The Payment Card Industry Data Security Standard (PCI DSS) contains six different
categories of control objectives. Each objective contains one or more requirements, which
must be followed in order to achieve compliance. Which of the following requirements
would best fit under the objective, "Implement strong access control measures"?
A.
Regularly test security systems and processes.
B.
Encrypt transmission of cardholder data across open, public networks.
C.
Assign a unique ID to each person with computer access.
D.
Use and regularly update anti-virus software on all systems commonly affected by malware.
Assign a unique ID to each person with computer access.
Bob, an attacker, has managed to access a target loT device. He employed an online tool
to gather information related to the model of the loT device and the certifications granted to
it. Which of the following tools did Bob employ to gather the above Information?
A.
search.com
B.
EarthExplorer
C.
Google image search
D.
FCC ID search
FCC ID search
You are tasked to configure the DHCP server to lease the last 100 usable IP addresses in
subnet to. 1.4.0/23. Which of the following IP addresses could be teased as a result of the
new configuration?
A.
210.1.55.200
B.
10.1.4.254
C.
10..1.5.200
D.
10.1.4.156
10..1.5.200
ViruXine.W32 virus hides their presence by changing the underlying executable code.
This Virus code mutates while keeping the original algorithm intact, the code changes itself
each time it runs, but the function of the code (its semantics) will not change at all.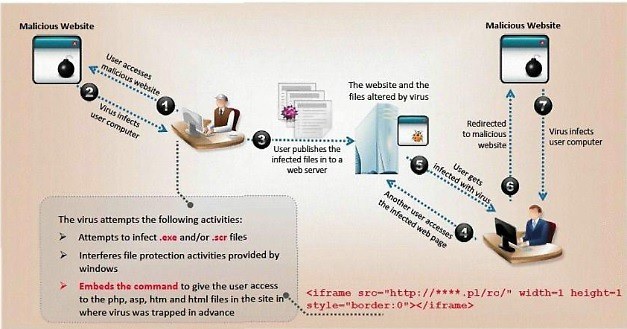
What is this technique called?
A.
Polymorphic Virus
B.
Metamorphic Virus
C.
Dravidic Virus
D.
Stealth Virus
Polymorphic Virus
Which method of password cracking takes the most time and effort?
A.
Dictionary attack
B.
Shoulder surfing
C.
Rainbow tables
D.
Brute force
Brute force
A new wireless client is configured to join a 802.11 network. This client uses the same
hardware and software as many of the other clients on the network. The client can see the
network, but cannot connect. A wireless packet sniffer shows that the Wireless Access
Point (WAP) is not responding to the association requests being sent by the wireless client.
What is a possible source of this problem?
A.
The WAP does not recognize the client’s MAC address
B.
The client cannot see the SSID of the wireless network
C.
Client is configured for the wrong channel
D.
The wireless client is not configured to use DHCP
The WAP does not recognize the client’s MAC address
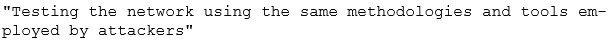
Identify the correct terminology that defines the above statement.
A.
Vulnerability Scanning
B.
Penetration Testing
C.
Security Policy Implementation
D.
Designing Network Security
Penetration Testing
Which regulation defines security and privacy controls for Federal information systems and organizations?
A.
HIPAA
B.
EU Safe Harbor
C.
PCI-DSS
D.
NIST-800-53
NIST-800-53
Samuel, a professional hacker, monitored and Intercepted already established traffic
between Bob and a host machine to predict Bob's ISN. Using this ISN, Samuel sent
spoofed packets with Bob's IP address to the host machine. The host machine responded
with <| packet having an Incremented ISN. Consequently. Bob's connection got hung, and
Samuel was able to communicate with the host machine on behalf of Bob. What is the type
of attack performed by Samuel in the above scenario?
A.
UDP hijacking
B.
Blind hijacking
C.
TCP/IP hacking
D.
Forbidden attack
TCP/IP hacking
Explanation:
A TCP/IP hijack is an attack that spoofs a server into thinking it’s talking with a sound
client, once actually it’s communication with an assaulter that has condemned (or hijacked)
the tcp session. Assume that the client has administrator-level privileges, which the
attacker needs to steal that authority so as to form a brand new account with root-level
access of the server to be used afterward. A tcp Hijacking is sort of a two-phased man-inthe-
middle attack. The man-in-the-middle assaulter lurks within the circuit between a
shopper and a server so as to work out what port and sequence numbers are being
employed for the conversation.
First, the attacker knocks out the client with an attack, like Ping of Death, or ties it up with
some reasonably ICMP storm. This renders the client unable to transmit any packets to the
server. Then, with the client crashed, the attacker assumes the client’s identity so as to talk
with the server. By this suggests, the attacker gains administrator-level access to the
server.
One of the most effective means of preventing a hijack attack is to want a secret, that’s a
shared secret between the shopper and also the server. looking on the strength of security
desired, the key may be used for random exchanges. this is often once a client and server
periodically challenge each other, or it will occur with each exchange, like Kerberos.
You have gained physical access to a Windows 2008 R2 server which has an accessible
disc drive. When you attempt to boot the server and log in, you are unable to guess the
password. In your toolkit, you have an Ubuntu 9.10 Linux LiveCD. Which Linux-based tool
can change any user’s password or activate disabled Windows accounts?
A.
John the Ripper
B.
SET
C.
CHNTPW
D.
Cain & Abel
CHNTPW
What is the role of test automation in security testing?
A.
It is an option but it tends to be very expensive.
B.
It should be used exclusively. Manual testing is outdated because of low speed and possible test setup inconsistencies.
C.
Test automation is not usable in security due to the complexity of the tests.
D.
It can accelerate benchmark tests and repeat them with a consistent test setup. But it cannot replace manual testing completely.
It can accelerate benchmark tests and repeat them with a consistent test setup. But it cannot replace manual testing completely.
What is the following command used for?
net use \targetipc$ "" /u:""
A.
Grabbing the etc/passwd file
B.
Grabbing the SAM
C.
Connecting to a Linux computer through Samba.
D.
This command is used to connect as a null session
E.
Enumeration of Cisco routers
This command is used to connect as a null session
| Page 8 out of 44 Pages |
| Previous |