A DevOps engineer is researching the least expensive way to implement an image batch
processing cluster on AWS. The application cannot run in Docker containers and must run
on Amazon EC2. The batch job stores checkpoint data on an NFS volume and can tolerate
interruptions. Configuring the cluster software from a generic EC2 Linux image takes 30
minutes.
What is the MOST cost-effective solution?
A. Use Amazon EFS (or checkpoint data. To complete the job, use an EC2 Auto Scaling group and an On-Demand pricing model to provision EC2 instances temporally.
B. Use GlusterFS on EC2 instances for checkpoint data. To run the batch job configure EC2 instances manually When the job completes shut down the instances manually.
C. Use Amazon EFS for checkpoint data Use EC2 Fleet to launch EC2 Spot Instances and utilize user data to configure the EC2 Linux instance on startup.
D. Use Amazon EFS for checkpoint data Use EC2 Fleet to launch EC2 Spot Instances Create a custom AMI for the cluster and use the latest AMI when creating instances.
A company deploys an application to Amazon EC2 instances. The application runs
Amazon Linux 2 and uses AWS CodeDeploy. The application has the following file
structure for its code repository:
The appspec.yml file has the following contents in the files section:
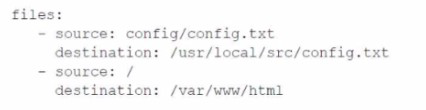
What will the result be for the deployment of the config.txt file?
A. The config.txt file will be deployed to only /var/www/html/config/config txt
B. The config.txt file will be deployed to /usr/local/src/config.txt and to /var/www/html/config/config txt.
C. The config.txt file will be deployed to only /usr/local/src/config txt
D. The config txt file will be deployed to /usr/local/src/config.txt and to /var/www/html/application/web/config txt
A company runs applications on Windows and Linux Amazon EC2 instances The instances
run across multiple Availability Zones In an AWS Region. The company uses Auto Scaling
groups for each application.
The company needs a durable storage solution for the instances. The solution must use
SMB for Windows and must use NFS for Linux. The solution must also have submillisecond
latencies. All instances will read and write the data.
Which combination of steps will meet these requirements? (Select THREE.)
A. Create an Amazon Elastic File System (Amazon EFS) file system that has targets in multiple Availability Zones
B. Create an Amazon FSx for NetApp ONTAP Multi-AZ file system.
C. Create a General Purpose SSD (gp3) Amazon Elastic Block Store (Amazon EBS) volume to use for shared storage.
D. Update the user data for each application's launch template to mount the file system
E. Perform an instance refresh on each Auto Scaling group.
F. Update the EC2 instances for each application to mount the file system when new instances are launched
A company uses an organization in AWS Organizations to manage its AWS accounts. The
company recently acquired another company that has standalone AWS accounts. The
acquiring company's DevOps team needs to consolidate the administration of the AWS
accounts for both companies and retain full administrative control of the accounts. The
DevOps team also needs to collect and group findings across all the accounts to implement
and maintain a security posture.
Which combination of steps should the DevOps team take to meet these requirements?
(Select TWO.)
A. Invite the acquired company's AWS accounts to join the organization. Create an SCP that has full administrative privileges. Attach the SCP to the management account.
B. Invite the acquired company's AWS accounts to join the organization. Create the OrganizationAccountAccessRole 1AM role in the invited accounts. Grant permission to the management account to assume the role.
C. Use AWS Security Hub to collect and group findings across all accounts. Use Security Hub to automatically detect new accounts as the accounts are added to the organization.
D. Use AWS Firewall Manager to collect and group findings across all accounts. Enable all features for the organization. Designate an account in the organization as the delegated administrator account for Firewall Manager.
E. Use Amazon Inspector to collect and group findings across all accounts. Designate an account in the organization as the delegated administrator account for Amazon Inspector.
Explanation: The correct answer is B and C. Option B is correct because inviting the acquired company’s AWS accounts to join the organization and creating the OrganizationAccountAccessRole IAM role in the invited accounts allows the management account to assume the role and gain full administrative access to the member accounts. Option C is correct because using AWS Security Hub to collect and group findings across all accounts enables the DevOps team to monitor and improve the security posture of the organization. Security Hub can automatically detect new accounts as the accounts are added to the organization and enable Security Hub for them. Option A is incorrect because creating an SCP that has full administrative privileges and attaching it to the management account does not grant the management account access to the member accounts. SCPs are used to restrict the permissions of the member accounts, not to grant permissions to the management account. Option D is incorrect because using AWS Firewall Manager to collect and group findings across all accounts is not a valid use case for Firewall Manager. Firewall Manager is used to centrally configure and manage firewall rules across the organization, not to collect and group security findings. Option E is incorrect because using Amazon Inspector to collect and group findings across all accounts is not a valid use case for Amazon Inspector. Amazon Inspector is used to assess the security and compliance of applications running on Amazon EC2 instances, not to collect and group security findings across accounts.
An application runs on Amazon EC2 instances behind an Application Load Balancer (ALB).
