Topic 2: Exam Pool B
When a security analyst prepares for the formal security assessment - what of the following
should be done in order to determine inconsistencies in the secure assets database and
verify that system is compliant to the minimum security baseline?
A.
Data items and vulnerability scanning
B.
Interviewing employees and network engineers
C.
Reviewing the firewalls configuration
D.
Source code review
Data items and vulnerability scanning
Susan, a software developer, wants her web API to update other applications with the
latest information. For this purpose, she uses a user-defined HTTP tailback or push APIs
that are raised based on trigger events: when invoked, this feature supplies data to other
applications so that users can instantly receive real-time Information. Which of the following techniques is employed by Susan?
A.
web shells
B.
Webhooks
C.
REST API
D.
SOAP API
Webhooks
Explanation: Webhooks are one of a few ways internet applications will communicate with
one another.
It allows you to send real-time data from one application to another whenever a given event
happens.
For example, let’s say you’ve created an application using the Foursquare API that tracks
when people check into your restaurant. You ideally wish to be able to greet customers by
name and provide a complimentary drink when they check in.
What a webhook will is notify you any time someone checks in, therefore you’d be able to
run any processes that you simply had in your application once this event is triggered.
The data is then sent over the web from the application wherever the event originally
occurred, to the receiving application that handles the data.
Here’s a visual representation of what that looks like:
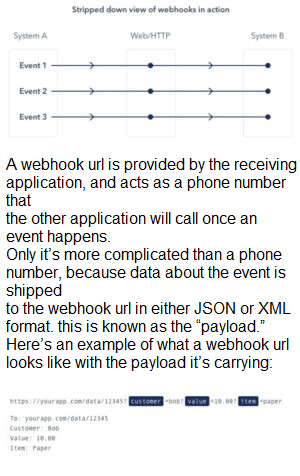
What are Webhooks? Webhooks are user-defined HTTP callback or push APIs that are
raised based on events triggered, such as comment received on a post and pushing code
to the registry. A webhook allows an application to update other applications with the latest information. Once invoked, it supplies data to the other applications, which means that
users instantly receive real-time information. Webhooks are sometimes called “Reverse
APIs” as they provide what is required for API specification, and the developer should
create an API to use a webhook. A webhook is an API concept that is also used to send
text messages and notifications to mobile numbers or email addresses from an application
when a specific event is triggered. For instance, if you search for something in the online
store and the required item is out of stock, you click on the “Notify me” bar to get an alert
from the application when that item is available for purchase. These notifications from the
applications are usually sent through webhooks
Which of the following DoS tools is used to attack target web applications by starvation of
available sessions on the web server?
The tool keeps sessions at halt using never-ending POST transmissions and sending an
arbitrarily large content-length header value.
A.
My Doom
B.
Astacheldraht
C.
R-U-Dead-Yet?(RUDY)
D.
LOIC
R-U-Dead-Yet?(RUDY)
John, a disgruntled ex-employee of an organization, contacted a professional hacker to
exploit the organization. In the attack process, the professional hacker Installed a scanner
on a machine belonging to one of the vktims and scanned several machines on the same
network to Identify vulnerabilities to perform further exploitation. What is the type of
vulnerability assessment tool employed by John in the above scenario?
A.
Proxy scanner
B.
Agent-based scanner
C.
Network-based scanner
D.
Cluster scanner
Network-based scanner
Explanation: Network-based scanner
A network-based vulnerability scanner, in simplistic terms, is the process of identifying
loopholes on a computer’s network or IT assets, which hackers and threat actors can
exploit. By implementing this process, one can successfully identify their organization’s
current risk(s). This is not where the buck stops; one can also verify the effectiveness of
your system's security measures while improving internal and external defenses. Through
this review, an organization is well equipped to take an extensive inventory of all systems,
including operating systems, installed software, security patches, hardware, firewalls, antivirus
software, and much more.
