Refer to the exhibit.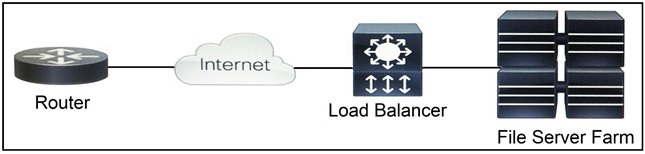
Which two functions are performed by the load balancer when it handles traffic originating
from the Internet destined to an application hosted on the file server farm? (Choose two.)
A.
the TLS over the UDP connection from the router and originate an HTTPS
connection to the selected server.
B.
Terminate the TLS over the UDP connection from the router and originate an HTTP
connection to the selected server.
C.
Terminate the TLS over the TCP connection from the router and originate an HTTP
connection to the selected server.
D.
Terminate the TLS over the TCP connection from the router and originate an HTTPS
connection to the selected server.
E.
Terminate the TLS over the SCTP connection from the router and originate an HTTPS
connection to the selected server.
Terminate the TLS over the TCP connection from the router and originate an HTTP
connection to the selected server.
Terminate the TLS over the TCP connection from the router and originate an HTTPS
connection to the selected server.

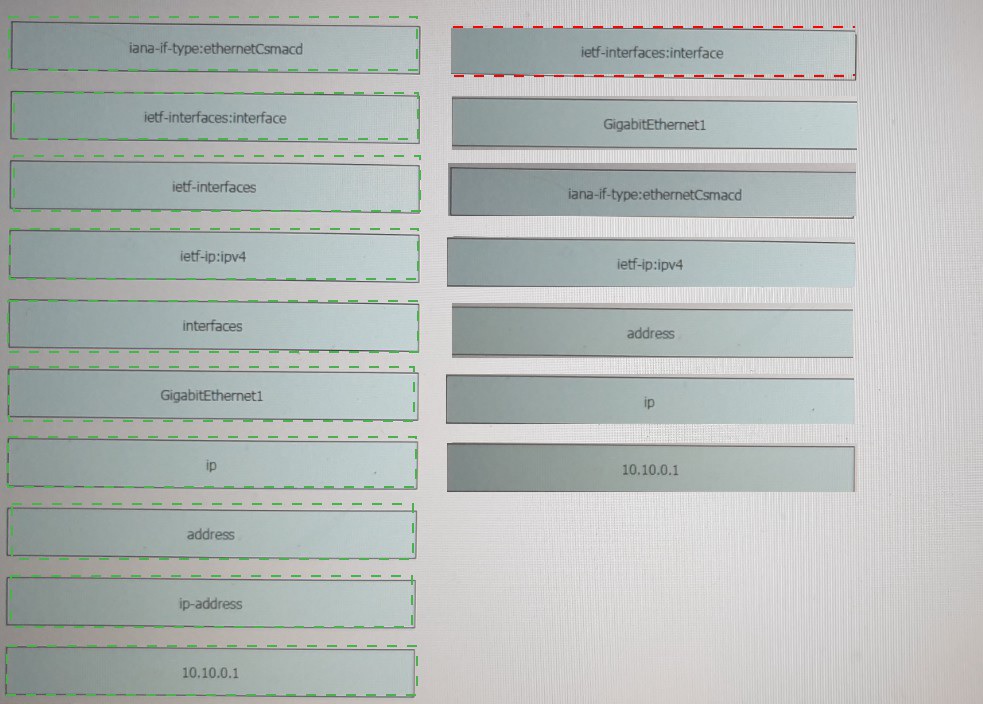
Refer to the exhibit.
Which key value pair from the ios_ntp Ansible module creates an NTP server peer?
A.
state: present
B.
state: True
C.
config: present
D.
config: True
state: present
Refer to the exhibit.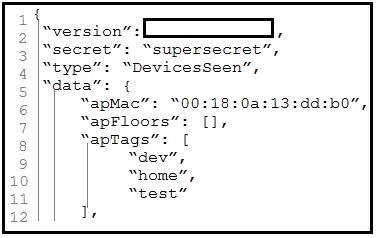
Which parameter is missing from the JSON response to confirm the API version that is
used?
