Topic 2: Exam Pool B
In the context of password security, a simple dictionary attack involves loading a dictionary
file (a text file full of dictionary words) into a cracking application such as L0phtCrack or
John the Ripper, and running it against user accounts located by the application. The larger
the word and word fragment selection, the more effective the dictionary attack is. The brute
force method is the most inclusive, although slow. It usually tries every possible letter and number combination in its automated exploration. If you would use both brute force and
dictionary methods combined together to have variation of words, what would you call such
an attack?
A.
Full Blown
B.
Thorough
C.
Hybrid
D.
BruteDics
Hybrid
To invisibly maintain access to a machine, an attacker utilizes a toolkit that sits undetected
In the core components of the operating system. What is this type of rootkit an example of?
A.
Mypervisor rootkit
B.
Kernel toolkit
C.
Hardware rootkit
D.
Firmware rootkit
Kernel toolkit
Explanation: Kernel-mode rootkits run with the best operating system privileges (Ring 0)
by adding code or replacement parts of the core operating system, as well as each the
kernel and associated device drivers. Most operative systems support kernel-mode device
drivers, that execute with a similar privileges because the software itself. As such, several
kernel-mode rootkits square measure developed as device drivers or loadable modules,
like loadable kernel modules in Linux or device drivers in Microsoft Windows. This category
of rootkit has unrestricted security access, however is tougher to jot down. The quality
makes bugs common, and any bugs in code operative at the kernel level could seriously
impact system stability, resulting in discovery of the rootkit. one amongst the primary wide
familiar kernel rootkits was developed for Windows NT four.0 and discharged in Phrack
magazine in 1999 by Greg Hoglund. Kernel rootkits is particularly tough to observe and
take away as a result of they operate at a similar security level because the software itself,
and square measure therefore able to intercept or subvert the foremost sure software
operations. Any package, like antivirus package, running on the compromised system is
equally vulnerable. during this scenario, no a part of the system is sure.
Which of the following commands checks for valid users on an SMTP server?
A.
RCPT
B.
CHK
C.
VRFY
D.
VRFY
VRFY
Explanation: The VRFY commands enables SMTP clients to send an invitation to an
SMTP server to verify that mail for a selected user name resides on the server. The VRFY
command is defined in RFC 821.The server sends a response indicating whether the user
is local or not, whether mail are going to be forwarded, and so on. A response of 250
indicates that the user name is local; a response of 251 indicates that the user name isn’t
local, but the server can forward the message. The server response includes the mailbox
name.
Why containers are less secure that virtual machines?
A.
Host OS on containers has a larger surface attack.
B.
Containers may full fill disk space of the host.
C.
A compromise container may cause a CPU starvation of the host.
D.
Containers are attached to the same virtual network.
Host OS on containers has a larger surface attack.
which of the following Bluetooth hacking techniques refers to the theft of information from a
wireless device through Bluetooth?
A.
Bluesmacking
B.
Bluebugging
C.
Bluejacking
D.
Bluesnarfing
Bluesnarfing
Explanation:
Bluesnarfing is the unauthorized access of information from a wireless device through
a Bluetooth connection, often between phones, desktops, laptops, and PDAs (personal
digital assistant).
John wants to send Marie an email that includes sensitive information, and he does not
trust the network that he is connected to. Marie gives him the idea of using PGP. What
should John do to communicate correctly using this type of encryption?
A.
Use his own public key to encrypt the message.
B.
Use Marie's public key to encrypt the message.
C.
Use his own private key to encrypt the message
D.
Use Marie's private key to encrypt the message.
Use Marie's public key to encrypt the message.
Explanation: When a user encrypts plaintext with PGP, PGP first compresses the
plaintext. The session key works with a very secure, fast conventional encryption algorithm
to encrypt the plaintext; the result is ciphertext. Once the data is encrypted, the session key
is then encrypted to the recipient's public key
https://en.wikipedia.org/wiki/Pretty_Good_Privacy
Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy
and authentication for data communication. PGP is used for signing, encrypting, and
decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the
security of e-mail communications.
PGP encryption uses a serial combination of hashing, data compression, symmetric-key
cryptography, and finally public-key cryptography; each step uses one of several supported
algorithms. Each public key is bound to a username or an e-mail address.
https://en.wikipedia.org/wiki/Public-key_cryptography
Public key encryption uses two different keys. One key is used to encrypt the information
and the other is used to decrypt the information. Sometimes this is referred to as
asymmetric encryption because two keys are required to make the system and/or process work securely. One key is known as the public key and should be shared by the owner with
anyone who will be securely communicating with the key owner. However, the owner’s
secret key is not to be shared and considered a private key. If the private key is shared with
unauthorized recipients, the encryption mechanisms protecting the information must be
considered compromised.
Take a look at the following attack on a Web Server using obstructed URL:
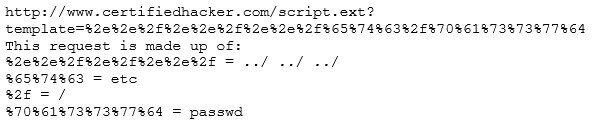
How would you protect from these attacks?
A.
Configure the Web Server to deny requests involving "hex encoded" characters
B.
Create rules in IDS to alert on strange Unicode requests
C.
Use SSL authentication on Web Servers
D.
Enable Active Scripts Detection at the firewall and routers
Create rules in IDS to alert on strange Unicode requests
what firewall evasion scanning technique make use of a zombie system that has low
network activity as well as its fragment identification numbers?
