A web application is susceptible to cross-site scripting. Which two methods allow this issue
to be mitigated? (Choose two.)
A.
Use only drop downs.
B.
Limit user input to acceptable characters.
C.
Encrypt user input on the client side.
D.
Use AES encryption to secure the script.
E.
Remove all HTML/XML tags from user input.
Limit user input to acceptable characters.
Remove all HTML/XML tags from user input.
How should a web application be designed to work on a platform where up to 1000 requests per second can be served?
A.
Use algorithms like random early detection to deny excessive requests.
B.
Set a per-user limit (for example, 5 requests/minute/user) and deny the requests from
the users who have reached the limit.
C.
Only 1000 user connections are allowed; further connections are denied so that all
connected users can be served.
D.
All requests are saved and processed one by one so that all users can be served
eventually.
Set a per-user limit (for example, 5 requests/minute/user) and deny the requests from
the users who have reached the limit.
Drag and drop the expressions from below onto the code to implement error handling. Not
all options are used.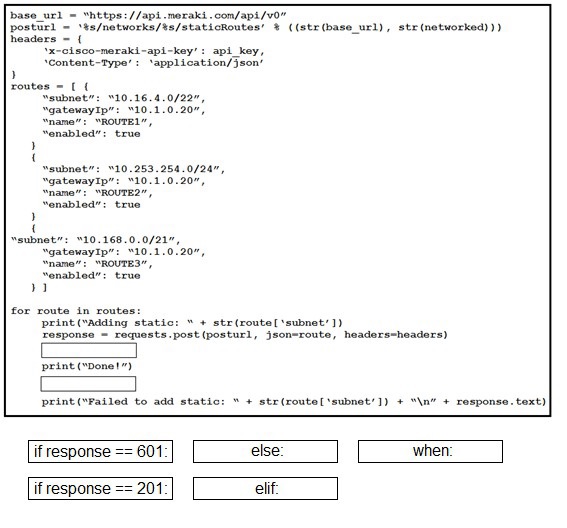
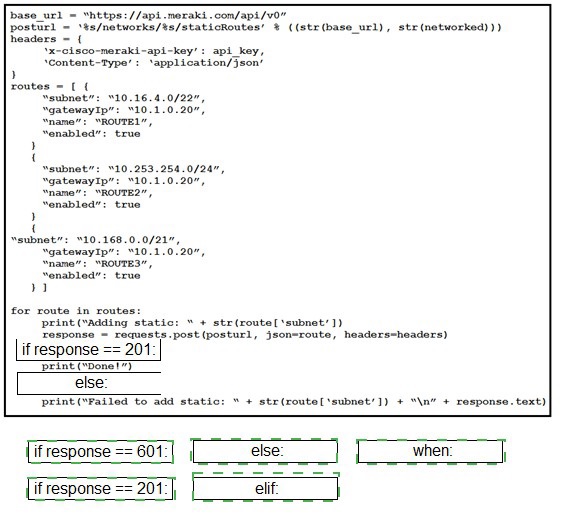
Refer to the exhibit.
A.
Option A
B.
Option B
C.
Option C
D.
Option D
Option A
A developer has created an application based on customer requirements. The customer
needs to run the application with the minimum downtime. Which design approach regarding
high-availability applications, Recovery Time Objective, and Recovery Point Objective must
be taken?
A.
Active/passive results in lower RTO and RPO. For RPO, data synchronization between
the two data centers must be timely to allow seamless request flow.
B.
Active/passive results in lower RTO and RPO. For RPO, data synchronization between
the two data centers does not need to be timely to allow seamless request flow.
C.
Active/active results in lower RTO and RPO. For RPO, data synchronization between
the two data centers does not need to be timely to allow seamless request flow.
D.
Active/active results in lower RTO and RPO. For RPO, data synchronization between
the two data centers must be timely to allow seamless request flow.
Active/passive results in lower RTO and RPO. For RPO, data synchronization between
the two data centers must be timely to allow seamless request flow.
Refer to the exhibit.
An application's REST API GET call is tested to the inventory database. Which missing
code must be included to limit
the number of values that are returned from the query to 20?
A.
?mventory=20
B.
limit=?2Q
C.
inventory=limit?20
D.
inventory? Iimit20
inventory? Iimit20
Which two types of storage are supported for app hosting on a Cisco Catalyst 9000 Series
Switch? (Choose two.)
A.
external USB storage
B.
internal SSD
C.
CD-ROM
D.
SD-card
E.
bootflash
external USB storage
internal SSD
Which two types of storage are supported for app hosting on a Cisco Catalyst 9000 Series Switch? (Choose two.)
A.
external USB storage
B.
internal SSD
C.
CD-ROM
D.
SD-card
E.
bootflash
external USB storage
internal SSD
Drag and drop the code from the bottom onto the box where the code is missing on the
Ansible task to enable a VLAN on a Meraki MX Device, Not all options are used

A developer deploys a SQLite database in a Docker container. Single-use secret keys are
generated each time
a user accesses the database. The keys expire after 24 hours. Where should the keys be
stored?
A.
Outside of the Docker container in the source code of applications that connect to the
SQLite database.
B.
