Topic 2: Exam Pool B
A switch with Dynamic ARP Inspection enabled has received a spoofed ARP response on
a trusted interface.
How does the switch behave in this situation?
A.
It forwards the packet after validation by using the MAC Binding Table.
B.
It drops the packet after validation by using the IP & MAC Binding Table
C.
It forwards the packet without validation
D.
It drops the packet without validation
It forwards the packet without validation
What are two DDoS attack categories? (Choose two)
A.
sequential
B.
protocol
C.
database
D.
volume-based
E.
screen-based
protocol
volume-based
There are three basic categories of attack:+
volume-based attacks, which use high traffic to inundate the network bandwidth+ protocol attacks, which focus on exploiting server resources+ application attacks, which focus on
web applications and are considered the most sophisticated and serious type of attacks
Reference: https://www.esecurityplanet.com/networks/types-of-ddos-attacks/
An administrator is configuring a DHCP server to better secure their environment. They
need to be able to ratelimit the traffic and ensure that legitimate requests are not dropped.
How would this be accomplished?
A.
Set a trusted interface for the DHCP server
B.
Set the DHCP snooping bit to 1
C.
Add entries in the DHCP snooping database
D.
Enable ARP inspection for the required VLAN
Set a trusted interface for the DHCP server
To understand DHCP snooping we need to learn about DHCP
spoofing attack first.
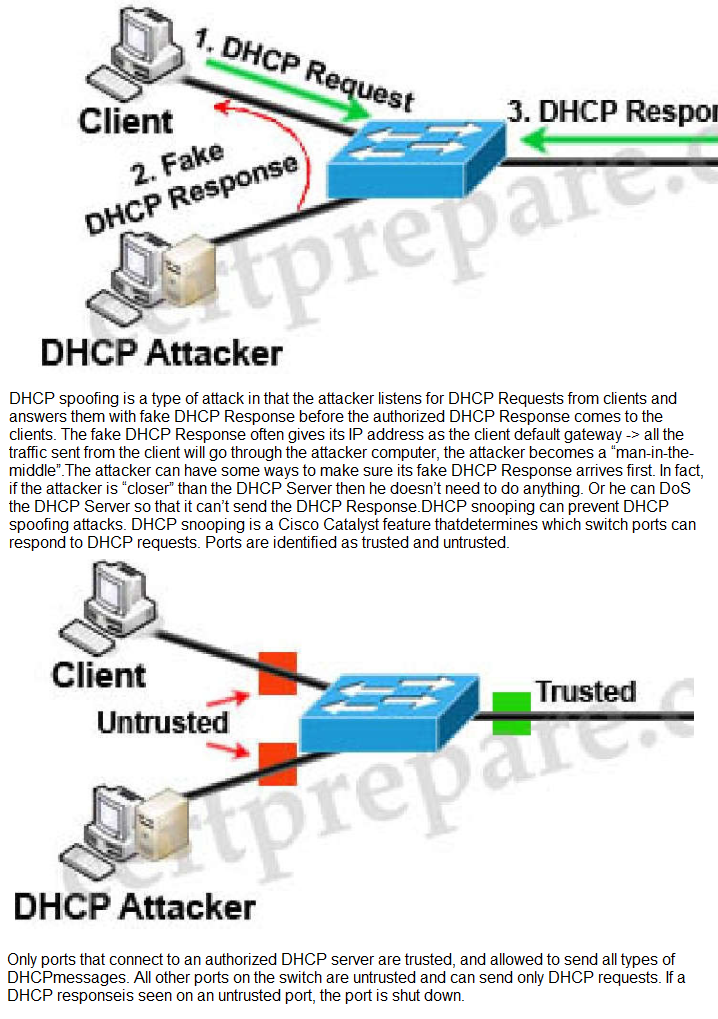
In which cloud services model is the tenant responsible for virtual machine OS patching?
A.
IaaS
B.
UCaaS
C.
PaaS
D.
SaaS
IaaS
ExplanationOnly in On-site (on-premises) and IaaS we (tenant) manage
O/S (Operating System).
In which two ways does Easy Connect help control network access when used with Cisco
TrustSec? (Choose two)
A.
It allows multiple security products to share information and work together to enhance
security posture in the network.
B.
It creates a dashboard in Cisco ISE that provides full visibility of all connected endpoints.
C.
It allows for the assignment of Security Group Tags and does not require 802.1x to be
configured on the switch or the endpoint.
D.
It integrates with third-party products to provide better visibility throughout the network.
E.
It allows for managed endpoints that authenticate to AD to be mapped to Security
Groups (PassiveID).
