Which two are benefits of using multi-tenancy mode on FortiClient EMS? (Choose two.)
A. Separate host servers manage each site.
B. Licenses are shared among sites
C. The fabric connector must use an IP address to connect to FortiClient EMS.
D. It provides granular access and segmentation.
Refer to the exhibit.
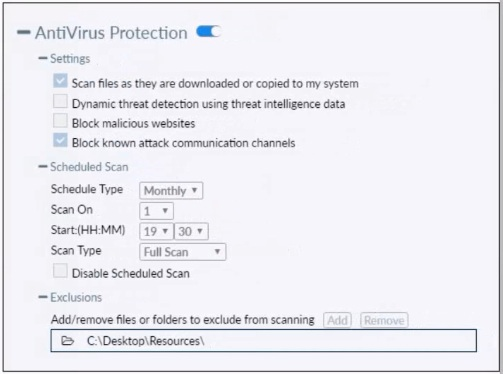
Based on the settings shown in the exhibit which statement about FortiClient behavior is true?
A. FortiClient quarantines infected files and reviews later, after scanning them.
B. FortiClient blocks and deletes infected files after scanning them.
C. FortiClient scans infected files when the user copies files to the Resources folder
D. FortiClient copies infected files to the Resources folder without scanning them.
Explanation: Action On Virus Discovery Warn the User If a Process Attempts to Access Infected Files Quarantine Infected Files. You can use FortiClient to view, restore, or delete the quarantined file, as well as view the virus name, submit the file to FortiGuard, and view logs. Deny Access to Infected Files Ignore Infected Files
Which statement about the FortiClient enterprise management server is true?
A. It receives the configuration information of endpoints from ForuGate.
B. It provides centralized management of multiple endpoints running FortiClient software.
C. It enforces compliance on the endpoints using tags
D. It receives the CA certificate from FortiGate to validate client certrficates.
What is the function of the quick scan option on FortiClient?
A. It scans programs and drivers that are currently running, for threats
B. It performs a full system scan including all files, executable files. DLLs, and drivers for throats.
C. It allows users to select a specific file folder on their local hard disk drive (HDD), to scan for threats.
D. It scans executable files. DLLs, and drivers that are currently running, for threats.
Which two third-party tools can an administrator use to deploy FortiClient? (Choose two.)
A. Microsoft Windows Installer
B. Microsoft SCCM
C. Microsoft Active Directory GPO
D. QR code generator
A new chrome book is connected in a school's network.
Which component can the EMS administrator use to manage the FortiClient web filter
extension installed on the Google Chromebook endpoint?
A. FortiClient EMS
B. FortiClient site categories
C. FortiClient customer URL list
D. FortiClient web filter extension
Which two statements are true about the ZTNA rule? (Choose two.)
A. It applies security profiles to protect traffic
B. It applies SNAT to protect traffic.
C. It defines the access proxy.
D. It enforces access control.
Why does FortiGate need the root CA certificate of FortiCient EMS?
A. To revoke FortiClient client certificates
B. To sign FortiClient CSR requests
C. To update FortiClient client certificates
D. To trust certificates issued by FortiClient EMS
An administrator has a requirement to add user authentication to the ZTNA access for remote or off-fabric users Which FortiGate feature is required m addition to ZTNA?
A. FortiGate FSSO
B. FortiGate certificates
C. FortiGate explicit proxy
D. FortiGate endpoint control
ZTNA Network Topology
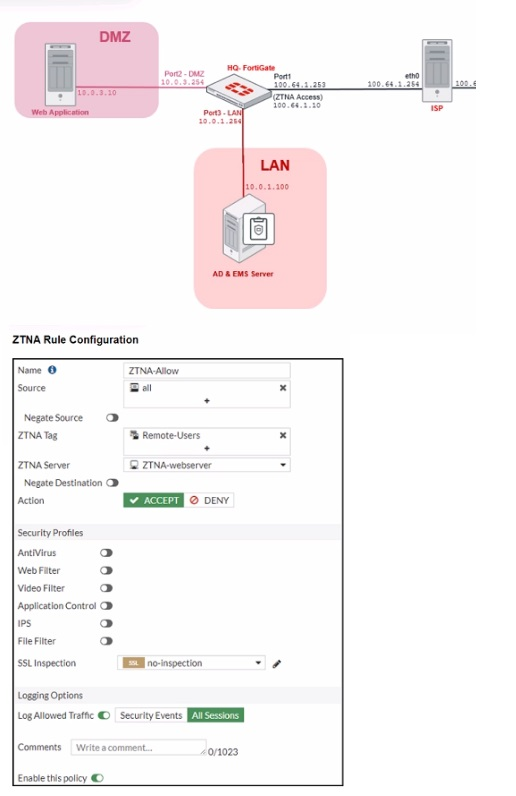
Refer to the exhibits, which show a network topology diagram of ZTNA proxy access and
the ZTNA rule configuration.
An administrator runs the diagnose endpoint record list CLI command on FortiGate to
check Remote-Client endpoint information, however Remote-Client is not showing up in theendpoint record list.
What is the cause of this issue?
A. Remote-Client has not initiated a connection to the ZTNA access proxy.
B. Remote-Client provided an empty client certificate to connect to the ZTNA access proxy.
C. Remote-Client provided an invalid certificate to connect to the ZTNA access proxy.
D. Remote-Client failed the client certificate authentication.
An administrator configures ZTNA configuration on the FortiGate. Which statement is true about the firewall policy?
A. It redirects the client request to the access proxy.
B. It uses the access proxy.
C. It defines ZTNA server.
D. It only uses ZTNA tags to control access for endpoints.
Refer to the exhibit.
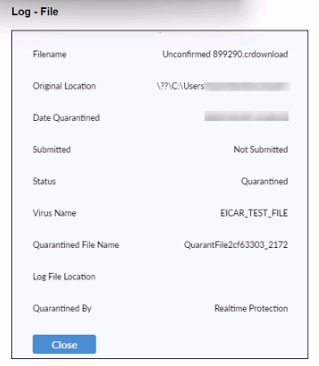
Based on the FortiClient tog details shown in the exhibit, which two statements ace true?
(Choose two.)
A. The filename Is Unconfirmed 899290.crdovnload.
B. The file status is Quarantined
C. The filename is sent to FortiSandbox for further inspection.
D. The file location is \??\D:\Users\.
| Page 1 out of 5 Pages |