Topic 2: Exam Pool B
Drag and drop the threats from the left onto examples of that threat on the right
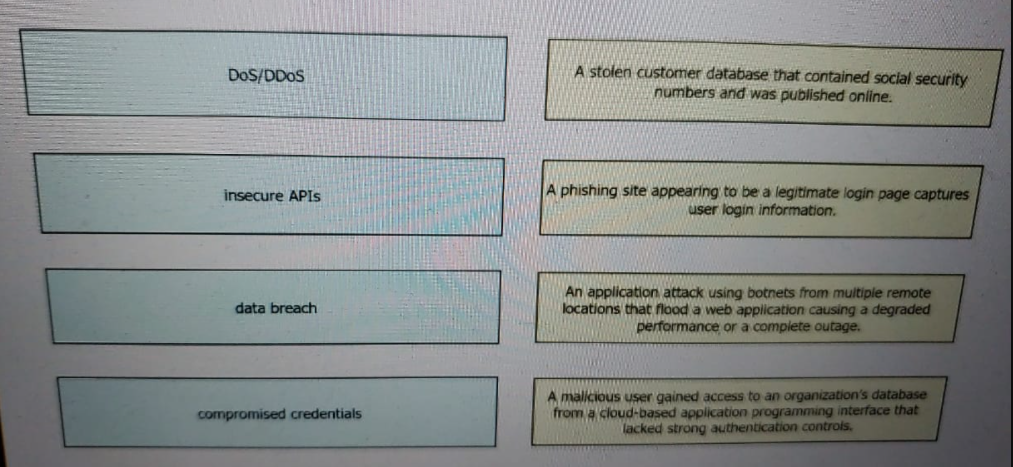
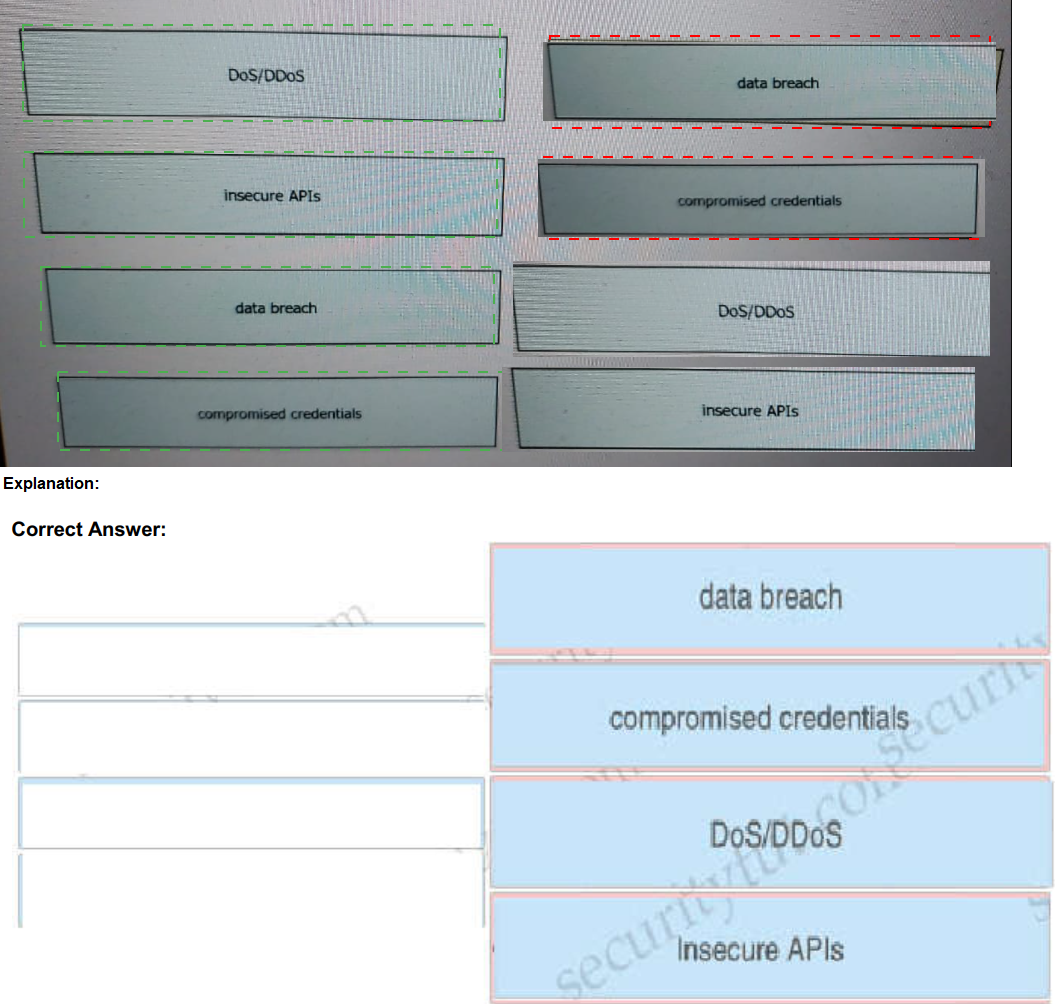
A data breach is the intentional or unintentional release of secure or
private/confidential information to anuntrusted environment.When your credentials have
been compromised, it means someone other than you may be in possession of your
account information, such as your username and/or password.
What is a difference between DMVPN and sVTI?
A.
DMVPN supports tunnel encryption, whereas sVTI does not.
B.
DMVPN supports dynamic tunnel establishment, whereas sVTI does not.
