An application that is hosted on an Amazon EC2 instance needs access to files that are stored in an Amazon S3 bucket. The application lists the objects that are stored in the S3 bucket and displays a table to the user. During testing, a developer discovers that the application does not show any objects in the list. What is the MOST secure way to resolve this issue?
A. Update the IAM instance profile that is attached to the EC2 instance to include the S3:* permission for the S3 bucket.
B. Update the IAM instance profile that is attached to the EC2 instance to include the S3:ListBucket permission for the S3 bucket.
C. Update the developer's user permissions to include the S3:ListBucket permission for the S3 bucket.
D. Update the S3 bucket policy by including the S3:ListBucket permission and by setting the Principal element to specify the account number of the EC2 instance.
Explanation: IAM instance profiles are containers for IAM roles that can be associated with EC2 instances. An IAM role is a set of permissions that grant access to AWS resources. An IAM role can be used to allow an EC2 instance to access an S3 bucket by including the appropriate permissions in the role’s policy. The S3:ListBucket permission allows listing the objects in an S3 bucket. By updating the IAM instance profile with this permission, the application on the EC2 instance can retrieve the objects from the S3 bucket and display them to the user.
A developer needs to write an AWS CloudFormation template on a local machine and deploy a CloudFormation stack to AWS. What must the developer do to complete these tasks?
A. Install the AWS CLI. Configure the AWS CLI by using an I AM user name and password.
B. Install the AWS CLI. Configure the AWS CLI by using an SSH key.
C. Install the AWS CLI. Configure the AWS CLI by using an 1AM user access key and secret key.
D. Install an AWS software development kit (SDK). Configure the SDK by using an X.509 certificate.
A large company has its application components distributed across multiple AWS accounts. The company needs to collect and visualize trace data across these accounts. What should be used to meet these requirements?
A. AWS X-Ray
B. Amazon CloudWatch
C. Amazon VPC flow logs
D. Amazon OpenSearch Service
A developer has written the following IAM policy to provide access to an Amazon S3
bucket: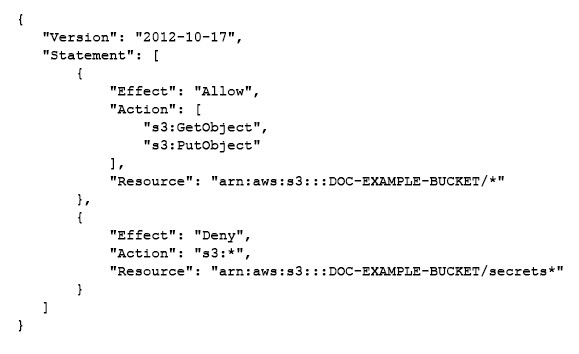
Which access does the policy allow regarding the s3:GetObject and s3:PutObject actions?
A. Access on all buckets except the “DOC-EXAMPLE-BUCKET” bucket
B. Access on all buckets that start with “DOC-EXAMPLE-BUCKET” except the “DOCEXAMPLE- BUCKET/secrets” bucket
C. Access on all objects in the “DOC-EXAMPLE-BUCKET” bucket along with access to all S3 actions for objects in the “DOC-EXAMPLE-BUCKET” bucket that start with “secrets”
D. Access on all objects in the “DOC-EXAMPLE-BUCKET” bucket except on objects that start with “secrets”
Explanation: The IAM policy shown in the image is a resource-based policy that grants or denies access to an S3 bucket based on certain conditions. The first statement allows access to any S3 action on any object in the “DOC-EXAMPLE-BUCKET” bucket when the request is made over HTTPS (the value of aws:SecureTransport is true). The second statement denies access to the s3:GetObject and s3:PutObject actions on any object in the “DOC-EXAMPLE-BUCKET/secrets” prefix when the request is made over HTTP (the value of aws:SecureTransport is false). Therefore, the policy allows access on all objects in the “DOC-EXAMPLE-BUCKET” bucket except on objects that start with “secrets”.
A developer is creating an application that uses an AWS Lambda function to transform and
load data from an Amazon S3 bucket. When the developer tests the application, the
developer finds that some invocations of the Lambda function are slower than others.
