Topic 2: Exam Pool B
A network administrator is configuring SNMPv3 on a new router. The users have already
been created;
however, an additional configuration is needed to facilitate access to the SNMP views.
What must the
administrator do to accomplish this?
A.
map SNMPv3 users to SNMP views
B.
set the password to be used for SNMPv3 authentication
C.
define the encryption algorithm to be used by SNMPv3
D.
specify the UDP port used by SNMP
set the password to be used for SNMPv3 authentication
How does Cisco Umbrella archive logs to an enterprise owned storage?
A.
by using the Application Programming Interface to fetch the logs
B.
by sending logs via syslog to an on-premises or cloud-based syslog server
C.
by the system administrator downloading the logs from the Cisco Umbrella web portal
D.
by being configured to send logs to a self-managed AWS S3 bucket
by being configured to send logs to a self-managed AWS S3 bucket
https://docs.umbrella.com/deployment-umbrella/docs/manage-logs
Refer to the exhibit.
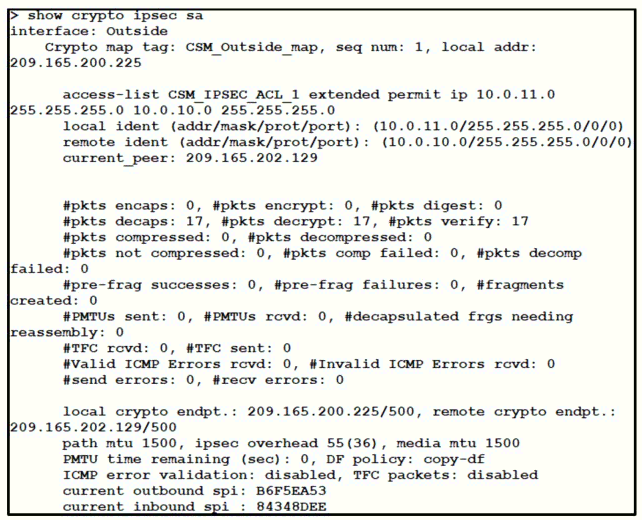
Traffic is not passing through IPsec site-to-site VPN on the Firepower Threat Defense
appliance. What is causing this issue?
A.
No split-tunnel policy is defined on the Firepower Threat Defense appliance
B.
The access control policy is not allowing VPN traffic in.
C.
Site-to-site VPN peers are using different encryption algorithms.
D.
Site-to-site VPN preshared keys are mismatched
No split-tunnel policy is defined on the Firepower Threat Defense appliance
A network administrator configures Dynamic ARP Inspection on a switch. After Dynamic ARP Inspection is applied, all users on that switch are unable to communicate with any destination. The network administrator checks the interface status of all interfaces, and there is no err-disabled interface. What is causing this problem?
A.
DHCP snooping has not been enabled on all VLANs
B.
The ip arp inspection limit command is applied on all interfaces and is blocking the traffic of all users.
C.
Dynamic ARP Inspection has not been enabled on all VLANs
D.
The no ip arp inspection trust command is applied on all user host interfaces
The no ip arp inspection trust command is applied on all user host interfaces
Dynamic ARP inspection (DAI) is a security feature that
validates ARP packets in a network. It intercepts, logs, and discards ARP packets with invalid IP-to-MAC address bindings. This capability protects the network from certain manin- the-middle attacks. After enabling DAI, all ports become untrusted ports.
What is an attribute of the DevSecOps process?
A.
mandated security controls and check lists
B.
security scanning and theoretical vulnerabilities
C.
development security
D.
isolated security team
development security
DevSecOps (development, security, and
operations) is a concept used in recent years to describe how to movesecurity activities to
the start of the development life cycle and have built-in security practices in the continuousintegration/continuous deployment (CI/CD) pipeline. Thus minimizing
vulnerabilities and bringing security closerto IT and business objectives.Three key things
make a real DevSecOps environment:+ Security testing is done by the development
team.+ Issues found during that testing is managed by the development team.+ Fixing
those issues stays within the development team.
Which method is used to deploy certificates and configure the supplicant on mobile devices
to gain access to
network resources?
A.
BYOD on boarding
B.
Simple Certificate Enrollment Protocol
C.
Client provisioning
D.
