Topic 1: Exam Pool A
MX record priority increases as the number increases. (True/False.)
A.
True
B.
False
False
Bob, a system administrator at TPNQM SA, concluded one day that a DMZ is not needed if
he properly configures the firewall to allow access just to servers/ports, which can have
direct internet access, and block the access to workstations.
Bob also concluded that DMZ makes sense just when a stateful firewall is available, which
is not the case of TPNQM SA.
In this context, what can you say?
A.
Bob can be right since DMZ does not make sense when combined with stateless
firewalls
B.
Bob is partially right. He does not need to separate networks if he can create rules by
destination IPs, one by one
C.
Bob is totally wrong. DMZ is always relevant when the company has internet servers
and workstations
D.
Bob is partially right. DMZ does not make sense when a stateless firewall is available
Bob is totally wrong. DMZ is always relevant when the company has internet servers
and workstations
The following is an entry captured by a network IDS. You are assigned the task of analyzing this entry. You notice the value 0x90, which is the most common NOOP
instruction for the Intel processor. You figure that the attacker is attempting a buffer
overflow attack.
You also notice "/bin/sh" in the ASCII part of the output.
As an analyst what would you conclude about the attack?
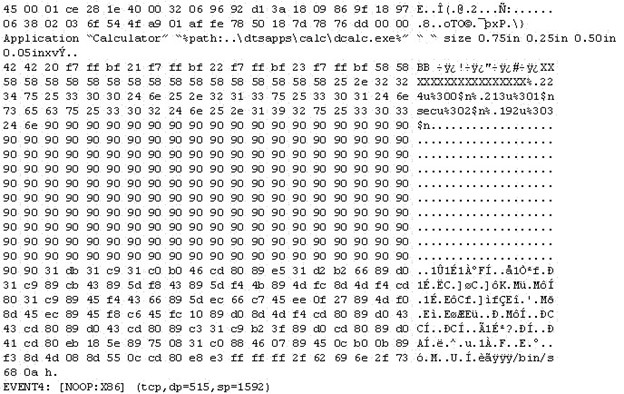
A.
The buffer overflow attack has been neutralized by the IDS
B.
The attacker is creating a directory on the compromised machine
C.
The attacker is attempting a buffer overflow attack and has succeeded
D.
The attacker is attempting an exploit that launches a command-line shell
The attacker is attempting an exploit that launches a command-line shell
If a tester is attempting to ping a target that exists but receives no response or a response
that states the destination is unreachable, ICMP may be disabled and the network may be
using TCP. Which other option could the tester use to get a response from a host using
TCP?
A.
Traceroute
B.
Hping
C.
TCP ping
D.
Broadcast ping
Hping
What is the following command used for?
net use \targetipc$ "" /u:""
A.
Grabbing the etc/passwd file
B.
Grabbing the SAM
C.
Connecting to a Linux computer through Samba
D.
This command is used to connect as a null session
E.
Enumeration of Cisco routers
This command is used to connect as a null session
Null sessions are un-authenticated connections (not using a username or password.) to an
NT or 2000 system. Which TCP and UDP ports must you filter to check null sessions on
your network?
A.
137 and 139
B.
137 and 443
C.
139 and 443
D.
139 and 445
139 and 445
What is a “Collision attack” in cryptography?
A.
Collision attacks try to get the public key
B.
Collision attacks try to break the hash into three parts to get the plaintext value
C.
Collision attacks try to break the hash into two parts, with the same bytes in each part to
get the private key
D.
Collision attacks try to find two inputs producing the same hash
Collision attacks try to find two inputs producing the same hash
Which of the following is a low-tech way of gaining unauthorized access to systems?
A.
Social Engineering
B.
Eavesdropping
C.
Scanning
D.
Sniffing
Social Engineering
You are a Network Security Officer. You have two machines. The first machine
(192.168.0.99) has snort installed, and the second machine (192.168.0.150) has kiwi
syslog installed. You perform a syn scan in your network, and you notice that kiwi syslog is
not receiving the alert message from snort. You decide to run wireshark in the snort
machine to check if the messages are going to the kiwi syslog machine. What Wireshark
filter will show the connections from the snort machine to kiwi syslog machine?
A.
tcp.srcport= = 514 && ip.src= = 192.168.0.99
B.
tcp.srcport= = 514 && ip.src= = 192.168.150
C.
tcp.dstport= = 514 && ip.dst= = 192.168.0.99
D.
tcp.dstport= = 514 && ip.dst= = 192.168.0.150
tcp.dstport= = 514 && ip.dst= = 192.168.0.150
Which of the following Linux commands will resolve a domain name into IP address?
A.
>host-t a hackeddomain.com
B.
>host-t ns hackeddomain.com
C.
>host -t soa hackeddomain.com
D.
>host -t AXFR hackeddomain.com
>host-t a hackeddomain.com
A user on your Windows 2000 network has discovered that he can use L0phtcrack to sniff
the SMB exchanges which carry user logons. The user is plugged into a hub with 23 other
systems.
However, he is unable to capture any logons though he knows that other users are logging
in.
What do you think is the most likely reason behind this?
A.
There is a NIDS present on that segment.
B.
Kerberos is preventing it.
C.
Windows logons cannot be sniffed.
D.
L0phtcrack only sniffs logons to web servers.
Kerberos is preventing it.
Hackers often raise the trust level of a phishing message by modeling the email to look
similar to the internal email used by the target company. This includes using logos,
formatting, and names of the target company. The phishing message will often use the
name of the company CEO, President, or Managers. The time a hacker spends performing research to locate this information about a company is known as?
A.
Exploration
B.
Investigation
C.
Reconnaissance
D.
Enumeration
Reconnaissance
| Page 11 out of 48 Pages |
| Previous |