Topic 2: Exam Pool B
What is a key difference between Cisco Firepower and Cisco ASA?
A.
Cisco ASA provides access control while Cisco Firepower does not.
B.
Cisco Firepower provides identity-based access control while Cisco ASA does not.
C.
Cisco Firepower natively provides intrusion prevention capabilities while Cisco ASA
does not.
D.
Cisco ASA provides SSL inspection while Cisco Firepower does not.
Cisco Firepower natively provides intrusion prevention capabilities while Cisco ASA
does not.
Refer to the exhibit.
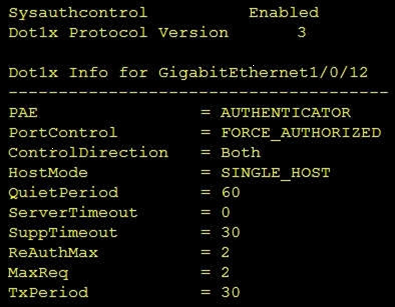
Which command was used to display this output?
A.
show dot1x all
B.
show dot1x
C.
show dot1x all summary
D.
show dot1x interface gi1/0/12
show dot1x all
A network administrator is using the Cisco ESA with AMP to upload files to the cloud for
analysis. The network
is congested and is affecting communication. How will the Cisco ESA handle any files
which need analysis?
A.
AMP calculates the SHA-256 fingerprint, caches it, and periodically attempts the upload
B.
The file is queued for upload when connectivity is restored
C.
The file upload is abandoned
D.
The ESA immediately makes another attempt to upload the file
The file upload is abandoned
https://www.cisco.com/c/en/us/support/docs/security/email-securityappliance/
118796-technoteesa-00.htmlIn this question, it stated “the network is congested”
(not the file analysis server was overloaded) so theappliance will not try to upload the file again.
A user has a device in the network that is receiving too many connection requests from
multiple machines.
Which type of attack is the device undergoing?
A.
phishing
B.
slowloris
C.
pharming
D.
SYN flood
SYN flood
Which license is required for Cisco Security Intelligence to work on the Cisco Next
Generation Intrusion Prevention System?
A.
control
B.
malware
C.
URL filtering
D.
protect
protect
What is the Cisco API-based broker that helps reduce compromises, application risks, and
data breaches in an environment that is not on-premise?
A.
Cisco Cloudlock
B.
Cisco Umbrella
C.
Cisco AMP
D.
Cisco App Dynamics
Cisco Cloudlock
Cisco Cloudlock is a cloud-native cloud access
security broker (CASB) that helps you move to the cloud safely.It protects your cloud users,
data, and apps. Cisco Cloudlock provides visibility and compliance checks,protects data
against misuse and exfiltration, and provides threat protections against malware like
ransomware.
What is a characteristic of traffic storm control behavior?
A.
Traffic storm control drops all broadcast and multicast traffic if the combined traffic
exceeds the level within the interval.
B.
Traffic storm control cannot determine if the packet is unicast or broadcast
C.
Traffic storm control monitors incoming traffic levels over a 10-second traffic storm
control interval.
D.
Traffic storm control uses the Individual/Group bit in the packet source address to
determine if the packet is unicast or broadcast
Traffic storm control drops all broadcast and multicast traffic if the combined traffic
exceeds the level within the interval.
An organization has a Cisco Stealthwatch Cloud deployment in their environment. Cloud logging is working as expected, but logs are not being received from the on-premise network, what action will resolve this issue?
A.
Configure security appliances to send syslogs to Cisco Stealthwatch Cloud
B.
Configure security appliances to send NetFlow to Cisco Stealthwatch Cloud
C.
Deploy a Cisco FTD sensor to send events to Cisco Stealthwatch Cloud
D.
Deploy a Cisco Stealthwatch Cloud sensor on the network to send data to Cisco
Stealthwatch Cloud
Deploy a Cisco Stealthwatch Cloud sensor on the network to send data to Cisco
Stealthwatch Cloud
Which attack is preventable by Cisco ESA but not by the Cisco WSA?
A.
buffer overflow
B.
DoS
C.
SQL injection
D.
phishing
phishing
What are two functions of secret key cryptography? (Choose two)
A.
key selection without integer factorization
B.
utilization of different keys for encryption and decryption
C.
utilization of large prime number iterations
D.
provides the capability to only know the key on one side
E.
utilization of less memory
utilization of different keys for encryption and decryption
provides the capability to only know the key on one side
What are the two most commonly used authentication factors in multifactor authentication?
(Choose two)
A.
biometric factor
B.
time factor
C.
confidentiality factor
D.
knowledge factor
E.
encryption factor
biometric factor
knowledge factor
https://www.cisco.com/c/en/us/products/security/what-is-multi-factorauthentication.htmlThe two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint,face, and retina scans. Biometrics is used commonly in mobile devices).
Due to a traffic storm on the network, two interfaces were error-disabled, and both
interfaces sent SNMP traps.
Which two actions must be taken to ensure that interfaces are put back into service?
(Choose two)
A.
Have Cisco Prime Infrastructure issue an SNMP set command to re-enable the ports
after the pre
configured interval.
B.
Use EEM to have the ports return to service automatically in less than 300 seconds
C.
Enter the shutdown and no shutdown commands on the interfaces
D.
Enable the snmp-server enable traps command and wait 300 seconds
E.
Ensure that interfaces are configured with the error-disable detection and recovery
feature
Enter the shutdown and no shutdown commands on the interfaces
Ensure that interfaces are configured with the error-disable detection and recovery
feature
You can also bring up the port by using these
commands:+ The “shutdown” interface configuration command followed by the “no
shutdown” interface configurationcommand restarts the disabled port.+ The “errdisable
recovery cause …” global configuration command enables the timer to automatically
recover error-disabled state, and the “errdisable recovery interval interval” global
configuration command specifies the time to recover error-disabled state.
| Page 13 out of 53 Pages |
| Previous |