MAC authentication bypass
BYOD on boarding
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
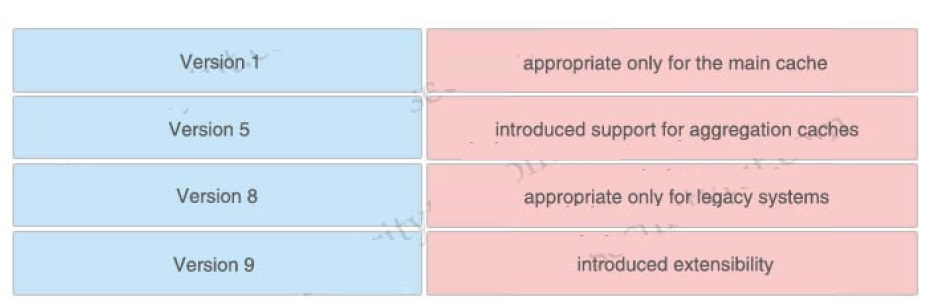
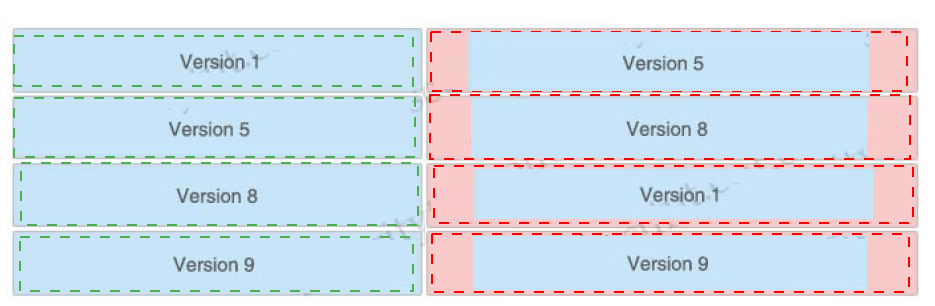
Which two risks is a company vulnerable to if it does not have a well-established patching solution for endpoints? (Choose two)
A.
exploits
B.
ARP spoofing
C.
denial-of-service attacks
D.
malware
E.
eavesdropping
exploits
malware
Malware means “malicious software”, is any software
intentionally designed to cause damage to a computer, server, client, or computer network.
The most popular types of malware includes viruses, ransomware and spyware. Virus
Possibly the most common type of malware, viruses attach their malicious code to clean
code and wait to be run.
Ransomware is malicious software that infects your computer and displays messages
demanding a fee to be paid in order for your system to work again.Spyware is spying
software that can secretly record everything you enter, upload, download, and store on
your computers or mobile devices. Spyware always tries to keep itself hidden.An exploit is
a code that takes advantage of a software vulnerability or security flaw.Exploits and
malware are two risks for endpoints that are not up to date. ARP spoofing and
eavesdropping are attacks against the network while denial-of-service attack is based on
the flooding of IP packets.
Refer to the exhibit.

When configuring a remote access VPN solution terminating on the Cisco ASA, an
administrator would like to utilize an external token authentication mechanism in conjunction with AAA authentication
using machine
certificates. Which configuration item must be modified to allow this?
A.
Group Policy
B.
Method
C.
SAML Server
D.
DHCP Servers
Method
In order to use AAA along with an external token
authentication mechanism, set the “Method” as “Both” inthe Authentication.
An engineer is implementing NTP authentication within their network and has configured
both the client and server devices with the command ntp authentication-key 1 md5
Cisc392368270. The server at 1.1.1.1 is attempting to authenticate to the client at 1.1.1.2,
however it is unable to do so. Which command is required to enable the client to accept the
server’s authentication key?
A.
ntp peer 1.1.1.1 key 1
B.
ntp server 1.1.1.1 key 1
C.
ntp server 1.1.1.2 key 1
D.
ntp peer 1.1.1.2 key 1
ntp server 1.1.1.1 key 1
To configure an NTP enabled router to require
authentication when other devices connect to it, use thefollowing
commands:NTP_Server(config)#ntp authentication-key 2 md5
securitytutNTP_Server(config)#ntp authenticateNTP_Server(config)#ntp trusted-key 2Then
you must configure the same authentication-key on the client
router:NTP_Client(config)#ntp authentication-key 2 md5 securitytutNTP_Client(config)#ntp
authenticateNTP_Client(config)#ntp trusted-key 2NTP_Client(config)#ntp server 10.10.10.1
key 2Note: To configure a Cisco device as a NTP client, use the command ntp server <IP
address>. For example:Router(config)#ntp server 10.10.10.1. This command will instruct
the router to query 10.10.10.1 for the time.
Refer to the exhibit.
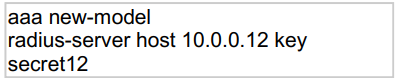
Which statement about the authentication protocol used in the configuration is true?
A.
The authentication request contains only a password
B.
The authentication request contains only a username
C.
The authentication and authorization requests are grouped in a single packet
D.
There are separate authentication and authorization request packets
The authentication and authorization requests are grouped in a single packet
ExplanationThis command uses RADIUS which combines authentication
and authorization in one function (packet).
Which cloud model is a collaborative effort where infrastructure is shared and jointly
accessed by several
organizations from a specific group?
A.
Hybrid
B.
Community
C.
Private
D.
Public
Community
Community Cloud allows system and services to be accessible
by group of organizations. It shares theinfrastructure between several organizations from a
specific community. It may be managed internally byorganizations or by the third-party.
| Page 11 out of 53 Pages |
| Previous |