A guest establishes an authenticated wireless session to an Aruba Mobility Controller (MC).
The controller uses a ClearPass server for all AAA functions.
Which AAA component disconnects the user when the guest exceeds their allowed
duration?
A.
RADIUS Change of Authorization
B.
Active Directory Session Limits
C.
RADIUS Authorization Profile
D.
SNMP Disconnect
RADIUS Change of Authorization
A company network implements Skype for Business, where voice and video calls, desktop
sessions, and file sharing sessions need to be prioritized. These applications are used
across a wireless network, implemented with Aruba APs and Aruba Mobility Controllers
(MC) that run ArubaOS 8.x.
Which Unified Communications and Collaboration (UCC) deployment mode should an
administrator recommend for this customer?
A.
WMM-only
B.
SDN API
C.
Zones
D.
Heuristics
SDN API
An administrator stages an AP and re-provisions it as a RAP from the Mobility Master
(MM). When re-provisioning the RAP, the administrator must enter a user’s credentials.
What is the purpose of these credentials?
A.
to authenticate users on wired and wireless ports
B.
to authenticate the RAP device
C.
to authenticate users on wireless ports
D.
to authenticate users on wired ports
to authenticate the RAP device
An administrator mistakenly configures the wrong VLAN setting on a managed controller’s
interface. This causes the controller to lose management access to the Mobility Master
(MM).
Which mechanism will then attempt to restore the previous working configuration on the
managed controller?
A.
disaster recovery
B.
auto-rollback
C.
restore config
D.
bulk configuration
auto-rollback
An administrator implements a per-port tunneled node configuration for an Aruba Mobility
Controller (MC) that runs ArubaOS 8.x. The controller performs both MAC and 802.1X
authentication.
What must the administrator specify on the controller to allow for 802.1X authentication to
succeed?
A.
Define External RADIUS servers in the AAA profile.
B.
Enable L2 Authentication Fail Through in the AAA profile.
C.
Define MAC addresses in the local database for the 802.1X users.
D.
Enable server roles in the AAA profile.
Enable L2 Authentication Fail Through in the AAA profile.
Refer to the exhibit.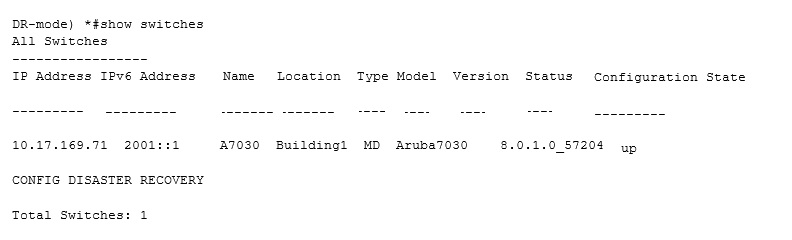
What is true about the operation of the Aruba Mobility Controller (MC) shown in the exhibit?
A.
The Mobility master is in disaster recovery mode and will push changes to a Managed Controller.
B.
The disaster recovery mode is enabled, and no changes will be forwarded to the Mobility Master.
C.
The disaster recovery mode is disabled, and changes will be sent to the Mobility Master.
D.
The disaster recovery mode is enabled, and changes will be sent to the Mobility Master.
The disaster recovery mode is enabled, and no changes will be forwarded to the Mobility Master.
Refer to the exhibit.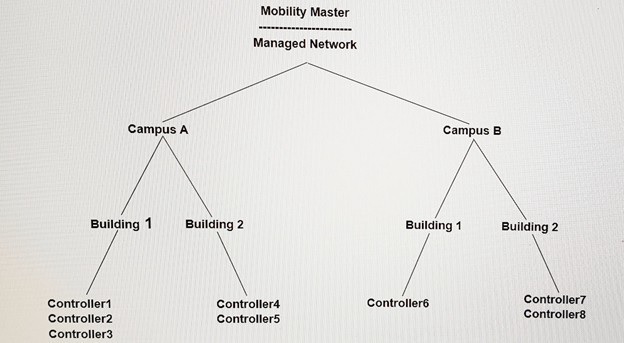
An administrator wants to centralize administrative access to the Aruba Mobility Controllers
(MC) and Mobility Master (MM). ClearPass is set up and the preferred authentication
protocols is TACACS+. Where should the administrator perform this configuration in the
MM hierarchy shown in the exhibit?
A.
At the Managed Network level
B.
At the two campus levels
C.
At both the Mobility Master and Managed Network levels
D.
At the controller levels
At both the Mobility Master and Managed Network levels
An administrator implements two redundant Aruba Mobility Masters (MMs). Which protocol
should the administrator use to detect a failure in a single subnet?
A.
PAPI
B.
SNMP
C.
VRRP
D.
IPSec
VRRP
An administrator wants to implement AAA in an Aruba wireless environment that
references two ClearPass servers for redundancy. To use these servers, what must the
administrator create that will be referenced in the AAA profile?
A.
ClearPass Group
B.
Server matching rules
C.
Server Group
D.
Server Load Balancing
Server Group
Where would an administrator define the split-tunneling mode for a RAP located at a branch office?
A.
the Firewall policy on the RAP
B.
the AAA policy on the controller
C.
the Firewall policy on the controller
D.
the VAP profile on the controller
the VAP profile on the controller
A VIA client tries to initially connect to corporate office controller through an intermediate
firewall. However, the VPN connection fails. The administrator examines the firewall rules
and determines that rules for UDP 4500 and UDP 500 are configured.
Which additional protocol must be allowed in the firewall rules to resolve this connection
failure?
A.
TCP 389
B.
UDP 4500
C.
UDP 8200
D.
TCP 993
UDP 4500
Refer to the exhibit.
The branch office RAP shown in the exhibit provides secure wireless employee access.
Because of security concerns, the company’s security policy does not allow wireless guest
access. Some customers that visit the Branch office need Internet access. A RAP’s
Ethernet Port 3 is used for wired guest access and Port2 is used for wired employee
access. When employees connect to Port2, they are authenticated successfully and splittunnel
policy allows them access to both corporate and Internet resources from the Branch
office. Guest users, however, cannot access Internet resources on Port 3.
How can the administrator provide guest users Internet access?
A.
Implement ClientMatch to handle the employee and guest user traffic correctly.
B.
Implement the MultiZone feature on the RAP.
C.
Configure a bridge role for the wired RAP port.
D.
Create a guest VAP that allows wired RAP port access
Configure a bridge role for the wired RAP port.
Explanation:
https://www.arubanetworks.com/techdocs/ArubaOS-6_3_1_Web_Help/Content/ArubaF
rameStyles/Remote_AP/Bridge.htm
| Page 6 out of 15 Pages |
| Previous |