The developer needs to update the Lambda function to have predictable invocation
durations that run with low latency. Any initialization activities, such as loading libraries and
instantiating clients, must run during allocation time rather than during actual function
invocations.
Which combination of steps will meet these requirements? (Select TWO.)
A. Create a schedule group in Amazon EventBridge Scheduler to invoke the Lambda function.
B. Configure provisioned concurrency for the Lambda function to have the necessary number of execution environments.
C. Use the SLATEST version of the Lambda function.
D. Configure reserved concurrency for the Lambda function to have the necessary number of execution environments.
E. Deploy changes, and publish a new version of the Lambda function.
A company has deployed an application on AWS Elastic Beanstalk. The company has configured the Auto Scaling group that is associated with the Elastic Beanstalk environment to have five Amazon EC2 instances. If the capacity is fewer than four EC2instances during the deployment, application performance degrades. The company is using the all-at-once deployment policy. What is the MOST cost-effective way to solve the deployment issue?
A. Change the Auto Scaling group to six desired instances.
B. Change the deployment policy to traffic splitting. Specify an evaluation time of 1 hour.
C. Change the deployment policy to rolling with additional batch. Specify a batch size of 1.
D. Change the deployment policy to rolling. Specify a batch size of 2.
Explanation: This solution will solve the deployment issue by deploying the new version of the application to one new EC2 instance at a time, while keeping the old version running on the existing instances. This way, there will always be at least four instances serving traffic during the deployment, and no downtime or performance degradation will occur. Option A is not optimal because it will increase the cost of running the Elastic Beanstalk environment without solving the deployment issue. Option B is not optimal because it will split the traffic between two versions of the application, which may cause inconsistency and confusion for the customers. Option D is not optimal because it will deploy the new version of the application to two existing instances at a time, which may reduce the capacity below four instances during the deployment.
A developer needs to build an AWS CloudFormation template that self-populates the AWS Region variable that deploys the CloudFormation template. What is the MOST operationally efficient way to determine the Region in which the template is being deployed?
A. Use the AWS:.Region pseudo parameter
B. Require the Region as a CloudFormation parameter
C. Find the Region from the AWS::Stackld pseudo parameter by using the Fn::Split intrinsic function
D. Dynamically import the Region by referencing the relevant parameter in AWS Systems Manager Parameter Store
Explanation:
A developer is using AWS Step Functions to automate a workflow The workflow defines
each step as an AWS Lambda function task The developer notices that runs of the Step
Functions state machine fail in the GetResource task with either an
UlegalArgumentException error or a TooManyRequestsException error.
The developer wants the state machine to stop running when the state machine encounters
an UlegalArgumentException error. The state machine needs to retry the GetResource
task one additional time after 10 seconds if the state machine encounters a
TooManyRequestsException error. If the second attempt fails, the developer wants the
state machine to stop running.
How can the developer implement the Lambda retry functionality without adding
unnecessary complexity to the state machine'?
A. Add a Delay task after the GetResource task. Add a catcher to the GetResource task. Configure the catcher with an error type of TooManyRequestsException. Configure the next step to be the Delay task Configure the Delay task to wait for an interval of 10 seconds Configure the next step to be the GetResource task.
B. Add a catcher to the GetResource task Configure the catcher with an error type of TooManyRequestsException. an interval of 10 seconds, and a maximum attempts value of 1. Configure the next step to be the GetResource task.
C. Add a retrier to the GetResource task Configure the retrier with an error type of TooManyRequestsException, an interval of 10 seconds, and a maximum attempts value of 1.
D. Duplicate the GetResource task Rename the new GetResource task to TryAgain Add a catcher to the original GetResource task Configure the catcher with an error type of TooManyRequestsException. Configure the next step to be TryAgain.
Explanation:
Step Functions Retriers: Retriers provide a built-in way to gracefully handle
transient errors within State Machines. Here's how to use them:
A developer is building a web application that uses Amazon API Gateway to expose an
AWS Lambda function to process requests from clients. During testing, the developer
notices that the API Gateway times out even though the Lambda function finishes under
the set time limit.
Which of the following API Gateway metrics in Amazon CloudWatch can help the
developer troubleshoot the issue? (Choose two.)
