Richard, an attacker, targets an MNC. in this process, he uses a footprinting technique to
gather as much information as possible. Using this technique, he gathers domain
information such as the target domain name, contact details of its owner, expiry date, and
creation date. With this information, he creates a map of the organization's network and
misleads domain owners with social engineering to obtain internal details of its network.
What type of footprinting technique is employed by Richard?
A.
VoIP footprinting
B.
VPN footprinting
C.
Whois footprinting
D.
Email footprinting
Email footprinting
Explanation:
Email header reveals information about the mail server, original sender’s email id, internal
IP addressing scheme, also because the possible architecture of the target network.
Tracking Email Communications• Email tracking is employed to watch the delivery of
emails to an intended recipient.• Attackers track emails to collect information a few target
recipient so as to perform social engineering and other attacks.• Get recipient’s system IP
address• Geolocation of the recipient• When the e-mail was received and skim• Whether or
not the recipient visited any links sent to them• Get recipient’s browser and OS information•
Time spent on reading the emails
Taylor, a security professional, uses a tool to monitor her company's website, analyze the
website's traffic, and track the geographical location of the users visiting the company's
website. Which of the following tools did Taylor employ in the above scenario?
A.
WebSite Watcher
B.
web-Stat
C.
Webroot
D.
WAFW00F
web-Stat
Explanation: Increase your web site’s performance and grow! Add Web-Stat to your site
(it’s free!) and watch individuals act together with your pages in real time.
Learn how individuals realize your web site. Get details concerning every visitor’s path
through your web site and track pages that flip browsers into consumers.
One-click install. observe locations, in operation systems, browsers and screen sizes and
obtain alerts for new guests and conversions
In Trojan terminology, what is a covert channel?
A.
A channel that transfers information within a computer system or network in a way that violates the security policy
B.
A legitimate communication path within a computer system or network for transfer of data
C.
It is a kernel operation that hides boot processes and services to mask detection
D.
It is Reverse tunneling technique that uses HTTPS protocol instead of HTTP protocol to establish connections
A channel that transfers information within a computer system or network in a way that violates the security policy
Every company needs a formal written document which spells out to employees precisely
what they are allowed to use the company's systems for, what is prohibited, and what will
happen to them if they break the rules. Two printed copies of the policy should be given to
every employee as soon as possible after they join the organization. The employee should
be asked to sign one copy, which should be safely filed by the company. No one should be
allowed to use the company's computer systems until they have signed the policy in
acceptance of its terms.
What is this document called?
A.
Information Audit Policy (IAP)
B.
Information Security Policy (ISP)
C.
Penetration Testing Policy (PTP)
D.
Company Compliance Policy (CCP)
Information Security Policy (ISP)
Kevin, a professional hacker, wants to penetrate CyberTech Inc.’s network. He employed a
technique, using which he encoded packets with Unicode characters. The company’s IDS
cannot recognize the packet, but the target web server can decode them.
What is the technique used by Kevin to evade the IDS system?
A.
Desynchronization
B.
Obfuscating
C.
Session splicing
D.
Urgency flag
Obfuscating
Explanation: Adversaries could decide to build an possible or file difficult to find or analyze
by encrypting, encoding, or otherwise obfuscating its contents on the system or in transit.
this is often common behavior which will be used across totally different platforms and
therefore the network to evade defenses
Payloads may be compressed, archived, or encrypted so as to avoid detection. These
payloads may be used throughout Initial Access or later to mitigate detection. typically a
user’s action could also be needed to open and Deobfuscate/Decode Files or info for User
Execution. The user can also be needed to input a parole to open a parole protected
compressed/encrypted file that was provided by the mortal. Adversaries can also used
compressed or archived scripts, like JavaScript.
Portions of files can even be encoded to cover the plain-text strings that will otherwise
facilitate defenders with discovery. Payloads can also be split into separate, ostensibly
benign files that solely reveal malicious practicality once reassembled.
Adversaries can also modify commands dead from payloads or directly via a Command
and Scripting Interpreter. surroundings variables, aliases, characters, and different
platform/language specific linguistics may be wont to evade signature based mostly
detections and application management mechanisms.
Which address translation scheme would allow a single public IP address to always correspond to a single machine on an internal network, allowing "server publishing"?
A.
Overloading Port Address Translation
B.
Dynamic Port Address Translation
C.
Dynamic Network Address Translation
D.
Static Network Address Translation
Static Network Address Translation
Henry Is a cyber security specialist hired by BlackEye - Cyber security solutions. He was
tasked with discovering the operating system (OS) of a host. He used the Unkornscan tool
to discover the OS of the target system. As a result, he obtained a TTL value, which
Indicates that the target system is running a Windows OS. Identify the TTL value Henry
obtained, which indicates that the target OS is Windows.
A.
A6
B.
128
C.
255
D.
138
128
Bob was recently hired by a medical company after it experienced a major cyber security
breach. Many patients are complaining that their personal medical records are fully
exposed on the Internet and someone can find them with a simple Google search. Bob's
boss is very worried because of regulations that protect those data. Which of the following
regulations is mostly violated?
A.
HIPPA/PHl
B.
Pll
C.
PCIDSS
D.
ISO 2002
Pll
If a tester is attempting to ping a target that exists but receives no response or a response
that states the destination is unreachable, ICMP may be disabled and the network may be
using TCP. Which other option could the tester use to get a response from a host using
TCP?
A.
Traceroute
B.
Hping
C.
TCP ping
D.
Broadcast ping
Hping
When a security analyst prepares for the formal security assessment - what of the following
should be done in order to determine inconsistencies in the secure assets database andverify that system is compliant to the minimum security baseline?
A.
Data items and vulnerability scanning
B.
Interviewing employees and network engineers
C.
Reviewing the firewalls configuration
D.
Source code review
Data items and vulnerability scanning
You are programming a buffer overflow exploit and you want to create a NOP sled of 200 bytes in the program exploit.c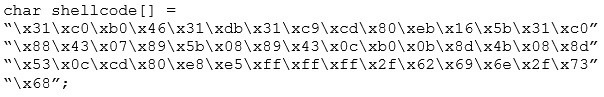
What is the hexadecimal value of NOP instruction?
A.
0x60
B.
0x80
C.
0x70
D.
0x90
0x90
Which definition among those given below best describes a covert channel?
A.
A server program using a port that is not well known.
B.
Making use of a protocol in a way it is not intended to be used.
C.
It is the multiplexing taking place on a communication link.
D.
It is one of the weak channels used by WEP which makes it insecure
Making use of a protocol in a way it is not intended to be used.
| Page 13 out of 44 Pages |
| Previous |