A.
Decoy scanning
B.
Packet fragmentation scanning
C.
Spoof source address scanning
D.
Idle scanning
Idle scanning
Explanation: The idle scan could be a communications protocol port scan technique that
consists of causing spoofed packets to a pc to seek out out what services square measure
obtainable. this can be accomplished by impersonating another pc whose network traffic is
extremely slow or nonexistent (that is, not transmission or receiving information). this might
be associate idle pc, known as a “zombie”.
This action are often done through common code network utilities like nmap and hping. The
attack involves causing solid packets to a particular machine target in an attempt to seek
out distinct characteristics of another zombie machine. The attack is refined as a result of
there’s no interaction between the offender pc and also the target: the offender interacts
solely with the “zombie” pc.
This exploit functions with 2 functions, as a port scanner and a clerk of sure informatics
relationships between machines. The target system interacts with the “zombie” pc and
distinction in behavior are often discovered mistreatment totally different|completely
different “zombies” with proof of various privileges granted by the target to different
computers.
The overall intention behind the idle scan is to “check the port standing whereas remaining
utterly invisible to the targeted host.”
The first step in execution associate idle scan is to seek out associate applicable zombie. It
must assign informatics ID packets incrementally on a worldwide (rather than per-host it
communicates with) basis. It ought to be idle (hence the scan name), as extraneous traffic
can raise its informatics ID sequence, confusing the scan logic. The lower the latency
between the offender and also the zombie, and between the zombie and also the target,
the quicker the scan can proceed.
Note that once a port is open, IPIDs increment by a pair of. Following is that the sequence:
offender to focus on -> SYN, target to zombie ->SYN/ACK, Zombie to focus on ->
RST (IPID increment by 1)
currently offender tries to probe zombie for result. offender to Zombie ->SYN/ACK,
Zombie to offender -> RST (IPID increment by 1)
So, during this method IPID increments by a pair of finally.
When associate idle scan is tried, tools (for example nmap) tests the projected zombie and
reports any issues with it. If one does not work, attempt another. Enough net hosts square
measure vulnerable that zombie candidates are not exhausting to seek out. a standard
approach is to easily execute a ping sweep of some network. selecting a network close to
your supply address, or close to the target, produces higher results. you’ll be able to
attempt associate idle scan mistreatment every obtainable host from the ping sweep results
till you discover one that works. As usual, it’s best to raise permission before mistreatment
someone’s machines for surprising functions like idle scanning.
Simple network devices typically create nice zombies as a result of {they square
measure|they’re} normally each underused (idle) and designed with straightforward
network stacks that are susceptible to informatics ID traffic detection.
While distinguishing an acceptable zombie takes some initial work, you’ll be able to keep
re-using the nice ones. as an alternative, there are some analysis on utilizing unplanned
public internet services as zombie hosts to perform similar idle scans. leverage the
approach a number of these services perform departing connections upon user submissions will function some quite poor’s man idle scanning.
What is the main security service a cryptographic hash provides?
A.
Integrity and ease of computation
B.
Message authentication and collision resistance
C.
Integrity and collision resistance
D.
Integrity and computational in-feasibility
Integrity and computational in-feasibility
You went to great lengths to install all the necessary technologies to prevent hacking
attacks, such as expensive firewalls, antivirus software, anti-spam systems and intrusion
detection/prevention tools in your company's network. You have configured the most
secure policies and tightened every device on your network. You are confident that hackers
will never be able to gain access to your network with complex security system in place.
Your peer, Peter Smith who works at the same department disagrees with you.
He says even the best network security technologies cannot prevent hackers gaining
access to the network because of presence of "weakest link" in the security chain.
What is Peter Smith talking about?
A.
Untrained staff or ignorant computer users who inadvertently become the weakest link in
your security chain
B.
"zero-day" exploits are the weakest link in the security chain since the IDS will not be
able to detect these attacks
C.
"Polymorphic viruses" are the weakest link in the security chain since the Anti-Virus
scanners will not be able to detect these attacks
D.
Continuous Spam e-mails cannot be blocked by your security system since spammers
use different techniques to bypass the filters in your gateway
Untrained staff or ignorant computer users who inadvertently become the weakest link in
your security chain
Which type of sniffing technique is generally referred as MiTM attack?
A.
Password Sniffing
B.
ARP Poisoning
C.
Mac Flooding
D.
DHCP Sniffing
ARP Poisoning
Attacker Rony Installed a rogue access point within an organization's perimeter and
attempted to Intrude into its internal network. Johnson, a security auditor, identified some
unusual traffic in the internal network that is aimed at cracking the authentication
mechanism. He immediately turned off the targeted network and tested for any weak and
outdated security mechanisms that are open to attack. What is the type of vulnerability
assessment performed by Johnson in the above scenario?
A.
Distributed assessment
B.
Wireless network assessment
C.
Most-based assessment
D.
Application assessment
Wireless network assessment
Explanation:
Expanding your network capabilities are often done well using wireless networks, but it also
can be a source of harm to your data system . Deficiencies in its implementations or
configurations can allow tip to be accessed in an unauthorized manner.This makes it
imperative to closely monitor your wireless network while also conducting periodic Wireless
Network assessment.It identifies flaws and provides an unadulterated view of exactly how
vulnerable your systems are to malicious and unauthorized accesses.Identifying
misconfigurations and inconsistencies in wireless implementations and rogue access points
can improve your security posture and achieve compliance with regulatory frameworks
| Page 14 out of 48 Pages |
| Previous |