An organization is implementing and deploying the SIEM with following capabilities.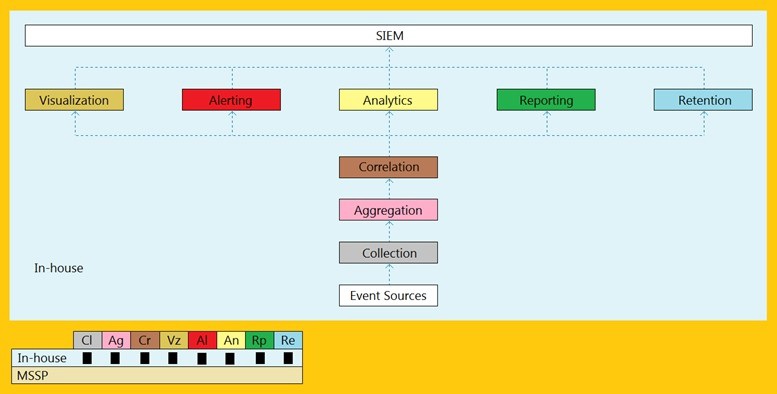
What kind of SIEM deployment architecture the organization is planning to implement?
A.
Cloud, MSSP Managed
B.
Self-hosted, Jointly Managed
C.
Self-hosted, Self-Managed
D.
Self-hosted, MSSP Managed
Cloud, MSSP Managed
In which log collection mechanism, the system or application sends log records either on the local disk or over the network.
A.
rule-based
B.
pull-based
C.
push-based
D.
signature-based
rule-based
Chloe, a SOC analyst with Jake Tech, is checking Linux systems logs. She is investigating
files at /var/log/ wtmp.
What Chloe is looking at?
A.
Error log
B.
System boot log
C.
General message and system-related stuff
D.
Login records
Login records
Where will you find the reputation IP database, if you want to monitor traffic from known bad IP reputation using OSSIM SIEM?
A.
/etc/ossim/reputation
B.
/etc/ossim/siem/server/reputation/data
C.
/etc/siem/ossim/server/reputation.data
D.
/etc/ossim/server/reputation.data
/etc/ossim/reputation
According to the forensics investigation process, what is the next step carried out right after collecting the evidence?
A.
Create a Chain of Custody Document
B.
Send it to the nearby police station
C.
Set a Forensic lab
D.
Call Organizational Disciplinary Team
Create a Chain of Custody Document
Which of the following command is used to enable logging in iptables?
A.
$ iptables -B INPUT -j LOG
B.
$ iptables -A OUTPUT -j LOG
C.
$ iptables -A INPUT -j LOG
D.
$ iptables -B OUTPUT -j LOG
$ iptables -A OUTPUT -j LOG
Reference: https://tecadmin.net/enable-logging-in-iptables-on-linux/
Peter, a SOC analyst with Spade Systems, is monitoring and analyzing the router logs of the company and wanted to check the logs that are generated by access control list numbered 210.
What filter should Peter add to the 'show logging' command to get the required output?
A.
show logging | access 210
B.
show logging | forward 210
C.
show logging | include 210
D.
show logging | route 210
show logging | include 210
What does the HTTP status codes 1XX represents?
A.
Informational messag
B.
Client error
C.
Success
D.
Redirection
Informational messag
Reference:
https://en.wikipedia.org/wiki/List_of_HTTP_status_codes#:~:text=1xx-informational%
20response-–-the-request,syntax-or-cannot-be-fulfilled
Which of the following is a report writing tool that will help incident handlers to generate efficient reports on detected incidents during incident response process?
A.
threat_note
B.
MagicTree
C.
IntelMQ
D.
Malstrom
IntelMQ
Ray is a SOC analyst in a company named Queens Tech. One Day, Queens Tech is
affected by a DoS/DDoS attack. For the containment of this incident, Ray and his team are
trying to provide additional bandwidth to the network devices and increasing the capacity of
the servers.
What is Ray and his team doing?
A.
Blocking the Attacks
B.
Diverting the Traffic
C.
Degrading the services
D.
Absorbing the Attack
Absorbing the Attack
Sam, a security analyst with INFOSOL INC., while monitoring and analyzing IIS logs,
detected an event matching regex /\\w*((\%27)|(\’))((\%6F)|o|(\%4F))((\%72)|r|(\%52))/ix.
What does this event log indicate?
A.
SQL Injection Attack
B.
Parameter Tampering Attack
C.
XSS Attack
D.
Directory Traversal Attack
SQL Injection Attack
Reference: https://community.broadcom.com/symantecenterprise/communities/communityhome/
librarydocuments/viewdocument?DocumentKey=001f5e09-88b4-4a9a-b310-
4c20578eecf9&CommunityKey=1ecf5f55-9545-44d6-b0f4-
4e4a7f5f5e68&tab=librarydocuments
Bonney's system has been compromised by a gruesome malware.
What is the primary step that is advisable to Bonney in order to contain the malware incident from spreading?
A.
Complaint to police in a formal way regarding the incident
B.
Turn off the infected machine
C.
Leave it to the network administrators to handle
D.
Call the legal department in the organization and inform about the incident
Turn off the infected machine
| Page 2 out of 9 Pages |
| Previous |