Topic 2: Exam Pool B
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch.
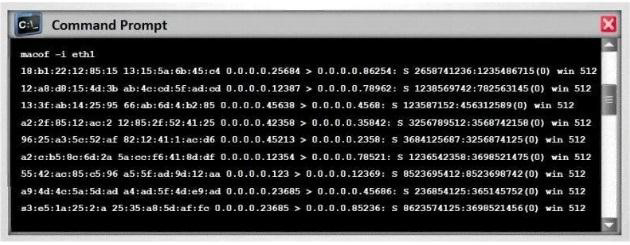
In MAC flooding attack, a switch is fed with many Ethernet frames, each containing
different source MAC addresses, by the attacker. Switches have a limited memory for
mapping various MAC addresses to physical ports. What happens when the CAM table
becomes full?
A.
Switch then acts as hub by broadcasting packets to all machines on the network
B.
The CAM overflow table will cause the switch to crash causing Denial of Service
C.
The switch replaces outgoing frame switch factory default MAC address of
FF:FF:FF:FF:FF:FF
D.
Every packet is dropped and the switch sends out SNMP alerts to the IDS port
Switch then acts as hub by broadcasting packets to all machines on the network
Widespread fraud ac Enron. WorldCom, and Tyco led to the creation of a law that was
designed to improve the accuracy and accountability of corporate disclosures. It covers
accounting firms and third parties that provide financial services to some organizations and
came into effect in 2002. This law is known by what acronym?
A.
Fed RAMP
B.
PCIDSS
C.
SOX
D.
HIPAA
SOX
Explanation: The Sarbanes-Oxley Act of 2002 could be a law the U.S. Congress passed
on July thirty of that year to assist defend investors from fallacious money coverage by
companies.Also called the SOX Act of 2002 and also the company Responsibility Act of
2002, it mandated strict reforms to existing securities rules and obligatory powerful new
penalties on law breakers.
The Sarbanes-Oxley law Act of 2002 came in response to money scandals within the early
2000s involving in public listed corporations like Enron Corporation, Tyco International plc,
and WorldCom. The high-profile frauds cask capitalist confidence within the trustiness of
company money statements Associate in Nursingd light-emitting diode several to demand
an overhaul of decades-old restrictive standards.
Nathan is testing some of his network devices. Nathan is using Macof to try and flood the
ARP cache of these switches.
If these switches' ARP cache is successfully flooded, what will be the result?
A.
The switches will drop into hub mode if the ARP cache is successfully flooded
B.
If the ARP cache is flooded, the switches will drop into pix mode making it less
susceptible to attacks.
C.
Depending on the switch manufacturer, the device will either delete every entry in its
ARP cache or reroute packets to the nearest switch.
D.
The switches will route all traffic to the broadcast address created collisions
The switches will drop into hub mode if the ARP cache is successfully flooded
You are tasked to configure the DHCP server to lease the last 100 usable IP addresses in
subnet to. 1.4.0/23. Which of the following IP addresses could be teased as a result of the
new configuration?
A.
210.1.55.200
B.
10.1.4.254
C.
10..1.5.200
D.
10.1.4.156
10..1.5.200
During the process of encryption and decryption, what keys are shared?
A.
Private keys
B.
User passwords
C.
Public keys
D.
Public and private keys
Public keys
An organization is performing a vulnerability assessment tor mitigating threats. James, a
pen tester, scanned the organization by building an inventory of the protocols found on the
organization's machines to detect which ports are attached to services such as an email
server, a web server or a database server. After identifying the services, he selected the
vulnerabilities on each machine and started executing only the relevant tests. What is the
type of vulnerability assessment solution that James employed in the above scenario?
A.
Product-based solutions
B.
Tree-based assessment
C.
Service-based solutions
D.
inference-based assessment
inference-based assessment
Explanation: In an inference-based assessment, scanning starts by building an inventory
of the protocols found on the machine. After finding a protocol, the scanning process starts
to detect which ports are attached to services, such as an email server, web server, or
database server. After finding services, it selects vulnerabilities on each machine and starts
to execute only those relevant tests.
Log monitoring tools performing behavioral analysis have alerted several suspicious logins
on a Linux server occurring during non-business hours. After further examination of all login
activities, it is noticed that none of the logins have occurred during typical work hours. A
Linux administrator who is investigating this problem realizes the system time on the Linux
server is wrong by more than twelve hours. What protocol used on Linux servers to
synchronize the time has stopped working?
A.
Time Keeper
B.
NTP
C.
PPP
D.
OSPP
NTP
Clark is a professional hacker. He created and configured multiple domains pointing to the
same host to switch quickly between the domains and avoid detection.
Identify the behavior of the adversary In the above scenario.
A.
use of command-line interface
B.
Data staging
C.
Unspecified proxy activities
D.
Use of DNS tunneling
Unspecified proxy activities
Explanation: A proxy server acts as a gateway between you and therefore the internet. It’s
an intermediary server separating end users from the websites they browse. Proxy servers
provide varying levels of functionality, security, and privacy counting on your use case,
needs, or company policy.If you’re employing a proxy server, internet traffic flows through
the proxy server on its thanks to the address you requested. A proxy server is essentially a
computer on the web with its own IP address that your computer knows. once you send an
internet request, your request goes to the proxy server first. The proxy server then makes
your web request on your behalf, collects the response from the online server, and
forwards you the online page data so you’ll see the page in your browser.
When discussing passwords, what is considered a brute force attack?
A.
You attempt every single possibility until you exhaust all possible combinations or
discover the password
B.
You threaten to use the rubber hose on someone unless they reveal their password
C.
You load a dictionary of words into your cracking program
D.
You create hashes of a large number of words and compare it with the encrypted
passwords
E.
You wait until the password expires
You attempt every single possibility until you exhaust all possible combinations or
discover the password
Bob is going to perform an active session hijack against Brownies Inc. He has found a target that allows session oriented connections (Telnet) and performs the sequence
prediction on the target operating system. He manages to find an active session due to the
high level of traffic on the network. What is Bob supposed to do next?
A.
Take over the session
B.
Reverse sequence prediction
C.
Guess the sequence numbers
D.
Take one of the parties offline
Guess the sequence numbers
Every company needs a formal written document which spells out to employees precisely
what they are allowed to use the company's systems for, what is prohibited, and what will
happen to them if they break the rules. Two printed copies of the policy should be given to
every employee as soon as possible after they join the organization. The employee should
be asked to sign one copy, which should be safely filed by the company. No one should be
allowed to use the company's computer systems until they have signed the policy in
acceptance of its terms.
What is this document called?
A.
Information Audit Policy (IAP)
B.
Information Security Policy (ISP)
C.
Penetration Testing Policy (PTP)
D.
Company Compliance Policy (CCP)
Information Security Policy (ISP)
Samuel a security administrator, is assessing the configuration of a web server. He noticed
that the server permits SSlv2 connections, and the same private key certificate is used on a
different server that allows SSLv2 connections. This vulnerability makes the web server
vulnerable to attacks as the SSLv2 server can leak key information.
Which of the following attacks can be performed by exploiting the above vulnerability?
A.
DROWN attack
B.
Padding oracle attack
C.
Side-channel attack
D.
DUHK attack
DROWN attack
| Page 18 out of 48 Pages |
| Previous |