In a separate file inside the Docker container that runs the SQLite database.
C.
In an encrypted database table within the SQLite database.
D.
In a separate storage volume within the Docker container.
In a separate storage volume within the Docker container.
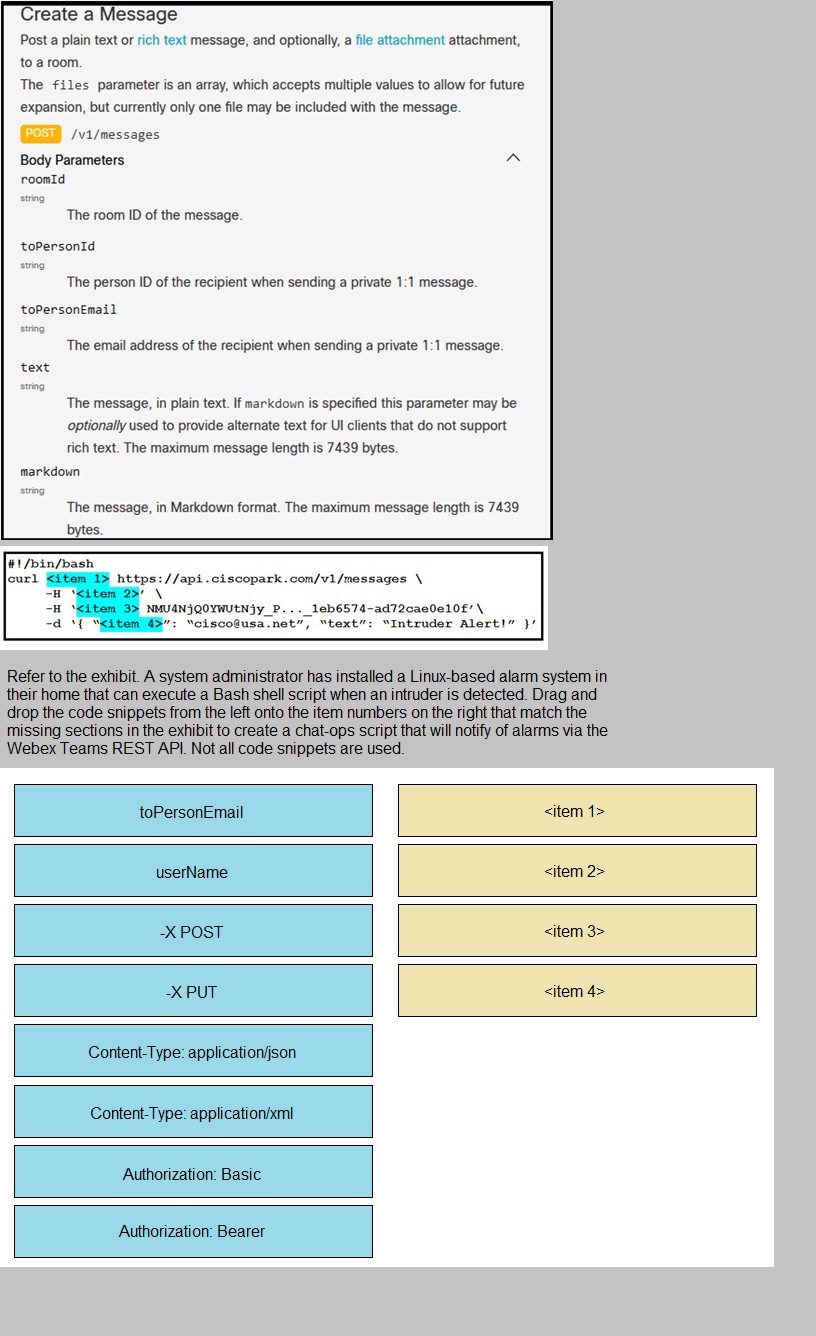
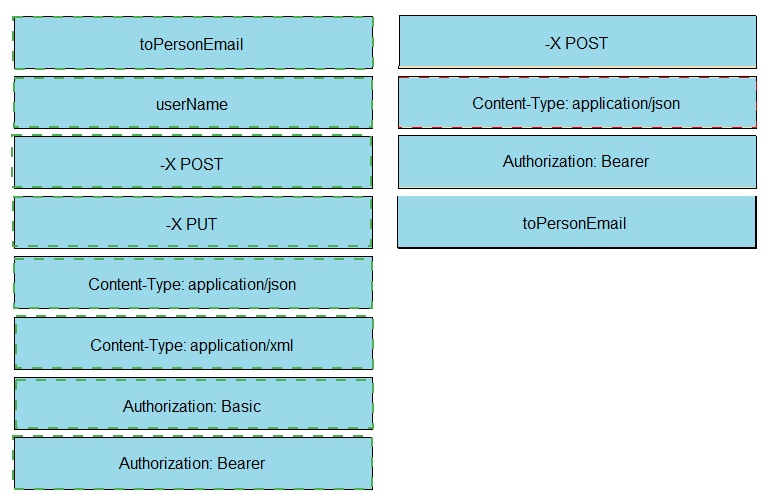

| Page 3 out of 15 Pages |
| Previous |