Topic 1: Exam Pool A
A new wireless client is configured to join a 802.11 network. This client uses the same
hardware and software as many of the other clients on the network. The client can see the
network, but cannot connect. A wireless packet sniffer shows that the Wireless Access
Point (WAP) is not responding to the association requests being sent by the wireless client.
What is a possible source of this problem?
A.
The WAP does not recognize the client’s MAC address
B.
The client cannot see the SSID of the wireless network
C.
Client is configured for the wrong channel
D.
The wireless client is not configured to use DHCP
The WAP does not recognize the client’s MAC address
Explanation: https://en.wikipedia.org/wiki/MAC_filtering
MAC filtering is a security method based on access control. Each address is assigned a
48-bit address, which is used to determine whether we can access a network or not. It
helps in listing a set of allowed devices that you need on your Wi-Fi and the list of denied
devices that you don’t want on your Wi-Fi. It helps in preventing unwanted access to the
network. In a way, we can blacklist or white list certain computers based on their MAC
address. We can configure the filter to allow connection only to those devices included in
the white list. White lists provide greater security than blacklists because the router grants
access only to selected devices.
It is used on enterprise wireless networks having multiple access points to prevent clients
from communicating with each other. The access point can be configured only to allow
clients to talk to the default gateway, but not other wireless clients. It increases the
efficiency of access to a network.
The router allows configuring a list of allowed MAC addresses in its web interface, allowing
you to choose which devices can connect to your network. The router has several functions
designed to improve the network's security, but not all are useful. Media access control
may seem advantageous, but there are certain flaws.
On a wireless network, the device with the proper credentials such as SSID and password
can authenticate with the router and join the network, which gets an IP address and access
to the internet and any shared resources.
MAC address filtering adds an extra layer of security that checks the device’s MAC address
against a list of agreed addresses. If the client’s address matches one on the router’s list,
access is granted; otherwise, it doesn’t join the network.
Why would you consider sending an email to an address that you know does not exist
within the company you are performing a Penetration Test for?
A.
To determine who is the holder of the root account
B.
To perform a DoS
C.
To create needless SPAM
D.
To illicit a response back that will reveal information about email servers and how they
treat undeliverable mail
E.
To test for virus protection
To illicit a response back that will reveal information about email servers and how they
treat undeliverable mail
In the field of cryptanalysis, what is meant by a “rubber-hose” attack?
A.
Forcing the targeted keystream through a hardware-accelerated device such as an
ASIC.
B.
A backdoor placed into a cryptographic algorithm by its creator
C.
Extraction of cryptographic secrets through coercion or torture
D.
Attempting to decrypt ciphertext by making logical assumptions about the contents of
the original plaintex
Extraction of cryptographic secrets through coercion or torture
A powerful and often the most effective cryptanalysis method in which the
attack is directed at the most vulnerable link in the cryptosystem - the person. In this attack,
the cryptanalyst uses blackmail, threats, torture, extortion, bribery, etc. This method's main
advantage is the decryption time's fundamental independence from the volume of secret
information, the length of the key, and the cipher's mathematical strength.
The method can reduce the time to guess a password, for example, for AES, to an
acceptable level; however, it requires special authorization from the relevant regulatory
authorities. Therefore, it is outside the scope of this course and is not considered in its
practical part.
The change of a hard drive failure is once every three years. The cost to buy a new hard
drive is $300. It will require 10 hours to restore the OS and software to the new hard disk. It
will require a further 4 hours to restore the database from the last backup to the new hard
disk. The recovery person earns $10/hour. Calculate the SLE, ARO, and ALE. Assume the
EF = 1(100%). What is the closest approximate cost of this replacement and recovery
operation per year?
A.
$1320
B.
$440
C.
$100
D.
$146
$146
Explanation: 1. AV (Asset value) = $300 + (14 * $10) = $440 - the cost of a hard drive
plus the work of a recovery person, i.e.how much would it take to replace 1 asset? 10
hours for resorting the OS and soft + 4 hours for DB restore multiplies by hourly rate of the
recovery person.
2. SLE (Single Loss Expectancy) = AV * EF (Exposure Factor) = $440 * 1 = $440
3. ARO (Annual rate of occurrence) = 1/3 (every three years, meaning the probability of
occurring during 1 years is 1/3)
4. ALE (Annual Loss Expectancy) = SLE * ARO = 0.33 * $440 = $145.2
Study the snort rule given below:
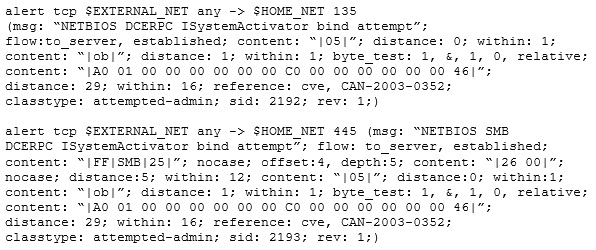
From the options below, choose the exploit against which this rule applies.
