Topic 2: Exam Pool B
Garry is a network administrator in an organization. He uses SNMP to manage networked
devices from a remote location. To manage nodes in the network, he uses MIB. which
contains formal descriptions of all network objects managed by SNMP. He accesses the
contents of MIB by using a web browser either by entering the IP address and Lseries.mlb
or by entering the DNS library name and Lseries.mlb. He is currently retrieving information
from an MIB that contains object types for workstations and server services. Which of the
following types of MIB is accessed by Garry in the above scenario?
A.
LNMIB2.MIB
B.
WINS.MIB
C.
DHCP.MIS
D.
MIB_II.MIB
LNMIB2.MIB
DHCP.MIB: Monitors network traffic between DHCP servers and remote hosts
HOSTMIB.MIB: Monitors and manages host resources
LNMIB2.MIB: Contains object types for workstation and server services
MIBJI.MIB: Manages TCP/IP-based Internet using a simple architecture and system
WINS.MIB: For the Windows Internet Name Service (WINS)
George is a security professional working for iTech Solutions. He was tasked with securely
transferring sensitive data of the organization between industrial systems. In this process,
he used a short-range communication protocol based on the IEEE 203.15.4 standard. This
protocol is used in devices that transfer data infrequently at a low rate in a restricted area,
within a range of 10-100 m. What is the short-range wireless communication technology
George employed in the above scenario?
A.
MQTT
B.
LPWAN
C.
Zigbee
D.
NB-IoT
Zigbee
Explanation: Zigbee could be a wireless technology developed as associate open
international normal to deal with the unique desires of affordable, low-power wireless IoT
networks. The Zigbee normal operates on the IEEE 802.15.4 physical radio specification
and operates in unauthorised bands as well as a pair of.4 GHz, 900 MHz and 868 MHz.
The 802.15.4 specification upon that the Zigbee stack operates gained confirmation by the
Institute of Electrical and physical science Engineers (IEEE) in 2003. The specification
could be a packet-based radio protocol supposed for affordable, battery-operated devices.
The protocol permits devices to speak in an exceedingly kind of network topologies and
may have battery life lasting many years.
The Zigbee three.0 Protocol
The Zigbee protocol has been created and ratified by member corporations of the Zigbee
Alliance.Over three hundred leading semiconductor makers, technology corporations,
OEMs and repair corporations comprise the Zigbee Alliance membership. The Zigbee
protocol was designed to supply associate easy-to-use wireless information answer
characterised by secure, reliable wireless network architectures.
THE ZIGBEE ADVANTAGE
The Zigbee 3.0 protocol is intended to speak information through rip-roaring RF
environments that area unit common in business and industrial applications. Version 3.0
builds on the prevailing Zigbee normal however unifies the market-specific application
profiles to permit all devices to be wirelessly connected within the same network, no matter
their market designation and performance. what is more, a Zigbee 3.0 certification theme
ensures the ability of product from completely different makers. Connecting Zigbee three.0
networks to the information science domain unveil observance and management from
devices like smartphones and tablets on a local area network or WAN, as well as the web,
and brings verity net of Things to fruition.
Zigbee protocol options include:
Support for multiple network topologies like point-to-point, point-to-multipoint and
mesh networks
Low duty cycle – provides long battery life
Low latency
Direct Sequence unfold Spectrum (DSSS)
Up to 65,000 nodes per network
128-bit AES encryption for secure information connections
Collision avoidance, retries and acknowledgements
This is another short-range communication protocol based on the IEEE 203.15.4 standard.
Zig-Bee is used in devices that transfer data infrequently at a low rate in a restricted area
and within a range of 10–100 m.
Wilson, a professional hacker, targets an organization for financial benefit and plans to
compromise its systems by sending malicious emails. For this purpose, he uses a tool to
track the emails of the target and extracts information such as sender identities, mall
servers, sender IP addresses, and sender locations from different public sources. He also
checks if an email address was leaked using the haveibeenpwned.com API. Which of the
following tools is used by Wilson in the above scenario?
A.
Factiva
B.
Netcraft
C.
infoga
D.
Zoominfo
infoga
Explanation: Infoga may be a tool gathering email accounts informations
(ip,hostname,country,…) from completely different public supply (search engines, pgp key
servers and shodan) and check if email was leaked using haveibeenpwned.com API. is a
really simple tool, however very effective for the first stages of a penetration test or just to
know the visibility of your company within the net.
Which of the following steps for risk assessment methodology refers to vulnerability identification?
A.
Determines if any flaws exist in systems, policies, or procedures
B.
Assigns values to risk probabilities; Impact values
C.
Determines risk probability that vulnerability will be exploited (High. Medium, Low)
D.
Identifies sources of harm to an IT system. (Natural, Human. Environmental)
Determines risk probability that vulnerability will be exploited (High. Medium, Low)
Tremp is an IT Security Manager, and he is planning to deploy an IDS in his small
company. He is looking for an IDS with the following characteristics: - Verifies success or
failure of an attack - Monitors system activities Detects attacks that a network-based IDS
fails to detect - Near real-time detection and response - Does not require additional
hardware - Lower entry cost Which type of IDS is best suited for Tremp's requirements?
A.
Gateway-based IDS
B.
Network-based IDS
C.
Host-based IDS
D.
