A company plans to build an entirely remote workforce that utilizes a cloud-based
infrastructure. The Chief Information Security Officer asks the security engineer to design
connectivity to meet the following requirements:
Only users with corporate-owned devices can directly access servers hosted by the cloud
provider.
The company can control what SaaS applications each individual user can access.
User browser activity can be monitored.
Which of the following solutions would BEST meet these requirements?
A.
IAM gateway, MDM, and reverse proxy
B.
VPN, CASB, and secure web gateway
C.
SSL tunnel, DLP, and host-based firewall
D.
API gateway, UEM, and forward proxy
VPN, CASB, and secure web gateway
After a security incident, a network security engineer discovers that a portion of the
company’s sensitive external traffic has been redirected through a secondary ISP that is
not normally used.
Which of the following would BEST secure the routes while allowing the network to function
in the event of a single provider failure?
A.
Disable BGP and implement a single static route for each internal network.
B.
Implement a BGP route reflector.
C.
Implement an inbound BGP prefix list.
D.
Disable BGP and implement OSPF.
Implement a BGP route reflector.
A company that uses AD is migrating services from LDAP to secure LDAP. During the pilot
phase, services are not connecting properly to secure LDAP. Block is an except of output
from the troubleshooting session: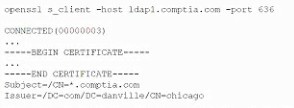
Which of the following BEST explains why secure LDAP is not working? (Select TWO.)
A.
The clients may not trust idapt by default.
B.
The secure LDAP service is not started, so no connections can be made.
C.
Danvills.com is under a DDoS-inator attack and cannot respond to OCSP requests.
D.
Secure LDAP should be running on UDP rather than TCP.
E.
The company is using the wrong port. It should be using port 389 for secure LDAP.
F.
Secure LDAP does not support wildcard certificates.
G.
The clients may not trust Chicago by default.
The secure LDAP service is not started, so no connections can be made.
The company is using the wrong port. It should be using port 389 for secure LDAP.
A security is assisting the marketing department with ensuring the security of the
organization’s social media platforms. The two main concerns are:
The Chief marketing officer (CMO) email is being used department wide as the username
The password has been shared within the department
Which of the following controls would be BEST for the analyst to recommend?
A.
Configure MFA for all users to decrease their reliance on other authentication.
B.
Have periodic, scheduled reviews to determine which OAuth configuration are set for
each media platform.
C.
Create multiple social media accounts for all marketing user to separate their actions.
D.
Ensue the password being shared is sufficiently and not written down anywhere.
Configure MFA for all users to decrease their reliance on other authentication.
A company is looking for a solution to hide data stored in databases. The solution must
meet the following requirements:
Be efficient at protecting the production environment
Not require any change to the application
Act at the presentation layer
Which of the following techniques should be used?
A.
Masking
B.
Tokenization
C.
Algorithmic
D.
Random substitution
Masking
A security analyst receives an alert from the SIEM regarding unusual activity on an
authorized public SSH jump server. To further investigate, the analyst pulls the event logs
directly from /var/log/auth.log: graphic.ssh_auth_log.
Which of the following actions would BEST address the potential risks by the activity in the
logs?
A.
Alerting the misconfigured service account password
B.
Modifying the AllowUsers configuration directive
C.
Restricting external port 22 access
D.
Implementing host-key preferences
Restricting external port 22 access
Reference: https://www.rapid7.com/blog/post/2017/10/04/how-to-secure-ssh-server-usingport-
knocking-on-ubuntu-linux/
Which of the following are risks associated with vendor lock-in? (Choose two.)
A.
The client can seamlessly move data.
B.
The vendor can change product offerings.
C.
The client receives a sufficient level of service.
D.
The client experiences decreased quality of service.
E.
The client can leverage a multicloud approach.
F.
The client experiences increased interoperability.
The vendor can change product offerings.
The client experiences decreased quality of service.
Reference: https://www.cloudflare.com/learning/cloud/what-is-vendor-lockin/#:~:
text=Vendor-lock%2Din-can-become,may-involve-reformatting%2
0the-data
A security engineer was auditing an organization’s current software development practice
and discovered that multiple open-source libraries were Integrated into the organization’s
software. The organization currently performs SAST and DAST on the software it develops.
Which of the following should the organization incorporate into the SDLC to ensure the
security of the open-source libraries?
A.
Perform additional SAST/DAST on the open-source libraries.
B.
Implement the SDLC security guidelines.
C.
Track the library versions and monitor the CVE website for related vulnerabilities.
D.
Perform unit testing of the open-source libraries.
Implement the SDLC security guidelines.
Reference: https://www.whitesourcesoftware.com/resources/blog/application-security-bestpractices/
A security engineer has been asked to close all non-secure connections from the corporate network. The engineer is attempting to understand why the corporate UTM will not allow users to download email via IMAPS. The engineer formulates a theory and begins testing by creating the firewall ID 58, and users are able to download emails correctly by using IMAP instead. The network comprises three VLANs:

Which of the following should the security engineer do to ensure IMAPS functions properly
on the corporate user network?
A.
Contact the email service provider and ask if the company IP is blocked.
B.
Confirm the email server certificate is installed on the corporate computers.
C.
Make sure the UTM certificate is imported on the corporate computers.
D.
Create an IMAPS firewall rule to ensure email is allowed.
Make sure the UTM certificate is imported on the corporate computers.
Which of the following is the MOST important security objective when applying
cryptography to control messages that tell an ICS how much electrical power to output?
A.
Importing the availability of messages
B.
Ensuring non-repudiation of messages
C.
Enforcing protocol conformance for messages
D.
Assuring the integrity of messages
Assuring the integrity of messages
Company A is establishing a contractual with Company B. The terms of the agreement are
formalized in a document covering the payment terms, limitation of liability, and intellectual
property rights. Which of the following documents will MOST likely contain these elements
A.
Company A-B SLA v2.docx
B.
Company A OLA v1b.docx
C.
Company A MSA v3.docx
D.
Company A MOU v1.docx
E.
Company A-B NDA v03.docx
Company A-B SLA v2.docx
An application server was recently upgraded to prefer TLS 1.3, and now users are unable
to connect their clients to the server. Attempts to reproduce the error are confirmed, and
clients are reporting the following:
ERR_SSL_VERSION_OR_CIPHER_MISMATCH
Which of the following is MOST likely the root cause?
A.
The client application is testing PFS.
B.
The client application is configured to use ECDHE.
C.
The client application is configured to use RC4.
D.
The client application is configured to use AES-256 in GCM
The client application is configured to use RC4.
Reference: https://kinsta.com/knowledgebase/err_ssl_version_or_cipher_mismatch/
| Page 3 out of 17 Pages |
| Previous |