A.
version 4
B.
v 10
C.
2
D.
version 2
2
Which two data encoding techniques are supported by gRPC? (Choose two.)
A.
XML
B.
JSON
C.
ASCII
D.
ProtoBuf
E.
YAML
JSON
ProtoBuf
Refer to the exhibit
Which action will complete the workflow that represents how an API call sends multiple
messages?
A.
{PUT} messages(roomID)
B.
{PUT} messages(BearerToken)
C.
{POST} messages(roomID)
D.
{POST} messages(BearerToken)
{PUT} messages(BearerToken)
A client is written that uses a REST API to interact with a server. Using HTTPS as the
transport, an HTTP request is sent and received an HTTP response. The response
contains the HTTP response status code: 503 Service Unavailable.
Which action is the appropriate response?
A.
Add an Authorization header that supplies appropriate credentials and sends the
updated request.
B.
Resend the request using HTTP as the transport instead of HTTPS.
C.
Add an Accept header that indicates the content types that the client understands and
send the updated request.
D.
Look for a Retry-After header in the response and resend the request after the amount
of time indicated.
Look for a Retry-After header in the response and resend the request after the amount
of time indicated.
The Meraki API URL https://api.meraki.com/api/v0/networks/123456789/ssids/2 has been
stored in the environment variable meraki_url and the API key has been stored in
meraki_api_key. Which snippet presents the API call to configure, secure and enable an
SSID using the Meraki API?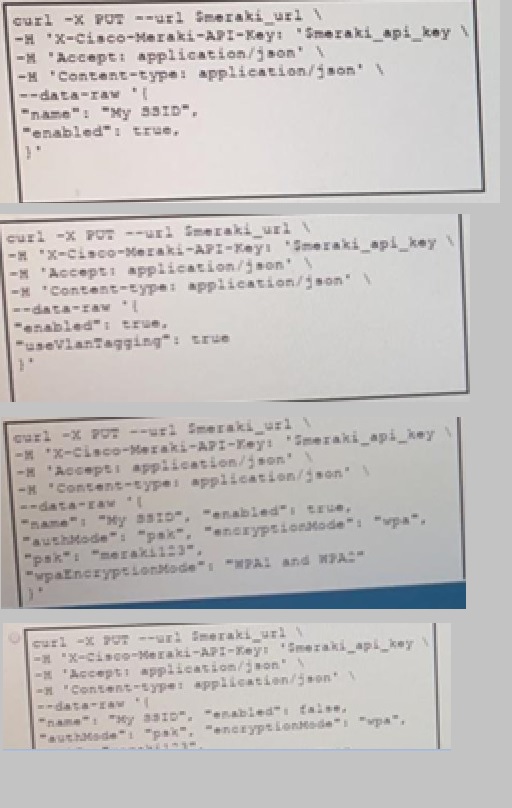
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option C

Which two techniques protect against injection attacks? (Choose two.)
A.
input validation
B.
trim whitespace
C.
limit text areas to 255 characters
D.
string escaping of user free text and data entry
E.
only use dropdown, checkbox, and radio button fields
input validation
string escaping of user free text and data entry
What are two principles according to the build, release, run principle of the twelve-factor
app methodology?
(Choose two.)
A.
Code changes are able to be made at runtime.
B.
Separation between the build, release, and run phases.
C.
Releases should have a unique identifier.
D.
Existing releases are able to be mutated after creation.
E.
Release stage is responsible for compilation of assets and binaries
Separation between the build, release, and run phases.
Releases should have a unique identifier.