A.
WebDav
B.
SQL Slammer
C.
MS Blaster
D.
MyDoom
MS Blaster
Why should the security analyst disable/remove unnecessary ISAPI filters?
A.
To defend against social engineering attacks
B.
To defend against webserver attacks
C.
To defend against jailbreaking
D.
To defend against jailbreaking
To defend against webserver attacks
Identify the UDP port that Network Time Protocol (NTP) uses as its primary means of
communication?
A.
113
B.
69
C.
123
D.
161
123
Explanation:
https://en.wikipedia.org/wiki/Network_Time_Protocol
The Network Time Protocol (NTP) is a networking protocol for clock synchronization
between computer systems over packet-switched, variable-latency data networks.
NTP is intended to synchronize all participating computers within a few milliseconds of
Coordinated Universal Time (UTC). It uses the intersection algorithm, a modified version of
Marzullo's algorithm, to select accurate time servers and is designed to mitigate variable
network latency effects. NTP can usually maintain time to within tens of milliseconds over
the public Internet and achieve better than one millisecond accuracy in local area networks.
Asymmetric routes and network congestion can cause errors of 100 ms or more.
The protocol is usually described in terms of a client-server model but can easily be used in
peer-to-peer relationships where both peers consider the other to be a potential time
source. Implementations send and receive timestamps using the User Datagram Protocol
(UDP) on port number 123.
PGP, SSL, and IKE are all examples of which type of cryptography?
A.
Digest
B.
Secret Key
C.
Public Key
D.
Hash Algorithm
Public Key
The “Gray-box testing” methodology enforces what kind of restriction?
A.
Only the external operation of a system is accessible to the tester.
B.
The internal operation of a system in only partly accessible to the tester
C.
Only the internal operation of a system is known to the tester.
D.
The internal operation of a system is completely known to the tester.
The internal operation of a system is completely known to the tester.
White-box testing (also known as clear box testing, glass box testing, transparent box
testing, and structural testing) is a method of software testing that tests internal structures
or workings of an application, as opposed to its functionality (i.e. black-box testing). In
white-box testing, an internal perspective of the system, as well as programming skills, are
used to design test cases. The tester chooses inputs to exercise paths through the code
and determine the expected outputs. This is analogous to testing nodes in a circuit, e.g. incircuit
testing (ICT). White-box testing can be applied at the unit, integration and system
levels of the software testing process. Although traditional testers tended to think of whitebox
testing as being done at the unit level, it is used for integration and system testing
more frequently today. It can test paths within a unit, paths between units during
integration, and between subsystems during a system-level test. Though this method of
test design can uncover many errors or problems, it has the potential to miss
unimplemented parts of the specification or missing requirements. Where white-box testing
is design-driven,[1] that is, driven exclusively by agreed specifications of how each
component of the software is required to behave (as in DO-178C and ISO 26262
processes) then white-box test techniques can accomplish assessment for unimplemented
or missing requirements.
White-box test design techniques include the following code coverage criteria:
· Control flow testing
· Data flow testing
· Branch testing
· Statement coverage
· Decision coverage
· Modified condition/decision coverage
· Prime path testing
· Path testing
What is the role of test automation in security testing?
A.
It is an option but it tends to be very expensive.
B.
It should be used exclusively. Manual testing is outdated because of low speed and
possible test setup inconsistencies.
C.
Test automation is not usable in security due to the complexity of the tests.
D.
It can accelerate benchmark tests and repeat them with a consistent test setup. But it
cannot replace manual testing completely.
It can accelerate benchmark tests and repeat them with a consistent test setup. But it
cannot replace manual testing completely.
As a securing consultant, what are some of the things you would recommend to a company
to ensure DNS security?
A.
Use the same machines for DNS and other applications
B.
Harden DNS servers
C.
Use split-horizon operation for DNS servers
D.
Restrict Zone transfers
E.
Have subnet diversity between DNS servers
Harden DNS servers
Use split-horizon operation for DNS servers
Restrict Zone transfers
Have subnet diversity between DNS servers
Your company performs penetration tests and security assessments for small and mediumsized
business in the local area. During a routine security assessment, you discover
information that suggests your client is involved with human trafficking.
What should you do?
A.
Confront the client in a respectful manner and ask her about the data.
B.
Copy the data to removable media and keep it in case you need it.
D.
Ignore the data and continue the assessment until completed as agreed
E.
Immediately stop work and contact the proper legal authorities.
Ignore the data and continue the assessment until completed as agreed
| Page 5 out of 48 Pages |
| Previous |