A DevOps engineer is using AWS CodeDeploy to release a new version. The deployment
fails during the AlIowTraffic lifecycle event, but a cause for the failure is not indicated in the
deployment logs.
What would cause this?
A. The appspec. yml file contains an invalid script that runs in the AllowTraffic lifecycle hook.
B. The user who initiated the deployment does not have the necessary permissions to interact with the ALB.
C. The health checks specified for the ALB target group are misconfigured.
D. The CodeDeploy agent was not installed in the EC2 instances that are pad of the ALB target group.
Explanation: This failure is typically due to incorrectly configured health checks in Elastic Load Balancing for the Classic Load Balancer, Application Load Balancer, or Network Load Balancer used to manage traffic for the deployment group. To resolve the issue, review and correct any errors in the health check configuration for the load balancer.
A company is implementing an Amazon Elastic Container Service (Amazon ECS) cluster to
run its workload. The company architecture will run multiple ECS services on the cluster.
The architecture includes an Application Load Balancer on the front end and uses multiple
target groups to route traffic.
A DevOps engineer must collect application and access logs. The DevOps engineer then
needs to send the logs to an Amazon S3 bucket for near-real-time analysis.
Which combination of steps must the DevOps engineer take to meet these requirements?
(Choose three.)
A. Download the Amazon CloudWatch Logs container instance from AWS. Configure this instance as a task. Update the application service definitions to include the logging task.
B. Install the Amazon CloudWatch Logs agent on the ECS instances. Change the logging driver in the ECS task definition to awslogs.
C. Use Amazon EventBridge to schedule an AWS Lambda function that will run every 60 seconds and will run the Amazon CloudWatch Logs create-export-task command. Then point the output to the logging S3 bucket.
D. Activate access logging on the ALB. Then point the ALB directly to the logging S3 bucket.
E. Activate access logging on the target groups that the ECS services use. Then send the logs directly to the logging S3 bucket.
F. Create an Amazon Kinesis Data Firehose delivery stream that has a destination of the logging S3 bucket. Then create an Amazon CloudWatch Logs subscription filter for Kinesis Data Firehose.
A company's development team uses AVMS Cloud Formation to deploy its application
resources The team must use for an changes to the environment The team cannot use
AWS Management Console or the AWS CLI to make manual changes directly.
The team uses a developer IAM role to access the environment The role is configured with
the Admnistratoraccess managed policy. The company has created a new
Cloudformationdeployment IAM role that has the following policy.
The company wants ensure that only CloudFormation can use the new role. The development team cannot make any manual changes to the deployed resources.
Which combination of steps meet these requirements? (Select THREE.)
A. Remove the AdministratorAccess policy. Assign the ReadOnIyAccess managed IAM policy to the developer role. Instruct the developers to use the CloudFormationDeployment role as a CloudFormation service role when the developers deploy new stacks.
B. Update the trust of CloudFormationDeployment role to allow the developer IAM role to assume the CloudFormationDepoyment role.
C. Configure the IAM to be to get and pass the CloudFormationDeployment role if cloudformation actions for resources,
D. Update the trust Of the CloudFormationDepoyment role to anow the cloudformation.amazonaws.com AWS principal to perform the iam:AssumeR01e action
E. Remove me Administratoraccess policy. Assign the ReadOnly/Access managed IAM policy to the developer role Instruct the developers to assume the CloudFormatondeployment role when the developers new stacks
F. Add an IAM policy to CloudFormationDeplyment to allow cloudformation * on an Add a policy that allows the iam.PassR01e action for ARN of if iam PassedT0Service equal cloudformation.amazonaws.com
A DevOps engineer is setting up an Amazon Elastic Container Service (Amazon ECS)
blue/green deployment for an application by using AWS CodeDeploy and AWS
CloudFormation. During the deployment window, the application must be highly available
and CodeDeploy must shift 10% of traffic to a new version of the application every minute
until all traffic is shifted.
Which configuration should the DevOps engineer add in the CloudFormation template to meet these requirements?
A. Add an AppSpec file with the CodeDeployDefault.ECSLineaMOPercentEverylMinutes deployment configuration.
B. Add the AWS::CodeDeployBlueGreen transform and the AWS::CodeDeploy::BlueGreen hook parameter with the CodeDeployDefault.ECSLinear10PercentEvery1 Minutes deployment configuration.
C. Add an AppSpec file with the ECSCanary10Percent5Minutes deployment configuration.
D. Add the AWS::CodeDeployBlueGroen transform and the AWS::CodeDeploy::BlueGreen hook parameter with the ECSCanary10Percent5Minutes deployment configuration
A company has a fleet of Amazon EC2 instances that run Linux in a single AWS account.
The company is using an AWS Systems Manager Automation task across the EC2
instances.
During the most recent patch cycle, several EC2 instances went into an error state
because of insufficient available disk space. A DevOps engineer needs to ensure that the
EC2 instances have sufficient available disk space during the patching process in the
future.
Which combination of steps will meet these requirements? {Select TWO.)
