Refer to the exhibit.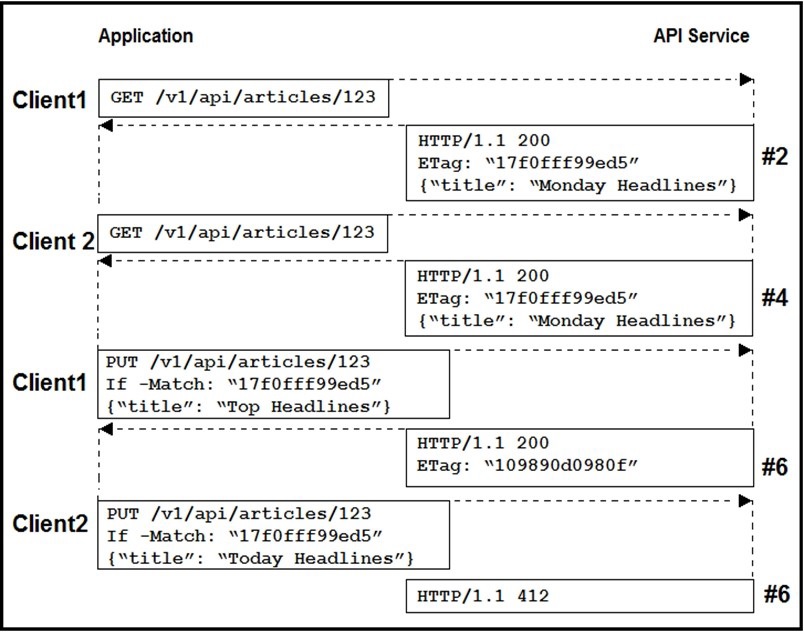
Two editors are concurrently updating an article’s headline from their mobile devices. What
results from this scenario based on this REST API sequence?
A.
The article is marked as “Conflicted”
B.
The article headline is “Monday Headlines”
C.
The article headline is “Today Headlines”
D.
The article headline is “Top Headlines
The article headline is “Top Headlines
A developer plans to create a new bugfix branch to fix a bug that was found on the release
branch. Which command completes the task?
A.
git checkout -b RELEASE BUGFIX
B.
git checkout -t BUGF1X RELEASE
C.
git checkout -b BUG FIX RELEASE
D.
git checkout -t RELEASE BUGFIX
git checkout -b BUG FIX RELEASE
While working with the Webex Teams API, on an application that uses end-to-end
encryption, a webhook has
been received. What must be considered to read the message?
A.
Webhook information cannot be used to read the message because of end-to-end
encryption. The API key
is needed to decrypt the message.
B.
Webhook returns the full unencrypted message. Only the body is needed to query the
API.
C.
Webhook returns a hashed version of the message that must be unhashed with the API
key.
D.
Webhook returns message identification. To query, the API is needed for that message
to get the decrypted
information.
Webhook information cannot be used to read the message because of end-to-end
encryption. The API key
is needed to decrypt the message.
Which two actions must be taken when an observable microservice application is
developed? (Choose two.)
A.
Know the state of a single instance of a single service.
B.
Place “try/except” statement in code.
C.
Place log statements in the code.
D.
Use distributed tracing techniques.
E.
Deploy microservice to multiple datacenters.
Place log statements in the code.
Use distributed tracing techniques.
Refer to the exhibit.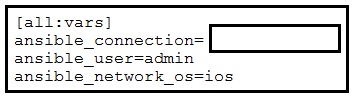
An engineer is configuring Ansible to run playbooks against Cisco IOS XE Software. What
should be configured in ansible.cfg as the connection type?
A.
network_cli
B.
ssh
C.
shell
D.
command
ssh
A network operations team is using the cloud to automate some of their managed customer
and branch locations. They require that all of their tooling be ephemeral by design and that
the entire automation environment can be recreated without manual commands.