A. CacheHitCount
B. IntegrationLatency
C. CacheMissCount
D. Latency
E. Count
Explanation: Amazon API Gateway is a service that enables developers to create, publish,
maintain, monitor, and secure APIs at any scale. Amazon CloudWatch is a service that
monitors AWS resources and applications. API Gateway provides several CloudWatch
metrics to help developers troubleshoot issues with their APIs. Two of the metrics that can
help the developer troubleshoot the issue of API Gateway timing out are:
A developer is creating an application that will be deployed on IoT devices. The application
will send data to a RESTful API that is deployed as an AWS Lambda function. The
application will assign each API request a unique identifier. The volume of API requests
from the application can randomly increase at any given time of day.
During periods of request throttling, the application might need to retry requests. The API
must be able to handle duplicate requests without inconsistencies or data loss.
Which solution will meet these requirements?
A. Create an Amazon RDS for MySQL DB instance. Store the unique identifier for each request in a database table. Modify the Lambda function to check the table for the identifier before processing the request.
B. Create an Amazon DynamoDB table. Store the unique identifier for each request in the table. Modify the Lambda function to check the table for the identifier before processing the request.
C. Create an Amazon DynamoDB table. Store the unique identifier for each request in the table. Modify the Lambda function to return a client error response when the function receives a duplicate request.
D. Create an Amazon ElastiCache for Memcached instance. Store the unique identifier for each request in the cache. Modify the Lambda function to check the cache for the identifier before processing the request.
Explanation: Amazon DynamoDB is a fully managed NoSQL database service that can store and retrieve any amount of data with high availability and performance. DynamoDB can handle concurrent requests from multiple IoT devices without throttling or data loss. To prevent duplicate requests from causing inconsistencies or data loss, the Lambda function can use DynamoDB conditional writes to check if the unique identifier for each request already exists in the table before processing the request. If the identifier exists, the function can skip or abort the request; otherwise, it can process the request and store the identifier in the table.
A developer built an application that calls an external API to obtain data, processes the
data, and saves the result to Amazon S3. The developer built a container image with all of
the necessary dependencies to run the application as a container.
The application runs locally and requires minimal CPU and RAM resources. The developer
has created an Amazon ECS cluster. The developer needs to run the application hourly in
Amazon ECS.
Which solution will meet these requirements with the LEAST amount of infrastructure
management overhead?
A. Add a capacity provider to manage instances.
B. Add an Amazon EC2 instance that runs the application.
C. Define a task definition with an AWS Fargate launch type.
D. Create an Amazon ECS cluster and add the managed node groups feature to run the application.
Explanation: Requirement Summary:
Containerized app
Runshourly
Minimal CPU and RAM
Goal:Least infrastructure management
Evaluate Options:
A. Add a capacity provider to manage instances
Capacity providers are used for managingEC2-backed ECS clusters, which still
requireunderlying EC2management.
B. Add an Amazon EC2 instance
Involvesmanaging infrastructure(provisioning, patching, scaling, etc.)
C. Use AWS Fargate launch type
Serverless containerruntime
No server management
Easily scheduled usingEventBridge + ECS Fargate Task
Best fit for periodic workloadslike this
D. Use managed node groups
Applies toEKS (Kubernetes), not ECS
Unnecessary overheadfor this use case
A company is providing read access to objects in an Amazon S3 bucket for different
customers. The company uses 1AM permissions to restrict access to the S3 bucket. The
customers can access only their own files.
Due to a regulation requirement, the company needs to enforce encryption in transit for
interactions with Amazon S3.
Which solution will meet these requirements?
A. Add a bucket policy to the S3 bucket to deny S3 actions when the aws:SecureTransport condition is equal to false.
B. Add a bucket policy to the S3 bucket to deny S3 actions when the s3:x-amz-acl condition is equal to public-read.
C. Add an 1AM policy to the 1AM users to enforce the usage of the AWS SDK.
D. Add an 1AM policy to the 1AM users that allows S3 actions when the s3:x-amz-acl condition is equal to bucket-owner-read.
| Page 4 out of 31 Pages |
| Previous |