Reference: https://www.bmc.com/blogs/twelve-factor-app/
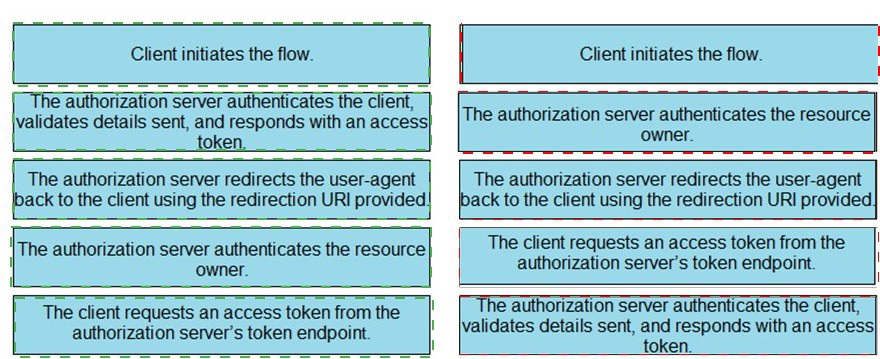
Refer to the exhibit.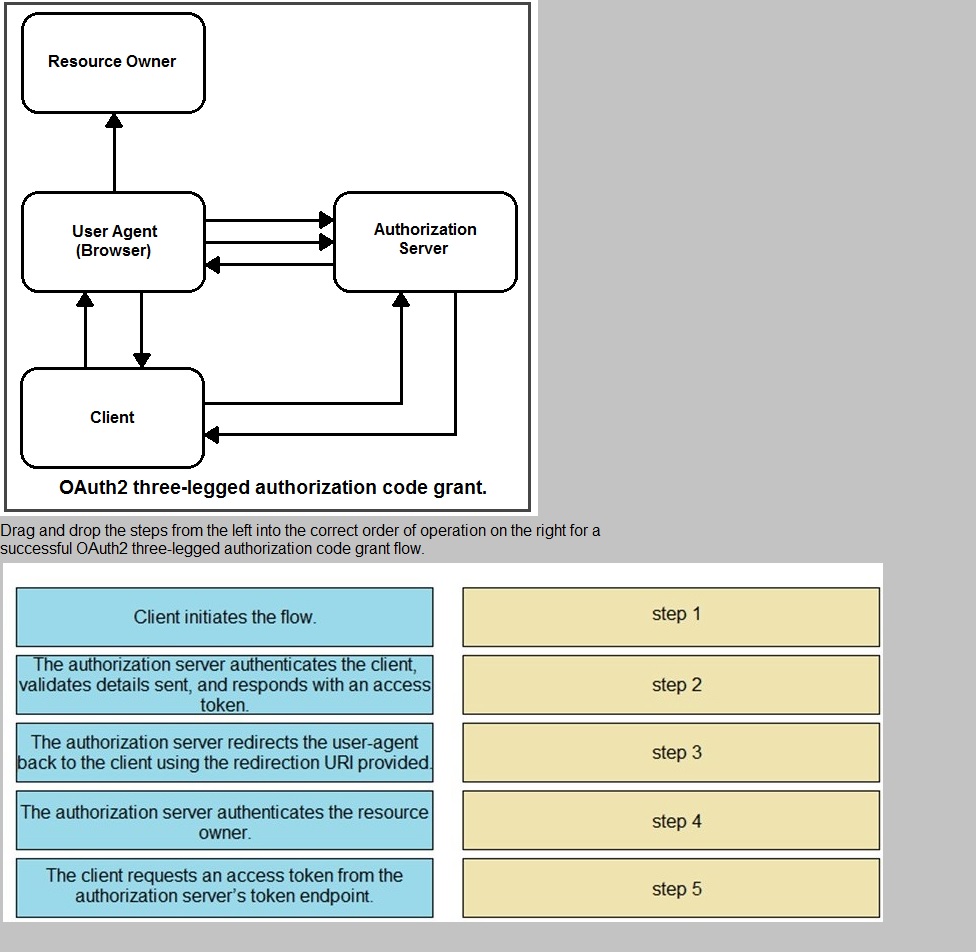
| Page 5 out of 15 Pages |
| Previous |