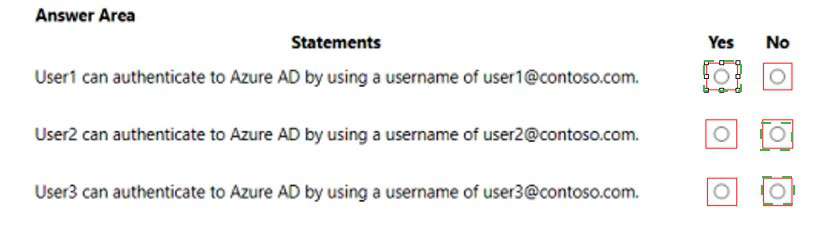
The forest contains the users shown in the following table.
Explanation:
Box 1: Yes
The UPN of user1 is user1@contoso.com so he can authenticate to Azure AD by using the username user1@contoso.com.
Box 2: No
The UPN of user2 is user2@east.contoso.com so he cannot authenticate to Azure AD by using the username user2@contoso.com.
Box 3: No
The UPN of user3 is user3@fabrikam.com so he cannot authenticate to Azure AD by using the username user3@contoso.com.
You plan to use Azure Sentinel and Microsoft Cloud App Security. You need to connect Cloud App Security to Azure Sentinel. What should you do in the Cloud App Security admin center?
A.
From Automatic log upload, add a log collector.
B.
From Automatic log upload, add a data source.
C.
From Connected apps, add an app connector.
D.
From Security extension, add a SIEM agent.
From Security extension, add a SIEM agent.
| Page 10 out of 26 Pages |
| Previous |