Topic 2: Exam Pool B
Which type of algorithm provides the highest level of protection against brute-force attacks?
A.
PFS
B.
HMAC
C.
MD5
D.
SHA
SHA
What is a difference between FlexVPN and DMVPN?
A.
DMVPN uses IKEv1 or IKEv2, FlexVPN only uses IKEv1
B.
DMVPN uses only IKEv1 FlexVPN uses only IKEv2
C.
FlexVPN uses IKEv2, DMVPN uses IKEv1 or IKEv2
D.
FlexVPN uses IKEv1 or IKEv2, DMVPN uses only IKEv2
FlexVPN uses IKEv2, DMVPN uses IKEv1 or IKEv2
When configuring ISAKMP for IKEv1 Phase1 on a Cisco IOS router, an administrator
needs to input the
command crypto isakmp key cisco address 0.0.0.0. The administrator is not sure what the
IP addressing in this command issued for. What would be the effect of changing the IP
address from 0.0.0.0 to 1.2.3.4?
A.
The key server that is managing the keys for the connection will be at 1.2.3.4
B.
The remote connection will only be allowed from 1.2.3.4
C.
The address that will be used as the crypto validation authority
D.
All IP addresses other than 1.2.3.4 will be allowed
The remote connection will only be allowed from 1.2.3.4
The command crypto isakmp key cisco address 1.2.3.4
authenticates the IP address of the 1.2.3.4 peer by using the key cisco. The address of “0.0.0.0” will authenticate any address with this key.
Which two features of Cisco Email Security can protect your organization against email threats? (Choose two)
A.
Time-based one-time passwords
B.
Data loss prevention
C.
Heuristic-based filtering
D.
Geolocation-based filtering
E.
NetFlow
Data loss prevention
Geolocation-based filtering
https://www.cisco.com/c/en/us/td/docs/security/esa/esa11-
0/user_guide_fs/b_ESA_Admin_Guide_11_0/b_ESA_Admin_Guide_chapter_00.html
Drag and drop the VPN functions from the left onto the description on the right.
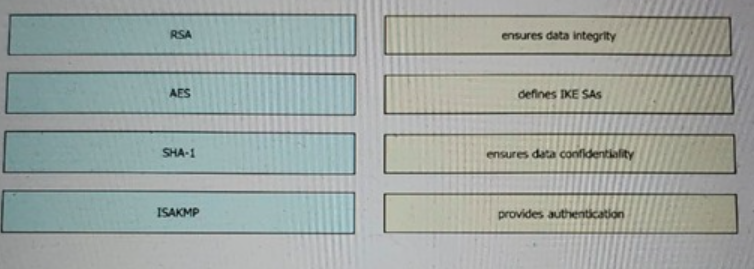
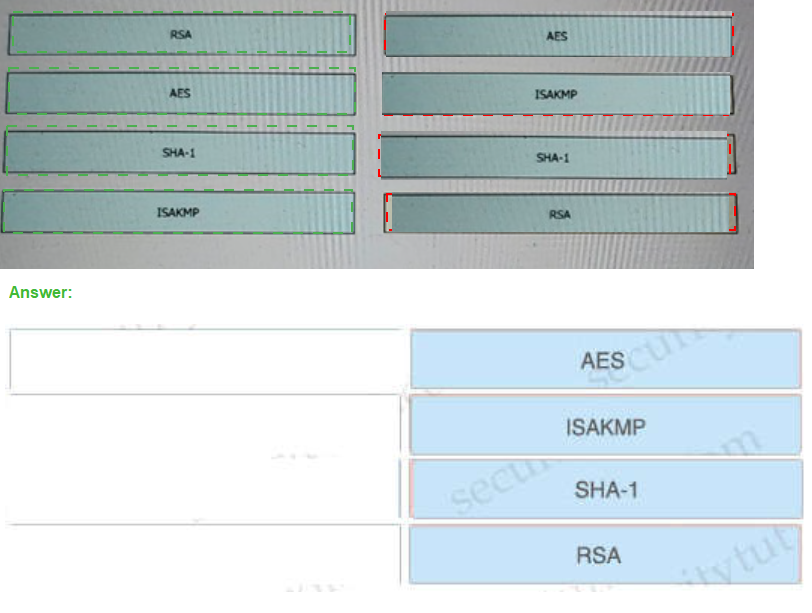
The purpose of message integrity algorithms, such as Secure Hash Algorithm
(SHA-1), ensures data has notbeen changed in transit. They use one way hash functions to determine if data has been changed.SHA-1, which is also known as HMAC-SHA-1 is a
strong cryptographic hashing algorithm, stronger thananother popular algorithm known as
Message Digest 5 (MD5). SHA-1 is used to provide data integrity (toguarantee data has not
been altered in transit) and authentication (to guarantee data came from the source itwas
supposed to come from). SHA was produced to be used with the digital signature
standard.A VPN uses groundbreaking 256-bit AES encryption technology to secure your
online connection againstcyberattacks that can compromise your security. It also offers
robust protocols to combat malicious attacks and reinforce your online identity.IKE SAs
describe the security parameters between two IKE devices, the first stage in establishing
IPSec.