It allows for the assignment of Security Group Tags and does not require 802.1x to be
configured on the switch or the endpoint.
It allows for managed endpoints that authenticate to AD to be mapped to Security
Groups (PassiveID).
Refer to the exhibit.
An administrator is adding a new Cisco FTD device to their network and wants to manage it
with Cisco FMC.
The Cisco FTD is not behind a NAT device. Which command is needed to enable this on
the Cisco FTD?
A.
configure manager add DONTRESOLVE kregistration key>
B.
configure manager add <FMC IP address> <registration key> 16
C.
configure manager add DONTRESOLVE <registration key> FTD123
D.
configure manager add <FMC IP address> <registration key>
configure manager add <FMC IP address> <registration key>
Which two deployment model configurations are supported for Cisco FTDv in AWS?
(Choose two)
A.
Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS
B.
Cisco FTDv with one management interface and two traffic interfaces configured
C.
Cisco FTDv configured in routed mode and managed by a physical FMC appliance on premises
D.
Cisco FTDv with two management interfaces and one traffic interface configured
E.
Cisco FTDv configured in routed mode and IPv6 configured
Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS
Cisco FTDv configured in routed mode and managed by a physical FMC appliance on premises
What are the two types of managed Intercloud Fabric deployment models? (Choose two)
A.
Service Provider managed
B.
Public managed
C.
Hybrid managed
D.
User managed
E.
Enterprise managed
Enterprise managed
What is a benefit of using Cisco FMC over Cisco ASDM?
A.
Cisco FMC uses Java while Cisco ASDM uses HTML5.
B.
Cisco FMC provides centralized management while Cisco ASDM does not.
C.
Cisco FMC supports pushing configurations to devices while Cisco ASDM does not.
D.
Cisco FMC supports all firewall products whereas Cisco ASDM only supports Cisco ASA
devices
Cisco FMC provides centralized management while Cisco ASDM does not.
Reference: https://www.cisco.com/c/en/us/products/collateral/security/firesightmanagement-
center/datasheetc78-736775.html
What is a capability of Cisco ASA Netflow?
A.
It filters NSEL events based on traffic
B.
It generates NSEL events even if the MPF is not configured
C.
It logs all event types only to the same collector
D.
It sends NetFlow data records from active and standby ASAs in an active standby
failover pair
It filters NSEL events based on traffic
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?
A.
authenticates the IKEv2 peers in the 172.16.0.0/16 range by using the key
ciscXXXXXXXX
B.
authenticates the IP address of the 172.16.0.0/32 peer by using the key ciscXXXXXXXX
C.
authenticates the IKEv1 peers in the 172.16.0.0/16 range by using the key
ciscXXXXXXXX
D.
secures all the certificates in the IKE exchange by using the key ciscXXXXXXXX
authenticates the IKEv1 peers in the 172.16.0.0/16 range by using the key
ciscXXXXXXXX
Configure a Crypto ISAKMP Key
In order to configure a preshared authentication key, enter the crypto isakmp key
command in global configuration mode:
crypto isakmp key cisco123 address 172.16.1.1
https://community.cisco.com/t5/vpn/isakmp-with-0-0-0-0-dmvpn/td-p/4312380
It is a bad practice but it is valid. 172.16.0.0/16 the full range will be accepted as possible
PEER
https://www.examtopics.com/discussions/cisco/view/46191-exam-350-701-topic-1-
question-71-
discussion/#:~:text=Command-reference-is-not-decisive,172.16.1.128-ci
sco123%0ACSR%2D1(config)%23
Testing without a netmask shows that command interpretation has a preference for /16 and
/24. CSR-1(config)#crypto isakmp key cisco123 address 172.16.0.0
CSR-1(config)#do show crypto isakmp key | i cisco
default 172.16.0.0 [255.255.0.0] cisco123
CSR-1(config)#no crypto isakmp key cisco123 address 172.16.0.0
CSR-1(config)#crypto isakmp key cisco123 address 172.16.1.0
CSR-1(config)#do show crypto isakmp key | i cisco
default 172.16.1.0 [255.255.255.0] cisco123
CSR-1(config)#no crypto isakmp key cisco123 address 172.16.1.0
CSR-1(config)#crypto isakmp key cisco123 address 172.16.1.128
CSR-1(config)#do show crypto isakmp key | i cisco default 172.16.1.128 cisco123
CSR-1(config)#
What is provided by the Secure Hash Algorithm in a VPN?
A.
integrity
B.
key exchange
C.
encryption
D.
authentication
integrity
| Page 12 out of 53 Pages |
| Previous |