Automation code and configuration state will be stored in git for change control and
versioning. The engineering high-level plan is to use VMs in a cloud- provider environment
then configure open source tooling onto these VMs to poll, test, and configure the remote
devices, as well as deploy the tooling itself.
Which configuration management and/or automation tooling is needed for this solution?
A.
Ansible
B.
Ansible and Terraform
C.
NSO
D.
Terraform
E.
Ansible and NSO
Ansible and Terraform
What are two features of On-Box Python for hosting an application on a network device?
(Choose two.)
A.
It has direct access to Cisco IOS XE CLI commands.
B.
It is a Python interpreter installed inside the guest shell.
C.
It enables execution of XML scripts on a Cisco IOS XE router or switch.
D.
It supports Qt for graphical interfaces and dashboards.
E.
It has access to Cisco IOS XE web UI through a controller
It has direct access to Cisco IOS XE CLI commands.
It is a Python interpreter installed inside the guest shell.
Refer to the exhibit.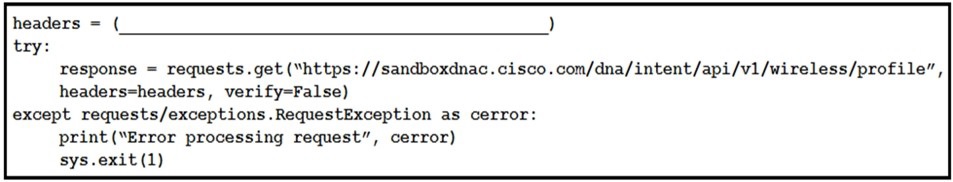
Which code snippet is required in the headers to successfully authorize wireless
information from Cisco DNA Center?
A.
headers = {‘X-auth-token’:’fa8426a0-8eaf-4d22-8e13-7c1b16a9370c’}
B.
headers = {‘Authorization’:’Basic YWRtaW46R3JhcGV2aW5IMQ==’}
C.
headers = {‘Authorization’:’Bearer ASDNFALKJER23412RKDALSNKF”}
D.
headers = {‘Content-type’:’application/json}
headers = {‘X-auth-token’:’fa8426a0-8eaf-4d22-8e13-7c1b16a9370c’}
Drag and drop the REST API authentication method from the left to the description on the
right
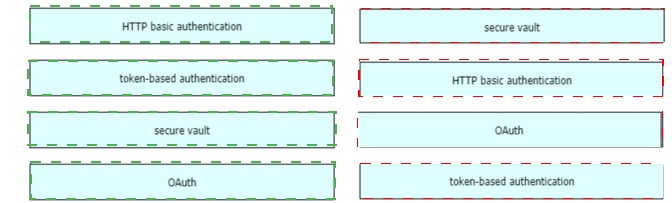
A container running a Python script is failing when it reaches the integration testing phase
of the CI/CD process. The code has been reviewed thoroughly and the build process works
on this container and all other containers pass unit and integration testing.
What should be verified to resolve the issue?
A.
that the correct port is exposed in the Dockerfile
B.
that the necessary modules and packages are installed on build
C.
that the script is running from the right directory
D.
that the Python version of the container image is correct
that the correct port is exposed in the Dockerfile
Refer to the exhibit.
A kubeconfig file to manage access to clusters is provided. How many clusters are defined and which of them are accessed using username/password authentication versus
certificate?
A.
two clusters; scratch
B.
three clusters; scratch
C.
three clusters; development
D.
two clusters; development
two clusters; scratch
Which two statements are considered best practices according to the 12-factor app
methodology for application design? (Choose two.)
A.
Application code writes its event stream to stdout.
B.
Application log streams are archived in multiple replicated databases.
C.
Application log streams are sent to log indexing and analysis systems.
D.
Application code writes its event stream to specific log files.
E.
Log files are aggregated into a single file on individual nodes.
Application code writes its event stream to stdout.
Application log streams are sent to log indexing and analysis systems.
| Page 6 out of 15 Pages |
| Previous |