Agent-based scanner
Agent-based scanners make use of software scanners on each and every device; the
results of the scans are reported back to the central server. Such scanners are well
equipped to find and report out on a range of vulnerabilities.
NOTE: This option is not suitable for us, since for it to work, you need to install a special
agent on each computer before you start collecting data from them.
The tools which receive event logs from servers, network equipment, and applications, and
perform analysis and correlation on those logs, and can generate alarms for security
relevant issues, are known as what?
A.
network Sniffer
B.
Vulnerability Scanner
C.
Intrusion prevention Server
D.
Security incident and event Monitoring
Security incident and event Monitoring
Windows LAN Manager (LM) hashes are known to be weak.
Which of the following are known weaknesses of LM? (Choose three.)
A.
Converts passwords to uppercase.
B.
Hashes are sent in clear text over the network.
C.
Makes use of only 32-bit encryption
D.
Effective length is 7 characters.
Converts passwords to uppercase.
Hashes are sent in clear text over the network.
Effective length is 7 characters.
what is the port to block first in case you are suspicious that an loT device has been
compromised?
A.
22
B.
443
C.
48101
D.
80
48101
Explanation: TCP port 48101 uses the Transmission management Protocol. transmission
control protocol is one in all the most protocols in TCP/IP networks. transmission control
protocol could be a connection-oriented protocol, it needs acknowledgement to line up endto-
end communications. only a association is about up user’s knowledge may be sent bidirectionally
over the association.
Attention! transmission control protocol guarantees delivery of knowledge packets on port
48101 within the same order during which they were sent. bonded communication over
transmission control protocol port 48101 is that the main distinction between transmission
control protocol and UDP. UDP port 48101 wouldn’t have bonded communication as
transmission control protocol.
UDP on port 48101 provides Associate in Nursing unreliable service and datagrams might
arrive duplicated, out of order, or missing unexpectedly. UDP on port 48101 thinks that
error checking and correction isn’t necessary or performed within the application, avoiding
the overhead of such process at the network interface level.
UDP (User Datagram Protocol) could be a borderline message-oriented Transport Layer
protocol (protocol is documented in IETF RFC 768).
Application examples that always use UDP: vocalisation IP (VoIP), streaming media and
period multiplayer games. several internet applications use UDP, e.g. the name System
(DNS), the Routing info Protocol (RIP), the Dynamic Host Configuration Protocol (DHCP),
the straightforward Network Management Protocol (SNMP).
Gerard, a disgruntled ex-employee of Sunglass IT Solutions, targets this organization to
perform sophisticated attacks and bring down its reputation in the market. To launch the
attacks process, he performed DNS footprinting to gather information about ONS servers
and to identify the hosts connected in the target network. He used an automated tool that
can retrieve information about DNS zone data including DNS domain names, computer
names. IP addresses. DNS records, and network Who is records. He further exploited this
information to launch other sophisticated attacks. What is the tool employed by Gerard in
the above scenario?
A.
Knative
B.
zANTI
C.
Towelroot
D.
Bluto
Bluto
Explanation: https://www.darknet.org.uk/2017/07/bluto-dns-recon-zone-transfer-bruteforcer/
"Attackers also use DNS lookup tools such as DNSdumpster.com, Bluto, and Domain
Dossier to retrieve DNS records for a specified domain or hostname. These tools retrieve
information such as domains and IP addresses, domain Whois records, DNS records, and
network Whois records." CEH Module 02 Page 138
What do Trinoo, TFN2k, WinTrinoo, T-Sight, and Stracheldraht have in common?
A.
All are hacking tools developed by the legion of doom
B.
All are tools that can be used not only by hackers, but also security personnel
C.
All are DDOS tools
D.
All are tools that are only effective against Windows
E.
All are tools that are only effective against Linux
All are DDOS tools
In this attack, a victim receives an e-mail claiming from PayPal stating that their account
has been disabled and confirmation is required before activation. The attackers then scam
to collect not one but two credit card numbers, ATM PIN number and other personal
details. Ignorant users usually fall prey to this scam.