Which risk is created when using an Internet browser to access cloud-based service?
A.
misconfiguration of infrastructure, which allows unauthorized access
B.
intermittent connection to the cloud connectors
C.
vulnerabilities within protocol
D.
insecure implementation of API
vulnerabilities within protocol
Which two kinds of attacks are prevented by multifactor authentication? (Choose two)
A.
phishing
B.
brute force
C.
man-in-the-middle
D.
DDOS
E.
teardrop
brute force
man-in-the-middle
Drag and drop the steps from the left into the correct order on the right to enable
AppDynamics to monitor an EC2 instance in Amazon Web Services

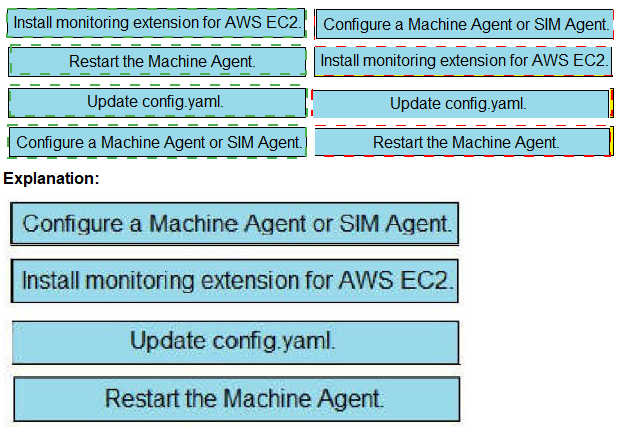
Graphical user interface, text, application, email
Description automatically generated
Refer to the exhibit.
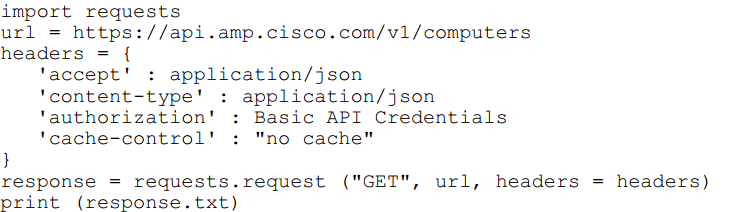
What will happen when this Python script is run?
A.
The compromised computers and malware trajectories will be received from Cisco AMP
B.
The list of computers and their current vulnerabilities will be received from Cisco AMP
C.
The compromised computers and what compromised them will be received from Cisco
AMP
D.
The list of computers, policies, and connector statuses will be received from Cisco AMP
The list of computers, policies, and connector statuses will be received from Cisco AMP
An engineer must force an endpoint to re-authenticate an already authenticated session without disrupting the endpoint to apply a new or updated policy from ISE. Which CoA type achieves this goal?
A.
Port Bounce
B.
CoA Terminate
C.
CoA Reauth
D.
CoA Session Query
CoA Reauth
An engineer has been tasked with implementing a solution that can be leveraged for securing the cloud users, data, and applications. There is a requirement to use the Cisco cloud native CASB and cloud cybersecurity platform. What should be used to meet these requirements?
A.
Cisco Umbrella
B.
Cisco Cloud Email Security
C.
Cisco NGFW
D.
Cisco Cloudlock
Cisco Cloudlock
Which two features of Cisco DNA Center are used in a Software Defined Network solution?
(Choose two)
A.
accounting
B.
assurance
C.
automation
D.
authentication
E.
encryption
assurance
automation
https://www.cisco.com/c/en/us/products/collateral/cloud-systemsmanagement/
dna-center/nb-06- cisco-dna-center-aag-cte-en.html
| Page 8 out of 53 Pages |
| Previous |