A. Ensure that the Amazon CloudWatch agent is installed on all EC2 instances
B. Create a cron job that is installed on each EC2 instance to periodically delete temporary files.
C. Create an Amazon CloudWatch log group for the EC2 instances. Configure a cron job that is installed on each EC2 instance to write the available disk space to a CloudWatch log stream for the relevant EC2 instance.
D. Create an Amazon CloudWatch alarm to monitor available disk space on all EC2 instances Add the alarm as a safety control to the Systems Manager Automation task.
E. Create an AWS Lambda function to periodically check for sufficient available disk space on all EC2 instances by evaluating each EC2 instance's respective Amazon CloudWatch log stream.
Explanation:
Ensure that the Amazon CloudWatch agent is installed on all EC2 instances:
The Amazon CloudWatch agent collects and logs metrics and sends them to
Amazon CloudWatch.
To install the CloudWatch agent:
Create an Amazon CloudWatch alarm to monitor available disk space on all EC2
instances Add the alarm as a safety control to the Systems Manager Automation task:
Create CloudWatch alarms to monitor the available disk space and trigger
notifications or actions when the disk space falls below a defined threshold.
Add the CloudWatch alarm to the Systems Manager Automation task to halt or fail
the task if disk space is insufficient.
A DevOps engineer is creating an AWS CloudFormation template to deploy a web service.
The web service will run on Amazon EC2 instances in a private subnet behindan
Application Load Balancer (ALB). The DevOps engineer must ensure that the service can
accept requests from clients that have IPv6 addresses.
What should the DevOps engineer do with the CloudFormation template so that IPv6
clients can access the web service?
A. Add an IPv6 CIDR block to the VPC and the private subnet for the EC2 instances. Create route table entries for the IPv6 network, use EC2 instance types that support IPv6, and assign IPv6 addresses to each EC2 instance.
B. Assign each EC2 instance an IPv6 Elastic IP address. Create a target group, and add the EC2 instances as targets. Create a listener on port 443 of the ALB, and associate the target group with the ALB.
C. Replace the ALB with a Network Load Balancer (NLB). Add an IPv6 CIDR block to the VPC and subnets for the NLB, and assign the NLB an IPv6 Elastic IP address.
D. Add an IPv6 CIDR block to the VPC and subnets for the ALB. Create a listener on port 443. and specify the dualstack IP address type on the ALB. Create a target group, and add the EC2 instances as targets. Associate the target group with the ALB.
Explanation: it involves adding an IPv6 CIDR block to the VPC and subnets for the ALB and specifying the dualstack IP address type on the ALB listener. This allows the ALB to listen on both IPv4 and IPv6 addresses, and forward requests to the EC2 instances that are added as targets to the target group associated with the ALB.
A company uses AWS Key Management Service (AWS KMS) keys and manual key
rotation to meet regulatory compliance requirements. The security team wants to be
notified when any keys have not been rotated after 90 days.
Which solution will accomplish this?
A. Configure AWS KMS to publish to an Amazon Simple Notification Service (Amazon SNS) topic when keys are more than 90 days old.
B. Configure an Amazon EventBridge event to launch an AWS Lambda function to call the AWS Trusted Advisor API and publish to an Amazon Simple Notification Service (Amazon SNS) topic.
C. Develop an AWS Config custom rule that publishes to an Amazon Simple Notification Service (Amazon SNS) topic when keys are more than 90 days old.
D. Configure AWS Security Hub to publish to an Amazon Simple Notification Service (Amazon SNS) topic when keys are more than 90 days old.
A company has developed a serverless web application that is hosted on AWS. The
application consists of Amazon S3. Amazon API Gateway, several AWS Lambda functions,
and an Amazon RDS for MySQL database. The company is using AWS CodeCommit to
store the source code. The source code is a combination of AWS Serverless Application
Model (AWS SAM) templates and Python code.
A security audit and penetration test reveal that user names and passwords for
authentication to the database are hardcoded within CodeCommit repositories. A DevOps
engineer must implement a solution to automatically detect and prevent hardcoded secrets.
What is the MOST secure solution that meets these requirements?
A. Enable Amazon CodeGuru Profiler. Decorate the handler function with @with_lambda_profiler(). Manually review the recommendation report. Write the secret to AWS Systems Manager Parameter Store as a secure string. Update the SAM templates and the Python code to pull the secret from Parameter Store.
B. Associate the CodeCommit repository with Amazon CodeGuru Reviewer. Manually check the code review for any recommendations. Choose the option to protect the secret. Update the SAM templates and the Python code to pull the secret from AWS Secrets Manager.
C. Enable Amazon CodeGuru Profiler. Decorate the handler function with @with_lambda_profiler(). Manually review the recommendation report. Choose the option to protect the secret. Update the SAM templates and the Python code to pull the secret from AWS Secrets Manager.
D. Associate the CodeCommit repository with Amazon CodeGuru Reviewer. Manually check the code review for any recommendations. Write the secret to AWS Systems Manager Parameter Store as a string. Update the SAM templates and the Python code to pull the secret from Parameter Store.
| Page 7 out of 21 Pages |
| Previous |