Open source-based
Host-based IDS
Emily, an extrovert obsessed with social media, posts a large amount of private
information, photographs, and location tags of recently visited places. Realizing this.
James, a professional hacker, targets Emily and her acquaintances, conducts a location
search to detect their geolocation by using an automated tool, and gathers information to
perform other sophisticated attacks. What is the tool employed by James in the above
scenario?
A.
ophcrack
B.
Hootsuite
C.
VisualRoute
D.
HULK
Hootsuite
Explanation: Hootsuite may be a social media management platform that covers virtually
each side of a social media manager’s role. With only one platform users area unit ready to do the easy stuff like reverend cool content
and schedule posts on social media in all the high to managing team members and
measure ROI.
There area unit many totally different plans to decide on from, from one user set up up to a
bespoken enterprise account that’s appropriate for much larger organizations.
Conducting location search on social media sites such as Twitter, Instagram, and
Facebook helps attackers to detect the geolocation of the target. This information further
helps attackers to perform various social engineering and non-technical attacks. Many
online tools such as Followerwonk, Hootsuite, and Sysomos are available to search for
both geotagged and non-geotagged information on social media sites. Attackers search
social media sites using these online tools using keywords, usernames, date, time, and so
on...
An attacker runs netcat tool to transfer a secret file between two hosts.
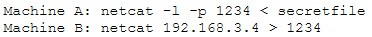
He is worried about information being sniffed on the network.
How would the attacker use netcat to encrypt the information before transmitting onto the
wire?
A.
Machine A: netcat -l -p -s password 1234 < testfileMachine B: netcat
1234
B.
Machine A: netcat -l -e magickey -p 1234 < testfileMachine B: netcat
1234
C.
Machine A: netcat -l -p 1234 < testfile -pw passwordMachine B: netcat
1234 -pw password
D.
Use cryptcat instead of netcat
Use cryptcat instead of netcat
Which utility will tell you in real time which ports are listening or in another state?
A.
Netstat
B.
TCPView
C.
Nmap
D.
Loki
TCPView
Henry Is a cyber security specialist hired by BlackEye - Cyber security solutions. He was
tasked with discovering the operating system (OS) of a host. He used the Unkornscan tool
to discover the OS of the target system. As a result, he obtained a TTL value, which
Indicates that the target system is running a Windows OS. Identify the TTL value Henry
obtained, which indicates that the target OS is Windows.
A.
64
B.
128
C.
255
D.
138
128
Explanation: Windows TTL 128, Linux TTL 64, OpenBSD 255 ...
https://subinsb.com/default-device-ttl-values/
Time to Live (TTL) represents to number of 'hops' a packet can take before it is considered
invalid. For Windows/Windows Phone, this value is 128. This value is 64 for Linux/Android.
What port number is used by LDAP protocol?
A.
110
B.
389
C.
464
D.
445
389
in an attempt to increase the security of your network, you Implement a solution that will
help keep your wireless network undiscoverable and accessible only to those that know It.
How do you accomplish this?
A.
Delete the wireless network
B.
Remove all passwords
C.
Lock all users
D.
Disable SSID broadcasting
Disable SSID broadcasting
Explanation: The SSID (service set identifier) is the name of your wireless network.
SSID broadcast is how your router transmits this name to surrounding devices. Its primary
function is to make your network visible and easily accessible. Most routers broadcast their
SSIDs automatically. To disable or enable SSID broadcast, you need to change your
router’s settings.
Disabling SSID broadcast will make your Wi-FI network name invisible to other users.
However, this only hides the name, not the network itself. You cannot disguise the router's
activity, so hackers can still attack it.
With your network invisible to wireless devices, connecting becomes a bit more
complicated. Just giving a Wi-FI password to your guests is no longer enough. They have
to configure their settings manually by including the network name, security mode, and
other relevant info.
Disabling SSID might be a small step towards online security, but by no means should it be
your final one. Before considering it as a security measure, consider the following aspects:
- Disabling SSID broadcast will not hide your network completely
Disabling SSID broadcast only hides the network name, not the fact that it exists. Your
router constantly transmits so-called beacon frames to announce the presence of a
wireless network. They contain essential information about the network and help the device
connect.
- Third-party software can easily trace a hidden network
Programs such as NetStumbler or Kismet can easily locate hidden networks. You can try
using them yourself to see how easy it is to find available networks – hidden or not.
- You might attract unwanted attention.
Disabling your SSID broadcast could also raise suspicion. Most of us assume that when
somebody hides something, they have a reason to do so. Thus, some hackers might be
attracted to your network.
You work for Acme Corporation as Sales Manager. The company has tight network
security restrictions. You are trying to steal data from the company's Sales database
(Sales.xls) and transfer them to your home computer. Your company filters and monitors
traffic that leaves from the internal network to the Internet. How will you achieve this without
raising suspicion?
A.
Encrypt the Sales.xls using PGP and e-mail it to your personal gmail account
B.
Package the Sales.xls using Trojan wrappers and telnet them back your home computer
C.
You can conceal the Sales.xls database in another file like photo.jpg or other files and
send it out in an innocent looking email or file transfer using Steganography techniques
D.
Change the extension of Sales.xls to sales.txt and upload them as attachment to your
hotmail account
You can conceal the Sales.xls database in another file like photo.jpg or other files and
send it out in an innocent looking email or file transfer using Steganography techniques
| Page 21 out of 48 Pages |
| Previous |