Which of the following statement is incorrect related to this attack?
A.
Do not reply to email messages or popup ads asking for personal or financial
information
B.
Do not trust telephone numbers in e-mails or popup ads
C.
Review credit card and bank account statements regularly
D.
Antivirus, anti-spyware, and firewall software can very easily detect these type of attacks
E.
Do not send credit card numbers, and personal or financial information via e-mail
Antivirus, anti-spyware, and firewall software can very easily detect these type of attacks
Gilbert, a web developer, uses a centralized web API to reduce complexity and increase
the Integrity of updating and changing data. For this purpose, he uses a web service that
uses HTTP methods such as PUT. POST. GET. and DELETE and can improve the overall
performance, visibility, scalability, reliability, and portability of an application. What is the
type of web-service API mentioned in the above scenario?
A.
JSON-RPC
B.
SOAP API
C.
RESTful API
D.
REST API
RESTful API
Explanation: *REST is not a specification, tool, or framework, but instead is an
architectural style for web services that serves as a communication medium between
various systems on the web. *RESTful APIs, which are also known as RESTful services,
are designed using REST principles and HTTP communication protocols RESTful is a
collection of resources that use HTTP methods such as PUT, POST, GET, and DELETE
RESTful API: RESTful API is a RESTful service that is designed using REST principles and
HTTP communication protocols. RESTful is a collection of resources that use HTTP
methods such as PUT, POST, GET, and DELETE. RESTful API is also designed to make applications independent to improve the overall performance, visibility, scalability, reliability,
and portability of an application. APIs with the following features can be referred to as to
RESTful APIs: o Stateless: The client end stores the state of the session; the server is
restricted to save data during the request processing o Cacheable: The client should save
responses (representations) in the cache. This feature can enhance API performance pg.
1920 CEHv11 manual.
https://cloud.google.com/files/apigee/apigee-web-api-design-the-missing-link-ebook.pdf
The HTTP methods GET, POST, PUT or PATCH, and DELETE can be used with these
templates to read, create, update, and delete description resources for dogs and their
owners. This API style has become popular for many reasons. It is straightforward and
intuitive, and learning this pattern is similar to learning a programming language API. APIs
like this one are commonly called RESTful APIs, although they do not display all of the
characteristics that define REST (more on REST later).
John, a professional hacker, targeted an organization that uses LDAP for accessing
distributed directory services. He used an automated tool to anonymously query the IDAP
service for sensitive information such as usernames. addresses, departmental details, and
server names to launch further attacks on the target organization.
What is the tool employed by John to gather information from the IDAP service?
A.
jxplorer
B.
Zabasearch
C.
EarthExplorer
D.
Ike-scan
jxplorer
Explanation: JXplorer could be a cross platform LDAP browser and editor. it’s a standards
compliant general purpose LDAP client which will be used to search, scan and edit any
commonplace LDAP directory, or any directory service with an LDAP or DSML interface.
It is extremely flexible and can be extended and custom in a very number of the way.
JXplorer is written in java, and also the source code and source code build system ar
obtainable via svn or as a packaged build for users who wish to experiment or any develop
the program.
JX is is available in 2 versions; the free open source version under an OSI Apache two style licence, or within the JXWorkBench Enterprise bundle with inbuilt reporting,
administrative and security tools.
JX has been through a number of different versions since its creation in 1999; the foremost
recent stable release is version 3.3.1, the August 2013 release.
JXplorer could be a absolutely useful LDAP consumer with advanced security integration
and support for the harder and obscure elements of the LDAP protocol. it’s been tested on
Windows, Solaris, linux and OSX, packages are obtainable for HPUX, AIX, BSD and it
should run on any java supporting OS.
| Page 20 out of 48 Pages |
| Previous |