C.
DMVPN supports static tunnel establishment, whereas sVTI does not.
D.
DMVPN provides interoperability with other vendors, whereas sVTI does not.
DMVPN supports dynamic tunnel establishment, whereas sVTI does not.
What is the function of the Context Directory Agent?
A.
maintains users’ group memberships
B.
relays user authentication requests from Web Security Appliance to Active Directory
C.
reads the Active Directory logs to map IP addresses to usernames
D.
accepts user authentication requests on behalf of Web Security Appliance for user
identification
reads the Active Directory logs to map IP addresses to usernames
https://www.cisco.com/c/en/us/td/docs/security/ibf/cda_10/Install_Config_guide/cda10/cda_oveviw.html
Why would a user choose an on-premises ESA versus the CES solution?
A.
Sensitive data must remain onsite
B.
Demand is unpredictable.
C.
The server team wants to outsource this service.
D.
ESA is deployed inline.
Sensitive data must remain onsite
What are two list types within AMP for Endpoints Outbreak Control? (Choose two)
A.
blocked ports
B.
simple custom detections
C.
command and control
D.
allowed applications
E.
URL
simple custom detections
allowed applications
Advanced Malware Protection (AMP) for Endpoints offers a
variety of lists, referred to as Outbreak Control, that allow you to customize it to your needs.
The main lists are: Simple Custom Detections, Blocked Applications, Allowed Applications,
Advanced Custom Detections, and IP Blocked and Allowed Lists.A Simple Custom
Detection list is similar to a blocked list. These are files that you want to detect
andquarantine.Allowed applications lists are for files you never want to convict. Some
examples are a custom application that is detected by a generic engine or a standard
image that you use throughout the company Reference:
https://docs.amp.cisco.com/AMP-for-Endpoints-User-Guide.pdf
What are two Trojan malware attacks? (Choose two)
A.
Frontdoor
B.
Rootkit
C.
Smurf
D.
Backdoor
E.
Sync
Rootkit
Backdoor
An organization has two systems in their DMZ that have an unencrypted link between them
for communication.
The organization does not have a defined password policy and uses several default
accounts on the systems.
The application used on those systems also have not gone through stringent code reviews.
Which vulnerability
would help an attacker brute force their way into the systems?
A.
weak passwords
B.
lack of input validation
C.
missing encryption
D.
lack of file permission
missing encryption
An administrator is trying to determine which applications are being used in the network but
does not want the
network devices to send metadata to Cisco Firepower. Which feature should be used to
accomplish this?
A.
NetFlow
B.
Packet Tracer
C.
Network Discovery
D.
Access Control
Network Discovery
Which two features are used to configure Cisco ESA with a multilayer approach to fight viruses and malware?
(Choose two)
A.
Sophos engine
B.
white list
C.
RAT
D.
outbreak filters
E.
DLP
Sophos engine
outbreak filters
Which Cisco platform ensures that machines that connect to organizational networks have
the recommended
antivirus definitions and patches to help prevent an organizational malware outbreak?
A.
Cisco WiSM
B.
Cisco ESA
C.
Cisco ISE
D.
Cisco Prime Infrastructure
Cisco ISE
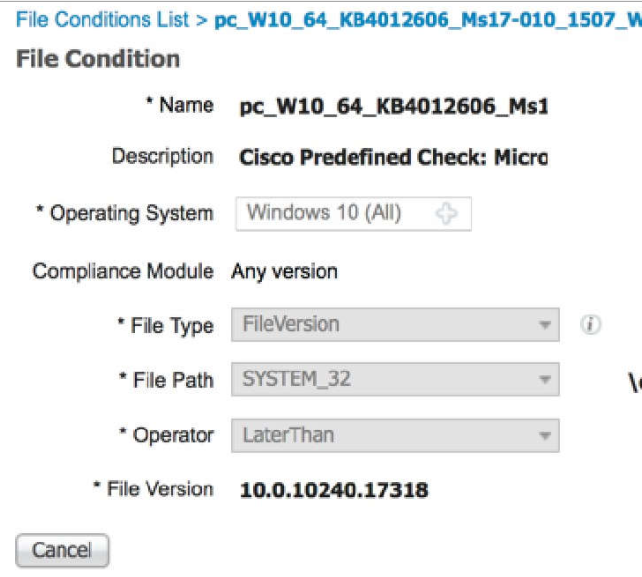
A posture policy is a collection of posture requirements, which
are associated with one or more identity groups, and operating systems. We can configure
ISE to check for the Windows patch at Work Centers > Posture > Posture Elements >
Conditions > File.In this example, we are going to use the predefined file check to ensure
that our Windows 10 clients have the critical security patch installed to prevent the Wanna
Cry malware; and we can also configure ISE to update the client with this patch.
In which two ways does a system administrator send web traffic transparently to the Web Security Appliance?
(Choose two)
A.
configure Active Directory Group Policies to push proxy settings
B.
configure policy-based routing on the network infrastructure
C.
reference a Proxy Auto Config file
D.
configure the proxy IP address in the web-browser settings
E.
use Web Cache Communication Protocol
configure policy-based routing on the network infrastructure
use Web Cache Communication Protocol
What is a benefit of conducting device compliance checks?
A.
It indicates what type of operating system is connecting to the network.
B.
It validates if anti-virus software is installed
C.
It scans endpoints to determine if malicious activity is taking place
D.
It detects email phishing attacks.
It validates if anti-virus software is installed
| Page 7 out of 53 Pages |
| Previous |