Topic 2: Exam Pool B
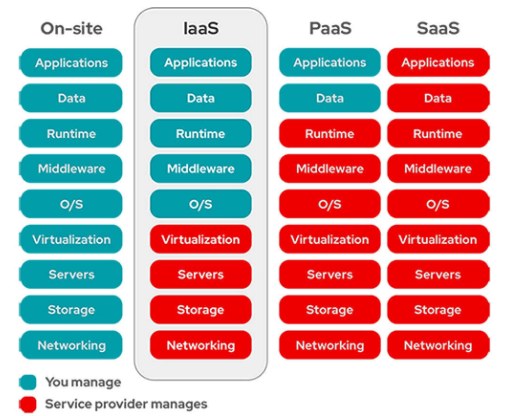
Which two aspects of the cloud PaaS model are managed by the customer but not the
provider? (Choose two)
A.
virtualization
B.
middleware
C.
operating systems
D.
applications
E.
data
applications
data
Customers must manage applications and data in PaaS.
Which type of attack is social engineering?
A.
trojan
B.
phishing
C.
malware
D.
MITM
phishing
Phishing is a form of social engineering. Phishing attacks use
email or malicious web sites to solicit personal,often financial, information. Attackers may send email seemingly from a reputable credit card company orfinancial institution that requests account information, often suggesting that there is a problem.
An organization has a Cisco ESA set up with policies and would like to customize the
action assigned for
violations. The organization wants a copy of the message to be delivered with a message
added to flag it as a
DLP violation. Which actions must be performed in order to provide this capability?
A.
deliver and send copies to other recipients
B.
quarantine and send a DLP violation notification
C.
quarantine and alter the subject header with a DLP violation
D.
deliver and add disclaimer text
deliver and add disclaimer text
In which type of attack does the attacker insert their machine between two hosts that are
communicating with each other?
A.
LDAP injection
B.
man-in-the-middle
C.
cross-site scripting
D.
insecure API
man-in-the-middle
The main function of northbound APIs in the SDN architecture is to enable communication between which two areas of a network?
A.
SDN controller and the cloud
B.
management console and the SDN controller
C.
management console and the cloud
D.
SDN controller and the management solution
SDN controller and the management solution
How does Cisco Advanced Phishing Protection protect users?
A.
It validates the sender by using DKIM
B.
It determines which identities are perceived by the sender
C.
It utilizes sensors that send messages securely
D.
It uses machine learning and real-time behavior analytics.
It uses machine learning and real-time behavior analytics.
An organization received a large amount of SPAM messages over a short time period. In
order to take action on the messages, it must be determined how harmful the messages
are and this needs to happen dynamically.
What must be configured to accomplish this?
A.
Configure the Cisco WSA to modify policies based on the traffic seen
B.
Configure the Cisco ESA to receive real-time updates from Talos
C.
Configure the Cisco WSA to receive real-time updates from Talos
D.
Configure the Cisco ESA to modify policies based on the traffic seen
Configure the Cisco ESA to modify policies based on the traffic seen
The Mail Policies menu is where almost all of the
controls related to email filtering happens. All the security and content filtering policies are
set here, so it’s likely that, as an ESA administrator, the pages on this menu are where you
are likely to spend most of your time.
Which policy is used to capture host information on the Cisco Firepower Next Generation Intrusion Prevention System?
A.
Correlation
B.
Intrusion
C.
Access Control
D.
Network Discovery
Network Discovery
https://www.cisco.com/c/en/us/td/docs/security/firepower/640/configuration/guide/fpmcconfigguide-
v64/introduction_to_network_discovery_and_identity.html
What are two benefits of Flexible NetFlow records? (Choose two)
A.
They allow the user to configure flow information to perform customized traffic
identification
B.
They provide attack prevention by dropping the traffic
C.
They provide accounting and billing enhancements
D.
They converge multiple accounting technologies into one accounting mechanism
E.
They provide monitoring of a wider range of IP packet information from Layer 2 to 4
They allow the user to configure flow information to perform customized traffic
identification
They converge multiple accounting technologies into one accounting mechanism
Reference:
https://www.cisco.com/en/US/docs/ios/fnetflow/configuration/guide/cust_fnflow_rec_mon_e
xternal_docbase_0900e4b18055d0d2_4container_external_docbase_0900e4b181b413
d9.html#wp1057997Note: Traditional NetFlow allows us to monitor from Layer 2 to 4 but
Flexible NetFlow goes beyond theselayers.
Which component of Cisco umbrella architecture increases reliability of the service?
A.
Anycast IP
B.
AMP Threat grid
C.
Cisco Talos
D.
BGP route reflector
Cisco Talos
Which CLI command is used to register a Cisco FirePower sensor to Firepower
Management Center?
A.
configure system add <host><key>
B.
configure manager <key> add host
C.
configure manager delete
D.
configure manager add <host><key
configure manager add <host><key
What is the purpose of the certificate signing request when adding a new certificate for a
server?
A.
It is the password for the certificate that is needed to install it with
B.
It provides the server information so a certificate can be created and signed
C.
It provides the certificate client information so the server can authenticate against it
when installing
D.
It is the certificate that will be loaded onto the server
It provides the server information so a certificate can be created and signed
A certificate signing request (CSR) is one of the
first steps towards getting your own SSL Certificate. Generated on the same server you
plan to install the certificate on, the CSR contains information (e.g. common name,
organization, country) that the Certificate Authority (CA) will use to create your certificate. It
also contains the public key that will be included in your certificate and is signed with the
corresponding private key.
| Page 10 out of 53 Pages |
| Previous |